Critical Apache OFBiz Zero-day AuthBiz (CVE-2023-49070 and CVE-2023-51467)
Cybersecurity researchers recently uncovered a critical flaw in the widely used Apache OFBiz Enterprise Resource Planning (ERP) system, CVE-2023-51467.
The zero-day vulnerability CVE-2023-51467 poses a significant threat, boasting a CVSS score of 9.8. This authentication bypass vulnerability stems from an incomplete patch for a previously disclosed Pre-auth Remote Code Execution (RCE) vulnerability, CVE-2023-49070.
Recognizing the system’s wide install base, attackers have exploited this flaw with large-scale attempts.
This blog delves into the details of these vulnerabilities, shedding light on their potential impact and the exploitation techniques employed by attackers.
What is Authentication Bypass Vulnerability?
An authentication bypass vulnerability is a security flaw that allows an attacker to gain unauthorized access to a system or application without providing the proper authentication credentials, such as usernames and passwords.
In essence, it enables an intruder to circumvent the standard authentication mechanisms designed to verify the identity of users and grant access only to those with the correct credentials.
Common causes of authentication bypass vulnerabilities include programming errors, flawed logic in the authentication mechanisms, incomplete patches or updates, or the misuse of certain features.
In the case of Apache OFBiz, the zero-day vulnerability CVE-2023-51467 was attributed to an incomplete patch. The Pre-auth Remote Code Execution (RCE) vulnerability CVE-2023-49070 did not fully fix the underlying issues.
Attackers adeptly analyzed the existing patch, identifying potential flaws and discovering alternative endpoints susceptible to exploitation.
Addressing the Apache OFBiz vulnerability CVE-2023-51467, the importance of virtual patching shines through. Virtual patching offers a swift and robust solution, bridging the gap when traditional patches fall short. Learn more about the protective power of virtual patching.
Vulnerability Analysis
CVE-2023-51467
Severity: Critical
CVSSv3.x: Base Score: 9.8 CRITICAL
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
CVSSv2: Base Score: 9.3 HIGH
Vector: (AV:N/AC:M/Au:N/C:C/I:C/A:C)
Exploit available in public: Yes
Exploit complexity: Low
Unveiled on December 26, 2023, with an identical CVSS v3.x rating of 9.8, this vulnerability emerged from a detailed analysis of the root causes of authentication weaknesses in Apache OFBiz.
Exploitable by remote, unauthenticated attackers manipulating request parameters, CVE-2023-51467 enabled complete bypassing of OFBiz’s authentication and authorization checks.
Significantly, it represented the core authentication weakness that initially manifested through the XML-RPC vector in CVE-2023-49070, making OFBiz servers vulnerable irrespective of XML-RPC being disabled.
CVE-2023-49070
Severity: Critical
CVSSv3.1: Base Score: 9.8 CRITICAL
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Disclosed on December 5, 2023, with a critical CVSS v3.x score of 9.8, this vulnerability exposed a flaw in handling password change parameters within the XML-RPC code in the Apache OFBiz system.
Exploiting this flaw allowed remote unauthenticated attackers to bypass authentication checks, leading to potential remote code execution on vulnerable OFBiz servers.
Exploitation Analysis
Researchers successfully crafted a proof-of-concept (PoC) exploit code for CVE-2023-51467, demonstrating its severity. Two distinct test cases were devised to exploit the vulnerability:
Test Case 1: Empty Credentials with requirePasswordChange=Y:
- The USERNAME and PASSWORD fields are intentionally kept blank.
- The URI includes requirePasswordChange=Y.
- The login function surprisingly returns requirePasswordChange, despite both parameters being empty.
- The conditional block is bypassed, allowing the checkLogin function to return success and facilitating authentication bypass.
Test Case 2: Known Invalid Values with requirePasswordChange=Y:
- Known invalid values are assigned to the USERNAME and PASSWORD parameters.
- The URI retains requirePasswordChange=Y.
- Similar to the previous case, the login function responds with requirePasswordChange.
- The conditional block is again bypassed, leading to a successful authentication bypass.
This dual-threat vulnerability allows unauthorized access and opens the door to a Server-Side Request Forgery (SSRF) exploit, adding complexity to the potential repercussions for organizations relying on Apache OFBiz.
Prevention and Mitigation
If the Apache OFBiz vulnerability is exploited, it could lead to severe risks. Unauthorized access could grant attackers control over the system, compromising confidential information and disrupting vital services.
The exploit might also create opportunities for supply chain attacks.
Given the widespread use of Apache OFBiz, a large-scale, coordinated attack could target multiple sectors simultaneously, leading to a more extensive and severe issue.
Therefore, addressing such vulnerabilities promptly is crucial to mitigate these risks.
Affected Versions:
- CVE-2023-51467: 18.12.10 and below are impacted.
- CVE-2023-49070: 18.12.9 and below are affected.
Address a security vulnerability by upgrading to the latest release, Apache OfBiz 18.12.11. Review the Apache Security Advisory for the latest security updates – Apache Security Advisory.
AppTrana WAAP Threat Coverage
AppTrana’s Web Application and API Protection (WAAP) customers are protected against CVE-2023-51467 and CVE-2023-49070.
In addition to the official patches, our dedicated Indusface Managed service team has deployed an extra layer of defense through a customized rule.
| Rule ID | Name |
| 99946 | Apache OFBiz Auth bypass and Pre-Auth RCE Vulnerability (CVE-2023-49070 and CVE-2023-51467) |
This rule quickly finds and stops any misuse of Apache OFBiz weaknesses without relying on vendor patches.
AppTrana WAAP in action – A practical demo of an authentication bypass attack on Apache OFBiz:
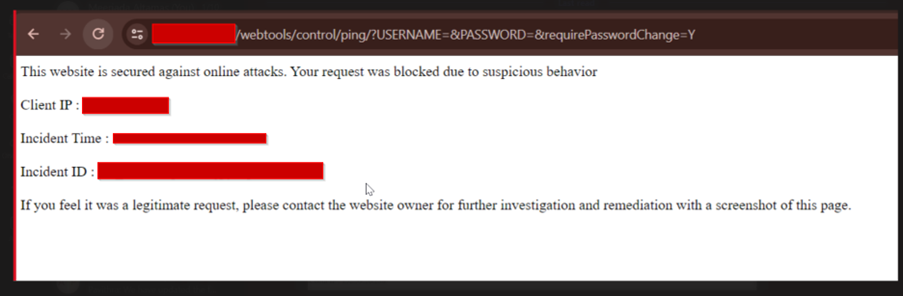
Malicious requests sent via Burp are promptly blocked by the WAAP, accompanied by a robust response with a status code 406.
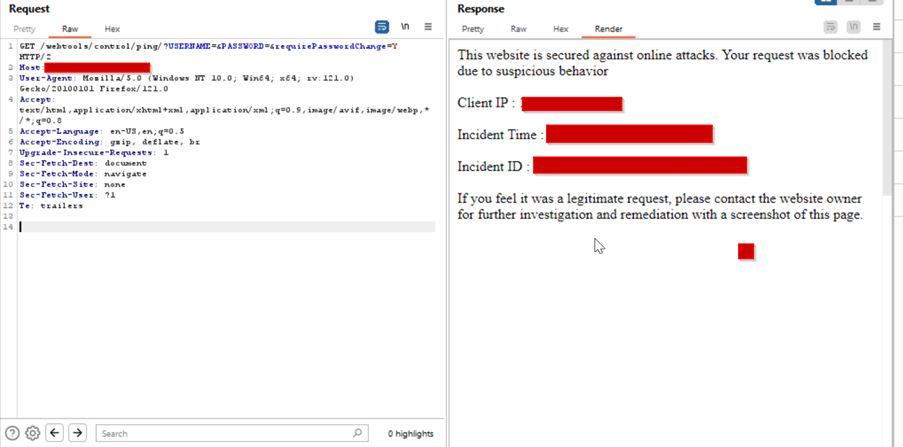
The error message displayed along with incident details:
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 January 16, 2024
January 16, 2024



