What is XML-RPC? Benefits, Security Risks, and Detection Techniques
XML-RPC is a powerful and versatile protocol in the ever-evolving web development and data communication landscape.
XML-RPC, which stands for Extensible Markup Language – Remote Procedure Call, provides a standardized way for software applications to communicate over the Internet.
XML-RPC for PHP is affected by a remote code-injection vulnerability. An attacker may exploit this issue to execute arbitrary commands or code in the webserver context. This may facilitate various attacks, including unauthorized remote access.
Find this vulnerability on your site with Free Website Security Scan.
In this blog, we will delve into the details of XML-RPC, examining its architecture, benefits, use cases, security vulnerabilities, and proactive measures for risk mitigation.
What is XML-RPC?
XML-RPC is a remote procedure call (RPC) protocol that uses XML to encode its messages and HTTP as the transport mechanism. It allows software applications running on different operating systems and written in different programming languages to communicate seamlessly.
XML RPC simplifies invoking procedures or methods across a network by enabling applications to request and receive responses in a standardized XML format.
XML-RPC Then and Now
XML-RPC traces its origins back to the late 1990s when Microsoft and UserLand Software developed it. The goal was to create a protocol that facilitates communication between different systems in a straightforward and language-neutral manner. The initial version was introduced in 1998, and since then, XML-RPC has gained widespread adoption due to its simplicity and ease of implementation.
XMLRPC is still used in specific contexts, but its popularity had decreased compared to newer communication protocols and data interchange formats. Technologies like JSON-RPC and RESTful APIs (often JSON or XML) have gained more traction due to their simplicity, ease of use, and compatibility with modern web development practices.
However, it’s essential to note that technology trends can change, and adopting specific protocols may vary across industries and use cases. XML-RPC is still in use in legacy systems, and some applications or services might continue to rely on it for specific purposes.
Key Components of XML-RPC
In XML-RPC, an HTTP request is sent to a server implanting the protocol. A client in the scenario is a software wanting to call a single method of the remote system. Multiple input parameters can be passed to the remote process; one return value is returned. The nesting of the parameter types can be used to transport a larger request structure. Therefore, XML-RPC can be used to transport objects or structures both as input and as output parameters.
The main difference between REST and XML-RPC protocols is that where resource representations (documents) are transferred, XML-RPC is designed to call methods.
Message Structure:
XML-RPC messages are encoded in XML format, making them human-readable and easy to understand. A typical XML-RPC message consists of a method call or response, with parameters passed as elements within the XML structure.
HTTP as the Transport:
XML-RPC utilizes HTTP as the transport protocol, allowing it to piggyback on existing web infrastructure. This makes it firewall-friendly and ensures compatibility with various network configurations.
Advantages of XML-RPC
Simplicity: XML-RPC is known for its simplicity. The XML format is easy to understand, and the protocol is lightweight. This simplicity contributes to quick adoption and ease of implementation.
Interoperability: XML-RPC promotes interoperability by allowing different systems, written in other programming languages, to communicate seamlessly. If the systems can understand XML and HTTP, they can exchange information using XML-RPC.
Web-Friendly – Leveraging HTTP as its transport protocol, XML-RPC easily traverses firewalls and proxies. This makes it a suitable choice for web-based applications that need to communicate over the internet.
Use Cases of XML-RPC
Content Management Systems (CMS) – Many CMS platforms use XML-RPC for remote content management. This allows users to create, update, and retrieve website content from external applications or services.
Blogs and Wikis: Blogging platforms often employ XML-RPC to enable users to publish and manage their blog posts remotely. This allows for creating third-party tools that can interact with the blogging platform.
E-commerce: In e-commerce, XML-RPC can facilitate communication between different components of an online store, such as inventory management, order processing, and payment systems.
Integration with Third-Party Services: XML-RPC is commonly used to integrate web applications with third-party services. This allows for seamless data exchange between different platforms and enhances the overall functionality of web applications.
The Security Risks in XML-RPC Files
While XML-RPC offers simplicity and ease of use, it is important to know the security risks associated with its implementation.
Vulnerability in XML-RPC allows an attacker to make a system call, which can be dangerous for the application and servers. Also, an attacker can use this method to craft a successful DOS attack against the application.
Various exploits like the Apache OFBiz 0-day exploit are publicly available, which can be used by an attacker to leverage the presence of XML-RPC on the application server.
Here are some key considerations:
Data Exposure
XML-RPC communicates using plain text, and the XML data is easily readable. Without proper encryption, sensitive information transmitted over XML-RPC can be intercepted and exposed. Secure communication channels, such as HTTPS, are crucial to encrypt data in transit and protect against eavesdropping.
Injection Attacks
XML-RPC, like other web-based protocols, is susceptible to injection attacks. Malicious actors may attempt to inject malicious XML code into requests, exploiting vulnerabilities in the server’s processing of XML data. Proper input validation and sanitation are essential to mitigate the risk of SQLi and other injection attacks.
DDoS Attacks
In WordPress, hackers can exploit the pingback feature and the xmlrpc.php file to launch DDoS attacks. By bombarding a targeted page with numerous pingback requests through xmlrpc.php, they overwhelm servers, causing the site to go offline. To bolster security, consider disabling xmlrpc.php on your WordPress website.
Brute Force Attacks
A brute force attack on an XML-RPC PHP file involves an attacker systematically attempting to gain unauthorized access by trying numerous username and password combinations. Beginning with identifying a target system utilizing XML-RPC functionality implemented in PHP, the attacker proceeds to enumerate valid usernames and then deploys automated tools to systematically guess passwords for each username.
This process continues until a successful login is achieved or until security measures, such as account lockouts, CAPTCHA challenges, or IP blacklisting, detect and thwart the attack. The attacker’s goal is to exploit vulnerabilities in the authentication system, emphasizing the importance of implementing robust security measures to safeguard against such malicious activities.
Lack of Authentication and Authorization
XML-RPC services may be exposed without proper authentication and authorization mechanisms. Unauthorized access to sensitive functionalities can lead to data breaches or unauthorized manipulation of resources. Implementing strong authentication and fine-grained authorization controls is essential for securing XML-RPC services.
XML Entity Expansion Attacks
XML-RPC messages can be susceptible to XML External Entity (XXE) attacks. An attacker may attempt to exploit the parsing of XML data to disclose sensitive information or cause a denial of service. Implementing secure XML processing practices and disabling external entity expansion is crucial to mitigating XXE attacks.
Detection of XML-RPC
Periodically conduct security audits and penetration testing to identify and address potential vulnerabilities. Engage in code reviews, static code analysis, and dynamic testing to ensure the security robustness of your XML-RPC implementation.
Crawl the FULL web application to see whether XML-RPC is being used or not. Once you get the URL, try to access the URL in the browser.
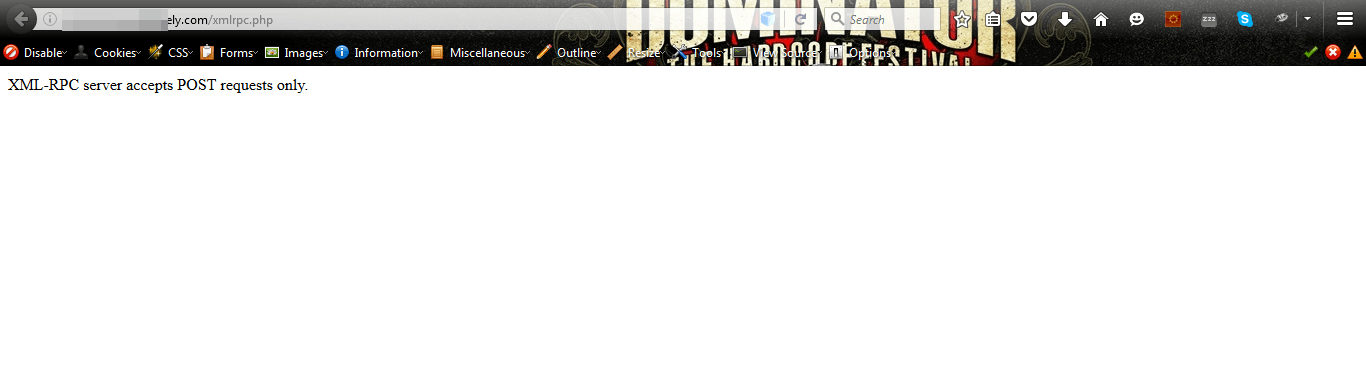
See the burp response for the same below
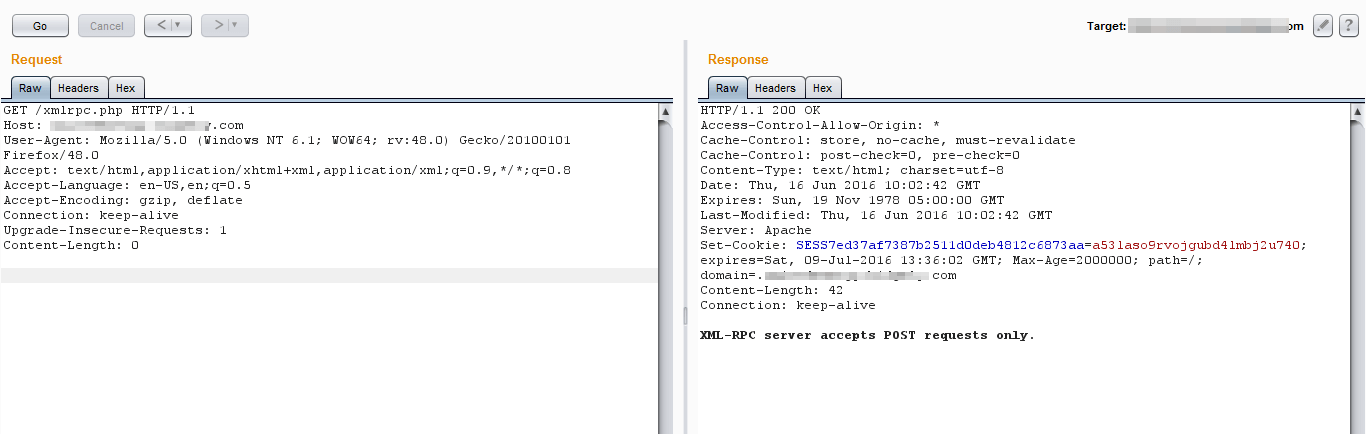
After detecting that XML-RPC is enabled on the server, an attacker can craft an XML request to list down all the methods enabled on the server, as shown below. Replace Get with a POST request and add a method call in the request.
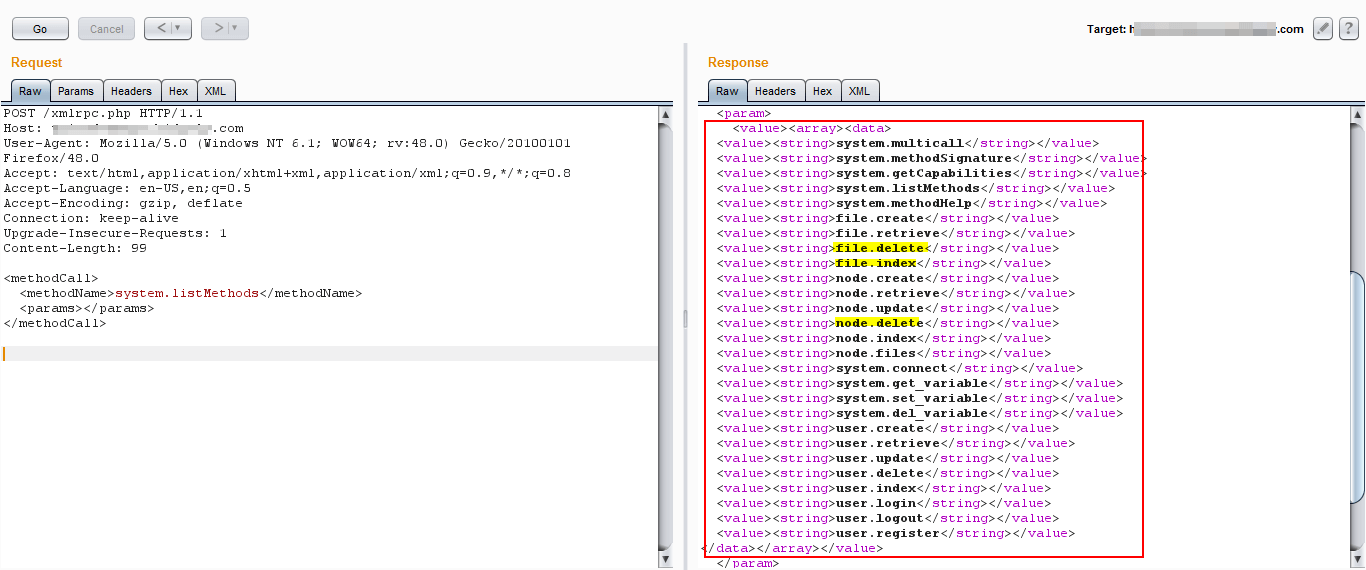
As observed in the screenshot, there are many dangerous methods like file.delete, node.delete, file. create etc, are allowed on the server-side. An attacker can use this method to perform any malicious activity. There are exploits available exploited for remote code execution.
Mitigation with AppTrana WAAP
If your XML-RPC implementation supports features not required for your application, consider disabling them. Reducing the attack surface by disabling unnecessary functionalities can enhance the overall security of your system.
AppTrana WAAP reports this remote code execution with an inbuilt DAST scanner. You can request a custom rule and POC for the vulnerability through our portal.
The Web Application Firewall will mitigate attacks by adding the following to .htaccess -file
<Files xmlrpc.php>
Order allow, deny
Deny from all
</Files>
Try our Free for Life Website Security Check to find out such issues.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 January 17, 2024
January 17, 2024






