The OWASP Top 10 is a list of the most critical web application security risks, regularly updated by the Open Web Application Security Project (OWASP) community. Each risk is assigned a risk score, which helps organizations prioritize their security efforts based on the severity and potential impact of the vulnerabilities.
The risk score considers factors such as ease of exploitability, prevalence, and detectability.
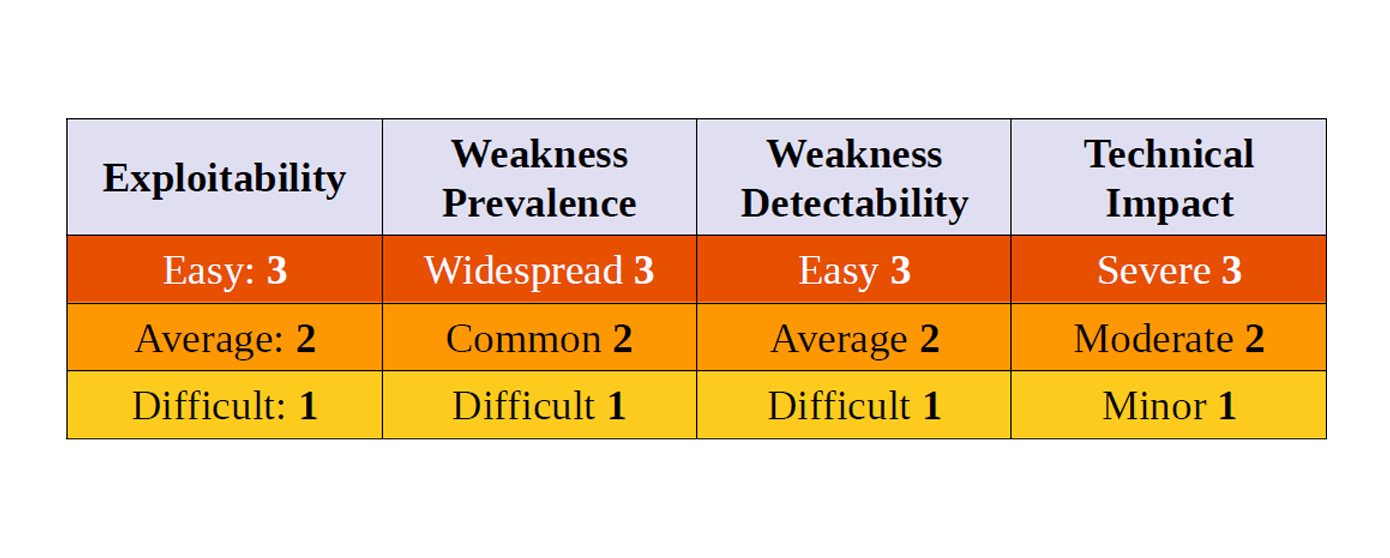
image source: OWASP
Understanding the OWASP Top 10 risk score can help you better assess and mitigate potential security risks in their web applications and APIs.
The exploitability score measures how likely a vulnerability is to be exploited. It considers various factors such as the type of vulnerability, the complexity of the attack required to exploit it, and the prevalence of tools and techniques that can be used to exploit it.
The score is typically calculated on a scale of 1 to 3, with 3 being the most exploitable. A vulnerability with a score of 3 would be very easy to exploit, whereas a score of 1 would indicate that the vulnerability is very difficult or impossible to exploit.
The exploitability score can be a useful tool when dealing with a large number of vulnerabilities or when deciding which vulnerabilities to address first. By focusing on vulnerabilities with higher scores, we can prioritize our efforts and address the most critical issues first.
In the context of the OWASP API Top 10, each of these vulnerabilities has a different exploitability score based on factors such as the complexity of the exploit and the potential impact of a successful attack.
For example, Injection vulnerabilities, which allow an attacker to inject malicious code into an application, typically have a high exploitability score, as they can be relatively easy to exploit and can significantly impact the target system.
In contrast, vulnerabilities such as Insufficient Logging and Monitoring, which can allow attackers to cover their tracks and evade detection, typically have a lower exploitability score. While these vulnerabilities can still pose a risk to an organization, they may be less attractive to attackers due to the additional effort required to exploit them.
The OWASP Top 10 uses the weakness prevalence score to help rank the most common types of vulnerabilities.
The weakness prevalence score is a metric used to measure the frequency of occurrence of specific software vulnerabilities. It is calculated by dividing the number of instances of a particular vulnerability type by the total number of vulnerabilities in each dataset or population. The score indicates how common a particular type of vulnerability is relative to other types of vulnerabilities in the same dataset.
Security experts often use the weakness prevalence score to identify the most common types of vulnerabilities and prioritize their remediation efforts accordingly.
For example, if a particular type of vulnerability has a high weakness prevalence score, it may be considered a higher priority for remediation than a less common vulnerability type.
Security misconfiguration is a common vulnerability when a web application is not configured correctly, leaving it vulnerable to potential attacks. This vulnerability has a prevalence score of 3 in the OWASP Top 10 because it is a widespread issue that can affect many types of web applications and APIs and have serious consequences if exploited by attackers.
The prevalence score of 3 indicates that security misconfiguration is a relatively common issue, affecting a significant number of web applications.
The detectability score is one of several factors used to calculate the overall ranking of each vulnerability type.
The detectability score is a metric used to measure the ease of detection of a particular vulnerability. It indicates how difficult it is to discover a given vulnerability based on factors such as the complexity of the vulnerability, the skill level required to identify it, and the amount of time and resources required to perform the necessary testing and analysis.
The detectability score of Broken Function Level Authorization vulnerability in the OWASP Top 10 is one because this type of vulnerability can be difficult to detect through automated scanning tools or other common detection methods.
Because BFLA often involves logic flaws in the application code, it can be difficult to detect using automated scanning tools. Furthermore, this vulnerability may not be apparent to users or administrators, as the application may function normally even if unauthorized access occurs.
The technical impact score is used in the OWASP Top 10 to help prioritize remediation efforts. The vulnerabilities with a higher technical impact score are considered more critical and require more attention.
The technical impact score is based on several factors, including the level of access that an attacker could gain if the vulnerability were exploited, the sensitivity of the data that could be compromised, and the extent to which the vulnerability could be used to launch further attacks against the application or other systems.
The 2019 edition of the OWASP Top 10 API includes technical impact scores for each vulnerability type, with – Broken Object Level Authorization and Broken User Authentication ranked as the highest-risk vulnerabilities based on their Technical Impact Scores.
This post was last modified on February 13, 2024 12:04
Introduction to Social Media Bots Social media bots, also known as social bots, are automated… Read More
Introduction to Sneaker Bots Sneaker bots, also called shoe bots, are automated software programs or… Read More
Introduction to Spam Bots Spam bots, short for "spam robots" or "spamming robots," are automated… Read More