Understanding the Zimbra Cross-Site Scripting Flaw (CVE-2023-37580)
On November 16, 2023, Google’s Threat Analysis Group revealed an alarming vulnerability in Zimbra Collaboration—a reflected cross-site scripting (XSS) vulnerability assigned CVE-2023-37580.
The Zimbra Collaboration Suite (ZCS) is a software platform that combines email, calendar, contacts, file sharing, and other collaboration tools into a single integrated package.
The CVE-2023-37580 allows an attacker to inject a malicious script directly into the URL parameter. The attacker’s code gets embedded within the application’s response, which is then sent back to the user’s browser.
When users click on a harmful link, these malicious scripts get executed. This flaw in the application can lead to unauthorized access to sensitive information, control over the user’s session, execute arbitrary code, or even can manipulate the entire webpage.
Campaigns Exploiting the Zimbra Cross-site Scripting Vulnerability
Google’s Threat Analysis Group (TAG) recently discovered four instances that exploited the CVE-2023-37580. The origin of these incidents dates to June of this year, when the issue was first identified as a zero-day vulnerability, indicating it was exploited before the creators could address it. Despite the official fix being issued in August, a fourth attack surprisingly persisted.
Initial Exploitation (June 2023):
In June, the CVE-2023-37580 flaw was first exploited in the real world, targeting a government organization in Greece.
Hackers used deceptive web links in emails to exploit the vulnerability.
Second Campaign (July 2023):
Another hacking group capitalized on the security issue for two weeks until the official fix arrived in July 2023.
During this period, numerous web links to exploit the vulnerability were discovered, primarily targeting government bodies in Moldova and Tunisia.
The group associated with Winter Vivern (UAC-0114) conducted phishing attacks against government organizations in Ukraine and Poland in February 2023.
Although not directly linked to the CVE-2023-37580 flaw, it represents another instance of cyber activity related to government organizations.
Third Campaign (July 2023)
Just a few days prior to the official patch release, an undisclosed group initiated a third campaign with the goal of stealing credentials from a public sector organization in Vietnam. The attack included credential phishing in Vietnam and the theft of Zimbra authentication tokens in Pakistan.
Post-Patch Activity (August 2023):
In August 2023, following the release of the official fix for CVE-2023-37580, a new wave of cyber activity was identified.
A fourth campaign leveraging the same vulnerability was discovered, targeting a Pakistan-based government organization. This campaign also aimed to steal the Zimbra authentication token.
The token was exfiltrated to ntcpk[.]org.
An example that could trigger the XSS for this vulnerability:
which decodes to:
The way attackers exploited was quite basic: it involved inserting harmful stuff into the web address itself, which caused issues because of how the website dealt with these addresses.
The exploitation was simple because it’s a typical case of reflected Cross-Site Scripting in an HTTP GET parameter.
CVE-2023-37580 Vulnerability: Key Details
Severity: Medium
CVSSv3.1: Base Score:6.1 Medium
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
CVSSv2: Base Score: N/A
NVD score not yet provided
Exploit available in public: Yes
Exploit complexity: Low
AppTrana WAAP Coverage for Zimbra XSS Vulnerability
Designed to ensure the security of web applications and APIs, AppTrana WAAP is a comprehensive solution that actively identifies and tackles threats in real-time. Protection against the XSS vulnerability is covered under our default CRS (Core Rule Set) and Premium rules.
AppTrana effectively stops this vulnerability exploitation with the following key features:
Vulnerability Scanning and Assessment
AppTrana WAAP, bundled with a DAST scanner, conducts regular vulnerability scans and assessments for your web applications.
By thoroughly inspecting the components and libraries of your application, AppTrana identifies any occurrences of CVE-2023-37580 or other known vulnerabilities. This proactive approach enables you to address potential weaknesses before attackers can exploit them.
Web Application Firewall (WAF)
Applying a fully managed WAF, AppTrana is a protective shield for your application against potential threats. By examining incoming traffic, the WAF filters out malicious requests attempting to exploit CVE-2023-37580.
It uses rule-based and anomaly-detection techniques to detect and block suspicious activities, preventing unauthorized access and XSS attacks.
Delve deeper into the preventive strategies of the WAF by exploring our detailed blog on how a WAF works.
Practical demonstration of XSS attack used at Zimbra:
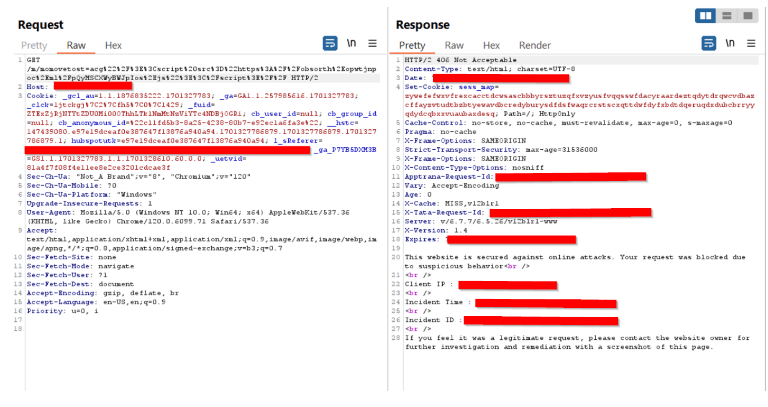
Image: Malicious request sent using burp, and the request is blocked by WAF with a response 406
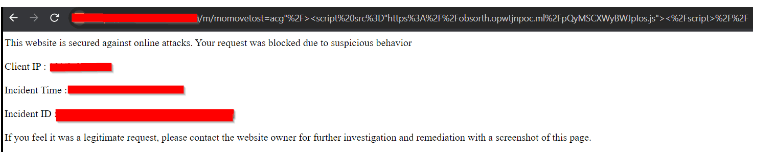
Image: Error message Displayed with the incident details
Sample other XSS attacks used across Wild
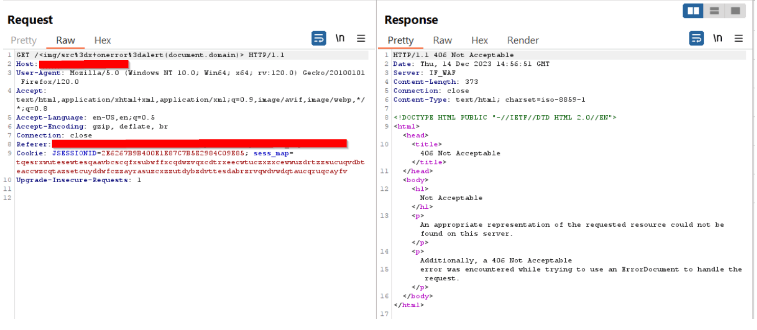
Malicious request sent using burp, and the request is blocked by WAF with a response of 406
The Power of Virtual Patching
Many threats and vulnerabilities emerge daily in the wild, posing constant risks to online security. These emerging risks can take various forms, from new attack methods to discovered weaknesses in software or systems.
AppTrana WAAP serves as a critical shield by immediately identifying and addressing these threats in this landscape.
The true strength lies in virtual patching, where our security team promptly thwarts requests exploiting CVEs. AppTrana comes equipped with pre-defined rules covering a wide array of CVEs in a default list.
Empowered by custom rule sets, you gain the ability to promptly address unpatched XSS vulnerabilities or newly identified weaknesses resulting from modifications to the application.
The power of virtual patching unfolds as a proactive defense against the ever-evolving landscape of digital threats.
References
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 December 18, 2023
December 18, 2023




