Critical OWASP Mobile Top 10 2023 Vulnerabilities [+Mobile App Pen-testing Checklists]
Get Android & iOS App Penetration Testing Checklists with OWASP Mobile Top 10
Securing mobile applications poses distinct challenges compared to websites. Mobile apps require specialized attention with risks ranging from secure data transfer to device-specific vulnerabilities.
Businesses need the right resources and guidance to protect their mobile applications. The OWASP Mobile Top 10 is a good starting point as it outlines the risks and provides actionable tips for mitigating risks.
Considering the latest threats and vulnerabilities that have emerged since the previous release in 2016, OWASP presents the mobile application OWASP Top 10 2023 – Initial release.
OWASP Top 10 Mobile Risks 2023 ( Initial Release )
M1: Improper Credential Usage
M2: Inadequate Supply Chain Security
M3: Insecure Authentication/Authorization
M4: Insufficient Input/Output Validation
M5: Insecure Communication
M6: Inadequate Privacy Controls
M7: Insufficient Binary Protections
M8: Security Misconfiguration
M9: Insecure Data Storage
M10: Insufficient Cryptography
OWASP Top 10 Mobile Risks 2016
M1: Improper Platform Usage
M2: Insecure Data Storage
M3: Insecure Communication
M4: Insecure Authentication
M5: Insufficient Cryptography
M6: Insecure Authorization
M7: Client Code Quality
M8: Code Tampering
M9: Reverse Engineering
M10: Extraneous Functionality
Comparison: Top 10 OWASP Mobile 2023 vs. 2016
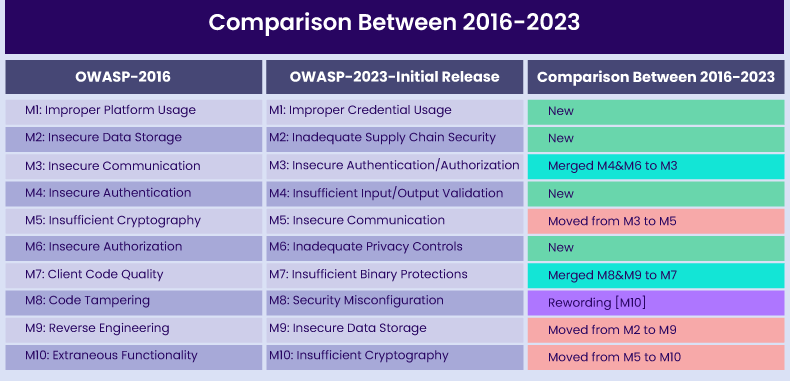
Unchanged Categories:
M5: Insecure Communication
2016: Ranked at position M3
The focus on securing communication channels suggests an awareness of the vulnerabilities associated with data in transit. This aligns with the increasing dependence on mobile devices for communication and the need to protect sensitive information during transmission.
M10: Insufficient Cryptography
2016: Ranked at position M5
The persistent importance of insufficient cryptography across both lists underscores its continued critical role in mobile security. It highlights the constant need for solid encryption practices to protect sensitive data.
M9: Insecure Data Storage
2016: Ranked at position M2
The retention of Insecure Data Storage at M9 underscores its sustained importance in mobile security. Despite its shift in ranking, this reflects an ongoing concern for securing data storage to prevent unauthorized access and potential data breaches.
New Additions:
M1: Improper Credential Usage
This new addition to the top 10 OWASP mobile 2023 indicates a broader concern for the mishandling of user credentials, possibly reflecting the importance of authentication methods and a focus on user identity protection.
M2: Inadequate Supply Chain Security
Reflects a growing recognition of securing the entire supply chain, from development to distribution. This addition acknowledges the potential risks introduced at various stages of the mobile development lifecycle.
M4: Insufficient Input/Output Validation
Indicates an expanded focus on the validation of input and output, suggesting a more thorough examination of data integrity throughout the mobile application’s processes.
M6: Inadequate Privacy Controls
Points to an evolving concern for user privacy. With increased awareness and regulations surrounding data privacy, ensuring robust privacy controls has become a prominent aspect of mobile security.
Categories that have been Updated
M3: Insecure Authentication/Authorization (2023): (Merged from M4 and M6(2016))
Compiling authorization alongside authentication highlights a more comprehensive approach to user access control. This update recognizes that secure authentication alone may not be sufficient without proper authorization mechanisms.
M7: Insufficient Binary Protections (2023): (Merged M8 & M9 (2016))
The merging of “Reverse Engineering” and “Code Tampering” into “Insufficient Binary Protections” reflects a consolidated approach to addressing threats related to the security of mobile application binaries.
M8: Security Misconfiguration (2023): (Rewording M10(2016))
Involves incorrect configuration settings within mobile applications, exposing them to potential security vulnerabilities.
This may lead to unauthorized access, data exposure, or exploitation of misconfigured settings by attackers.
The Complete Top 10 OWASP Mobile 2023 Risks
M1: Improper Credential Usage
The OWASP top ten mobile’s first risk, “Improper Credential Usage,” underscores the critical issue of mishandling credentials within mobile applications.
One specific manifestation of this risk is the prevalence of hardcoded credentials in application binaries, a common but dangerous practice. Hardcoded credentials pose a significant security risk as they can be easily exposed, leading to unauthorized access and potential harm to the business.
Attackers can leverage vulnerabilities associated with both hardcoded credentials and improper credential usage.
Once these vulnerabilities are identified, attackers can exploit hardcoded credentials to infiltrate the application, potentially gaining access to sensitive data and functionalities.
Additionally, they may misuse credentials by exploiting improperly validated or stored credentials, bypassing legitimate access controls.
Mobile Application Vulnerabilities to Look For:
- Hardcoded Mobile Application Vulnerabilities
- Insecure Credential Transmission
- Insecure Credential Storage
- Weak User Authentication
- Poor Credential Management Mistakes
Prevention and Mitigation Strategies:
- Refrain from embedding credentials directly in the source code.
- Utilize secure communication protocols (e.g., HTTPS) to encrypt credential transmission.
- Prevent interception risks by avoiding plain text transmission of credentials.
- Enforce strong password policies to enhance overall user authentication security.
- Conduct frequent security assessments, including penetration testing and code reviews.
- Use automated tools to scan for hardcoded credentials and other security weaknesses.
M2: Improper Supply Chain Security
The supply chain encompasses the entire process from collecting materials, such as software libraries and SDKs, through the development phase to the final distribution via mobile app stores. Failures in securing this supply chain can introduce vulnerabilities that adversaries may exploit.
For example, an attacker could put malicious code in a mobile app or change it while building it. This could let them steal info, spy on users, or control the mobile device. They might also find weaknesses in other software parts to get into the app or servers, causing problems like unauthorized access or completely taking over the app or device.
Prevention and Mitigation Strategies
- Regularly assess and vet software libraries and SDKs for security vulnerabilities.
- Implement a secure process for selecting and incorporating third-party components.
- Ensure that the development environment is secure and free from vulnerabilities.
- Implement code signing to verify the integrity of the application during the distribution phase.
- Employ mechanisms to detect and prevent tampering or unauthorized modifications.
- Partner with reputable app stores and leverage secure distribution channels.
- Regularly monitor and verify the app’s integrity during the distribution process.
M3: Insecure Authentication/Authorization
Unlike traditional web apps, mobile devices’ unique input form factor often leads to weaker authentication practices, such as using shorter passwords like 4-digit PINs.
Additionally, the irregular and less predictable nature of mobile internet connections requires thoughtful consideration for offline authentication, introducing complexities for developers.
In addition to authentication challenges, improper authorization practices can amplify risks in mobile app security.
Improper authorization may result in users accessing functionalities or data beyond their intended scope, potentially leading to data breaches or misuse.
Exploiting these security risks in mobile apps can occur through two distinct methods:
1. Authentication Manipulation:
Attackers can manipulate authentication by forging or bypassing it, submitting service requests directly to the app’s backend without engaging with the app directly.
2. User Impersonation and Administrative Actions:
Another tactic involves attackers logging in as legitimate users and navigating to specific mobile application threats. This enables them to execute administrative functionalities stealthily.
Protection and Mitigation Strategies:
- Enforce complex password requirements and regular updates.
- Add an extra layer of security with methods like SMS codes or biometrics.
- Store passwords using strong hashing algorithms and include salting.
- Implement secure session timeouts and reauthentication mechanisms.
- Protect against attacks like brute force and implement secure communication (HTTPS).
- Implement mechanisms to lock out accounts after a certain number of failed login attempts.
- Use RBAC to assign specific permissions based on user roles.
M4: Insufficient Input/Output Validation
The process of validating inputs is a common practice to examine potentially harmful data, ensuring its safety for processing within the code or when interfacing with other components.
When software fails to perform proper input validation, it opens the door for attackers to manipulate inputs in unexpected ways. Consequently, various system parts may receive unintended input, potentially leading to SQL injection, Command Injection, and cross-site scripting (XSS) attacks.
In scenarios involving sensitive information, insufficient output validation can lead to the inadvertent exposure of confidential data. For instance, if a system fails to properly validate and sanitize output in log files or error messages, it may unintentionally disclose sensitive information.
These security lapses can lead to unauthorized access data manipulation and compromise the overall integrity of the mobile app.
Protection and Mitigation Strategies
- Implement thorough validation of user inputs to ensure adherence to expected criteria and reject potentially harmful data.
- Use whitelisting techniques to permit only specific, known-safe inputs, preventing unauthorized or malicious data acceptance.
- Apply output encoding to prevent interpreting malicious content as executable code, reducing the risk of injection attacks.
- Utilize parameterized queries when interacting with databases to prevent SQL injection attacks by properly separating data and code.
- Enforce Content Security Policies (CSP) to mitigate cross-site scripting (XSS) attacks by specifying valid content sources.
- Keep all security libraries and frameworks up-to-date to benefit from patches and updates addressing known vulnerabilities.
M5: Insecure Communication
Insecure communication in a mobile app refers to transmitting sensitive information (such as login credentials, personal data, or financial details) over unsecured channels, making it susceptible to interception and unauthorized access.
It is crucial for app developers to implement secure communication practices to protect user data and maintain the integrity of the application.
Risks and Impacts
- Sending data over unencrypted channels (HTTP instead of HTTPS) exposes it to potential eavesdropping.
- Without certificate pinning (SSL Pinning), attackers could perform a man-in-the-middle (MITM) attack by presenting their own SSL certificate.
- Weak authentication mechanisms or insecurely storing sensitive information (like passwords) can lead to unauthorized access.
- Lack of input validation can lead to security vulnerabilities, such as SQL injection or cross-site scripting (XSS).
Protection and Mitigation Strategies
- Use HTTPS for secure data transit.
- Utilize robust authentication methods (e.g., OAuth, tokens).
- Avoid local storage of sensitive data.
- Enforce secure session practices (e.g., timeouts, token regeneration).
- Apply TLS/SSL for secure communication.
- Implement certificate pinning to thwart MITM attacks.
- Securely store sensitive data with encryption.
- Adhere to key management best practices
M6: Inadequate Privacy Controls
Inadequate privacy controls in mobile apps pose significant risks to user data, potentially compromising sensitive information and eroding user trust. This risk arises when developers fail to implement robust measures to protect user data privacy, leading to various privacy violations.
Issues include collecting more than needed, sharing data without user consent, and careless handling of Personally Identifiable Information (PII). This exposes users to privacy violations, potential identity theft, and legal consequences.
Prevention and Mitigation Strategies
- Integrate privacy considerations from the app’s inception.
- Conduct regular privacy assessments and updates throughout the app’s lifecycle.
- Communicate data collection and usage policies to users.
- Regularly update and educate users on privacy policies, ensuring transparency.
- Implement clear and informed consent mechanisms for data collection.
- Allow users to easily manage and update their consent preferences within the app.
- Collect only the necessary data for the app’s functionality.
- Regularly review and purge unnecessary user data, minimizing potential risk.
M7: Insufficient Binary Protection
The binary code is a critical component of the app’s functionality, and its security is paramount for protecting user data and ensuring the app operates as intended.
However, attackers often target the binary code due to its vulnerability, seeking to exploit weaknesses for malicious purposes.
Attackers take advantage of this weakness by doing things like figuring out how the app works (reverse engineering), changing its code (tampering), or analyzing it while it’s running (dynamic analysis). This can lead to serious problems, such as stealing sensitive data or creating malicious app versions.
Prevention and Mitigation Strategies:
- Encrypt sensitive parts of the app’s binary code to protect them from unauthorized access and tampering.
- Use code obfuscation tools to make it harder for attackers to understand and reverse engineer the app’s code.
- Implement checks to ensure the app’s binary code has not been modified during runtime, helping detect and prevent tampering.
- Employ RASP solutions that monitor and defend the app during runtime, detecting and blocking malicious activities.
- Include mechanisms to detect if the device running the app has been rooted (Android) or jailbroken (iOS), as these conditions can make the app more vulnerable.
M8: Security Misconfiguration
Security misconfiguration refers to situations where crucial security settings are either not implemented, implemented with errors, or deployed with default (potentially insecure) settings. This vulnerability can introduce weaknesses that make the mobile app susceptible to cyberattacks or data breaches.
For instance, mobile apps often come with default settings for ease of use, but these defaults may not prioritize security. If developers fail to customize and secure these default settings, the app can be left exposed.
Prevention and Mitigation Strategies:
- Conduct routine vulnerability assessments to identify and rectify misconfigurations.
- Adhere to established security best practices and guidelines during app development.
- Customize default settings to prioritize security, considering encryption, access controls, and other protective measures.
- Employ automated security tools that can scan for misconfigurations and vulnerabilities.
- Implement continuous monitoring to detect and respond promptly to any security misconfigurations.
M9: Insecure Data Storage
Insecure data storage in mobile apps is like keeping your personal secrets in a place that’s not well-protected. Imagine if your important passwords or private information were stored on your phone without being properly guarded. This is a problem because two things can happen:
- If someone gets physical access to your phone, they can easily look at or take the information you stored.
- Some sneaky software (like viruses) can secretly enter your phone and remove your private data without you knowing.
Prevention and Mitigation Strategies
- Use encryption to lock up sensitive data, making it unreadable without the proper key.
- Store sensitive information in secure locations difficult for unauthorized users or other apps to access.
- Implement secure methods for storing and handling user passwords and identification information.
- Get rid of old or unnecessary data regularly to reduce the risk of unauthorized access.
- Apply security measures to protect data stored offline, ensuring it remains safe.
M10: Insufficient Cryptography
Insufficient cryptography refers to using encryption methods that can be easily compromised. This vulnerability can arise from flaws in the encryption process or the adoption of weak encryption algorithms to safeguard sensitive data.
It’s essential for mobile developers to grasp that the objective of cryptography is not to create unbreakable codes but rather to make breaking them impractical within a reasonable timeframe, given the current state of computational power.
Prevention and Mitigation Strategies:
- Strong algorithms, such as AES (Advanced Encryption Standard), provide a higher level of security and are less prone to vulnerabilities.
- As computational power improves, regularly updating encryption methods helps maintain their effectiveness against evolving threats.
- Proper key management is crucial for the effectiveness of encryption. Protecting encryption keys from unauthorized access is vital to prevent data breaches.
- Periodic security assessments help detect and rectify potential weaknesses in the encryption processes or algorithms.
- Using secure channels, such as HTTPS, for key exchange reduces the risk of interception or manipulation by malicious actors.
Incorporating mobile application scanning is the first crucial step in defending your apps against potential threats. This process protects your business applications from the vulnerabilities outlined in the OWASP mobile top 10 list.
Additionally, engaging pen testers to simulate hacker techniques and uncover potential vulnerabilities is essential. Their manual approach is instrumental in identifying business logic risks that automated tools might overlook. Explore our comprehensive blogs on the Android pen testing checklist and iOS pen testing checklist for detailed insights.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 December 7, 2023
December 7, 2023



