At present, nearly half the global population is online and by 2022, it is predicted that 75% of the global population will be online. Needless to say, businesses of all kinds are going online and leveraging the cutting-edge tech solutions to transform how they function and do business online. On the other hand, cybercriminals too are leveraging technological advancements and the internet to orchestrate new and innovative attacks that are extremely vicious and damaging.
Cybercrimes, according to Cybersecurity Ventures, is the greatest threat faced by every company irrespective of size, nature, and scale of operations and probably the biggest menace the world population will face for at least the next two decades. It is the fastest growing crime in the US in terms of size, sophistication, and cost of attacks. In their 2019 Official Annual Cybercrime Report, Cybersecurity Ventures also predicts that the cost of cybercrimes globally will be around $10.5 trillion by 2025, up from $3 trillion in 2015.
There have been several major hacking incidents and data breaches in the past few years including some big players like Yahoo, Equifax, and Facebook which have affected millions of users worldwide. These big players have the infrastructure and resources to recuperate from these attacks, but small and medium players may not be able to recover from such cyber-attacks and may have to shut down.
Three of the most widely used forms of cyber-attacks today are phishing (which involves clicking a link, opening an email, etc.), ransomware, and DDoS attacks. The percentage of such attacks along with zero-day attacks is forecasted to quadruple by 2025.
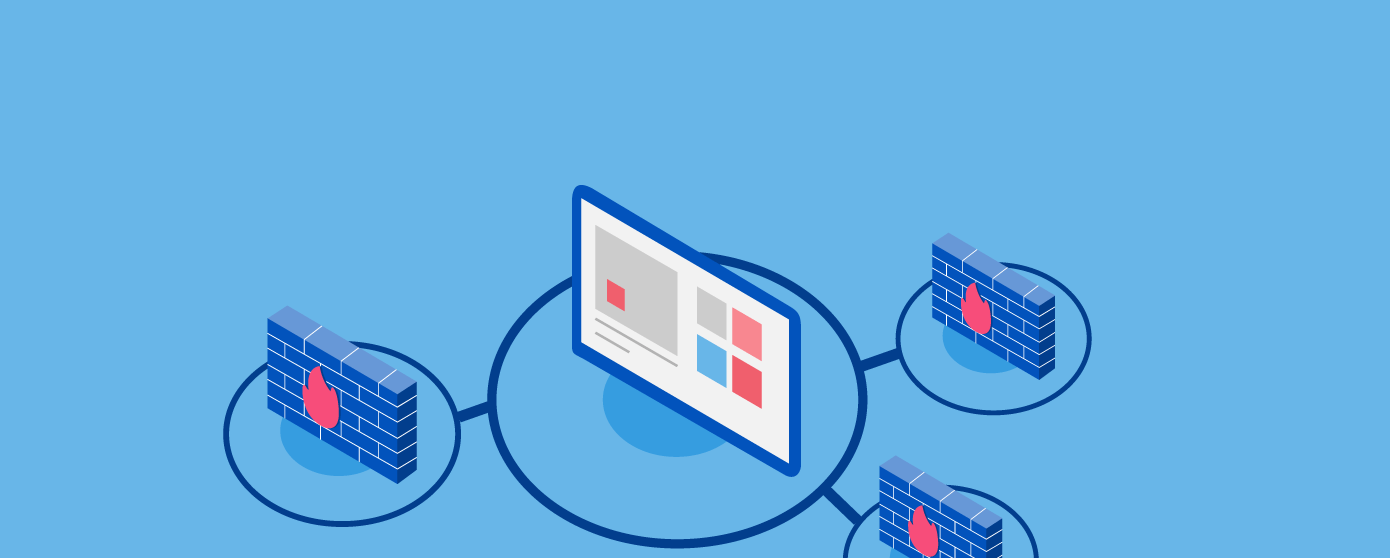
So, we cannot stress the importance of employing a comprehensive, managed cybersecurity solution like AppTrana enough. Such a solution will stop cyber-attacks and application security threats and majorly minimize their impact. The most important part of such a solution that helps increase web application security is a Web Application Firewall (WAF).
Web Application Firewall (WAF) is the first line of defense between a web application and the internet traffic and shields the web application from being accessed by malicious actors, botnets, and bad traffic. It monitors all the traffic and requests made to the application and filters out the malicious requests.
To increase the level of web application security provided by a WAF, always look out for the following.
Finding the vulnerabilities in the web application through testing is the first step to fixing it as it promotes urgency and proactiveness. It is equally important to finding it before a cyber-attacker finds it in order to have a first-mover advantage in securing the application.
In order to increase web app security, it is critical that the WAF finds the vulnerability before the bad actors and responds instantaneously when it is found. As fixing even critical vulnerabilities requires coordination with third-party teams and may take nearly 100 days, the WAF must instantaneously apply a quick virtual patch so that the gap cannot be found and exploited by the bad actors. This instantaneous virtual patching provides developers the time required to fix the vulnerabilities and reduces the risk exposure of the application.
Virtual patching is the starting point for web application security. But to increase the level of security, the WAF must provide real intelligence.
The WAF you choose must provide the foundational units of intelligence about cases of the attack attempts that the WAF blocked. Such intelligence about the attempted attacks in the form of data about that blocked user, their IP, their course of action, their session ID and other information on what all they attempted can be translated into actionable items to block the user, IP and/or create custom rules based on attack behavior to shut them off.
WAF must provide security analytics and insights into attempted attacks with its policies. As discussed in the previous point, real intelligence on attempted attacks helps thwart attacks and increase web application security.
Not just that, security analytics and insights that tell developers where the attacks are coming from and what type of attacks are happening can form the basis for the application team to take important calls and proactive actions to increase the defense posture of the application. For instance, shutting off a GEO if they do not care about business from that region and thereby, increase the defense posture or more advanced calls like throwing in a CAPTCHA based on rate controls and insights they get from the WAF dashboard.
Quoting Art Wittman (VP, Business Technology Network), “As we’ve come to realize, the idea that security starts and ends with the purchase of a prepackaged firewall is simply misguided.”
WAF is an application layer protection and to increase the security with WAF, the business needs to look not just at the product features. They must ensure that the security plan includes the expertise and creative-thinking skills of the certified application security experts along with the WAF to accomplish those aspects of security that machines and software by themselves cannot.
Management is the differentiation between a working WAF versus something that gathers dust and provides diminishing value over time. Without management, WAF will end up being a piece of box gathering dust.
Lastly, to improve web application security with WAF, it is important that there is a program in place to co-relate the current risk posture of the application with the vulnerability management programs. This will serve as the basis to create security policies and defense postures in WAF.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.
This post was last modified on December 15, 2023 12:24
Explore crucial tactics like Asset Inventory, Patch Management, Access Control & Authentication, and additional best… Read More
Delve into the data privacy questions including consent protocols, data minimization strategies, user rights management,… Read More
Secure Node.js APIs using best practices: Employ proper HTTP methods, robust authentication, and API-specific security… Read More