Zero-day Vulnerability – Examples, Detection & Prevention [+ Monthly 0-day Reports]
Get Latest Zero-Day Vulnerability Report [PDF]
Unknown threats are the real risk. One such example is, Zero-day vulnerability, having been used in real-time attacks but not yet disclosed by the software vendor.
In 2024 alone, 2851 zero-day vulnerabilities were identified in websites protected by AppTrana WAAP, highlighting the urgency of understanding and addressing these risks.
What is a Zero Day Vulnerability?
Zero-day vulnerabilities refer to security flaws in software or hardware exploited by attackers before the developer becomes aware of them.
Unlike known vulnerabilities, which developers can patch with updates, zero-day vulnerabilities are particularly dangerous because there are no existing fixes or defenses.
The term “zero-day” stems from the notion that developers have zero days to prepare for an attack once the vulnerability is discovered. These vulnerabilities often originate during software development due to coding errors or design flaws.
However, they can also arise from reverse engineering, where attackers dissect software to uncover weaknesses.
Zero Day Vulnerability Vs. Zero Day Exploits Vs. Zero Day Attack
“Zero-day” or “0-day” refers to the number of days since a vulnerability has been discovered, patched, or publicly disclosed.
When paired with terms like “vulnerability,” “exploit,” and “attack,” it provides a clearer understanding of the context and implications:
- Zero-day vulnerability refers to a flaw in software or hardware that is unknown to the vendor and remains unpatched. Attackers exploit these vulnerabilities before developers have had a chance to fix them, making them particularly dangerous.
- Zero-day exploit is software or code that uses a vulnerability for malicious actions. A zero-day exploit targets a zero-day vulnerability, allowing attackers to compromise systems, steal data, or cause harm before a patch is available.
- Zero-day attack: This term describes exploiting a zero-day vulnerability using a zero-day exploit. It highlights the proactive nature of the attackers who leverage unknown vulnerabilities to launch surprise attacks, often with devastating consequences.
Anatomy of Zero-Day Vulnerability
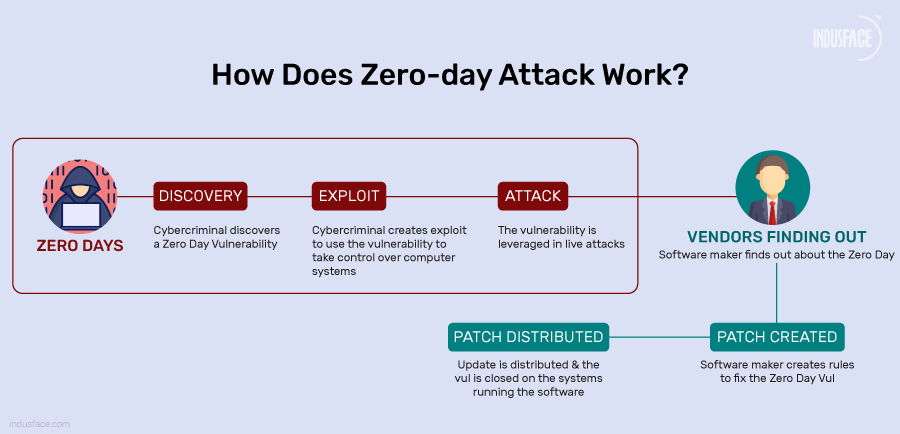
- Vulnerability Concealment: The vulnerability exists in software code but is unknown to the public and the software vendor.
- Vulnerability Discovery: It is found by a security researcher, hacker, or through automated tools during testing or analysis.
- Vulnerability Exploitation: Attackers use the vulnerability to gain unauthorized access or execute malicious code.
- Vulnerability Disclosure: The vulnerability becomes known to the software vendor or the public.
- Patch Development: The vendor works on creating and testing a fix or patch to address the vulnerability.
- Patch Deployment: Users and organizations apply the patch to their systems to protect against exploitation.
- Zero Day Attack Mitigation: Additional security measures reduce the risk until a patch can be applied to all systems.
Eventually, the vulnerability becomes obsolete as systems are patched or mitigated, but the impact may persist.
The Hidden Dangers of Zero Day Exploits
Zero-day exploits are like hidden traps in the digital world, waiting for the perfect moment to strike. Let’s uncover why they’re so dangerous in a way that’s easy to understand.
Surprise Attack
Zero-day exploits catch everyone off guard. Unlike known vulnerabilities, there’s no heads-up for software developers or security teams. Attackers can sneak in and cause chaos before anyone knows what’s happening.
No Defenses
Because they’re brand new, no shields are up against zero-day exploits. No patches, no updates, nothing. This opens computers, networks, and data for bad actors to exploit.
Significant Impact
When zero-day exploits hit, they hit hard. The impact of zero-day vulnerabilities can be disastrous, enabling attackers to execute a remote code, steal sensitive data, or disrupt critical systems. High-profile incidents like the Stuxnet worm and the Equifax data breach have underscored the devastating consequences of zero-day exploits.
Constant Battle
The fight against zero-day exploits is ongoing. It’s like a game of cat and mouse between the defenders and the attackers. Attackers are already looking for the next vulnerability as soon as one vulnerability is patched.
Examples of Latest Zero-day Attacks and Exploits
1. MOVEit Transfer Zero-Day Attack (CVE-2023–42793)
Disclosure Date: May 2023
Vulnerability Type: Remote Code Execution (RCE) Attack, Authentication Bypass
A Russian ransomware ring exploited a zero-day vulnerability in MOVEit Transfer, a managed file transfer software. The flaw, discovered through a SQL injection issue, allowed attackers to execute ransomware attacks on hundreds of organizations, including government agencies, universities, banks, and significant health networks.
This attack underscored the widespread impact of zero-day vulnerabilities, affecting any organization using the vulnerable software.
2. JetBrains TeamCity CVE-2023-42793 Authentication Bypass Vulnerability
Disclosure Date: September 20, 2023
Vulnerability Type: Authentication Bypass, RCE
JetBrains disclosed CVE-2023-42793, a critical authentication bypass vulnerability in their TeamCity CI/CD server on-premises instances. Exploiting this vulnerability allows an unauthenticated attacker with HTTP(S) access to perform a remote code execution attack, potentially gaining server administrative control.
Threat intelligence companies GreyNoise and PRODAFT reported that multiple attackers began exploiting this critical authentication bypass flaw just days after it was disclosed.
3. Cytrox Zero-Day Exploit Sales
Cytrox, a commercial surveillance company, was exposed for selling zero-day exploits to government-backed actors. Research by Meta, investigative journalists, and other researchers revealed that Cytrox engaged in indiscriminate targeting, including journalists, dissidents, opposition and human rights activists, and critics of authoritarian regimes.
This revelation sheds light on the clandestine trade of zero-day exploits and its potential impact on individuals and organizations worldwide
Other Notable Zero-Day Vulnerabilities
- Apache OFBiz 0-day AuthBiz (CVE-2023-49070 and CVE-2023-51467)
- Ivanti EPMM zero-day vulnerability
- Apache Web Server Path Traversal and File Disclosure Vulnerability (CVE-2021-41773)
Who Discovers Zero Day Vulnerability?
Zero-day vulnerabilities can be discovered by various entities, including:
Independent Security Researchers: Individual researchers or groups often uncover zero-day vulnerabilities through independent efforts, either by analyzing the software code, conducting security assessments, or participating in bug bounty programs.
Security Companies: Dedicated cybersecurity firms and companies specializing in vulnerability research actively search for zero-day vulnerabilities as part of their security research efforts. These companies may discover vulnerabilities through automated scanning, manual code analysis, or targeted research.
Government Agencies: Government agencies, particularly those involved in intelligence and national security, may discover zero-day vulnerabilities through their own research and monitoring activities. These vulnerabilities may be used for defensive purposes or exploited in offensive cyber operations.
Hackers and Cybercriminals: Unfortunately, malicious actors also play a role in discovering zero-day vulnerabilities. Some hackers and cybercriminals actively search for vulnerabilities to exploit for personal gain, such as financial profit, espionage, or sabotage.
Bug Bounty Programs: Many software vendors and technology companies run bug bounty programs that incentivize security researchers to report vulnerabilities they discover. These programs offer rewards, such as cash prizes or recognition, for responsibly disclosing vulnerabilities, including zero-day issues.
How to Identify Zero-Day Vulnerability?
Vulnerability Scanning
Vulnerability scanning is an essential aspect of cybersecurity, particularly in detecting zero-day attacks. Organizations can proactively identify vulnerabilities by systematically assessing systems and networks for potential weaknesses, including those previously unknown to software vendors.
This proactive approach enables early detection and mitigation of 0-day threats, allowing organizations to prioritize patches and security updates to prevent exploitation.
Organizations must be quick to act on the results of such a scan because attackers tend to act quite fast on vulnerabilities they find.
Behavioral Anomalies
Monitor network and system behavior for unusual patterns or activities that deviate from normal operations. This includes unexpected network traffic, unusual system resource usage, or unauthorized access attempts.
Signature-less Detection
Implement advanced threat detection techniques, such as anomaly detection and machine learning algorithms, that can identify suspicious behavior without relying on known attack signatures.
Threat Intelligence
Leverage threat intelligence feeds and information-sharing communities to stay informed about emerging threats and zero-day vulnerabilities. Proactively monitor for indicators of compromise (IOCs) associated with zero-day attacks and take appropriate action to defend against them.
Sandboxing and Emulation
Employ sandboxing and emulation techniques to analyze suspicious files or executables in isolated environments. By observing the behavior of these files in a controlled setting, you can identify potential zero-day exploits before they can cause harm.
User Behavior Analytics (UBA)
Monitor user activity and access patterns to detect abnormal behavior or unauthorized access attempts. UBA solutions can identify anomalies that may indicate the presence of a zero-day attack, such as unusual login locations or privilege escalation attempts.
Continuous Monitoring and Incident Response
Implement robust monitoring practices and incident response procedures to detect, investigate, and mitigate zero-day attacks in a timely manner. Regular security audits, penetration testing, and tabletop exercises can help prepare organizations to respond effectively to zero-day threats.
How to Protect from Zero-Day Attacks?
Here are best practices to protect your systems from 0-day attacks and enhance your zero-day protection:
Stay Up to Date
Ensure your software, operating systems, and applications are regularly updated to the latest versions. Vendors regularly release patches to fix known vulnerabilities, including zero-day exploits.
Implement Security Patches Quickly
Applying patches quickly whenever vulnerabilities are discovered is very important. It reduces the risk of an attack and sends signals to attackers that the developers are constantly looking to improve security. Efficient patch management depends on software users’ speed of development and applications.
Add virtual patching as part of your patch management strategy. Most WAFs automatically apply virtual patches to the application when vulnerabilities are identified.
Utilize Endpoint Protection
Deploy endpoint protection solutions, such as antivirus software and intrusion detection systems, to detect and prevent malicious activity on individual devices. These solutions can help identify and block zero-day exploits before they can cause harm.
Implement Least Privilege Access
Limit user privileges and access rights to only those necessary for performing job functions. This reduces the impact of potential zero-day attacks by minimizing the attack surface and limiting the scope of compromise, contributing to zero-day protection and mitigation strategies.
Educate Employees
Train employees on cybersecurity best practices, such as identifying phishing emails, avoiding suspicious links and attachments, and reporting security incidents promptly. Zero-day attacks often exploit human error, so awareness training is essential.
Use Network Segmentation
Segment your network into separate zones with different security levels to contain the spread of attacks and limit the impact of breaches. This can help prevent lateral movement by attackers and mitigate the damage caused by zero-day exploits, enhancing overall zero-day mitigation efforts.
Incident Response Plan
Given the financial, operational, and reputational damage that zero-day exploits can have on an organization, it would be advisable to have an incident response plan. The plan should help detect attacks faster, limit the damage, and recover as quickly as possible.
Zero-day Attack Mitigation with AppTrana WAAP
Vulnerability scanning and patch management only provide partial solutions to zero-day attacks. The time taken to develop and apply patches and code fixes often creates a large window of vulnerability.
The DAST Scanner embedded in AppTrana WAAP actively tracks an organization’s overall security status, providing continuous insights into potential risks, including zero-day vulnerabilities.
By leveraging virtual patching, AppTrana provides a quick solution by patching known vulnerabilities using security policies (core and custom rules), offering protection without immediate patch deployment.
Check out in detail about autonomous patching with SwyftComply.
Reducing exposure time for zero-day vulnerabilities hinges on the WAAP vendor’s update and patch timeliness.
The video illustrates how Indusface’s managed service team promptly reacted to a zero-day vulnerability in the Spring Framework using virtual patching.
Indusface security researchers constantly monitor the security landscape and lead security websites to identify any new vulnerabilities identified/published and monitor/update rules to ensure around-the-clock protection for customer sites from day zero.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 February 5, 2024
February 5, 2024




