How Web Application Firewall Can Ensure Safety?
If you have been to an airport, you know how airport security works. You must go through a thorough check and your belongings are scanned through metal detectors, walk-through body scanners, and other machines to ensure that you are not carrying any dangerous/ prohibited items on yourself or in your belongings and that it is safe to allow you entry into the airport. If necessary, you may be called aside for a thorough pat check/ frisking and your belongings may be checked by security personnel. If any security threat is detected, the security personnel will act as per protocol. These measures always help keep the security of the airport intact. Web Application Firewall (WAF) works in a similar fashion to secure websites/ web applications.
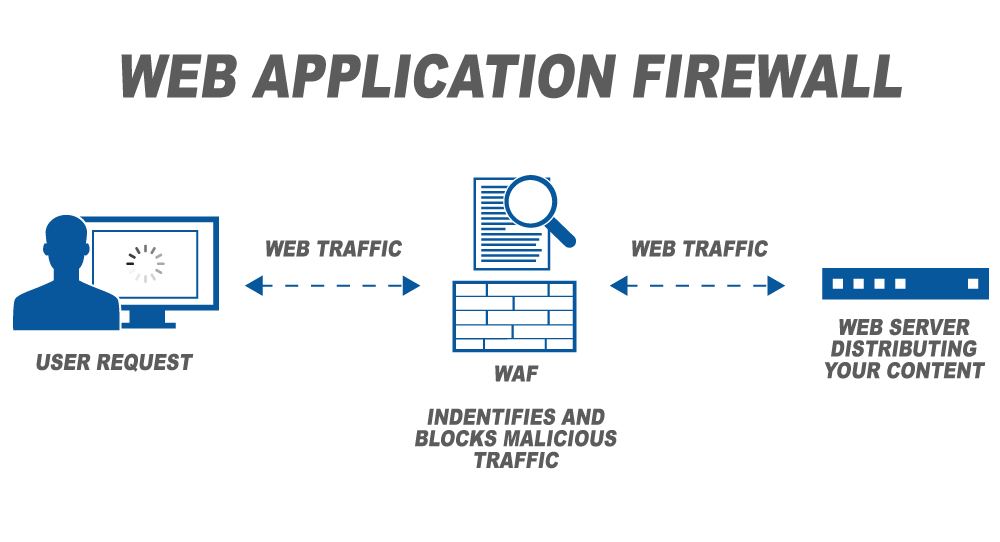
Web Application Firewall is the protective shield and first line of defense between the web application/ website/ web server and the web traffic trying to access the web servers/ websites. Every request is scanned and monitored based on the set of rules given to the WAF to filter out and block bad requests and secure the application against malicious actors, botnets, and bad traffic. They regularly scan the website to identify vulnerabilities, gaps, and loopholes and immediately patch them to ensure that the website is safe while the developers fix the vulnerability/ loophole/ weakness. (Note that it takes 100 days to fix even critical vulnerabilities).
It is important to note that not all web app firewalls are effective in securing the website. They need to have certain features that enable the WAF to be effective in ensuring safety and security. Let us take a look at these features.
How does WAF ensure safety and security?
1. Cloud deployment
WAFs are deployed as on-premise as a hardware or software installation or over the cloud. Of these ways, cloud WAFs are considered most effective to elevate web security, especially for SaaS businesses and others who heavily rely on the websites/ web applications for their services/ solutions such as e-commerce, entertainment, etc. Cloud WAFs are easy and relatively effective to deploy and maintain, updates are automatic, and updates do not disturb work or affect website speed and offer the agility required in web security for agile and dynamic websites with several moving parts.
2. Custom rules/ policies
Web App Firewalls work based on present rules, known as policies. Using the policies, they identify vulnerabilities, monitor the traffic for threats, block malicious requests, patch vulnerabilities, and take any other requisite action. These policies need to be customized based on the context, risk profile, and overall security posture of the website/ web application.
A one-size-fits-all approach does not work. While the policies to identify and thwart known vulnerabilities such as cross-site scripting, SQL injections, etc. are similar for most websites, the policies need to be tuned to equip the WAF to identify botnets and other malicious actors, prevent DDoS attacks, etc. For instance, if the business does not operate in/ does not target certain countries/ geographical locations, then the WAF policies can be tuned to block access to users from those countries, thereby, reducing the attack surface. Similarly, there also need to be custom rules to prevent business logic vulnerabilities that may pass off as legitimate requests if the policies are not custom-built with surgical accuracy.
Latest updates on Apptrana WAF Rules https://files.helpdocs.io/1fZENFEEfs/other/1576654658451/apptrana-protection-waf-rules-coverage.pdf
3. Proactiveness, Intelligence, and Intuitiveness
An intelligent, proactive, and intuitive WAF like Indusface WAF continuously monitors traffic, acts instantaneously, and can decide whether a request needs to be allowed, blocked, challenged, or flagged. Indusface WAF is also endowed with the Global Threat Intelligence Database to ensure that the WAF learns from attack patterns from across the globe and acts with urgency to uphold the security posture of the website/ web application.
4. Managed by certified security experts
Machines have their limitations when it comes to cybersecurity. For heightened web security, the intelligence and creative problem-solving skills of certified security professionals are indispensable whether it is to understand and alleviate business logic flaws or analyze traffic patterns/ real-time security data to prevent DDoS attacks or to quickly block zero-day threats. The experts custom-build the rules with surgical accuracy based on a deep understanding of the business context and risk exposure.
If you choose a managed, intelligent, comprehensive, and proactive web application firewall like the one AppTrana offers, you can ensure the highest standards of safety for your website/ web application and focus on your core business.


 January 7, 2020
January 7, 2020