What is OSI Model?
The OSI (Open Systems Interconnection) model is a conceptual framework for understanding and standardizing how different networking protocols and technologies communicate with each other in a network.
Developed by the ISO (International Organization for Standardization) in 1984, it breaks down the complex process of network communication into seven distinct layers, with each layer serving a specific function.
The 7 Layers of the OSI Model
The OSI model divides networking into seven layers, each responsible for a particular part of the communication process. This modular approach helps troubleshoot issues and ensures that changes in one layer do not affect the others. Let’s dive into each layer to understand its purpose and how it contributes to seamless data transfer.
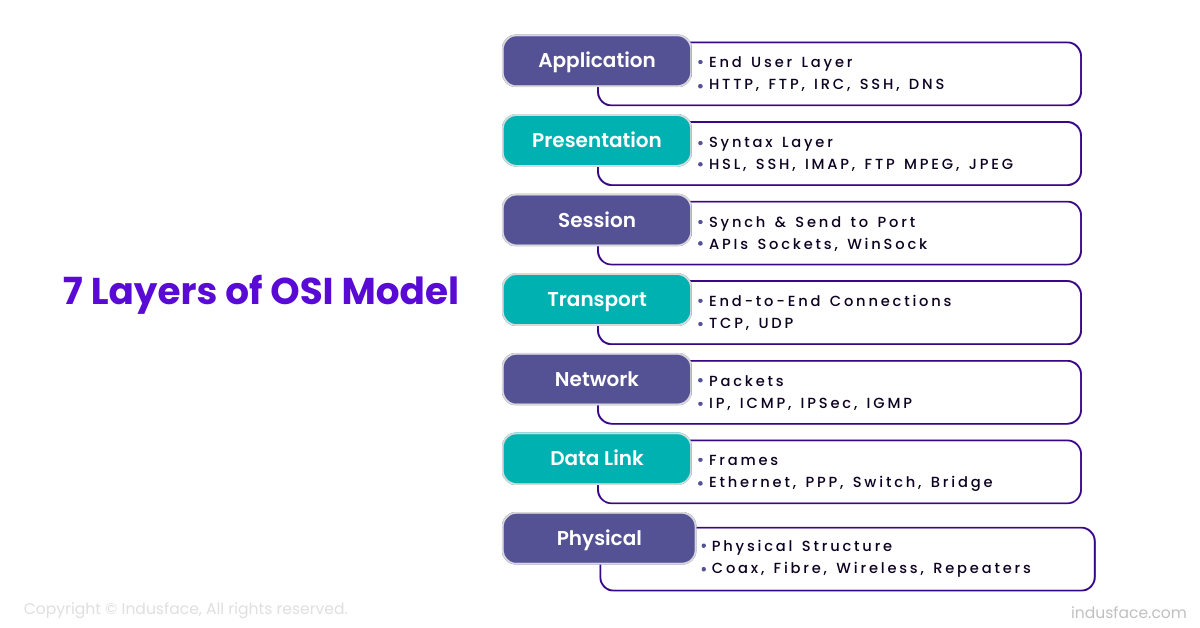
Physical Layer (Layer 1)
This is the lowest layer of the OSI model. On this layer, the raw bits are transmitted physically over copper cables, fiber optics, and wireless signals. Characteristics such as voltage levels, cable specifications, data rates, and physical connectors are defined on this layer.
Key responsibilities:
- Transmission and reception of unstructured raw data.
- Managing the hardware aspects like signal transmission, voltage levels, and data rates.
- Ensuring synchronization between the sender and receiver.
- Converting digital data into signals for transmission (and vice versa).
Example: The Ethernet cable that connects your device to the internet or the fiber optic cables used by ISPs operate at the physical layer.
Data Link Layer (Layer 2)
This OSI layer establishes a reliable link between two directly connected nodes over a physical medium. It packages raw bits from the physical layer into frames (structured data units) and handles error detection and correction.
The data link layer has two sublayers:
1. Logical Link Control (LLC) Sub-layer – This sub-layer handles error detection and flow control between two communicating devices. It also identifies network layer protocols and provides an interface for them to interact with the data link layer.
2. Media Access Control (MAC) Sub-layer – The MAC sub-layer controls access to the physical transmission medium. It is responsible for addressing the hardware on the network using MAC addresses and determining when devices can send data over the network.
Key responsibilities:
- Frame sequencing – Grouping bits into frames for transmission.
- Error detection and correction using checksums and parity bits.
- Flow control to manage the rate of data transfer.
Network Layer (Layer 3)
The network layer routes data packets between different networks. It addresses, forwards, and routes data across various network segments. The IP (Internet Protocol) operates at this layer.
Key responsibilities:
- Routing: Determining the best path for data to travel across multiple networks.
- Logical addressing: Assigning IP addresses to ensure data is sent to the correct destination.
- Packet forwarding: Moving packets from one network to another.
- Fragmentation and reassembly of data for transmission across different types of networks.
Example: Routers operate at the Network Layer, using IP addresses to route packets from the source to the destination across multiple networks.
Transport Layer (Layer 4)
The OSI layer 4 is responsible for end-to-end communication between devices. It manages:
Segmentation: This is the process where a large packet of data (files, videos, etc.) are divided into smaller segments before transmitting them on a network. This is done to ensure that the segments fall within the maximum payload size specified by the network.
Reassembly: This is the reverse process where the multiple segments are joined at the receiver’s end so that the files are received in full.
Flow control: This is the process of managing the speed at which data is sent to make sure that the receiver is not overwhelmed, which could lead to data loss due to congestion.
Error detection: These are techniques that are used to identify whether data transmitted over the network has been corrupted during transmission.
Correction: This is the next step after error detection. Once errors are detected, the transport layer attempts to fix the errors by asking for retransmission of corrupted packets.
The Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) are examples of transport layer protocols.
Session Layer (Layer 5)
The session layer establishes, maintains, and terminates communication sessions between two devices. It manages:
Dialogue control: This manages the communication process between two applications.
It ensures that data exchange follows a predefined structure or protocol to prevent conflicts, such as two applications trying to send data simultaneously or out of order.
Synchronization: This coordinates the timing and sequencing of data exchange between two applications. It ensures that data is sent and received in a manner that both sender and receiver can understand and interpret correctly. These mechanisms help avoid issues such as data arriving too quickly for the receiver to process.
In summary, the session layer ensures that data is sent, received, and processed in a way that maintains meaningful communication and prevents conflicts or confusion during a session.
Example: When you engage in an online video conference, the Session Layer ensures that the video and audio streams remain synchronized and properly managed throughout the call.
Presentation Layer (Layer 6)
The Presentation Layer is responsible for translating data between the application layer and the network format.
This OSI layer handles data translation, encryption, compression, and other transformations necessary to ensure that the application layer of another system can understand data from the application layer of one system. It ensures that data is presented in a consistent format across different devices and platforms.
Example: Secure Sockets Layer (SSL) encryption, which secures data communication between a web browser and server, operates at the Presentation Layer.
Application Layer (Layer 7)
The application layer is the topmost layer of the OSI model and is the one closest to the end-user. It provides network services directly to applications. Examples of OSI layer 7 protocols include HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), SMTP (Simple Mail Transfer Protocol), and DNS (Domain Name System).
Example: When you browse a website using HTTP/HTTPS, or send an email using SMTP, you’re interacting with the Application Layer.
OSI Layer 7 (Application Layer) is also a frequent target, where attacks like HTTP floods mimic legitimate user traffic, overloading web servers by generating a high volume of requests. DDoS mitigation techniques, such as rate limiting, deep packet inspection, and traffic filtering helps to counter DDoS attacks effectively. Learn more about the application layer DDoS attacks.
How Data Flows Through the OSI Layers?
To explain this in detail, let’s take the example of a video call on WhatsApp between Mike and Sara.
Application Layer (Layer 7)
Mike’s WhatsApp initiates the call. It prepares the audio and video data streams for transmission.
Presentation Layer (Layer 6)
The presentation layer is responsible for data translation and encryption. WhatsApp encrypts the audio and video data streams using a secure encryption algorithm.
Encrypted Audio and Video Streams
Session Layer (Layer 5)
The session layer of the OSI model plays a significant role in managing the video conference session.
- Session establishment: Mike’s application initiates a session request to Sara’s application. It includes session negotiation details, such as supported encryption algorithms and session parameters.
Session Layer Data:
Session Request
Supported Encryption: AES - 256
Session ID: 99876432
Encrypted Audio and Video Streams
- Session confirmation: Sara’s application receives the session request, negotiates session parameters, and confirms the session.
Session Layer Data:
Session Confirmation
Supported Encryption: AES - 256
Session ID: 99876432
During the session, the session layer manages aspects like session timeouts, retransmissions, and session termination.
Transport Layer (Layer 4)
The transport layer adds headers for data segmentation and error checking.
Data is divided into smaller packets, each carrying a portion of the encrypted audio and video streams.
Transport Layer Headers:
Source Port: 12345
Destination Port: 54321
Sequence Numbers
Network Layer (Layer 3)
The network layer handles routing and addressing.
Network Layer Headers:
Source IP: 192.168.1.2 (Mike's computer)
Destination IP: 192.168.1.3 (Sara's computer)
Data Link Layer (Layer 2)
The data link layer adds MAC addresses for local network communication.
Link Layer Frames:
Source MAC: AA:BB:CC:DD:EE:FF (Mike's computer)
Destination MAC: 11:22:33:44:55:66 (Sara's computer)
Physical Layer (Layer 1)
The entire frame, including data link layer frames, is converted into signals suitable for transmission over the physical medium.
The encrypted audio and video streams and session management data are transmitted securely from Mike’s computer to Sara’s computer.
Sara’s computer receives the packets, and as they traverse the OSI model in reverse, the layers handle decryption, reassembly, and session management to ensure a secure and reliable video conference call.
Comparison Between OSI and TCP IP Model
The OSI and TCP/IP models differ significantly in structure and purpose. The 7 layers of OSI model provides a detailed framework with distinct functionalities, including separate layers for session management and data formatting.
In contrast, the TCP/IP model consists of four layers: Network Interface (Link), Internet, Transport, and Application, which combine several layers into broader categories for practical implementation. Additionally, the OSI model supports both connection-oriented and connectionless services in its Transport Layer, whereas the TCP/IP model primarily defines TCP and UDP services. Ultimately, the OSI layers offers greater flexibility and a comprehensive understanding of networking, while the TCP/IP model emphasizes streamlined deployment and integration in practical networking scenarios.
What are the Benefits of OSI Model ?
The OSI model layers provides several key benefits, helping standardize communication between different networking systems.
Standardization: The OSI model establishes a universal framework for network communication, ensuring that diverse hardware and software systems can work together seamlessly, promoting interoperability across different vendors and technologies.
Modular Design: By dividing the networking process into seven distinct layers, the OSI model allows each layer to be developed and improved independently. This modularity enables easier updates and enhancements without impacting other layers.
Troubleshooting: The layered structure simplifies network diagnostics. When issues arise, administrators can isolate problems by examining specific layers, such as identifying routing errors at the Network Layer or session issues at the Session Layer.
Interoperability: The OSI model layers facilitates communication between various network devices and applications by standardizing protocols at each layer, allowing for seamless data exchange across heterogeneous systems and networks.
Scalability: Each layer can evolve independently, making it easier to scale networks. Organizations can introduce new technologies at one layer (e.g., upgrading physical media) without necessitating a complete system overhaul.
Layer Independence: The model allows different protocols to operate at each layer. This flexibility means that organizations can choose the most suitable protocols for their needs, adapting to technological advancements and specific use cases.



