What is Vulnerability Testing? Benefits, Tools, and Process
What is Vulnerability Testing?
Vulnerability testing is a systematic process of identifying, evaluating, and assessing weaknesses, flaws, or vulnerabilities in computer systems, networks, applications, or other digital assets.
Vulnerability testing aims to discover security weaknesses that malicious actors could exploit proactively and provides actionable insights for remediation.
Various tools and techniques are employed during vulnerability testing to scan and analyze the target system or application for potential vulnerabilities. This may include automated scans, manual penetration testing, code reviews, and configuration analysis.
The goal is to uncover flaws such as:
- Unpatched operating systems or applications
- Insecure configurations (e.g., default passwords, unnecessary services)
- Weak or outdated encryption protocols
- Vulnerable third-party libraries
- Excessive permissions or misconfigured access controls
- Web application vulnerabilities like SQL injection, XSS, and CSRF
Unlike penetration testing, which tries to exploit vulnerabilities to assess real-world impact, vulnerability testing focuses on identifying and documenting potential weaknesses.
Why is Vulnerability Testing Critical?
- The numbers don’t lie: The 2025 Verizon DBIR reported a 34% increase in breaches caused by exploited vulnerabilities compared to the previous year.
- New vulnerabilities emerge constantly: The National Vulnerability Database (NVD) sees over 133 new vulnerabilities disclosed every day, creating a rapidly expanding attack surface.
- Most breaches involve known issues: Over 60% of breaches exploit vulnerabilities that were known but left unpatched.
- Compliance requirements: Standards like PCI DSS, HIPAA, ISO 27001, and GDPR require regular vulnerability testing.
- Cyber insurance mandates: Many insurers require proof of vulnerability testing as a prerequisite for coverage.
Benefits of Vulnerability Testing
Vulnerability testing is not just a checkbox for compliance, it is a proactive strategy that strengthens your entire security posture. Here is a deep dive into the key benefits you gain when you make vulnerability testing an ongoing part of your security program:
Reduce the Risk of Breaches
The biggest benefit of vulnerability testing is that it helps you find and fix security gaps before attackers can exploit them. Regular testing strengthens your networks, applications, databases, and cloud environments, making it much harder for attackers to break in and reducing the chances of a successful breach.
Prioritize Remediation Based on Real Risk
Vulnerability testing provides context about the severity and exploitability of each vulnerability. This allows you to prioritize which issues to fix first, focusing resources on vulnerabilities that pose the highest risk to your organization instead of wasting time on low-impact findings.
Indusface WAS enables instant patching of identified vulnerabilities beyond prioritization, using SwyftComply to virtually patch all open vulnerabilities immediately while your teams work on permanent fixes.
Support Compliance and Regulatory Requirements
Vulnerability testing is essential for meeting the requirements of standards like PCI DSS, HIPAA, ISO 27001, and FISMA, which mandate regular vulnerability assessments to protect sensitive data and systems.
For instance, PCI DSS 4.0’s Requirement 11.3.1 calls for quarterly scans, and HIPAA’s Security Rule obligates covered entities to assess technical vulnerabilities in systems storing ePHI. Performing and documenting vulnerability testing demonstrates compliance, helps avoid penalties, and provides audit-ready proof of your security efforts making it a foundational requirement rather than a mere recommendation.
Improve Patch Management Efficiency
Vulnerability testing complements patch management by identifying outdated or unpatched software across your environment. It helps you measure metrics like Mean Time to Patch (MTTP), which is the average time taken to deploy patches after a vulnerability is discovered, and ensures patches are applied effectively, reducing the attack surface and avoiding known exploits.
Enhance Incident Response Capabilities
When vulnerabilities are detected and tracked proactively, your security and IT teams can move faster during incidents. Knowing your environment’s weaknesses enables you to respond decisively to exploit attempts, limit lateral movement, and reduce the blast radius of a potential breach.
Provide Visibility Across the Entire Attack Surface
Modern organizations have sprawling IT environments: on-premises servers, cloud workloads, mobile apps, IoT devices, and third-party integrations. Automated vulnerability assessment tools like Indusface WAS include built-in asset discovery to identify and catalog all systems, ensuring you do not miss unmanaged or forgotten assets that could expose your organization to risk.
Enable Data-Driven Security Decisions
Vulnerability testing provides valuable metrics such as Total Vulnerabilities Detected, Vulnerability Aging, and Remediation Throughput. These metrics allow you to track risk reduction over time, prove the effectiveness of your security investments, and justify additional budget or staffing to executives.
For key metrics and KPIs, see our detailed Vulnerability Management Metrics blog.
Reduce Downtime and Costs Associated with Breaches
Fixing vulnerabilities proactively is far less costly than dealing with the fallout of a successful attack. The fallout can include recovery efforts, regulatory fines, legal fees, customer notifications, and reputational damage. Vulnerability testing helps prevent these costs by stopping breaches before they occur.
Foster a Culture of Security
Regular vulnerability testing sends a clear message across your organization: security is a priority. It encourages developers, sysadmins, and business leaders to bake security into their processes, resulting in a more resilient security culture.
Boost Customer and Partner Confidence
Customers, investors, and partners want assurance that you are serious about security. Demonstrating a mature vulnerability testing program shows you are actively working to protect sensitive data, increasing trust and differentiating your organization in the market. Providing a zero vulnerability report as evidence of clean scans can further strengthen confidence by proving that you have proactively identified and remediated vulnerabilities to keep systems secure.
How Does Vulnerability Testing Work?
Vulnerability testing involves various methods, and a widespread method involves deploying automated vulnerability scanning tools.
The automated scanning tool thoroughly examines your technology, offering a detailed report upon completion. This report identifies existing issues and proposes recommended actions to address and eliminate potential threats.
These tools leverage extensive databases containing information about known vulnerabilities to pinpoint potential weaknesses across your technological landscape, spanning networks, applications, containers, systems, and data.
More sophisticated tools go above basic scanning functionalities, allowing seamless integration of vulnerability scanning data into an SIEM system. This integration enhances the overall threat analytics capabilities.
5 Steps in the Vulnerability Testing Process
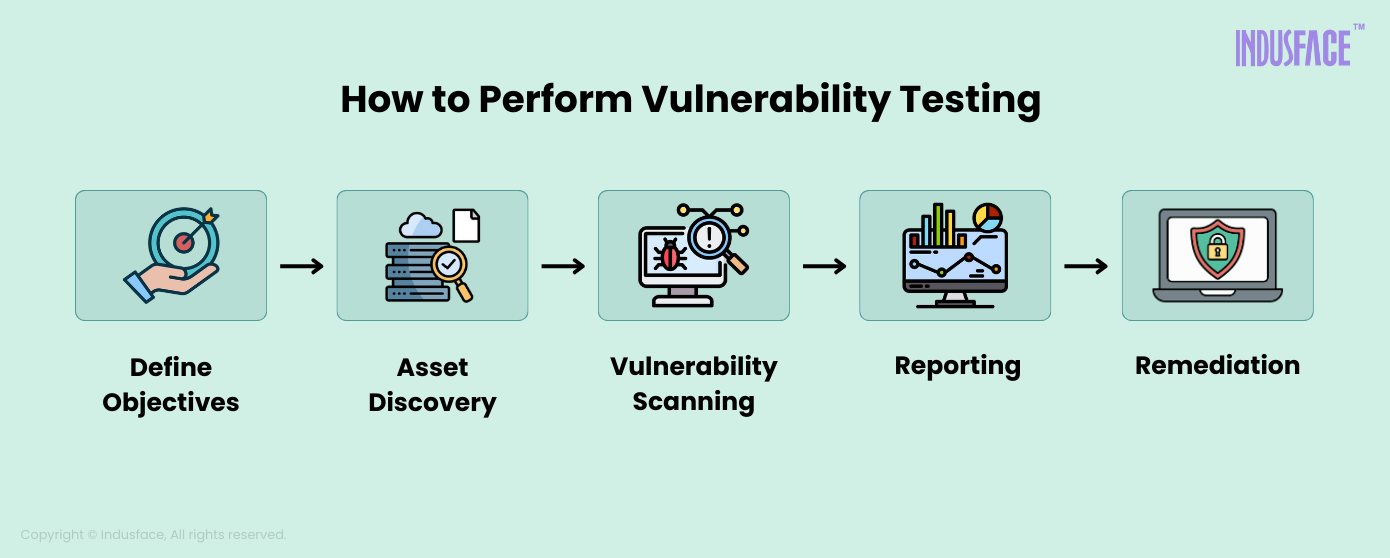
1. Define Objectives
The first step is to outline the goals of vulnerability testing clearly. This involves determining the primary objectives, such as discovering vulnerabilities, assessing risk levels, improving overall security, and validating existing security controls. Establishing these goals helps in planning and executing the testing process effectively.
2. Asset Discovery
Comprehensive testing requires gathering detailed information about the specific application or application cluster.
Figuring out what you want to scan may sound easy, but many organizations struggle with a common cybersecurity issue: the lack of visibility into their digital assets. The good news is that automation can make the discovery part easier.
3. Vulnerability Scanning
Vulnerability scanners are employed to scan the IT environment and detect security vulnerabilities. While automated tools are effective, more intricate flaws may require manual penetration testing for a thorough evaluation.
4. Reporting
Upon completion of the testing phase, the scanner adeptly compiles a comprehensive report encapsulating all identified vulnerabilities. The scanner then conducts an in-depth analysis of these vulnerabilities, unraveling their root causes and potential impact.
Utilizing a severity-based ranking system, the scanner categorizes the flaws, providing a quantified understanding of the threats akin to its systematic approach. This facilitates the prioritization of issues based on urgency and associated risk, aligning with the scanner’s efficient reporting mechanism.
Want to derive actionable decisions from your reports? Read more about vulnerability assessment reports.
5. Remediation
With the vulnerabilities identified and ranked, the next step involves vulnerability remediation. Prioritize and patch the most critical threats first. Regular scheduling of security and vulnerability testing is essential to track the status of your security posture over time.
Indusface WAS provides remediation guidelines and follow-up testing to ensure all identified issues are resolved effectively.
Prepare for your vulnerability assessment process from our blog on the vulnerability assessment checklist [Free Excel File].
7 Best Practices for Vulnerability Testing
To stay informed about changes in your software, the addition of new systems to your network, and to regularly discover new vulnerabilities, follow these best practices in vulnerability testing:
1. Regular and Systematic Testing
Conduct vulnerability assessments regularly, as the digital environment is dynamic. Schedule systematic tests to adapt to changes in software, configurations, and emerging threats.
2. Thorough Information Gathering
Prioritize a detailed understanding of your digital landscape. Gather comprehensive information about applications, clusters, business logic, and privilege requirements. This forms the foundation for targeted and effective testing.
3. Utilize Automated Tools and Manual Testing
While automated vulnerability scanning is crucial in the assessment process, it represents just one facet of vulnerability management. Manual penetration testing is vital in uncovering diverse threats, including business logic vulnerabilities specific to your organization.
Indusface WAS goes a step further by including bundled penetration testing, which complements automated scanning by detecting complex logic vulnerabilities that automated tools might miss.
4. Stay Informed on Evolving Threat Landscapes
Keep abreast of the latest threats and techniques employed by cyber adversaries to ensure your vulnerability testing remains proactive and effective.
5. Test in Realistic Production-Like Environments
Conduct vulnerability testing in environments that closely emulate your production systems, providing a genuine assessment of potential vulnerabilities within your operational landscape.
6. Follow Data Protection and Privacy Measures
Integrate vulnerability testing best practices by prioritizing robust data protection and privacy considerations. Ensure compliance with regulations and safeguard sensitive data to uphold user privacy.
7. Virtual Patching as an Immediate Remediation
In instances where immediate resolution is challenging, deploy virtual patching through a WAF(WAAP). Virtual patching provides an instant and effective solution to mitigate vulnerabilities without directly altering the source code.
Tools for Vulnerability Testing
Vulnerability assessment tools can be categorized into different types based on their specific focus and capabilities. The most common types of vulnerbaility testing tools include:
Network Vulnerability Scanners
These tools specialize in scanning and assessing vulnerabilities present in network devices, such as routers, switches, firewalls, and servers. They identify open ports, outdated firmware, misconfigurations, and known vulnerabilities in network services.
Web Application Scanners
Web application scanners are designed to assess the security of web applications and websites. They identify vulnerabilities like SQL injection, cross-site scripting (XSS), insecure authentication mechanisms, and other web-specific vulnerabilities.
Database Scanners
These tools focus on assessing the security of databases by scanning for vulnerabilities in database management systems (DBMS). They identify misconfigurations, weak authentication mechanisms, and vulnerabilities in database systems.
Wireless Network Scanners
Wireless network scanners are specifically designed to assess the security of wireless networks. They identify vulnerabilities in wireless access points, encryption weaknesses, and other wireless network-related risks.
Source Code Analysis Tools
These tools analyze the source code of applications to identify potential security flaws and vulnerabilities. They help identify insecure coding practices, buffer overflows, injection vulnerabilities, and other code-related weaknesses.
Configuration Auditing Tools
Auditing tools assess the security configurations of systems, devices, and applications. They check for compliance with security best practices, industry standards, and organizational security policies.
Cloud-Based Vulnerability Management Platforms
Cloud-based vulnerability management platforms provide centralized scanning and management of vulnerabilities across multiple systems, networks, and cloud environments. They offer a wide range of vulnerability scanning and reporting capabilities.
Exploitation Frameworks
Exploitation frameworks like Metasploit focus on simulating real-world attacks and exploiting known vulnerabilities. They can be used for offensive security testing and defensive purposes.
Some vulnerability assessment tools may have overlapping functionalities and fall into multiple categories. You can use different tools to cover various vulnerability assessment and management aspects based on your specific requirements and environments.
Indusface WAS provides continuous and comprehensive web application dynamic security testing, which includes daily or on-demand automated scanning with penetration testing for mission-critical applications.
Start your free trial today to secure your applications now.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 June 27, 2025
June 27, 2025






