How to Check Safety of Website?
Securing websites and periodic testing are mandatory for online businesses.
Today, data breaches bring catastrophic repercussions. Websites and applications are an integral part of any business. This is where ensuring your website is safe becomes very important.
According to the 2016 Ponemon Cost of Data Breach Study, the average consolidated total cost of a data breach jumped from $3.8 million to $4 million.
But what are the chances your organization will actually be affected? Reporting from CIO found that mobile security breaches have affected over 68% of global organizations over the span of 12 months. DDoS attacks alone strike 84% of companies every 12 months, according to a Neustar survey of 1,000 enterprise firms.
Staying on top of modern security risks goes beyond reading up on the latest malware entering through mobile phones, tablets, and vulnerable servers. There are other causes of data theft and loss you’re probably overlooking.
| What | Why |
| Step 1. Website Reputation Check | Reputation Check |
| Step 2. Automatic Safety Check | To find security issues |
| Step 3. Get Your Tech Right | To ensure patches are updated |
| Step 4. Identify Major Security Risks | To set priorities |
| Step 5. Prepare Documentation | For a uniform view |
| Step 6. Conduct Training | To communicate the risks |
| Step 7. Reward Employee Involvement | For proactive actions |
Here are 7 Steps to Check Website Safety
Step 1. Website Reputation check
The first step is to check the reputation of your website and is it rated as safe already. If it is not it is catastrophic and you are already impacted.
Step 2. Automatic Safety Check
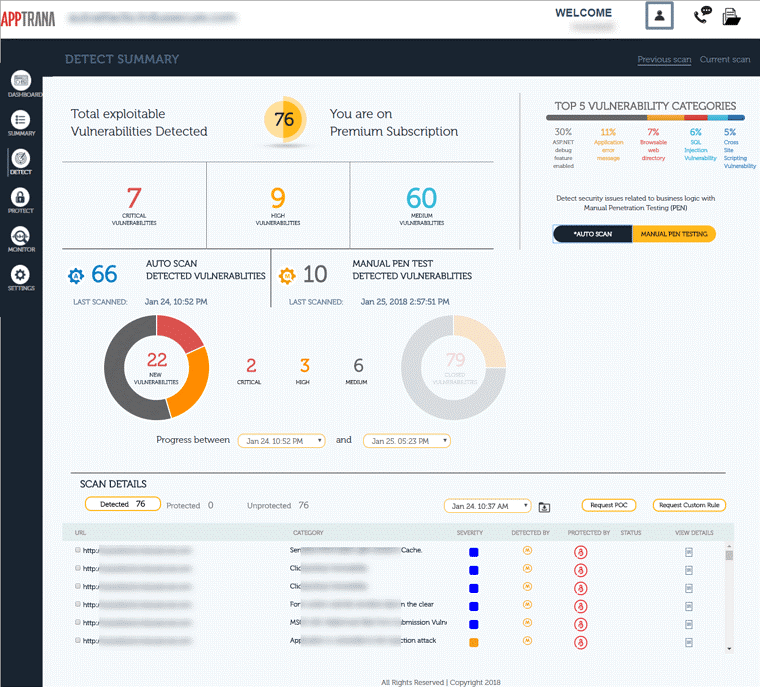
The next step towards ensuring a safe and secure website is to schedule frequent scans. A company employee simply cannot test the website every day looking for security loopholes and malware. A thorough web scanning such as AppTrana ensures automatic scanning and reporting.
It looks for frequently exploited vulnerabilities such as OWASP top 10 and SANS 25. Although we are also providing you other steps to ensure that the development and production cycles are clean, this is the step to ensure that you stay aware of the risks.
Step 3. Get Your Safety Tech Right
Obviously, you can’t build a culture of website security if your organization and systems aren’t actually secure. Start by taking inventory of which devices, both personal and professional, are being used to access sensitive information. Remember that access can happen in the office, as well as at an employee’s home, an airport, or a coffee shop.
Employees using their personal smartphones for pleasure shouldn’t have access to sensitive files in the cloud. Your team also shouldn’t readily connect to free WiFi from their work computers where data can easily be compromised.
If you offer up devices for employee use, choose models that are already encrypted. According to the Wall Street Journal, about 10% of the world’s Androids are encrypted. Meanwhile, Apple enjoys a reputation for its encrypted devices and even made a few enemies in law enforcement when it refused to create a backdoor method for police to access an encrypted iPhone belonging to the San Bernardino shooter.
Beyond encryption, your company should also use mobile device management (MDM) to give IT personnel a way to revoke access or wipe a device to factory settings if lost or stolen. MDM can also keep tabs on how employees are using data, and give insight into their behavior towards security.
There’s also a way to control the geography of where employees use work-sponsored devices with geofencing tools. Geofencing sends business owners real-time alerts when devices are taken outside of specific boundaries that could be miles away, and also revoke access to data and files when a device has strayed too far.
These rules and consequences should also be outlined in your BYOD and website security policy so employees know when their devices will be accessed and for what reasons. Your employees need to know your expectations and the consequences, but this also helps keep your team focused on security as an everyday part of the work culture.
Put Your House on Lockdown
Secure your in-house systems with web application scanning tools and application firewalls to help prevent attacks without obstructing legitimate online traffic.
SSL Certificates should also be used to secure customer communications and protect their transactions when using credit cards and supplying personal information.
Scrutinize your SDLC
Security starts from the moment your company commits to building its own website or digital resource. Your team should always rely on the Security Development Lifecycle (SDLC) to adhere to best security practices. According to Microsoft, the SDLC process helps developers build more secure software and address security compliance requirements, all while reducing development costs.
Microsoft identifies 17 steps to the SDLC process, starting with Core Security Training and ending with Threat Modeling. Each step focuses on how to integrate security into every phase of the creation, deployment, and post-release process. For example, during the implementation process, SDLC practices require using approved tools and depreciating unsafe functions.
It should be noted that SDLC is not restricted to up to the point of deployment. For SaaS products or web applications, continuous security assessment – even after deployment in production – via application security is a must.
Why? As the application is still running and interacting with many moving parts (the web server and application server it runs on, the infrastructure it is hosted on, the other services it interacts with, etc.) continuous assessment and immediate protection is imperative during and beyond the SDLC – even when the software is live and in use.
Step 4. Identify Your Biggest Security Risks
Where are the biggest website risks and vulnerabilities in your company? It may not have anything to do with BYOD or unsecured backups. Instead, you could have a problem with your actual employees.
Require every new employee to undergo a screening and background check. Create an onboarding system that emphasizes your company’s security protocols and standards in their role. Some red flags are easy enough to spot, like a candidate with a history of excessive job-hopping or a criminal past, or an employee who won’t commit to set their devices to ask before connecting to free wireless signals.
But even once you’ve substantiated that new hires are sound, you could still have a bigger problem on your hands: your employees’ online passwords may be inviting hackers to infiltrate your servers and steal sensitive data.
Password security
An infographic published on Entrepreneur found that 47% of people use passwords that are at least 5 years old, and 21% use passwords that are over 10 years old.
Even if your company implements a password policy that requires employees to regularly update passwords for accounts and devices, that doesn’t mean employees aren’t duplicating their use: 73% of online accounts are guarded by duplicate passwords. That creates a domino effect that makes it easy for hackers to access accounts and sensitive data. Create a policy to regularly update passwords and require system-generated passwords to boost their strength.
And if by some chance you’re not doing so already, make sure you are automatically blocking former employees’ access to your systems and data. Outdated credentials and access should be revoked the moment an employee leaves your company. Otherwise, they have free reign to continue accessing all of your company’s data, or the passwords on their old accounts will remain unchanged for so long that hackers will eventually catch up and find easy access.
Web Application Security
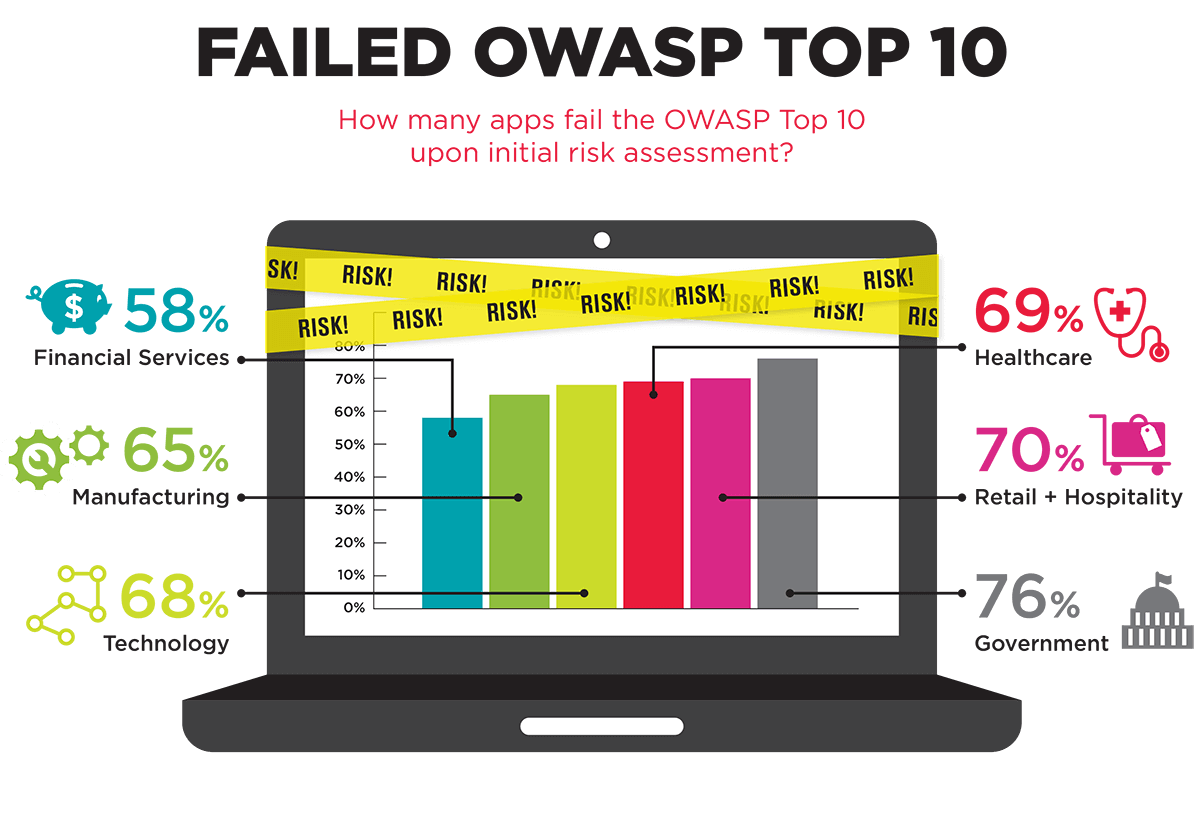
Take a look at how your team is accessing personal and professional apps, and how they obtain and download them to their devices. Require that all apps be downloaded from a qualified source like Google Play or the Apple App Store, and research the developer’s reputation.
For added insurance, consider creating a pre-approval process before any apps can be used on company devices. Give employees a tutorial on setting up their smartphones and devices to prompt their users for permissions before downloading an app or allowing them to access any data.
Remotely-accessed data
Accessing data remotely can inadvertently open back doors with open WiFi, but can also lead to malware attacks from risky behavior. Your team may think checking email is no big deal, but your employees could be doing much more than that, and on devices that are far from secure.
For example, a study from Cisco found that half of those polled said they use their own personal devices to access corporate resources. Yet only half of the devices were actually protected by antivirus or security software. The same study found employees used company devices for online shopping and accessing third-party apps.
Free WiFi may be a blessing for employees on the go and working in the field, but can be a nightmare for malicious data breaches. Educate employees on a hacker’s ability to intercept data transmission from unsecured WiFi. Use password-protected wireless signals, and keep sensitive data and communication off of vulnerable smartphones that openly connect to WiFi.
Employees need education and information on when, how, and why to use WiFi, and what security tools are required, before engaging in any activity involving remote access.
Step 5. Prepare Documentation
Handing over a thick manual with a less-than-engaging security policy might get a glance, but it won’t be digested by employees or motivate them to act. Policies stuffed with information with plenty of technical jargon, but no context will lose your employees. Instead, focus on offering segmented and customized documentation and training for your team.
Skip One-Size-Fits-All Policies
There’s no need for a one-size-fits-all policy for security for your entire company. One employee may process and retain information best with videos, while another may want a roundtable discussion on security issues and how to handle them.
Get inspired by companies who take a more holistic approach to security, and study how they create a culture around it. For example, Uber creates security programs for its employees catered to different regions, departments, and roles, to translate the idea that security is part of the company culture.
Small business owners can do the same by catering documentation and training specific to that employee’s needs and everyday work responsibilities. After all, the security policies for the sales team with access to client data will look different than for the marketing department using online social media apps to schedule posts.
Step 6. Conduct Training
Security isn’t just for IT departments or executive assistants with a hand in sensitive data. Security is for everyone to embrace and incorporate into their day-to-day work life. Recruit top management to get on board with security, and set the example for taking ongoing security training as seriously as a performance review.
Think back to past security issues, like an employee who accidentally downloaded malware onto their work device.
Next, walk through the process of how that security breach even happened in the first place, and run phishing and spear-phishing simulations. Collect feedback and data to see how each department did on the simulation. You could also consider offering prizes and a monthly drawing for every suspicious email an employee reports. The incentive keeps minds hyper-focused on security and constantly monitoring for malicious activity.
To make training as fun and engaging as possible, skip the lecture and turn it into a game instead. Divide employees into teams from various departments and run a trivia contest. Quiz teams on different security issues, technology, and malicious activity like ransomware. Your employees will have fun and are more likely to remember the information that they would be skimming through a security manual. The trivia dynamic can also help build trust and camaraderie among teammates and give your culture of security an interactive boost.
Step 7. Reward Employee Involvement
Relying on fear-mongering and shaming during security training won’t get you very far. Employees are likely to view security as a negative and stressful process, instead of a part of business life.
No matter how passionate your employees care about security, they’re much more likely to be motivated by rewards and incentives than manual and ongoing security training. Bonuses are one way to do that, but employees are likely to respond to perks like a lunch meeting with executives or a bonus day off.
Make the incentives for following security protocols public with ongoing reminders in meetings and with break room conversation. Publicly acknowledge and thank employees for their commitment to security to foster a positive and proactive mindset throughout your business.
However, that doesn’t mean your team shouldn’t know the risks. Explain what’s at stake when engaging in non-compliant behavior, from client security breaches to data loss, and the costs involved. Security should be viewed as bringing value to the company, and as integral to the company’s success as fostering sales leads and customer service.
Improving Security is an Ongoing Process
At the end of the day, your culture of security is all about personal accountability and team momentum. Your employees won’t follow protocols if you’re not following through with the policy yourself. They also won’t take the initiative to master security if there’s no incentive and momentum. Hold monthly or quarterly security meetings and stimulations to keep employees’ minds on security. Make improving security an ongoing process that’s as non-negotiable as your sales goals.
Do you have a culture of security in your organization? How did you create it, and how has it impacted the way you conduct business? Let us know by leaving a comment below.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 April 11, 2018
April 11, 2018





