ScreenConnect Authentication Bypass (CVE-2024-1709 & CVE-2024-1708)
ConnectWise ScreenConnect, a widely used remote desktop product, has recently been found vulnerable to two critical security flaws, assigned CVE numbers CVE-2024-1709 and CVE-2024-1708.
These vulnerabilities, if exploited, can lead to remote code execution, potentially compromising sensitive data and critical systems.
What’s more alarming is that reports are indicating active exploitation of these vulnerabilities in the wild.
CVE-2024-1709 – Authentication Bypass
Severity: Critical
CVSSv3.x: Base Score: 10.0 CRITICAL
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
Exploit available in public: Yes
Exploit complexity: Low
The first vulnerability, CVE-2024-1709, exposes an authentication bypass flaw in ScreenConnect versions 23.9.7 and earlier. This oversight in the authentication process allows unauthorized access via various paths, including the setup wizard, posing a severe risk to system security. Check out the impacts of broken authentication vulnerability here.
The vulnerability shares similarities with recent flaws that enable attackers to reinitialize applications or create initial user’s post-setup.
CVE-2024-1708 – Path Traversal
Severity: HIGH
CVSSv3.x: Base Score: 8.4 HIGH
Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:H/I:H/A:H
Exploit available in public: Yes
Exploit complexity: Low
The second vulnerability, CVE-2024-1708, involves improper limitation of the pathname, commonly known as “path traversal,” which can be exploited through a type of attack called ZipSlip.
This vulnerability enables attackers to manipulate ZIP files to execute malicious code, potentially leading to remote code execution.
What makes these vulnerabilities particularly dangerous is the possibility of chaining them together.
Cybercriminals can exploit the authentication bypass vulnerability (CVE-2024-1709) to gain initial access and then leverage the path traversal vulnerability (CVE-2024-1708) to move laterally within the system, potentially compromising critical systems and data.
Prevention and Mitigation
ConnectWise has advised all customers using ScreenConnect versions 23.9.7 and earlier to upgrade to the patched version 23.9.8 or later immediately to mitigate the risks posed by these vulnerabilities.
Additionally, organizations are advised to follow their patching and testing guidelines to minimize operational impact.
AppTrana WAAP Threat Coverage
In response to these vulnerabilities, Indusface security experts have developed detection rules and filters to help identify and prevent potential exploitation. Customers using AppTrana WAAP can benefit from enhanced detection coverage against these vulnerabilities.
AppTrana’s vulnerability management system ranks critical vulnerabilities, enabling teams to tackle the most pressing threats first.
AppTrana’s built-in scanner finds and keeps track of system weaknesses, providing important information for targeted security actions and smooth patch management.
Indusface’s security team has made a special rule. This rule quickly finds and stops any misuse of ScreenConnect Authentication Bypass, without just relying on patches from the vendor.
| Rule ID | Name |
| 99969 | Auth bypass ScreenConnect CVE-2024-1708 and CVE-2024-1709 Policy |
AppTrana WAAP in action – A practical demo of a ScreenConnect Authentication Bypass
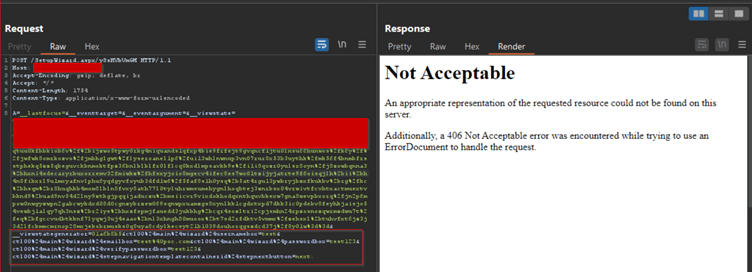
Malicious requests intercepted through Burp are swiftly thwarted by the WAAP, delivering a robust response with a 406-status code.
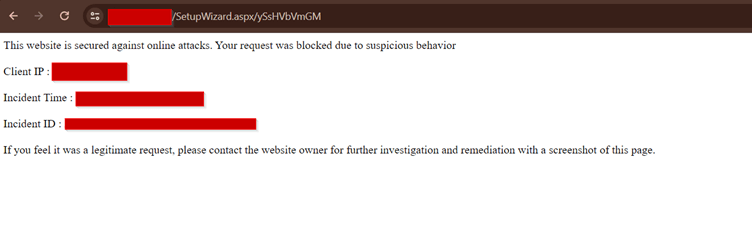
By promptly applying patches, leveraging detection rules, and following security best practices, organizations can strengthen their defense against emerging threats and protect their sensitive assets from exploitation.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 February 26, 2024
February 26, 2024



