Over 2 million Websites Vulnerable to XSS Exploit (CVE-2023-30777) in WordPress Plugin
A zero-day vulnerability, denoted by the CVE identifier CVE-2023-30777, exposes a dangerous reflected cross-site scripting (XSS) flaw.
This high-severity vulnerability has been discovered within the WordPress plugin (Advanced Custom Fields (ACF) and Advanced Custom Fields Pro). The CVE-2023-30777 exposes over 2 million installations to security risks, triggering widespread concern and anxiety among website owners and administrators.
This flaw poses a significant security risk, potentially allowing malicious actors to inject malicious scripts, execute arbitrary code and compromise vulnerable websites.
CVE-2023-30777 Exposed: An In-depth Analysis
The Advanced Custom Fields (ACF) plugin is a powerful tool for WordPress websites that allows users to create and manage custom fields easily. With ACF, website administrators can add custom fields to posts, pages, and custom post types, enhancing their websites’ flexibility and customization options. The Advanced Custom Fields plugin enables users to extend and enhance their websites’ functionality easily.
On May 2, 2023, a security researcher at Patchstack discovered the CVE-2023-30777. The identified security vulnerability could enable attackers to inject malicious scripts into a website, such as redirects, advertisements, and various HTML payloads. These injected scripts would execute when visitors access the site, potentially leading to harmful consequences.
An attacker can steal sensitive information or gain admin privileges on the WordPress site by tricking privileged users into visiting the crafted URL path.
The vulnerability was identified in the admin_body_class function handler. In the implementation of the admin_body_class, we can observe that the output value is not properly sanitized and directly constructed on the HTML page, leading to a potential XSS vulnerability.
$admin_body_classes = apply_filters( 'admin_body_class', '' );
$admin_body_classes = ltrim( $admin_body_classes . ' ' . $admin_body_class );
?>
<body class="wp-admin wp-core-ui no-js <?php echo $admin_body_classes; ?>">
<script type="text/javascript">
document.body.className = document.body.className.replace('no-js','js');
</script>
public function admin_body_class( $classes ) {
$classes .= " acf-admin-page acf-internal-post-type {$this->admin_body_class}";
if ( $this->view ) {
$classes .= " view-{$this->view}";
}
return $classes;
}
The code directly concatenates $this->view variable to $classes variable, which is returned as a class string. Attackers can fully control the $this->view variable from the current_screen function:
public function current_screen() {
if ( ! acf_is_screen( "edit-{$this->post_type}" ) ) {
return;
}
$this->view = isset( $_GET['post_status'] ) ? sanitize_text_field( $_GET['post_status'] ) : '';
Sanitization by sanitize_text_field function here is not enough to prevent XSS and could get bypassed easily with the below payload:
http://Wordpress-URL/wp-admin/edit.php?post_type=acf-field-group&post_status=xxxxxxx” onload=alert(document.domain) xxx=”
It has been discovered that CVE-2023-30777 poses a threat to all default installations or configurations of ACF. However, it is important to highlight that only logged-in users with plugin access can exploit this vulnerability.
The Severity and Impact of CVE-2023-30777
An unauthenticated attacker can easily exploit the vulnerability, and successful exploitation allows any user to steal sensitive information, escalate privilege and upload a web shell and gain command execution on the WordPress site.
Malicious actors are actively taking advantage of this vulnerability in ongoing attacks. Just 24 hours after releasing a proof-of-concept (PoC) exploit, malicious actors seized the opportunity to leverage this security flaw.
CVE-2023-30777 Vulnerability: Key Details
Exploit available in public: Yes
Exploit complexity: Low
The vendor has released the security patch for Advanced Custom Fields and Advanced Custom Fields Pro plugins. We strongly recommend that our customers running on (versions 6.1.5 and below) update their installations to version 6.1.6 as soon as possible.
Addressing XSS Flaw – CVE-2023-30777: AppTrana WAAP Coverage
AppTrana WAAP is a comprehensive web application and API security solution designed to identify and mitigate threats in real-time proactively. Protection against the XSS vulnerability is covered under our default CRS(Core Rule Set) and Premium rules.
The key features that enable AppTrana to block this vulnerability include the following:
Vulnerability Scanning and Assessment
AppTrana WAAP, bundled with a web application scanner, conducts regular vulnerability scans and assessments of your web applications. AppTrana identifies any instances of CVE-2023-30777 or other known vulnerabilities by thoroughly examining your application’s components and libraries. This proactive approach allows you to address potential weaknesses before attackers exploit them.
Web Application Firewall (WAF)
AppTrana employs a fully managed WAF that acts as a shield between your application and potential threats. By analyzing incoming traffic, the WAF filters out malicious requests attempting to exploit CVE-2023-30777. It uses rule-based detection and anomaly detection techniques to identify and block suspicious activities, effectively preventing unauthorized access and XSS attacks. Here is a detailed blog on common methods WAF uses to block malicious attacks.
Practical demonstration of AppTrana blocking the exploitation of an XSS attack:
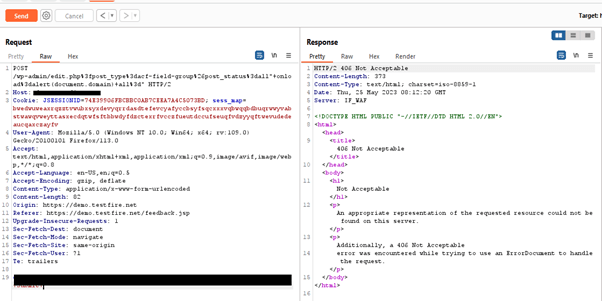
Image: Malicious request captured in burp
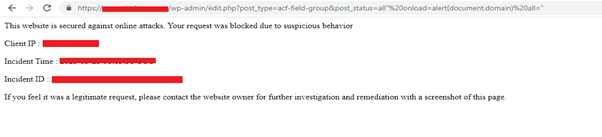
Image: Error message Displayed
Virtual Patching
Our security team implements virtual patching to block requests that exploit CVEs instantly. AppTrana offers pre-defined rules specifically designed to cover a wide range of CVEs in a default list.
By leveraging custom rule sets, you can rapidly respond to unpatched XSS vulnerabilities or newly exposed vulnerabilities resulting from application modifications.
Regular Updates
AppTrana ensures its security features are regularly updated with the latest threat intelligence to stay ahead of emerging threats. This includes timely patches and fixes for vulnerabilities such as CVE-2023-30777. By keeping your application security up to date, AppTrana minimizes the risk of exploitation and helps maintain a strong defense against evolving threats.
Zero False Positives
AppTrana takes an advanced approach to block, enhancing detection accuracy by employing a threshold-based methodology that separates blocking decisions from initial detections.
Rather than instantly blocking requests that match a regular expression (regex), AppTrana utilizes anomaly data from the request and response to make informed blocking decisions. This results in precise detections and offers a comprehensive context for different types of attacks.
With AppTrana WAAP, you can attain more precise and comprehensive blocking coverage for the OWASP Top 10 vulnerabilities and advanced threats by utilizing a blend of default detections and rules functionality.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 June 2, 2023
June 2, 2023



