How Do You Maintain Secure Remote Working?
Remote work has significantly changed how employers hire and manage employees. Research shows the remote trend is only rising. 58% of US workers have the option to work remotely.
More companies are leveraging talent across the U.S. and the world, making their companies stronger and more diverse.
Sean O’Brien of PGi told CIO in an interview,
“To think that a company can only be successful by drawing on a pool of talent that’s geographically local is just not accurate — it’s almost obsolete.”
Attracting top talent through remote work can revolutionize your business. However, it also leaves your sensitive data and assets vulnerable to hackers.
A report from Verizon revealed that 79% of organizations agreed remote working had negatively impacted their cybersecurity.
That means you must be prepared to address remote work security risks. We have put together this blog to help you secure remote working.
Cybercrime – The Risks of Remote Working
Although remote working has many advantages for enterprises, it comes with a cost:
- The average data breach cost increased by over 1 million when remote workers are involved – IBM Cost of a Data Breach report.
Another survey from Tenable highlights 80% of businesses are more prone to security breaches of remote working. Three primary factors drove it:
- The growth of the software supply chain (remote access tools)
- Migration to the cloud – cloud services and apps
- Lack of visibility into remote employee behaviors – BYOD policy
Cyber risks have always been a concern for all organizations. However, this has been intensified through poor remote work practices like insecure personnel networks, poor IT Support, lack of employee training, and more.
Here are the biggest cybersecurity concerns with remote work – according to Malwarebytes.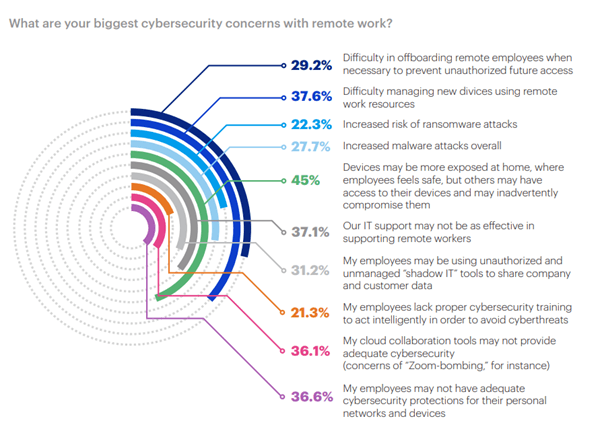
These sobering statistics just scratch the surface of the cybersecurity risks of working from home.
8 Best Practices for Secure Remote Working
1. Create Strong Authentication
Not sure where to start? It starts with ensuring you have strong authentication.
It ensures accurate identification before a worker can access corporate data and assets. You should be worried about access to data for the right person.
It starts by identifying the remote worker to be given access to the data. From this, you can build audit trails of the actions against the identity.
2. Monitor Remote Workers, Remotely

Not knowing exactly how your workers access and use your files also leaves your business open to an attack.
Get started with remote access security by monitoring:
- What your remote workers are doing online?
- How they’re doing it?
Of course, part of the appeal of remote work is limited distractions and the ability for employees to work autonomously. Yet, there are cloud-based tools that can make monitoring seamless:
- Time Doctor keeps track of remote workers’ hours, what projects they’re working on and when. You can even take screenshots of their computers.
- Hive Desk is another option that will give you a glimpse into which apps your team uses. It also provides how much time they’re spending on different projects.
Both tools give you better insights into your employees’ actions while maintaining accountability. It also ensures that everyone is adhering to secure remote working best practices.
You can also consider monitoring or surveillance tools to check:
- When employees are searching for vacation rentals
- Hopping on social media
- Trying to access restricted data
The surveillance tool sends a message to employees about workplace accountability while ensuring employer data is safe from hacking and malware.
However, brushing up on local laws before you get up and running with your virtual monitoring tools is important. Some areas in the U.S. require consent before monitoring employees remotely.
Even if you’re on solid ground from a legal standpoint, it’s also wise to be upfront with employees about any monitoring or surveillance.
It could help your remote team stay more productive if they know they’re being watched. It will also deter them from wandering to websites that could put your files at risk through malware and hacking.
3. Document Your Security Policy

Employees can’t follow secure remote working protocols if they don’t know what they are. Document and outline your specific security policy, and hold periodic training, workshops, or meetings. Make sure they are fully understood, followed, and executed.
A written policy may work for your business. But it’s advantageous to customize it to cater to different departments with different responsibilities.
For example:
- Training videos on accessing files and graphics may be appropriate for highly visual learners in your graphic design department.
- Case studies and simulations on spot email phishing may work well for customer service representatives.
Once your security policy is in place, ensure all employees have easy access to it with the freedom to ask questions.
Your security policy should also be integral to your employee onboarding process. Before remote workers transition into their workplace responsibilities, ensure they have read and acknowledged the policy.
To start on the right foot, consider requiring an in-person meeting, training session, or hacking simulation during the remote worker’s first week on the job.
4. Scrutinize Your Technology

Bring Your Own Device (BYOD) policies are increasingly becoming the workplace norm. But they also create work-from-home security risks. It comprises weaknesses and points of entry for hackers intruding into your business.
Consider eliminating BYOD policies. Instead, mandate that all work be done on employer-supplied equipment and devices.
Regardless of your take on BYOD in the workplace, take the time to scrutinize the technology and devices used by your team members. Make sure all operating systems are completely up to date.
5. Update Your Systems
Wendy’s found out the hard way that they continued to use outdated technology that opened the door to hackers.
Thousands of franchises were accessed. The customer’s credit card information was stolen and used to rack up fraudulent charges.
Wendy’s was in litigation with customers, banks, and other financial institutions over the data breach. Their reputation has also taken a fatal hit as it dealt with the fallout.
6. Encrypt Your Devices
It’s not enough to simply update your operating systems to secure remote working. Your data and devices should also be encrypted with SSL certificates.
Mandate that workers only use encrypted devices like iPhones. iPhones can be difficult to crack and offer some added built-in protections.
Cloud-based tools are also an issue for businesses and remote workers. It may not practically be to ban cloud-based storage and file transfer services. But you can require using secure, encrypted cloud-based tools, as necessary.
7. Safeguard Your Communications
One of your biggest remote work security risks could be your email system. Investigate what services your remote workers use to send and receive clients’ correspondence, files, and sensitive information. Upgrade their services if needed.
For example, G Suite email encryption offers an email encryption service for G Suite customers. It could help keep your correspondence safer.
You can also get your remote workers up with a VPN to encrypt all their business communications.
8. Conquer Your Biggest Security Risks – Internal Threats

Your biggest security risk may not be your cloud-based providers, devices, or even the growing knowledge base of sophisticated hackers.
More than likely, it’s your remote workers themselves and how they conduct business.
A combination of poor security protocols and rogue workers can make your business a prime candidate for hacking. It might result in high-profile disasters and plenty of financial damage. Some companies have halted remote work policies altogether due to issues with hacking.
In fact, according to IBM, 95% of security breaches caused due to human error.
Even without intentionally creating data breaches and backdoors for hackers, remote workers could jeopardize your business. Here’s what to look out for:
Weak or Duplicate Passwords
Almost 51% of those polled use the same passwords for multiple accounts. Many people haven’t changed duplicate passwords in over five years.
And it’s not just consumers using old passwords on personal email accounts.
Even Facebook founder Mark Zuckerberg once used a terrible password that was revealed in a hack. A hacker group called themselves “OurMine Team” publicly shared that Zuckerberg’s Twitter and Pinterest password was “dadada.”
Fortunately, the OurMine Team hackers only seemed interested in humiliating the billionaire. They didn’t compromise his bank accounts and business matters. But your own company may not fare quite so well in a hack.
Research shows hackers rely on weak passwords when brute forcing PoS terminals.
Crackdown on weak passwords. Require remote and in-office workers alike to regularly update their login information.
Use an automatic password generator to create safe and secure passwords companywide.
Uploading Files to Unsecure Systems
Remote workers unknowingly invite hackers to access their files by using unsecured systems. A few ways your business data can be readily compromised are:
- Uploading sensitive information directly into an email
- Stashing data away in unencrypted storage
- Leaving data on devices without password protection
- Leaving systems open for employees to upload files freely
Hackers could upload their own files with malicious code that can be executed directly on your server.
This could consequently lead to malware or ransomware attacks that could put your company – and your clients – at risk.
Poor Application Security
One-third of all data breaches are caused by unpatched vulnerabilities – 2021 X-Force Threat Intelligence Index from IBM.
That number can seem staggering in a world where we rely on apps and cloud-based tools to run our entire business and personal lives.
Using a combination of open-source CMS and cloud-based apps increases your remote work risks. Make it part of your security policy to approve web app purchases and free downloads.
Your business needs a security company like Indusface to continuously scan web applications and work with a robust WAF. Otherwise, your remote workers invite hackers by using poorly secured apps.
Unlimited Data Access for Nonessential Purposes
Granting unlimited data access to workers comprises your data security for remote workers. To avoid this:
- Limit data access for nonessential purposes. It cuts off dangerous hacking vulnerabilities.
- Only allow remote employees to access the data they need.
- Automatically revoke access to programs and files when they leave your company, finish a project, or move on to a different position.
Make Security Training Fun

Remote access security training probably won’t evoke much enthusiasm around the office. But keeping your business secure doesn’t have to be a dry exercise in compliance. Instead, turn remote work access security training into a competition:
- Start getting your team engaged in the training by setting up phishing email simulators. So, they can see the potential dangers in action.
- Encourage ongoing research about current hacking trends and malware. It keeps your team alert and in the know.
- Offer prizes to engage your team in secure remote working.
- Keep a tally of employees who continuously report suspicious emails and other online activity.
- Offer monthly or quarterly prizes ranging from gift cards to lunch with the executives.
- Make it fun, and employees will want to participate in keeping company data secure.
Conclusion
There is no one way to secure remote working. That’s why it’s crucial to make remote work access security an integral part of your employees’ ongoing training and workplace culture.
Think of your staff as a cohesive unit – and your company’s first line of defense. After all, these days, it takes a unified team dedicated to security to monitor, prevent, and combat security breaches.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 November 17, 2022
November 17, 2022



