Why Authentication alone is not enough for Web App Security?
Authentication is the starting point of almost all serious digital transactions and service consumptions whether it be social media chats, banking, or any other B2B SAAS applications. Almost all of the modern-day applications require users to authenticate their identity based on which they are authorized to consume services from web applications.
The type of authentication for end-users for web applications could be different, but user id and password is a common denominator across all applications. On top of these different web applications, uses few additional factors to make the allow/deny decision on every request based on the following factors.
- Cookie-based authentication. (issue cookie on authentication and use it on subsequent request)
- Token-based (request additional inputs based on time/event synchronized tokes)
- SAML (protocol of communication of identity validation between independent systems)
- OpenID (protocol of identity trust between independent systems)
Most Common Web Application Authentication Vulnerabilities
Applications are changing at a rapid phase and there are still a lot of application security vulnerabilities in a lot of platforms and strong authentication provides the first layer of defense from hiding those vulnerabilities from general access without authenticating to use it first (even if the intent is for hacking). But You might come across many web apps on the internet which follow a very weak authentication process and it is important to address this first and use an authentication system with cost / spend proportionally to the risk you are trying to mitigate. (example – no need for smart card-based authentication for a social media gossip application).

It is important to note that these authentication vulnerabilities mostly relate to the login aspect.
- 2FA (Two-factor Authentication)
Most of the very popular web application security includes two-factor authentication on their login page. However, you will still come across multiple web apps that compromise on this mechanism and do not implement this layer of security or authentication.
- Lack of strong password policy
The password policies have been very strong these days. Case sensitivity, special characters, alpha-numeric, etc., are a few of the high-security techniques that a lot of web applications follow.
However, despite this, there are still a lot of websites and applications that do not mandate a tough password. In fact, you might come across a lot of websites/apps that still work with a 5-digit password for the users.
- Brute force
Thousands of developers implement another layer of web application security to protect against brute force. WordPress, for example, has an option to limit login attempts that is a great step to fight against brute force.
However, you will still find web apps that do not have any security against brute force. Plus, paired with the lack of a strong password policy, the security is more vulnerable to compromises.
Why is authentication not enough in web application security?
When it comes to web applications, the users expect them to be extremely safe and secure with the login. However, the security risks with applications are much more complicated than it sounds. The developer might encounter greater risks than just the login.

Here are some of the most common threats with web app security beyond just authentication and can happen post authentication of a user but by a hacker on the other end who has access to the credentials either by victimizing the user or by exploiting the authentication process itself in the system.
- Broken authentication and management of sessions
Session management results directly in a compromised web application security. This, along with broken authentication, can give the hackers access to session IDs, passwords, and tokens. The accounts can be easily hacked by impersonators with just the use of active session IDs that can be obtained from the URL.
- Injection
Inputting data in forms might not be the safest thing to do on the internet. The data that you enter to fill up forms are stored in a database and are displayed. This makes it easier for hackers to inject commands to SQL and LDAP to gain access to the information on the forms.
- Protection of extremely sensitive data
When it comes to end-users, the most sensitive data can be of the payment methods. Credit and debit card information might be vulnerable to hackers if not protected in the best way possible.
Since there is strong encryption, hackers cannot get into the information directly. So, they use keys and cause middle man attacks to steal clean text data from the browser or the server at large.
All of these points prove that having a strong authentication might not be enough to have excellent web app security.
The concept of zero trust
Now, since the vulnerability in web application security has to take into account the whole application stack which can be consumed after authentication, there is a whole different level of development to ensure uncompromised protection against cyber hacking threats. This is where the importance of a Zero-Trust network comes into the picture.

As the name suggests it is built on the premise of “do not trust any request by default”, even if the user has authenticated. Try to establish the intent of that request before allowing it. In a Web application scenario, this could be the implementation of dynamic trust policies in an application firewall to establish the intent of the user (even authenticated users) before allowing the request to go thru
The strategy includes the fact that the system cuts off every single network access with people who the organization does not recognize. This cut-off includes no access to the IP address or to any machines or server systems within the perimeter of the organization.
Now, the implementation of zero-trust has been the way forward in the IT sector. Statistically speaking, according to a study conducted by Ponemon Institute in 2017, the average cost of data breaches was a whopping $3.62 million.
Moreover, Cybersecurity Ventures predicts, based on the 2017 Annual Cybercrime Report, that cybercrime cost could go up to $6 trillion by 2021, which will be a big leap from $3 trillion in 2015. Such reports have come up even from Gartner Inc., which is an advisory and tech research firm.
Now, these figures have shown up even though major corporate organizations are spending a lot more on their security setup.
The technology that goes behind Zero Trust
To begin with, Zero Trust is not a completely new technology. Instead, it makes use of various existing governance processes and technologies to achieve the level of security it is known for. So, let’s delve deep into the mechanism behind Zero Trust.
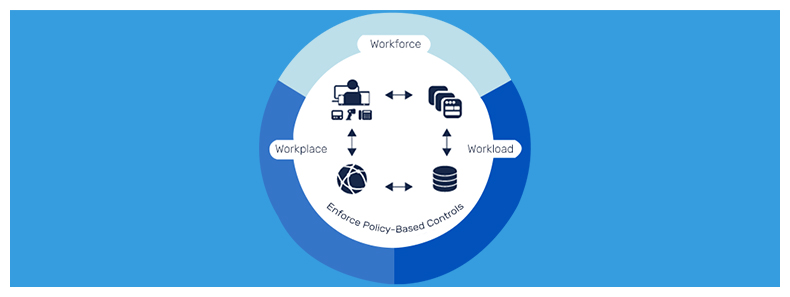
Zero Trust requires all organizations to make use of the granular perimeter and micro-segmentation based on the location and other data of the users. This is done to determine whether any particular user, machine, or network is to be trusted to be given access to the server or not.
Now, some of the most vital technologies that are drawn to Zero trust are orchestration, multi-factor authentication, analytics, IAM, encryption, file system permission, and scoring.
Besides just this, Zero Trust also makes use of the Governance policies to determine the level of access required to complete any particular tasks. And it is only after this that the users are given just the amount of access that is required to perform the task.
How to get started with Zero Trust?
Implementing a Zero Trust network isn’t simple. In fact, according to many experts (Gero, Cunningham, and Mann), the most appropriate implementation of Zero Trust happens only when the network is successful in retaining access to everything until the individual, machine, or system has established complete trust including getting an understanding of the intent of the request. And post that too, the access should always be restricted with the governance policies.

Five fundamental elements of a strong Zero Trust Network
A Zero Trust Network is built on 5 fundamental elements. These elements are:
- There are internal and external threats on the network at all times.
- The network is always hostile.
- The policies must be dynamic in nature and should be taken from as many data sources as possible.
- The network locality is not enough to establish trust in any foreign network.
- Every user, device, and network within the organization is authenticated and then authorized.
Implementation of Zero Trust Network
Now, when it comes to implementing a Zero-Trust network as a web application security, there are some small components that should be taken care of. Here are they:

- Utilizing micro-segmentation
Micro-segmentation means breaking down the organizations’ security perimeter into small zones. This enables the organization to enable separate access to different zones.
- Using multi-factor authentication
Multi-factor is one of the most essential aspects of implementing a Zero-Trust network. It draws its concept from the basic two-factor authentication and adds extra layers of application security. It follows a simple concept – “never trust any foreign user or network, verify and verify again”. If there is something suspicious (for example a Bot attack) ask them to authenticate again for that specific request with a CAPTCHA challenge to prove they are human.
- Practicing Principles of Least Privilege
PoLP (or Principles of Least Privilege) is a part of the governance and ensures that organizations provide the least level of access to individuals or networks to perform any particular task.
- Validating devices
Now, this is nearly the last and among the most important aspects of a Zero-Trust Network. All the devices or machines used by the foreign network within the network perimeter of the organization should be validated. This indicates device verification to determine that the ground level lower hierarchy devices on the network access meet the security requisites.
Summing up
For any major organization in the IT sector, authentication is just a part of the bigger web app security and is not sufficient as a standalone. In fact, the authentication level is increased to a great extent (multi-factor authentication or MFA) in order to comply with the requisites of a Zero Trust Network.
And needless, Zero Trust increases the visibility and transparency in the network access to offer maximum monitoring prowess and goes beyond authentication to ensure every request and every transaction has to be validated with dynamic trust policies with the zero trust principle put in place. In the context of an application, it would mean a Web application firewall with policies updated based on vulnerabilities of application, continuously updating the policies dynamically and taking actions in real-time by not trusting every request, to begin with, have them go thru the trust policy filters in real-time before allowing them access.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 July 3, 2020
July 3, 2020






