Hackers make $193 per Credential Globally through Database Breaches
In the 21st century data is everything. We log and report everything from voting habits of a certain region to purchasing preferences for market segments. It helps governments, businesses, and institutions analyze and strategize better. Take this piece of information for an instance.
“For every two degrees the temperature goes up, check-ins at ice cream shops go up by 2%”
This random piece of information means almost nothing to most of the general public, but for an ice-cream company, it may provide some hint on how to stay ahead of the competition. Now imagine that this information is backed by complete data on regular consumers along with their purchase preferences and contact details. Wouldn’t that be just too great?
That is exactly the kind of information that the data breaches target? Today, digitalism based on the cloud and data is everything. It’s everywhere too. Data is being logged about our choices, ideology, age, hobbies, income, and much more. To enterprises and governments, such detailed data on an entire market segment, region, or country.
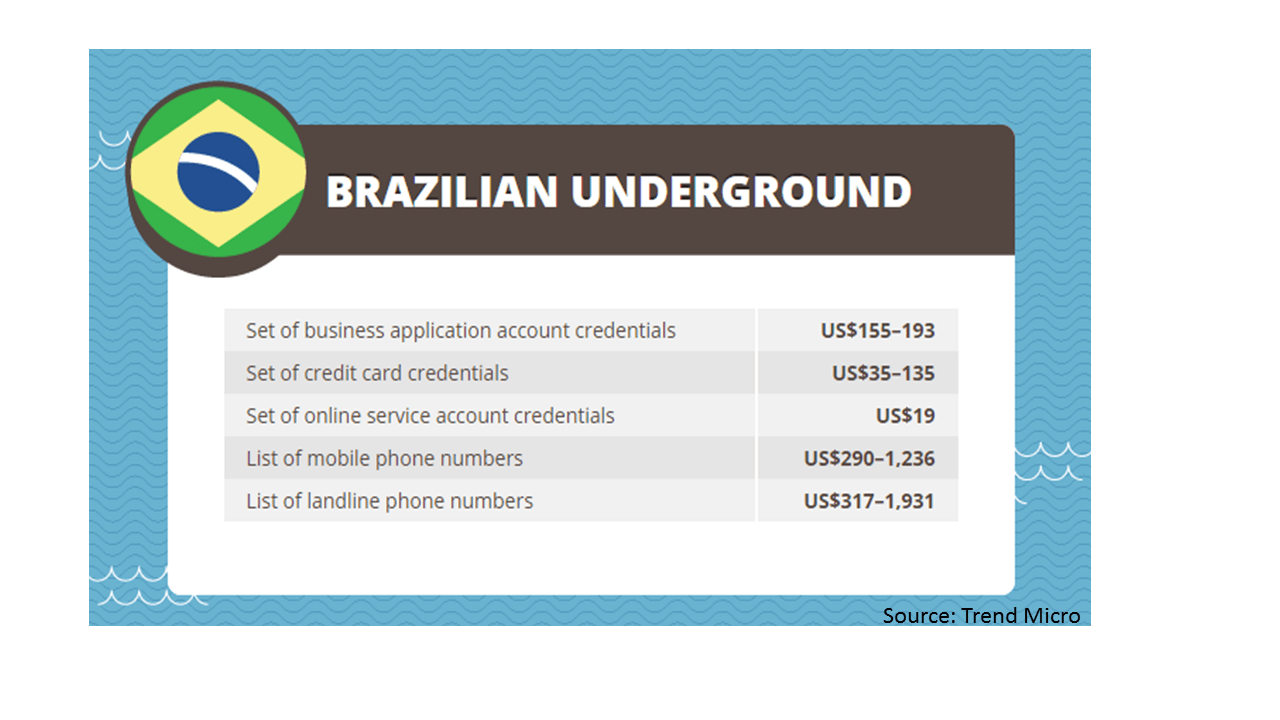
According to Trend Micro, the Brazilian underground market sells business application account credentials for anywhere from $155 to $193 while credit card credentials are sold for $35 to $135. We can just imagine how much this market is worth globally.
Last year, we’ve already witnessed big houses like Sony, Amazon, Alibaba, and JP Morgan Chase falling to data breach attempts. And earlier in 2015, it happened with British Airways, Anthem, and others, indicating that attackers are in no mood to slow down.
Probably every organization understands the value of data, given that they take important business decisions based on that and even invest a lot of both time and money. Unfortunately, they are not doing enough to protect it on the other hand.
On a traditional approach, it is believed that money is more important than data. After all, what can be worse than losing hard cash through online breaches, right? Well not exactly if you look at how data breaches impact finance. According to early estimates, Sony will be losing close to $35 million in just an investigation of the breach that revealed internal emails, unreleased movies, contracts, and details of about 45,000 celebrities.
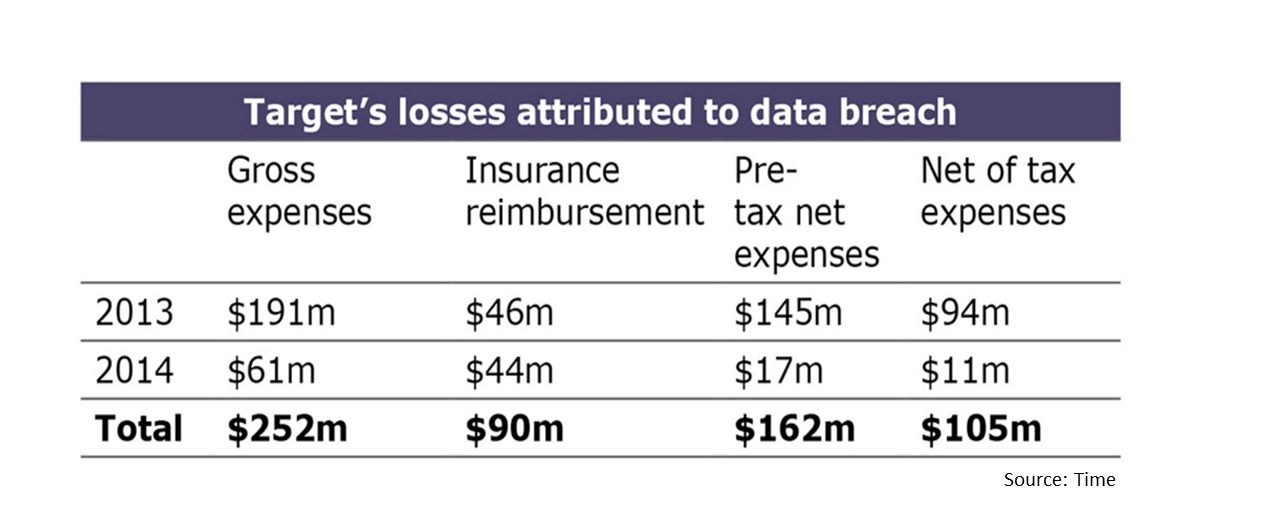
In a similar picture, Target has lost $252 million due to the data breach that involved 70 million individual address-phone records, and 40 million debit and credit card records.
Top Data Breach Threats
While large enterprises can fuel in a lot of money into post-breach postmortems the small and medium-sized organizations do not have that option. At the same time, big data and cloud will be our way of the future, so it’s rather smart to start looking into risk factors and then patching them before it is too late.
At Indusface, we have worked out the potential threats that can lead to data breaches, along with ways to deal with these loopholes.
1) OWASP Top 10 Vulnerabilities
Information research firm Gartner says that 75% of the hacking attempts happen at the application layer. The Open Web Application Security Project, popularly known as the OWASP, has listed the top 10 application vulnerabilities that can be exploited by attackers. Amongst these 10, SQL injection or input injection is the most prevalent way for hackers to get to the databases. Under such an attack, they insert malicious codes or input fields to trick web applications into providing unauthorized access. It is believed that most of the data breaches are a result of this type of attack.
Similarly other OWASP application vulnerabilities including Cross-Site Scripting (XSS) and Cross-Site Request Forgery (XSRF) and can also be exploited to reach the database. Dynamic application security testing for web applications is the best way to start looking for risks that mimic real-life attacks with the help of a security analyst to discover risks.
The detected application vulnerabilities can then be mitigated through a managed web application firewall. It shields application without any changes to the code and makes sure that attackers cannot exploit vulnerabilities.
2) Privilege Abuse
Database and server privileges can be exploited by users internally. Often organizations fail to limit such access to only trusted employees and end up losing sensitive data without knowledge. Consider a healthcare company’s database user who is limited to viewing patient info, what if he takes screenshots or saves the file in personal storage? This data can later be distributed or sold.
Privilege control mechanism control according to job profiles should be monitored periodically. Define and maintain the policy for roles too.
3) Malware
Attackers widely use intrusive and hostile programs to steal sensitive information through computers, networks, web, and mobile applications. These executable code scripts remain untraced for long periods and send data to the owner in batches without any notification to the system administrator.
Regular malware hunting is critical for enterprise and government websites to prevent the transmission of sensitive data. System and web application scanning can help detect malware through the OSI layers.
4) Weak Database Management
Database records huge chunks of information and it’s often impossible to keep track of what’s where on the server. As a matter of fact, most organizations do not really pay a lot of attention in the direction and that’s exactly where they fail. Many times during the testing phase of applications too, unknown new databases are created randomly that the security team might not be able to locate.
5) Weak or No Encryption
Whether it is a backup database or data communication over the internet, encryption with unique keys is the best way to ensure that it’s not sniffed around. However, until today, most companies have not switched to best encryption practices and with vulnerabilities like POODLE and FREAK, it gets easier to hack. And for unencrypted data, it’s a nightmare.
Organizations should adopt advanced encryption techniques. Updated SSL certificates with strong encryption are recommended and so is a web application scanner to mark the loopholes.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 April 8, 2015
April 8, 2015






