What is Credential Stuffing? 11 Best Practices to Prevent Attacks
Data breaches and their immediate impact on the organization are widely publicized.
But what happens after the breach, especially with the breached credentials such as usernames and passwords?
The breached credentials are often sold in the black market or leveraged by the attacker to attack the same or other organizations. This leads to credential stuffing attacks, where the stolen credentials are reused on different websites.
In this blog, we’ll explore the best practices to prevent credential stuffing attacks and the importance of incorporating advanced bot detection strategies.
What is Credential Stuffing Attack?
A credential stuffing attack is a cyberattack where attackers utilize automated tools or botnets to inject stolen or purchased credentials into various online platforms, aiming to gain unauthorized access to user accounts.
These credentials are typically obtained from previous data breaches or are openly sold on the dark web.
How Do Credential Stuffing Attacks Work?
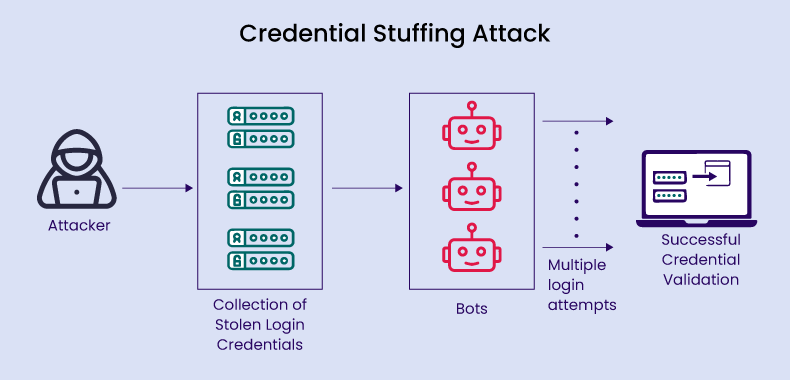
- Attackers compile lists of stolen credentials and feed them into botnets or automated tools.
- The botnets or tools automatically try these credentials across multiple websites simultaneously, using different IP addresses to evade detection.
- Through automation, attackers quickly identify websites with valid stolen credentials.
- Upon successful login, attackers engage in various malicious activities, including extracting sensitive information, financial fraud, identity theft, brand impersonation, and more.
Credential Stuffing vs. Brute Force Attacks
While both credential stuffing and brute force attacks aim to gain unauthorized access, their methodologies differ significantly.
Credential stuffing exploits reused credentials, while brute force attacks rely on guessing passwords through exhaustive trial and error.
Brute force attacks involve making repeated, random attempts to guess passwords without any prior knowledge. This method relies on sheer volume, attempting numerous combinations until the correct one is found.
To prevent both brute force and credential stuffing attacks, implement rate limiting, account lockout, and multi-factor authentication. Additionally, enforce strong password policies and monitor for abnormal login activities.
Real-Time Examples of Credential Stuffing Attacks
- Roku, March 2024: Roku, the streaming service, disclosed that 576,000 accounts were compromised in a new credential stuffing attack. Attackers utilized automated bots to input stolen login details from other websites into Roku’s login pages, exploiting users who reuse passwords across multiple platforms.
- Hot Topic, November 2023: The clothing retailer Hot Topic experienced two waves of credential stuffing attacks in November, resulting in the exposure of customer information such as names, emails, and partial payment data. This affected customers who had accounts with Hot Topic’s rewards program, potentially exposing sensitive details.
- Norton, January 2023: Norton Lifelock Password Manager, a cybersecurity product, fell victim to a credential stuffing attack. Threat actors targeted over 925,000 users, gaining unauthorized access to their accounts and data. Norton had to notify more than 6,500 customers about the security breach, highlighting the widespread impact of credential-stuffing attacks.
Why are Credential Stuffing Attacks Successful?
- Reuse of Credentials: Many users employ the same login credentials across multiple platforms, amplifying the impact of a successful breach.
- Abundance of Compromised Credentials: A vast quantity of stolen credentials is readily available, either for sale on the dark web or openly accessible in plaintext.
- Credential Stuffing Vulnerability: Systems that lack robust protections against repeated login attempts are highly susceptible to credential stuffing. Weak authentication controls, insufficient rate limiting, lack of account lockout mechanisms, and absence of multi-factor authentication (MFA) increase the risk of these attacks succeeding.
How to Prevent Credential Stuffing Attacks?
Preventing credential stuffing attacks requires a multi-layered approach that combines strong password policies, user education, and advanced bot detection techniques.
Bot detection solutions can identify and block automated login attempts, reducing the effectiveness of credential-stuffing attacks.
Below are 11 best practices for credential stuffing mitigation:
1. Enforce Strong Password Policies
Make sure passwords are strong, with a mix of letters, numbers, and symbols. Set them to expire regularly and add extra security layers like MFA.
Store user info securely using hashing, never in plain text. Keep an eye on public breaches; if any user info is compromised, make them reset their password and use MFA.
2. Educate Users About Security Awareness
Raise awareness among users about the importance of safeguarding their credentials and recognizing phishing attempts. Provide regular training sessions on cybersecurity best practices and encourage the use of password managers to securely store and manage passwords.
3. Implement Account Lockout Mechanisms
Implement account lockout mechanisms that temporarily lock user accounts after a specified number of failed login attempts. This helps thwart brute force attacks and prevents automated bad bots from gaining unauthorized access.
4. Monitor Dark Web for Stolen Credentials
Utilize dark web monitoring tools to proactively search for compromised credentials associated with your organization. Promptly notify affected users to change their passwords and take necessary security measures.
5. Rate Limiting
Set thresholds for the number of login attempts allowed within a specified time window. For example, you might limit login attempts to five per minute per IP address. If the threshold is exceeded, further login attempts are temporarily blocked. Know more about rate limiting here.
6. CAPTCHA Challenges
Incorporate login challenges into the authentication procedure. CAPTCHAs, for instance, offer tasks that are simple for humans but challenging for automated bots, like deciphering distorted text or selecting specific images.
However, it’s essential to use CAPTCHAs alongside other methods, as they can potentially disrupt business operations if overused.
7. User Behavior Patterns
Analyze various aspects of user behavior, including typing speed, mouse movements, and navigation patterns. Legitimate users often exhibit consistent behavior over time, while bots may demonstrate erratic or repetitive actions.
8. Anomaly Detection
Use machine learning algorithms to detect anomalies in login patterns. For example, multiple login attempts with different credentials within a short period may indicate a credential stuffing attack. By monitoring for such anomalies, you can identify and mitigate suspicious login activity.
Train machine learning algorithms using historical login data to recognize patterns indicative of credential-stuffing attacks. By analyzing factors such as login frequency, IP address reputation, and behavioral characteristics, machine-learning models can identify suspicious activity and adapt to new attack tactics over time.
9. Challenge-response Mechanisms
Introduce challenges that require human interaction to verify the authenticity of login attempts. For example, present users with tasks such as selecting images with specific objects or answering knowledge-based questions.
These challenges are designed to differentiate between human users and automated bots, adding an extra layer of security to the authentication process.
10. Threat Intelligence Feeds
Stay informed about emerging threats and the latest botnet tactics by subscribing to threat intelligence feeds and security bulletins. Regularly monitor industry sources for information on new attack techniques, vulnerabilities, and malware campaigns. Threat intelligence feeds provide valuable insights into evolving threats and enable proactive defense measures.
11. Implement WAAP
WAAP (Web Application and API Protection) solutions go beyond traditional security measures by bundling multiple protections, including WAF, bot mitigation, API security, and DDoS protection.
A WAF, as a core component of WAAP, plays a critical role in mitigating credential stuffing attacks. It detects and blocks suspicious login attempts by analyzing traffic patterns and identifying anomalies. By implementing IP blocking and rate limiting, a WAF prevents automated tools from making multiple login attempts, significantly reducing the risk of account compromise.
Additionally, WAAP solutions integrate advanced bot mitigation features to identify and block malicious bots attempting credential stuffing, account takeover, and automated attacks. These features analyze user behavior, request headers, and device fingerprints to differentiate between legitimate users and automated bots. CAPTCHA challenges, JavaScript-based bot detection, and AI-driven risk scoring further enhance bot mitigation efforts, ensuring that real users can access applications while malicious automation is blocked.
By continuously monitoring web traffic and correlating information from various sources, WAAP solutions like AppTrana provide real-time attack mitigation, protecting applications from bot-driven attacks, API abuse, and sophisticated threats. With customizable security policies, WAAP allows organizations to define tailored authentication, access control, and bot detection strategies—effectively preventing credential stuffing while maintaining a seamless user experience.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 March 11, 2025
March 11, 2025