Web Application Penetration Testing (WAPT) is a simulated cyberattack against a website or web application to identify and exploit vulnerabilities before attackers exploit them. It focuses not just on listing vulnerabilities but demonstrating how they can be chained to cause real business impact such as data breaches, privilege escalation, or service disruption.
Why is Web Application Penetration Testing Important?
Web applications are the most exposed layer in any digital infrastructure they are public-facing, globally accessible from any device, and unlike internal systems, require no internal access to be attacked. As a result, they become a preferred focus for attackers seeking entry points. Behind these web layers often lie your most critical assets such as login portals, transaction systems, customer records, and sensitive business logic, all of which are directly exposed to the internet.
These vulnerabilities are often subtle and deeply embedded in custom workflows, making penetration testing essential. As organizations adopt agile and CI/CD practices, new code is pushed rapidly, often daily while security struggles to keep up. Without continuous penetration testing or DevSecOps integration, vulnerabilities can slip into production unnoticed.
Moreover, real-world exploitation goes beyond detection, pen testers demonstrate how vulnerabilities can be exploited, what data can be exfiltrated, whether privilege escalation is possible, and how vulnerabilities can be chained for full-system compromise. Regulatory frameworks like PCI DSS 4.0, HIPAA, and ISO 27001 have also evolved, placing greater emphasis on application-layer and API-level security rather than just infrastructure protection.
This is especially important as API vulnerabilities like BOLA, token leakage, or lack of rate limits are now among the most exploited and can be even more dangerous than UI bugs. Beyond compliance and risk mitigation, web application security is also a matter of brand trust. Customers entrust applications with their most sensitive information, and a single breach can cause irreversible damage such as loss of reputation, legal consequences, and erosion of customer confidence. Conducting penetration tests on web applications is therefore not just a best practice, it is a business-critical priority.
Step-by-Step Web Application Penetration Testing Process
The typical WAPT lifecycle follows these seven stages:
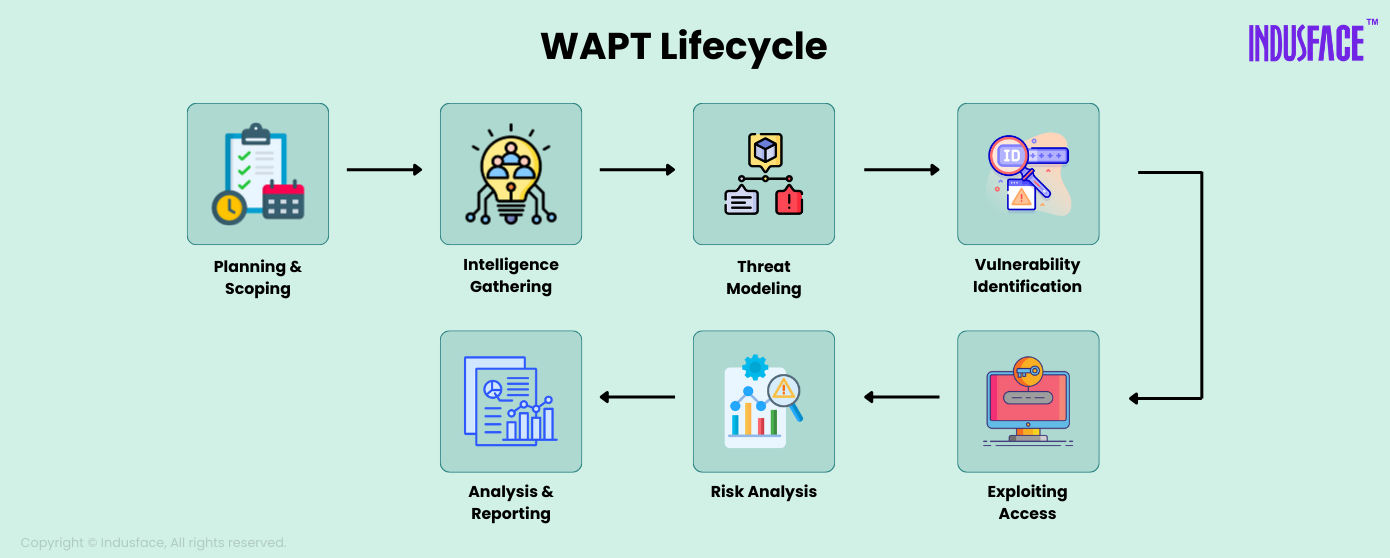
1. Planning and Scoping
The process begins with planning and scoping, where the objectives of the penetration test are clearly defined. This includes identifying which web applications, APIs, or components will be tested, determining whether the testing will occur in a production or staging environment, and setting any limitations or compliance requirements. Both technical and business stakeholders collaborate to establish timelines, communication protocols, and expected outcomes.
2. Intelligence Gathering
The next step is commonly referred to as reconnaissance. This involves gathering information about the application’s infrastructure, technologies used, third-party integrations, exposed endpoints, and publicly accessible data. The goal is to map the application’s surface area and identify potential entry points that an attacker might exploit.
3. Threat Modeling
With a clear understanding of the application’s structure, testers move to threat modeling. In this phase, they analyze user roles, workflows, and data flows to identify high-risk components and potential abuse cases. Business logic, authentication mechanisms, and access control layers are examined to prioritize areas that may be vulnerable to targeted attacks.
4. Vulnerability Identification
Next comes vulnerability identification. Automated tools such as DAST or SAST are often used to scan for common vulnerabilities like SQL injection, XSS, insecure headers, and outdated software. However, testers also manually probe the application to uncover deeper vulnerabilities that scanners might miss such as business logic vulnerabilities, chained vulnerabilities, or environment-specific misconfigurations.
5. Exploitation/Gaining Access
At this stage, the testers enter the target through the entry points they discovered at the time of intelligence gathering and scanning. They gain access to the system by exploiting the vulnerabilities. They perform a test case for compromised systems under each scenario.
6. Post-Exploitation and Risk Analysis
After exploitation, the focus shifts to analyzing how far an attacker could potentially go. This includes assessing whether lateral movement is possible, if data can be accessed or manipulated, and what business functions are affected. This context helps in understanding the true severity of each vulnerability beyond just technical ratings.
7. Analysis and Reporting
The final stage of penetration testing comprises analyzing the results and submitting a report to the organization. This report elaborates the vulnerabilities that were exploited, steps that were taken from beginning to end of the testing, data accessed during the testing, and everything else that the organization should know about its security architecture to mitigate potential cyberattacks.
Types of Web Application Penetration Testing: Black Box, White Box, Grey Box
| Type | Description |
|---|---|
| Black Box | Tester knows nothing about the app, just like a real outsider attacker. |
| White Box | Full knowledge of the system, source code, credentials, etc., ideal for deep testing. |
| Grey Box | Partial knowledge, common in real-world simulations (e.g., logged-in user with some privileges). |
Each method offers different levels of insight. Black box mimics unknown external threats, while white box reveals hidden logic vulnerabilities.
What Does a Web Application Pen Tester Look For?
A web application penetration tester does not just skim through code or click around the UI. They think like an attacker, with curiosity, creativity, and a deep understanding of how things can go wrong beneath the surface. While automated pen testing tools check for known vulnerabilities, a human pen tester goes beyond checklists to uncover logic vulnerabilities, chained vulnerabilities, and real-world exploit paths.
Let us break down what exactly a pen tester looks for in a web application:
1. Injection Vulnerabilities
Vulnerabilities where user input is improperly handled, allowing attackers to inject malicious commands (e.g., SQL, OS, or LDAP). These vulnerabilities can expose to sensitive data, allow unauthorized access to user credentials, or even result in a complete breach of the system.
What a pen tester does:
They test how user inputs are processed across forms, URLs, headers, cookies, and APIs. They may try:
- OR ‘1’=’1′ in login forms (SQLi)
- Shell commands in file uploads (Command Injection)
- Payloads in HTTP headers or parameters
2. Authentication and Session Vulnerability
Weaknesses in login mechanisms, password resets, multi-factor authentication, or session management. If attackers can bypass login or hijack valid sessions, they can impersonate users, potentially even administrators, gaining unauthorized access to sensitive data and functionality.
What a pen tester does:
- Attempt brute-force or credential stuffing attacks
- Try session fixation or hijack existing session tokens
3. Authorization Vulnerabilities (Broken Access Control)
Weak or missing checks that allow users to access data or perform actions beyond their privileges. Broken access controls are one of the most exploited vulnerabilities. If not properly implemented, even low-privileged users could gain access to confidential data or admin functions.
What a pen tester does:
- Tamper with user IDs in URLs (testing for IDOR – Insecure Direct Object Reference)
- Try accessing admin-only features as a standard user
- Attempt to elevate privileges by modifying roles or tokens
4. Cross-Site Scripting (XSS)
A vulnerability where untrusted data is injected into a web page without proper sanitization, allowing attackers to execute scripts in users’ browsers. XSS can lead to session theft, phishing, content manipulation, or redirection to malicious sites, putting users at direct risk.
What a pen tester does:
- Inject malicious JavaScript into form fields, URLs, or comments
- Check if inputs are reflected back without sanitization
- Use browser dev tools to inspect script behaviors
5. Cross-Site Request Forgery (CSRF)
An attack where a user’s authenticated session is tricked into performing unwanted actions. CSRF attacks may result in unauthorized transactions or profile modifications under the user’s identity.
What a pen tester does:
- Craft malicious forms or image requests that simulate valid user actions (like changing an email or password)
- Check whether tokens are used and validated properly
- Test actions that are accessible via GET or POST without CSRF protection
6. Business Logic Vulnerabilities
Vulnerabilities in the application’s flow that attackers can abuse to gain unfair advantages (e.g., bypassing payments, reusing promo codes, or manipulating prices). These vulnerabilities are often missed by scanners because they are specific to your app’s logic. A well-crafted exploit can cost businesses millions or compromise integrity.
What a pen tester does:
- Test “happy” and “unhappy” paths to find exploitable logic
- Try race conditions, double submissions, or timing attacks
- Analyze how workflows behave when parameters are manipulated
7. File Upload Vulnerabilities
Improper handling of file uploads that allows malicious files (e.g., backdoors, scripts) to be uploaded and executed. A vulnerable file upload can give attackers remote code execution (RCE) or allow them to host phishing pages on your domain.
What a pen tester does:
- Upload PHP, ASPX, or shell files disguised as images
- Bypass file extension restrictions using double extensions (e.g.,jpg.php)
- Check where files are stored and if they can be accessed/executed
8 Best Practices for Web Application Penetration Testing
1. Prepare the Pen testing Environment
Web application pen testing should be performed on the production environment. While conducting the test directly on production, you should set certain limits for the pen testers. Also, schedule the test in a way that is not slowing down the network response time for your organization and your clients.
The most important restriction is not to run DDoS attacks on production. If your pen test cannot be conducted on the production environment, prepare an environment, which is identical to production, and generate user accounts for the pen testers.
2. Build Attackers Personas
For better results, web-based penetration testing must be enacted realistically. While doing testing, you should put yourself in the shoes of the attackers’ persona. You must think and act like a real cyber attacker, equipped with an advanced set of a motive, goal, and skills. The motive is a vital element in structuring hacker personas.
Business or money advantage, revenge by an ex-business partner, culture or religious ideology, and peer recognition are few possible motives. Rank the personas based on which personas you should be concerned about. Sketching attackers this way aids you to narrow down your concentration and helps you to be prepared for the real attacks.
3. Set Testing Boundaries Clearly
One thing everyone should remember is that web app penetration testing is just a simulation, not an actual attack. Hence, the testing boundaries should be outlined as to:
- Who will perform the test?
- When to conduct the test
- What is permissible and what cannot be done
- Whom to send all reports and communications
4. Define Web Penetration Testing Methodology
When it comes to penetration testing best practices, pen test methodology is such an imperative step that applies for both external and internal pen testers. The testing methodology is a set of security guidelines, on which your web penetration testing should be conducted. Make sure the testing is aligned with industry-standard security frameworks and comprised of both automatic and manual advanced testing.
Some of the important security testing methodologies & standards:
- Open Web Application Security Project (OWASP)
- Penetration Testing Framework (PTF)
- Open-Source Security Testing Methodology Manual (OSSTMM)
- Information Systems Security Assessment Framework (ISSAF)
- Payment Card Industry Data Security Standard (PCI_DSS)
A solid methodology not only helps ensure testing quality but also builds consistency across different engagements. Once the methodology is set, it should be operationalized using a well-defined checklist to ensure no critical step is missed during execution.
5. Launch Security Monitors Before
If you really do not want to waste your valuable pen-testing time, it is best practice to implement a security scanner or monitor. If you have the web application monitoring in place to detect your basic vulnerabilities, the pen testers need not spend their energy in uncovering those vulnerabilities.
6. Freeze Development in Penetration Testing Environment
The best practice of penetration testing is to test the application as a whole, not individual pieces of it. Pen testing will detect the vulnerabilities within the given settings. If you change that setting by adding new patches or packages or modifying hardware components, you won’t be able to get the valid pen testing results.
Similarly, it is not advisable to fix the vulnerabilities while testing though this is vital for some occasions. You will get a more authoritative result when a stable application is tested and get more value for your money.
7. Choose the Right Penetration Testing Tools
There are plenty of pen-testing tools available in the market. Some are free to download and use and some are vendors supplied. Selecting the right tool(s) depends mainly on the pen-testing environment you are using.
If you are confused about what makes the best penetration testing tool, here is our guide.
8. Decide Between In-house Testers and External Pen-Testing Services
You can get a lot of advantages from in-house pen testers if they have the skillset as the in-house team is more familiar with your application.
However, it is better to opt for specialized external web app penetration testing professionals to leverage more expertise and an out-of-box point of view. It also ensures organizational independence for web-based penetration testing that not only ensure best practice to the difference of opinion, but also a need by PCI compliance.
A penetration testing consultant from Indusface is certified and also gives a safe-to-host certificate after a revalidation test. This can be used during external audits to prove that the application is safe.
The Hybrid Approach: Automation + Human Expertise
Many organizations struggle to choose between automated and manual penetration testing. The truth is, each has its strengths, and the right choice often depends on your goals, application complexity, and risk profile. For high-frequency deployments and broad vulnerability checks, automated testing is efficient. For simulating real-world attacks, validating critical vulnerabilities, and protecting complex workflows, manual testing is essential.
The most effective web application penetration tests today follow a hybrid model, combining the speed and breadth of automation with the depth and intuition of human expertise. Automated tools can quickly identify known vulnerabilities like SQL injection, cross-site scripting (XSS), or missing headers. But their ability to understand business logic, user behavior, and multi-step attack chains is limited.
That is where manual testing bridges the gap. Skilled security professionals simulate real-world adversarial behavior, validate whether vulnerabilities can be exploited in production, and assess the actual risk and business impact. This combination delivers a 360-degree view covering both technical vulnerabilities and logical weaknesses while also reducing false positives and ensuring that reported vulnerabilities are relevant and actionable.
Why Choose Indusface WAS for Web Application Pen Testing?
Indusface WAS Web Application Penetration Testing offers a comprehensive, hybrid approach to securing your web applications by combining automated scanning with expert manual testing. While the platform’s automated engine rapidly identifies known vulnerabilities like SQL injection, XSS, and misconfigurations, its real strength lies in the integration of certified security professionals who validate findings and uncover complex vulnerabilities like business logic vulnerabilities and chained exploits. This ensures a deep, real-world assessment tailored to your application’s unique risk profile.
With SwyftComply, it enables instant autonomous remediation of open vulnerabilities at the WAAP level, so you are not just finding vulnerabilities but closing them faster. Combined with features like proof of exploit, risk-based prioritization, and on-demand retests, Indusface WAS not only detects threats with precision but also accelerates remediation, offering organizations a streamlined, context-rich, and reliable security solution.
Do not let hidden vulnerabilities put your business at risk. Schedule a web application penetration testing with Indusface WAS today.


