According to the latest Verizon Data Breach Investigations Report (DBIR), over 60% of breaches involved known vulnerabilities that had not been patched or properly assessed. This alarming statistic highlights a persistent gap between vulnerability detection and action. Even in environments where security tools are in place, attackers often succeed by exploiting overlooked or underestimated vulnerabilities.
In a threat landscape where breaches are often the result of unpatched vulnerabilities, weak authentication, or misconfigured systems, businesses must move beyond surface-level scans. Vulnerability Assessment and Penetration Testing (VAPT) offers a proactive approach to uncovering and addressing these risks, before malicious actors do.
What is VAPT?
VAPT (Vulnerability Assessment and Penetration Testing) is a layered testing methodology that uncovers, validates, and prioritizes security vulnerabilities across applications, infrastructure, APIs, and cloud assets.
- Vulnerability Assessment identifies weaknesses such as outdated components, misconfigurations, and common exposures using automated tools.
- Penetration Testing simulates actual attacks, exploiting the vulnerabilities to measure how much damage an attacker could do.
Together, they provide a complete risk picture, far beyond what traditional vulnerability scanners or audits can reveal on their own.
Why is VAPT Important?
1. Uncover Vulnerabilities Before Threat Actors Do
Automated scans are fast, but they cannot determine which issues are exploitable. Penetration testing adds critical context by mimicking attacker behavior, showing how vulnerabilities can be chained together or used for privilege escalation.
2. Strengthen Security Posture Through Actionable Insights
VAPT does not just find vulnerabilities; it helps prioritize remediation based on business impact. The result is a practical roadmap for reducing risk, improving code quality, and hardening infrastructure.
3. Proof of Exploitability
Automated tools flag hundreds of vulnerabilities. Penetration testing shows which ones are exploitable, reducing false positives.
4. Achieve and Maintain Regulatory Compliance
Frameworks like PCI DSS, GDPR, ISO 27001, and HIPAA require periodic security assessments. VAPT helps organizations demonstrate due diligence with evidence-based reports that satisfy audit requirements. For example, PCI DSS Requirement 11.3 explicitly states that organizations must “implement a methodology for penetration testing” at least annually and after significant infrastructure or application changes. These assessments are critical not only for passing audits but also for proving that appropriate safeguards are in place to protect sensitive data.
Explore how effective vulnerability management supports compliance efforts.
5. Reduce the Risk of Business Disruption
Unpatched vulnerabilities in applications, APIs, or third-party integrations often lead to data breaches or ransomware. VAPT identifies these risks early, helping teams fix them before attackers do.
Understanding the Two Halves of VAPT
VAPT is not a single process; it is a combination of two distinct but complementary approaches: Vulnerability Assessment (VA) and Penetration Testing (PT).
| Parameter | Vulnerability Assessment (VA) | Penetration Testing (PT) |
|---|---|---|
| Goal | Identify known vulnerabilities | Simulate real-world attacks to exploit those vulnerabilities |
| Method | Automated tools and scans | Manual testing by ethical hackers |
| Depth of Analysis | Surface-level vulnerabilities and misconfigurations | Deep dive into chained exploits and business logic flaws |
| Examples of Findings | OWASP Top 10, Outdated software, open ports, CVEs | Authentication bypass, privilege escalation, logic flaws |
| Effort | Low (automated) | High (manual and contextual) |
| Outcome | List of vulnerabilities | Proof-of-concept and impact report |
| Frequency | Regular (monthly/quarterly scans) | Periodic or milestone-based (e.g., before major releases) |
| Ideal Use | Continuous monitoring | In-depth testing for compliance and assurance |
How VAPT Works: Step-by-Step Breakdown of an Effective Security Testing Process
VAPT is not a one-off task, but a structured process that combines automation, expert insight, and iterative improvement. Each step from planning to remediation ensures vulnerabilities are not just identified but thoroughly understood and addressed. Let’s break down how the process typically unfolds in seven essential stages.
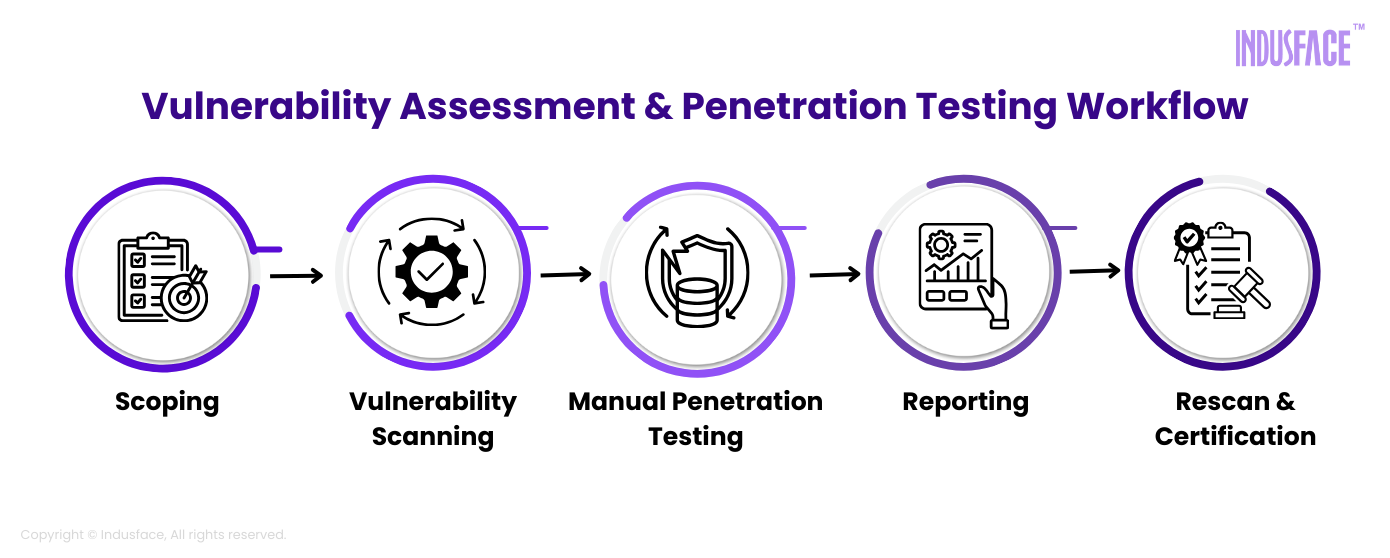
1. Scoping
The first step is to define the scope of testing: what systems, applications, APIs, or cloud resources will be assessed. This includes deciding on the type of testing to be performed: unauthenticated (black box), authenticated (white box), or a combination (grey box).
Scoping is more than listing assets, it is about understanding where your attack surface truly lies.
With Indusface WAS, this process is supported by automated Attack Surface Mapping on Asset Discovery, which helps organizations identify all public-facing domains, subdomains, and API endpoints tied to their infrastructure. By uncovering forgotten or unmanaged digital assets, it ensures full coverage and eliminates blind spots from the VAPT process.
The clarity gained during scoping also helps:
- Set expectations for the depth and breadth of testing
- Define success criteria for remediation
- Align testing with business-critical assets
2. Automated Scanning
In this phase, security tools are used to identify known vulnerabilities, such as:
- CVEs (Common Vulnerabilities and Exposures)
- Server misconfigurations
- Insecure HTTP headers
- Weak cryptographic configurations
- Outdated software components
Scans are configured to run against defined targets: web applications, APIs, cloud interfaces, using a consistent schedule and customizable rules. The goal is to cover a broad range of risks, including:
- OWASP Top 10 vulnerabilities (like XSS, SQL Injection, and CSRF)
- SSL/TLS misconfigurations
- Insecure or exposed APIs
- Open ports and legacy code components
Indusface WAS automates this entire process using an intelligent, risk-based scanning engine. It regularly scans both websites and APIs for vulnerabilities, focusing not just on standard CVEs but also on exposure based on application behavior and context. With coverage for OWASP Top 10 and beyond, it ensures both depth and accuracy.
The platform also allows businesses to:
- Schedule recurring scans
- Configure greybox scans using authentication credentials
- Customize scan depth and targets
- Receive prioritized findings that ensure zero false positives to help save developers
Explore guided authenticated scanning with Indusface WAS.
3. Manual Testing
While automated tools are excellent for detecting known issues, they often miss complex vulnerabilities such as:
- Chained exploits
- Authentication bypasses
- Business logic flaws
- Privilege escalation paths
This is where manual testing by ethical hackers becomes critical. Pen testers simulate real-world attack scenarios tailored to your application’s logic, user roles, and workflows. They explore how a series of low-risk issues can be combined to create high-impact breaches.
Indusface WAS does not stop at automated scanning. It complements automated scans with manual verification by certified security experts. These experts validate scan findings, eliminate false positives, and dig deeper to uncover hidden flaws that tools may overlook.
With this hybrid model:
- You get validated, high-confidence results.
- Developers receive actionable remediation steps.
- Security teams can prioritize based on exploitability and real-world risk.
Manual testing can uncover hidden vulnerabilities, but how do financial organizations prioritize them effectively? Learn more in our VAPT guide for financial services here:
4. Reporting
All findings are categorized by risk, severity, exploitability, and compliance relevance. Reports provide detailed remediation guidance aligned with your business impact.
All validated findings are compiled into a structured report, which includes:
- CVSS scores and exploitability details
- Screenshots or payloads used in exploitation
- Business impact analysis
- Compliance relevance (e.g., PCI, ISO, GDPR)
- Tailored remediation recommendations
Indusface WAS vulnerability reports are designed to bridge the gap between security and development teams. Risk levels are aligned with technical severity and business priority, helping teams focus their efforts on what matters most.
The result is not just a list of vulnerabilities, but a security roadmap with actionable next steps.
5. Rescan & Certification
After remediation, a rescan is conducted to verify that vulnerabilities have been fixed properly. This step ensures that vulnerabilities have not just been marked as resolved but are no longer exploitable.
Once confirmed, a final report or VAPT certificate can be issued, which is often required for:
- Regulatory compliance (e.g., PCI DSS, ISO 27001 audits)
- Customer assurance during security reviews
- Internal security milestones and board-level reporting
Indusface WAS supports this re-scanning cycle with easy scheduling of follow-up scans and automated change detection to catch regressions early.
What Makes a Good VAPT Report
A quality VAPT report does not just list vulnerabilities; it connects them to real business impact. At Indusface, reports are designed to be both technical and actionable.
- Executive Summary for stakeholders
- Exploitation Proof including screenshots or payloads
- Remediation Guidance tailored to your tech stack and environment
- Risk Scoring that goes beyond CVSS to include ease of exploitation, east-west dependence and more
Indusface WAS users receive these reports with every assessment. Expert validation ensures findings are accurate, relevant, and risk-prioritized, enabling focused remediation.
Secure Smarter with VAPT
VAPT is not just about finding flaws; it is about understanding and fixing what really matters. With Indusface WAS, you get automated scanning, expert-led manual testing, and reports that drive action, not confusion.
Ready to strengthen your security and meet compliance with confidence? Start your Scan now.


