The OWASP Top 10:2025 has arrived and it is more than just a list. It is a reflection of how rapidly the software security landscape is changing. Backed by industry data and community insights, this new edition highlights both familiar risks that continue to plague developers and new, emerging threats reshaping application security.
What is New in OWASP Top 10 2025
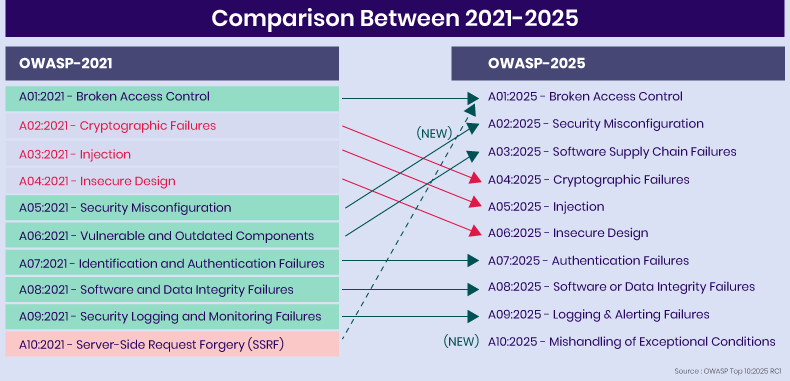
The OWASP Top 10:2025 introduces two new categories and consolidates one, refining how risks are classified. The changes emphasize supply chain integrity, misconfiguration risks, and error handling weaknesses, reflecting the modern threat landscape where interconnected systems and third-party dependencies dominate.
New Additions:
- A03: Software Supply Chain Failures
- A10: Mishandling of Exceptional Conditions
Consolidation:
- Server-Side Request Forgery (SSRF) has been absorbed into Broken Access Control.
The OWASP Top 10:2025 Breakdown
Let us explore each category and what it means for modern application security.
A01:2025 – Broken Access Control
Access control is broken when users (or attackers) are able to perform actions or access resources they should not be permitted to. This includes bypassing authorization checks, exploiting direct object reference vulnerabilities, and leveraging SSRF (“Server-Side Request Forgery”) now folded into this category.
Broken access control remains #1 because despite mature controls, authorization logic remains fragile across frameworks, APIs, microservices and cloud-based systems. In the dataset ~3.73% of tested applications had at least one mapped weakness.
Typical CWEs/Examples: Direct object references (CWE-2000-ish), use of “allow all” predicates, SSRF via internal services, missing tamper-proofing of role checks.
What you should check:
- Ensure role/permission matrices are enforced server-side (not only client-side).
- Verify internal APIs/services cannot be invoked inadvertently by external users.
- Review SSRF-capable endpoints (e.g., proxy, fetcher, URL parameter) and ensure they validate whitelisted hosts.
- Monitor for “excess privileges” and review for orphaned access rights.
A02:2025 – Security Misconfiguration
Configuration mistakes in software stack, frameworks, platform, container, cloud or application settings that leave systems open or improperly secured. In OWASP Top 10 2025 this category has moved up to #2 (~3.00% of applications had one or more of the 16 CWEs).
As modern applications increasingly rely on configuration (deployment, cloud, containers, feature toggles, infrastructure as code), misconfiguration becomes pervasive. A minor mis-setting (e.g., public bucket, default credential) can result in massive exposure.
Typical CWEs/Examples: Default accounts/credentials, unnecessary enabled features (e.g., debug endpoints in production), open cloud-storage buckets, insecure HTTP headers, unpatched/unhardened chassis.
What you should check:
- Harden deployment pipelines: remove default credentials, disable unused endpoints.
- Review IaC (Infrastructure as Code) templates & cloud-permissions for unnecessary public exposure.
- Ensure secure headers (CSP, HSTS, etc) are used and configuration is validated post-deployment.
- Implement configuration scanning and compliance checks as part of CI/CD.
A03:2025 – Software Supply Chain Failures
This new category (expanded from “Vulnerable and Outdated Components”) covers failures in the software ecosystem: dependencies, build systems, distribution infrastructure, package management, and trust in those components.
While the testing data is still limited (few apps flagged), the exploit impact and community concern are high. Attackers increasingly target the supply chain because compromise here scales broad.
Typical CWEs/Examples: Use of a compromised library, malicious update injected into build pipeline, dependency tree with unchecked transitive risks, compromised distribution channel.
What you should check:
- Maintain a software bill of materials (SBOM) and map all dependencies (direct & transitive).
- Validate integrity of build pipelines (CI/CD) and ensure updates are signed/verified.
- Monitor third-party component alerts and have patch/replace process for high-risk dependencies.
- Treat supply-chain risk as a first‐class security risk (not just “componentupdate”).
A04:2025 – Cryptographic Failures
Failures around encryption, key management, secure channel usage, or cryptographic algorithms. (~3.80% of tested applications had one or more of the 32 CWEs)
Encryption does not get fewer attacks rather the surface expands (cloud, mobile, IoT). Weak or mis-used crypto leads directly to data exposure or system compromise.
Typical CWEs/Examples: Hard-coded keys, weak algorithm (e.g., MD5/SHA1), insecure random number generation, storing sensitive data unencrypted, failing to enforce TLS/HTTPS.
What you should check:
- Ensure sensitive data is encrypted at rest and in transit; review algorithm and key-length appropriateness.
- Validate key lifecycle: creation, rotation, retirement, access control.
- Check for usage of obsolete algorithms or libraries flagged by modern cryptographic standards.
- Verify via code reviews that crypto primitives are not being mis-used (e.g., home-grown crypto).
A05:2025 – Injection
Injection vulnerabilitiesoccur when untrusted data is sent to an interpreter as part of a command or query, letting attackers execute unintended commands. This category covers a broad range (38 CWEs) from SQL injection, command injection, XSS to OS command injection.
Though ranked #5 in 2025 (down from earlier positions), injection is still highly exploited and continues to surface frequently, especially in legacy code or mis-handled input scenarios.
Typical CWEs/Examples: SQL Injection, XSS (Cross-Site Scripting), OS command injection, LDAP injection, NoSQL injection, expression language injection.
What you should check:
- Validate all user input; use parameterized queries or safe APIs rather than string-concatenation.
- Escaping/encoding output based on context (HTML, JavaScript, URL, SQL).
- Disable dangerous interpreter features (e.g., dynamic evaluation).
- Have active dynamic scanning (DAST) + static analysis with injection detection rules.
A06:2025 – Insecure Design
Introduced in the 2021 edition and maintained here at #6 for OWASP Top 10 2025. Focuses on architectural and design flaws when threats, misuse cases or business logic fail to be addressed in early phases.
As security teams push left into design/threat-modeling, the presence of insecure design shows the gap between development process and security process. Fixing design flaws later is expensive.
Typical CWEs/Examples: Lack of threat modelling, insecure defaults by design, poor trust boundary definition, business-logic vulnerabilities (e.g., price manipulation, discount escalation).
What you should check:
- Incorporate threat modelling and security architecture review in project planning.
- Define and document trust boundaries, data flow diagrams, misuse cases.
- Review business logic for abnormal flows (e.g., discount stacking, role escalation).
- Ensure security requirements (not just functional) are part of UI/UX and backend design.
A07:2025 – Authentication Failures
This category (formerly “Identification & Authentication Failures”) remains at #7 in OWASP Top 10 2025. It relates to vulnerabilities in authentication mechanisms, session management, identity life-cycle, and improper credential handling.
Even though frameworks improve out‐of‐the-box, custom code and integration gaps lead to authentication vulnerabilities that enable account take-over, impersonation or session hijack.
Typical CWEs/Examples: Weak password policy, missing MFA for sensitive actions, page accessible without login, session fixation, insecure credential storage.
What you should check:
- Use robust authentication libraries; avoid custom home-built auth implementations.
- Enforce MFA for privileged or sensitive operations.
- Review session-management (timeout, invalidation after logout, secure cookies).
- Ensure credential storage uses best practices (salted hashes, no plaintext).
A08:2025 – Software or Data Integrity Failures
Focuses on failures to verify integrity of code, libraries, data, or configurations within the system, distinct but related to supply-chain vulnerabilties (A03).
Even if dependencies are trusted, if integrity checks are missing (unsigned updates, unchecked data deserialization), an attacker may insert malicious code or data flows.
Typical CWEs/Examples: Unsigned software updates, deserialization of untrusted data, manipulation of configuration files, loading of unverified plugins.
What you should check:
- Verify digital signatures and checksums in update mechanisms.
- Restrict deserialization of untrusted data or use safe serializers.
- Audit build and deploy pipelines to ensure integrity checks and artifact verification.
- Control plugin/extension usage and validate that they originate from trusted sources.
A09:2025 – Logging & Alerting Failures
At #9 in the OWASP Top 10 2025 list. Emphasises not just logging, but the alerting and monitoring side of security because logs without alerting and action are limited in value.
As environments grow complex (microservices, cloud, containers), it becomes harder to detect incidents unless logging, monitoring and alerting are integrated and acted upon. Under-represented in testing data but high in community concern.
Typical CWEs/Examples: Lack of logging of critical events, inability to change log level in production, absence of alert on suspicious events, missing link between logs and incident response.
What you should check:
- Ensure security events (authentication failures, privilege escalations, configuration changes) are logged reliably.
- Configure alerting rules (SIEM/IDS) to notify when suspicious patterns appear.
- Review retention and integrity of logs (immutable storage, audit trail).
- Integrate logging monitoring into your DevSecOps pipeline (e.g., detect anomaly post deployment) rather than leaving it only to ops.
A10:2025 – Mishandling of Exceptional Conditions
A new category for OWASP Top 10 2025. Focuses on how systems behave under abnormal conditions: exceptions, unexpected inputs, fail-open logic, error handling vulnerabilities.
Attackers increasingly exploit “edge cases” and “exception paths”; code paths that were not covered well in design/test. Systems fail safe? Fail open? The absence of oversight here is a growing risk.
Typical CWEs/Examples: Unhandled exceptions leading to stack traces disclosed, fallback logic that bypasses security controls, insecure default behavior on error, logic that grants access when an error occurs.
What you should check:
- Audit exception handling flows: what happens when things go wrong? Are security controls bypassed inadvertently?
- Review fallback or default logic to avoid “secure by default” becoming “fail-to-open”.
- Include error and abnormal-state flows in threat modelling and test them (fault injection, chaos testing).
- Ensure user-friendly errors don’t disclose sensitive internals (stack traces, system info).
OWASP Top 10:2025 – Category Breakdown and Security Focus
| Category | Focus | Key Checkpoints |
| Broken Access Control | Authorization & access logic | Role enforcement, SSRF, object references |
| Security Misconfiguration | Deployment/config stack | Default creds, cloud config, IaC |
| Supply Chain Failures | Dependencies & build/trust-chain | SBOM, pipeline integrity, third-party risk |
| Cryptographic Failures | Encryption/key management | Algorithm choice, key lifecycle, TLS usage |
| Injection | Interpreter misuse via untrusted input | Parameterised queries, escaping, input validation |
| Insecure Design | Architectural/business logic flaws | Threat modelling, misuse cases, design reviews |
| Authentication Failures | Identity & session management | MFA, session invalidation, credential storage |
| Software/Data Integrity Failures | Unverified code/data integrity | Signed updates, plugin verification, safe deserialization |
| Logging & Alerting Failures | Logging + actionable alerts | Event coverage, SIEM/monitoring, alert rules |
| Mishandling of Exceptional Conditions | Error-path, fail-open logic | Exception flows, fallback logic, chaos/fault testing |
AppTrana WAAP Coverage Across OWASP Top 10:2025
AppTrana WAAP delivers comprehensive protection across the updated OWASP Top 10:2025 risk categories through its unified, managed security platform. It safeguards against Broken Access Control and Authentication Failures with adaptive, behavior-based policies and managed rule tuning, while Injection and Security Misconfiguration risks are mitigated through its continuously updated, AI-driven WAF engine.
AppTrana’s integrated API discovery, bot management, and adaptive rate limiting defend against access abuse and volumetric attacks, while Cryptographic and Integrity Failures are addressed through enforced TLS, secure traffic inspection, and configuration validation. Its client-side protection module extends visibility and security beyond the server by detecting malicious JavaScript injections, preventing formjacking and Magecart-style attacks, and ensuring real-time integrity of third-party scripts. Backed by expert-managed security and intelligent risk scoring, AppTrana combines continuous visibility, automation, and human-in-the-loop tuning to deliver measurable, adaptive coverage against all major OWASP 2025 threats.


