API Security 101: Understanding the Risks and Implementing Best Practices
What is API Security?
API security refers to the practices and measures taken to protect APIs from unauthorized access, data breaches, and other security threats.
It includes authentication, encryption, input validation, rate limiting, monitoring, and secure coding practices to ensure the secure exchange of data between different software systems.
API security lies at the intersection of three broad security areas:
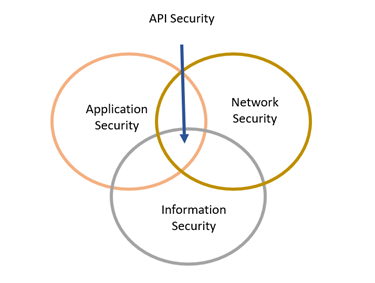
With sensitive data getting transferred via API, API security can guarantee the confidentiality of its message by making it available to the applications, users, and servers with proper permissions.
Similarly, securing APIs guarantees content integrity by ensuring the message has not been altered after transmission.
Learn how API security works in detail.
Why is API Security Important?
As organizations accelerate their digital transformation journeys, APIs have become the foundation for building interconnected applications, especially in cloud-native and microservices-based environments. However, this growing reliance introduces new risks and demands a dedicated security approach.
According to the State of Application Security Report by Indusface, the API threat landscape is rapidly evolving:
- API attacks surged by over 3000% YoY in India (Q3 2024), with 271 million attacks recorded in just one quarter.
- API-targeted DDoS attacks are 85% more frequent than those targeting websites.
- Bot attacks exploiting APIs increased by 145%, accounting for 215 million malicious incidents.
- Nearly 30% of critical API vulnerabilities remain unpatched for over six months.
These stats underscore the urgent need for robust API security measures. Here’s why it’s more critical than ever:
1. Integration Demands
As digital systems evolve, seamless integration between services becomes essential. APIs are the connectors, but they also become gateways for attackers if not secured properly. Weak APIs can expose sensitive data, leading to breaches.
2. Cloud Dependency
Modern cloud applications heavily rely on APIs for real-time data exchange and service interaction. A vulnerability in one API can ripple across the entire application stack, compromising overall cloud security.
3. Unique API Vulnerabilities
Traditional security solutions often fall short when it comes to APIs. APIs expose business logic, parameters, and endpoints in ways web apps don’t — making them a different class of target. Attackers exploit vulnerabilities such as broken authentication or improper authorization that are specific to APIs.
4. Complex Ecosystems
Microservices architecture means multiple services communicate via APIs. Every connection increases the attack surface. Without centralized visibility and control, securing these APIs becomes a significant challenge.
5. Expanded Attack Surface
Each API endpoint acts as a potential door for attackers. When organizations scale quickly, they often lose track of exposed endpoints, making them vulnerable to reconnaissance, injection, and DDoS attacks.
6. Inconsistent Security Practices
There’s often a lack of uniformity in how APIs are developed and secured across teams. This inconsistency leads to misconfigurations, insecure defaults, or unprotected endpoints.
7. External API Risks
Organizations frequently integrate third-party APIs (e.g., payment gateways, messaging services). If these are compromised, it can expose internal systems, even if the organization’s own APIs are secure.
How are APIs Abused?
By design, the Application Programming Interface is not insecure. However, the immense volume of API deployed has created challenges for the security team. Further, insufficient skills in API development and failure to incorporate the web and cloud API security rules may lead to vulnerable APIs. API vulnerabilities can be observed across various areas like data exposures, denial of service, authorization flaws, security misconfigurations, and endpoints (virtual environment, devices, servers, and more).
Likewise, attackers can use various other techniques to abuse APIs.
OWASP has listed the potential risks associated with APIs in its OWASP Top 10 API Risks list, which includes:
API1:2023 Broken Object Level Authorization – This vulnerability occurs when an API fails to adequately enforce access controls at the object level, allowing unauthorized users to manipulate object identifiers and gain unauthorized access to sensitive data within the system.
API2:2023 Broken Authentication – Broken Authentication happens when an API’s authentication mechanisms are compromised or improperly implemented, leading to unauthorized access and potential misuse of user accounts and sensitive information.
API3:2023 Broken Object Property Level Authorization – Similar to Broken Object Level Authorization, this vulnerability extends to the properties of objects. It occurs when an API does not properly control access to specific object properties, resulting in unauthorized access to sensitive data attributes.
API4:2023 Unrestricted Resource Consumption – This vulnerability arises when an API lacks proper resource consumption controls. Attackers may exploit this weakness to overwhelm the system’s resources, leading to denial-of-service scenarios or performance degradation.
API5:2023 Broken Function Level Authorization – Broken Function Level Authorization occurs when an API fails to adequately check whether a user has the required permissions to perform specific functions, allowing unauthorized access to critical functionalities.
API6:2023 Unrestricted Access to Sensitive Business Flows – This vulnerability implies that an API grants unrestricted access to sensitive business processes or workflows. Attackers can potentially exploit this to manipulate or disrupt critical business operations.
API7:2023 Server-Side Request Forgery (SSRF) – SSRF occurs when an API allows an attacker to make unauthorized requests to internal resources, potentially leading to information disclosure, data manipulation, or further exploitation of vulnerabilities within the network.
API8:2023 Security Misconfiguration – Security Misconfiguration happens when an API is not properly configured, leaving default settings, unnecessary services, or overly permissive access controls in place. This can expose sensitive data and increase the risk of unauthorized access.
API9:2023 Improper Inventory Management – This vulnerability relates to inadequate management of API-related assets and resources. Organizations may face risks if they lack awareness of all APIs or fail to implement proper controls over these assets.
API10:2023 Unsafe Consumption of APIs – Unsafe Consumption of APIs highlights vulnerabilities related to how APIs are used or consumed. This could involve inadequate input data validation, potentially leading to injection attacks, data breaches, or other security compromises.
API Security Breaches Examples
API security breaches can be particularly damaging as they expose sensitive data and functionality of an organization’s software systems to unauthorized users.
Here are some notable examples of API security breaches:
T-Mobile API Breach (2022): T-Mobile has reported a recent data breach where a threat actor accessed the personal information of 37 million current postpaid and prepaid customer accounts via one of its APIs.
LinkedIn API Breach (2021): In June 2021, a significant security breach occurred when a public API without authentication was exposed. It resulted in the compromise of data associated with 92 percent of its users. This allowed a malicious actor to scrape the platform for information on approximately 700 million users, including their email addresses and phone numbers.
Facebook Data Breach (2019): More than 530 million Facebook users’ personal information, such as phone numbers, account names, and Facebook IDs, was compromised in April 2019. The information was contained in two datasets from third-party Facebook applications that were publicly exposed. The attacker leveraged a vulnerability in the third-party developer’s API to carry out the attack. This allowed them to acquire access tokens and escalate their privileges to compromise the affected accounts.
Strava API Breach (2018): Strava, a fitness app widely used by military personnel to track their exercise routines inadvertently revealed sensitive information about military bases across the globe. This occurred as a result of a vulnerable API that transmitted users’ location data online.
Equifax API Breach (2017): Equifax, a credit reporting agency, experienced a massive data breach when hackers accessed sensitive data on over 143 million customers. The breach occurred due to a vulnerability in the company’s API, allowing attackers to access the data without proper authentication.
API Security vs. Application Security: What’s the difference?
Click here for a complete replay of the webinar “Comprehensive Risk-based API Protection.”
As this short clip illustrates, API security is more than web security. API security shares many of the same principles as web security. However, securing APIs presents unique challenges that require specialized security measures.
APIs are often accessed over the web and use HTTP as the underlying protocol. As a result, many of the same security principles that apply to web security also apply to API security.
For example, API security involves protecting against SQL Injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) and other common API attacks.
API security also involves using secure communication protocols such as HTTPS to protect data in transit, which is also an important part of web security.
However, some unique API security issues extend beyond the realm of web security.
One of the biggest API security challenges is that APIs are often designed to be accessible by third-party applications or services. This means that APIs are exposed to a wider range of potential attackers than traditional web applications. Attackers can use APIs to exploit vulnerabilities in the application, steal sensitive data, or launch attacks against other applications or services.
Another challenge of API protection is that APIs are often designed to be highly flexible and customizable, making them more vulnerable to attacks. For example, APIs may allow users to specify the data type they want to receive or the format in which the data is returned. This flexibility can make it easier for attackers to exploit API code or configuration vulnerabilities.
API protection also presents challenges when it comes to authentication and access control. APIs often use tokens or other authentication forms to control API access. However, these tokens can be stolen or compromised, allowing attackers to access the API and its data.
Finally, API security can be challenging because of the sheer number of APIs used in modern software systems. Applications may use dozens or hundreds of APIs to communicate with other applications or services. This makes it difficult to monitor and protect APIs effectively.
Uncover the best 15 API security tools of 2024 and their key features, benefits, and limitations
Is an API Gateway Enough to Ensure Robust API Security?
An API gateway is essential in securing APIs, but it is not enough to ensure robust API security on its own.An API gateway can provide some security features, such as
- Rate limiting and throttling to ensure APIs aren’t overused and/or abused
- The authorization and routing of API calls to the right backend services and frontend endpoints
- Access management to prevent abuses and ensure only authorized entities access different functionalities
- Authentication through credential and token validation to verify identities
- Analytics, monitoring, logging, and alerts
However, it is still vulnerable to various attacks. An API gateway covers only the endpoints and does not cover every layer of advanced API security.
Check out why you need an API security solution even if you have API Gateway:
Some instances where API gateway security is found wanting are:
- It doesn’t provide visibility and control over the entire API architecture
- It doesn’t unearth misconfigured, rogue, or shadow APIs, leaving them open for attackers to find and exploit
- It cannot effectively distinguish between human and bot activity. Given how sophisticated today’s bots are, they cannot thwart complex and highly damaging API-specific bot attacks
- It is not equipped to stop advanced, multi-vector DDoS attacks
- To ensure robust API security, it is essential to implement a defense-in-depth strategy, including multiple security control layers
Top 10 API Security Best Practices Checklist
As attackers continue to expose and exploit the weaknesses in APIs, the need for API security is urgent and critical. Use this API security checklist to start solidifying your API security posture.
1. API Discovery and Inventorying
API discovery is critical to API security, as understanding the APIs present in a system is fundamental to securing them effectively. Security vulnerabilities often arise when organizations are unaware of all the APIs in their ecosystem or are not properly documented and managed.
Best practices for API discovery in the context of API security:
- Keep an updated list of all APIs, including details like names, versions, endpoints, and authentication methods.
- Employ tools to automatically scan networks, code repositories, and documentation for API identification.
- Ensure comprehensive and standardized API documentation to aid developers and security teams.
- Implement versioning for APIs and establish clear policies for deprecating older versions to ensure security updates.
- Set up continuous monitoring for API activities with alerts for suspicious behaviour to detect security incidents promptly
2. Implement A Zero Trust Philosophy
When considering the concept of API security, while many emphasize API authentication, the essence of API security lies more in API threat prevention.
Zero Trust is a security policy that states that companies should not trust anyone by default and must verify everything when accessing their systems.
Zero-Trust ideology should be applied to even authorized API endpoints, authenticated clients, and unauthenticated and unauthorized entities.
Consider this checklist while implementing a zero-trust policy on your API include:
- Ensure HTTPS or other secure protocols for data in transit.
- Thoroughly analyze API requests for potential threats.
- Follow secure deployment practices in cloud environments.
- Implement measures like encryption and access controls to prevent data leakage.
- Stay updated on security threats through threat intelligence feeds.
- Set up robust logging and monitoring for proactive threat detection.
3. Identify API Vulnerabilities and Associated Risks
Ensuring robust API security involves proactively detecting and protecting against potential threats. Neglecting API vulnerabilities can pose significant risks. Follow these guidelines for effective API threat prevention:
- Employ behavioural, pattern, and heuristic analysis for proactive threat detection, surpassing reliance on basic signature-based methods.
- Implement multi-layered security measures to safeguard APIs from various threats, including DDoS attacks, bot attacks, and vulnerabilities outlined in the OWASP Top 10 API security risks.
- Harness advanced technologies like self-learning AI, analytics, and automation to elevate API protection.
- Maintain real-time visibility into the security posture of your APIs.
- Strengthen API protection by encrypting all data transmitted.
- Deploy virtual patching to secure vulnerabilities until developers can address them.
- Before making any code changes, assess API endpoints to ensure compliance with data handling requirements and maintain security standards.
Continuous security testing is crucial for a comprehensive API security checklist. Through thorough testing, identify vulnerable aspects of your API.
It’s important to note that while automated scanning is valuable, it has limitations and may not catch security misconfigurations or business logic flaws.
Regular manual security testing conducted by certified experts through penetration tests and audits is vital to address potential gaps and ensure a robust security posture.
For a detailed guide on API penetration testing best practices, refer to our API Penetration Testing Checklist blog.
4. Enforce Strong Authentication and Authorization
Though authentication and authorization play different roles, these two API best practices work as powerful tools for API protection when implemented together.
Authentication is necessary for securely verifying the user of the API. Authorization is concerned with what data they have access to.
API authentication allows to restriction or removal of users who abuse the API. API authorization usually starts after the identity is confirmed through authentication and verifies whether users or applications can access the API.
API authentication and authorization serve the following purposes:
- Authenticate calls to the API to legitimate users only
- Track the requesters
- Track API usage
- Enable different levels of permissions for different users
- Block the requester who exceeds the rate limit
API Best practices for authentication and authorization
- Include human and machine identities while implementing access controls and authentication. Do not forget third-party applications and services.
- Use modern authorization protocols for robust security.
- Public APIs should not be exposed to unvalidated requests, even if the users are authorized.
- Implement strong and complex passwords in combination with multifactor authentication.
- Non-admin users should only be granted read-only privileges to data.
- Sessions must have a limited duration.
- Tokens must expire at regular intervals to prevent replay attacks.
Here’s how to implement strong authentication mechanisms for APIs.
5. Expose Only Limited Data
When we think of web API security best practices, we often think of blocking out malicious activity. It is also vital to limit the accidental exposure of sensitive information.
As APIs are a developer’s tool, they often include passwords, keys, and other secret information that reveals too many details about the API endpoints.
Ensure APIs only expose as much data as needed to fulfill their operation. Further, enforce data access controls and the principle of least privilege at the API level, track data, and conceal if the response exposes confidential data.
Consider the following checklist points to ensure limited data exposure:
- Expose only the minimum necessary data for API operations.
- Track and conceal any inadvertent exposure of confidential data in API responses.
- Conduct periodic audits to identify and address inadvertent data exposure.
- Conceal sensitive data in API responses, especially for non-privileged users.
- Protect passwords, keys, and secrets with secure management practices.
- Conduct frequent security reviews to assess data exposure risks and refine access controls.
6. Implement Rate Limits
DDoS (Distributed Denial of Service) is the most common practice of attacking an API by overwhelming it with an unlimited API request. This attack affects the availability and performance of APIs.
Rate limiting, also known as API limiting, enforces a limit on how often an API is called (to ensure that an API remains available to legitimate requests). Beyond DDoS attack mitigation, it limits abusive actions like aggressive polling, credential stuffing, and rapidly updating configurations. API rate limiting not only deals with fair usage of shared resources but also can be used to:
- Implement different access levels on API– based services
- Meter the API usage
- Guarantee API performance
- Ensure system availability
API rate limiting checklist:
- Specify rate limits for each API endpoint, indicating the maximum number of requests allowed within a defined time window.
- Implement a mechanism to gracefully handle requests that exceed rate limits, returning appropriate HTTP status codes and error messages.
- Tailor rate limits based on the criticality of specific API endpoints.
- Implement logging and monitoring API usage and rate-limiting events for proactive issue identification and troubleshooting.
- Review and adjust rate limits periodically based on changing usage patterns, business requirements, and API performance.
7. API Design and Development
Due to developers’ pressure to ensure speed to market, they often do not have time for security testing. Further, they tend to deploy APIs with known vulnerabilities and dark spots for future functionalities, leave old versions deployed for backward compatibility, etc.
So, API security should not be limited to production. An advanced API security tactic is implementing security controls and techniques from the design and development stages.
Embed these best practices into your API security checklist to systematically identify and rectify misconfigurations.
- Build secure-by-design APIs
- Use secure development frameworks, code, templates, libraries, and so on
- Restrict source code accessibility to only those who need it
- Review design and code for flaws, especially those related to business logic
- Include security configuration checks in your API security checklist to root out misconfigurations
- Look for hidden form fields and document API response
8. API Logging and Monitoring
Logging and monitoring APIs help construct a baseline for what is considered ‘normal’ so that outlier incidents can be quickly detected.
To enhance API security, consider the following practices:
- Identify and clearly define all elements, infrastructure, and apps that must be logged.
- Track and log non-security parameters such as API performance, speed, and uptime.
- Regularly review anomalies in the logged data and tune your APIs accordingly, aligning with best practices for API security.
9. Incidence Response
Detecting and stopping breaches has been just a part of the security response. Data breaches, at times, are unavoidable. In such cases, having a robust incident response plan is essential as it enables organizations to bounce back quickly and minimize the impact of breaches.
It should clearly define the policies and measures related to immediate response, investigation, forensics, escalation, compliance, etc.
Incident Response Best Practices
- Develop a clear plan covering immediate response, investigation, forensics, escalation, and compliance.
- Conduct tests and drills to ensure the effectiveness of the response plan.
- Foster collaboration between IT, security, legal, and relevant teams.
- Document response activities and establish clear communication channels.
- Ensure compliance with legal and regulatory requirements.
- Analyze incidents, identify root causes, and implement preventive measures.
10. Implement Web Application and API Protection (WAAP)
We recommend a Web Application and API Protection (WAAP) solution for business use cases where API calls are made from the web and mobile apps. These apps commonly have access to ample amounts of sensitive information, and APIs in these channels is tough to defend.
Common security tools like traditional firewalls and API gateways are insufficient to prevent API attacks. WAAP solution is centered around four consolidated capabilities: DDoS protection, Web Application Firewall, Bot Management, and API protection.
It employs a fully managed and risk-based application security approach by monitoring traffic to detect abnormal activities and malicious traffic across all four vectors. The data collected across all the applications assess risks and update mitigation strategies to enhance cyber defense in real-time.
WAAP also aids in reducing operational complexity by reducing the number of parameters that need to be managed, streamlining security rulesets, and automatically suggesting rules with their AI capabilities.
While WAF protects against OWASP top 10 attacks and API gateway defends against standard attacks, AI-enabled behavioral analysis of WAAP ensures the defense against automated and more sophisticated attacks.
As APIs become a strategic necessity to offer your business the speed and agility needed to succeed, your goal should be defending them from evolving attacks.
With Indusface WAAP, keep API threats and malicious bots at bay. Our AppTrana platform ensures that your API is highly available and guarantees the confidentiality and integrity of the data it processes.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 December 15, 2023
December 15, 2023





