API Discovery 101: Importance, Steps, and AppTrana WAAP Capabilities
APIs are now among the most targeted components in modern web applications. According to the State of Application Security Report 2025 APIs experienced 43% more attacks per host compared to websites and suffered 166% higher rates of DDoS attacks.
This rising trend is not just about quantity. As applications grow more interconnected, organizations often lose sight of what APIs they have deployed, who is accessing them, and how they behave. This creates blind spots, which attackers can exploit easily.
The solution lies in API discovery, a crucial security practice that brings clarity and control to your API landscape.
What is API Discovery?
API discovery is the process of identifying and cataloging all APIs used within your organization. The goal is to build a complete and accurate inventory of your APIs, which forms the foundation for strengthening security controls, understanding risk exposure, enforcing compliance, and detecting anomalies and threats.
Without this visibility, your security teams are blind to a growing part of your application.
Why is API Discovery Essential for API Security?
Let’s start with a simple question: Do you really know all your APIs?
Consider these prompts:
- How many APIs are currently active in your organization?
- How often are these APIs updated?
- What happens to old versions when a new one is released?
- Have developers built unofficial APIs to bypass processes or speed up work?
These unknowns represent real, exploitable gaps in your defenses. According to OWASP’s API Security Top 10, poor API management leads to vulnerabilities like broken authorization, excessive data exposure, and improper asset management. API discovery addresses these risks at the root.
Common API Threats Linked to Poor Discovery
Shadow APIs
Shadow APIs are undocumented or unmanaged APIs that operate outside the purview of the security team. They often arise during development or due to miscommunication between teams.
Recent research found that 31 percent of 16.7 billion malicious API requests targeted shadow APIs. That is over 5 billion requests slipping past conventional monitoring. Because these APIs are not included in standard security tests or controls, they become ideal targets for attackers.
Zombie APIs
Zombie APIs are outdated endpoints that were never properly decommissioned after a newer version went live. While everyone assumes they are gone, they continue to run, often without updates, patches, or even authentication.
For example, an organization may upgrade from v4/profile/edit (no auth) to v17/profile/edit (secure). But if v4 remains active, attackers can exploit it to bypass all security. These forgotten endpoints are particularly risky because they are easily overlooked.
Rogue APIs
Rogue APIs are created without formal approval or oversight, usually by developers or third-party vendors trying to bypass long approval processes. They are rarely documented, not included in compliance checks, and often lack basic security hygiene. Worse, they may interact with sensitive internal systems.
For example, a third-party mobile app may integrate with your backend without authorization, accessing user data, and sending it to external servers.
The Role of API Discovery in Security Strategy
An effective API discovery strategy enables security teams to:
- Detect and decommission unused or unauthorized APIs such as shadow, zombie, and rogue APIs
- Classify APIs by risk based on data sensitivity and exposure
- Apply tailored security controls like rate limiting, authentication, and access policies
- Continuously monitor for suspicious usage or configuration changes
- Maintain compliance with security frameworks and regulatory requirements like GDPR, HIPAA, or PCI-DSS
API Discovery Must Be Continuous
Many organizations treat discovery as a one-time event, but that is a dangerous approach. API ecosystems are dynamic. New APIs are added regularly, old ones evolve or get deprecated, and integrations shift constantly. Automated and continuous discovery is the only way to keep pace with this change.
How AppTrana WAAP Strengthens API Discovery and Security
Traditional API security often starts too late, only after APIs are in production and potentially exposed. AppTrana API Protection shifts this approach by integrating continuous and intelligent API discovery into the heart of its protection model. Here is how AppTrana transforms API discovery into a strategic security advantage:
AppTrana inspects all incoming traffic and automatically detects new or changed APIs. It builds a real-time inventory across all domains, capturing:
- Documented APIs: Those with published Swagger/OpenAPI specifications.
- Shadow APIs: Active but undocumented APIs that may have bypassed development or security reviews.
- Zombie APIs: Deprecated or old APIs that remain accessible but unprotected.
By identifying these API types automatically, AppTrana ensures no endpoint remains hidden or unmonitored.
1. Smart Identification and Classification
AppTrana identifies APIs using the method and URI path combination. For instance:
- GET /api/v1/orders
- POST /api/v1/orders
These are treated as two distinct APIs. For endpoints with dynamic path parameters, such as /api/v1/orders/123, AppTrana generalizes them as /api/v1/orders/{integer_param1}. This parameterized abstraction helps group similar APIs and analyze them at scale.
It also classifies APIs by usage type, such as admin, customer, or internal APIs, making it easier to assign ownership, assess exposure, and prioritize protection.
2. Visibility into Behavior and Metadata
AppTrana goes beyond simple discovery. It collects detailed behavioral insights for each API, including:
- Request and response body content
- Query and path parameters
- Method type (GET, POST, PUT, DELETE, etc.)
- API authentication status
- Deprecated indicators
- Presence of sensitive data like PII
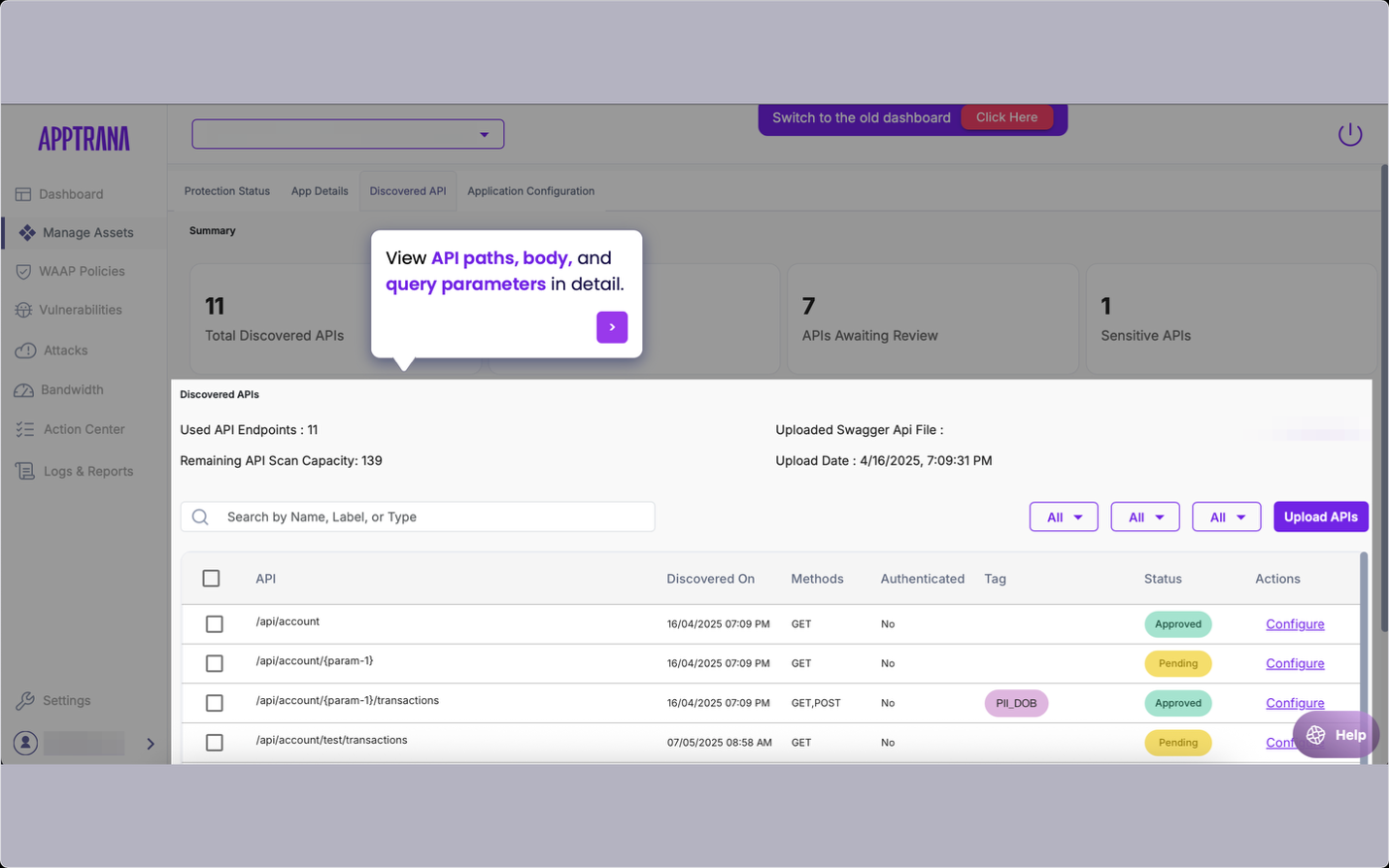
This rich metadata helps teams understand the risk level of each API, especially those handling personal or financial data.
3. Instant Security Enforcement with Positive Security Model
When a new API is discovered, AppTrana allows users to take immediate action:
- Approve the API to enforce positive security rules.
- Block the API if it is unauthorized or suspicious.
- Deprecate unused or outdated APIs.
Upon approval, you can apply the Positive Security Model, which enforces strict controls based on the API’s parameters:
- Block new methods that were not part of the original spec.
- Enforce path parameters to prevent misuse of dynamic URLs.
- Enforce query and body parameters to ensure only allowed inputs are accepted.
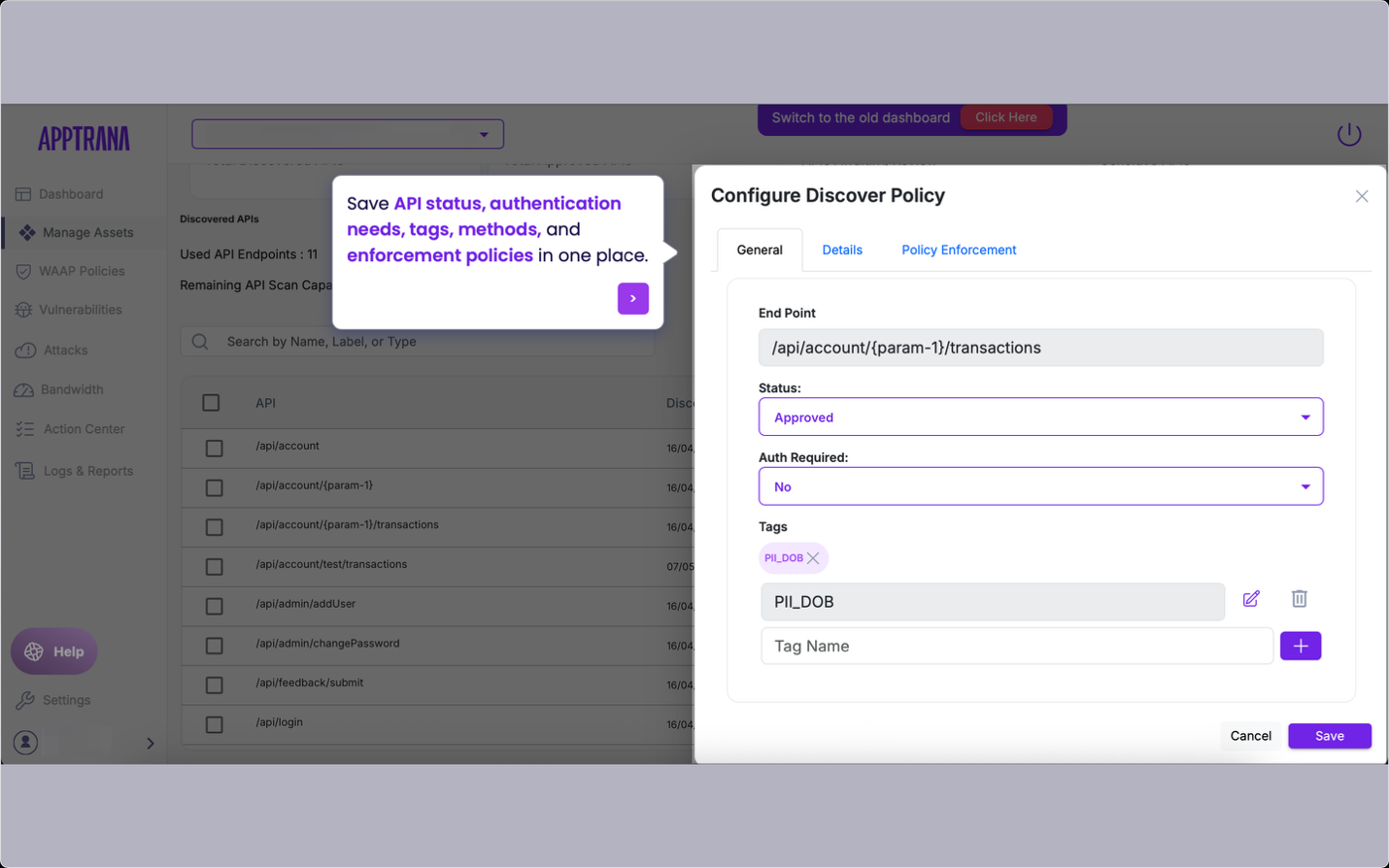
This proactive enforcement helps neutralize attacks such as injection, unauthorized access, and abuse of business logic.
4. Risk-Based Classification for Prioritization
AppTrana does not treat all APIs equally. It assigns risk levels based on:
- Whether authentication is required
- Type of data handled (public, internal, PII, payment)
- Frequency and volume of usage
- Anomalies in API behavior
This helps security teams focus on securing high-impact and high-risk APIs first, rather than spreading efforts thin across the entire API ecosystem.
5. Change Tracking and Version Control
AppTrana automatically detects when an existing API changes, such as a new method being added or a parameter being modified. It flags these changes in the dashboard, helping avoid:
- Regression vulnerabilities
- Gaps in security enforcement due to silent updates
- Misalignment between production and documented APIs
This real-time change tracking keeps security measures tightly aligned with application updates.
6. Bulk Management and Exporting
Managing hundreds of APIs across multiple teams and domains is challenging. AppTrana provides bulk actions to:
- Approve or block multiple APIs at once
- Export the API inventory for offline review
- Sync discovered APIs with your existing Swagger or OpenAPI files
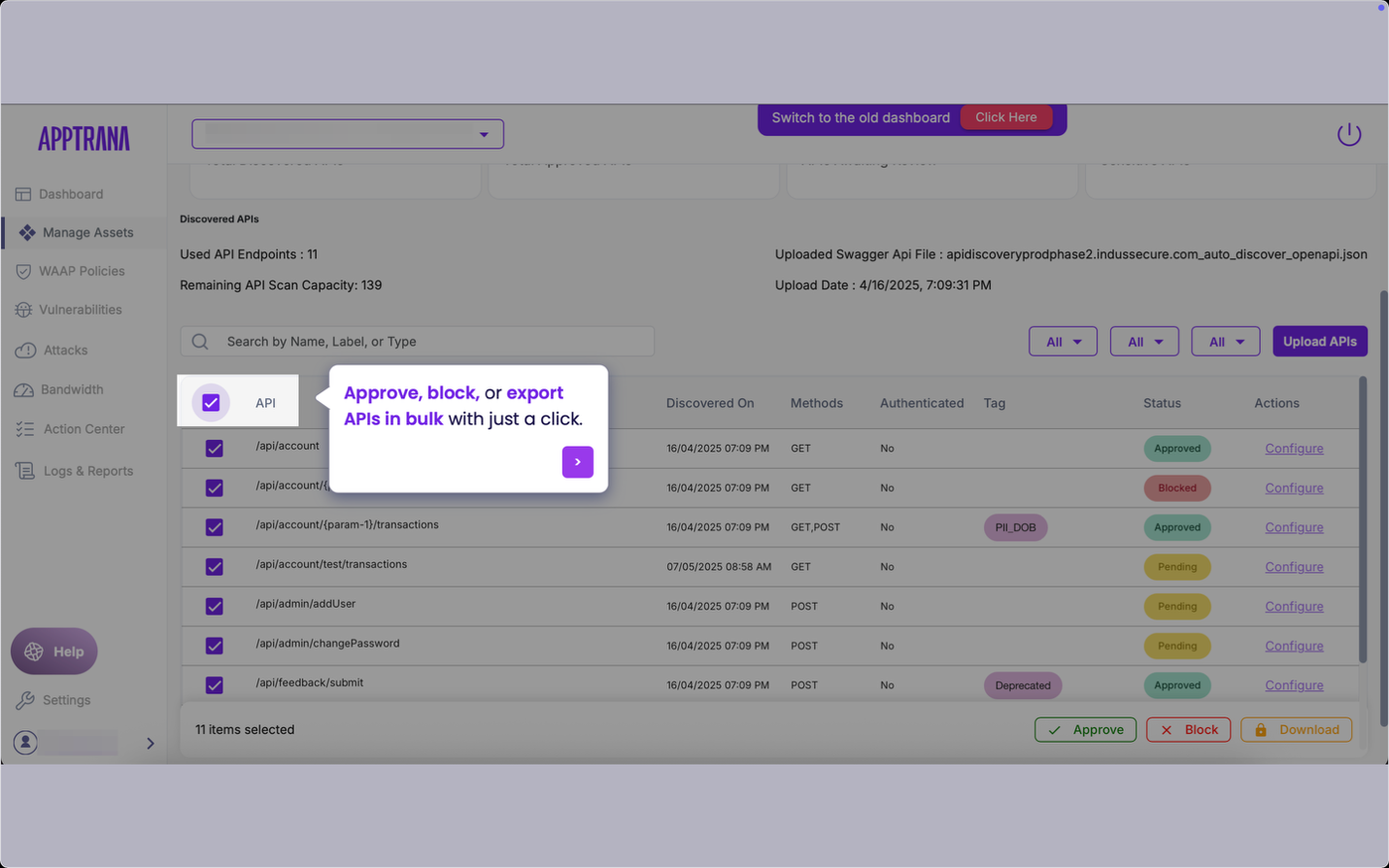
This makes the tool scalable for large enterprises and supports collaboration between security and development teams.
7. Real-Time Dashboard for Monitoring and Decision-Making
AppTrana includes a powerful dashboard that provides a live view of:
- Total APIs discovered
- Approved and blocked APIs
- Sensitive APIs handling PII or payment data
- APIs awaiting security review
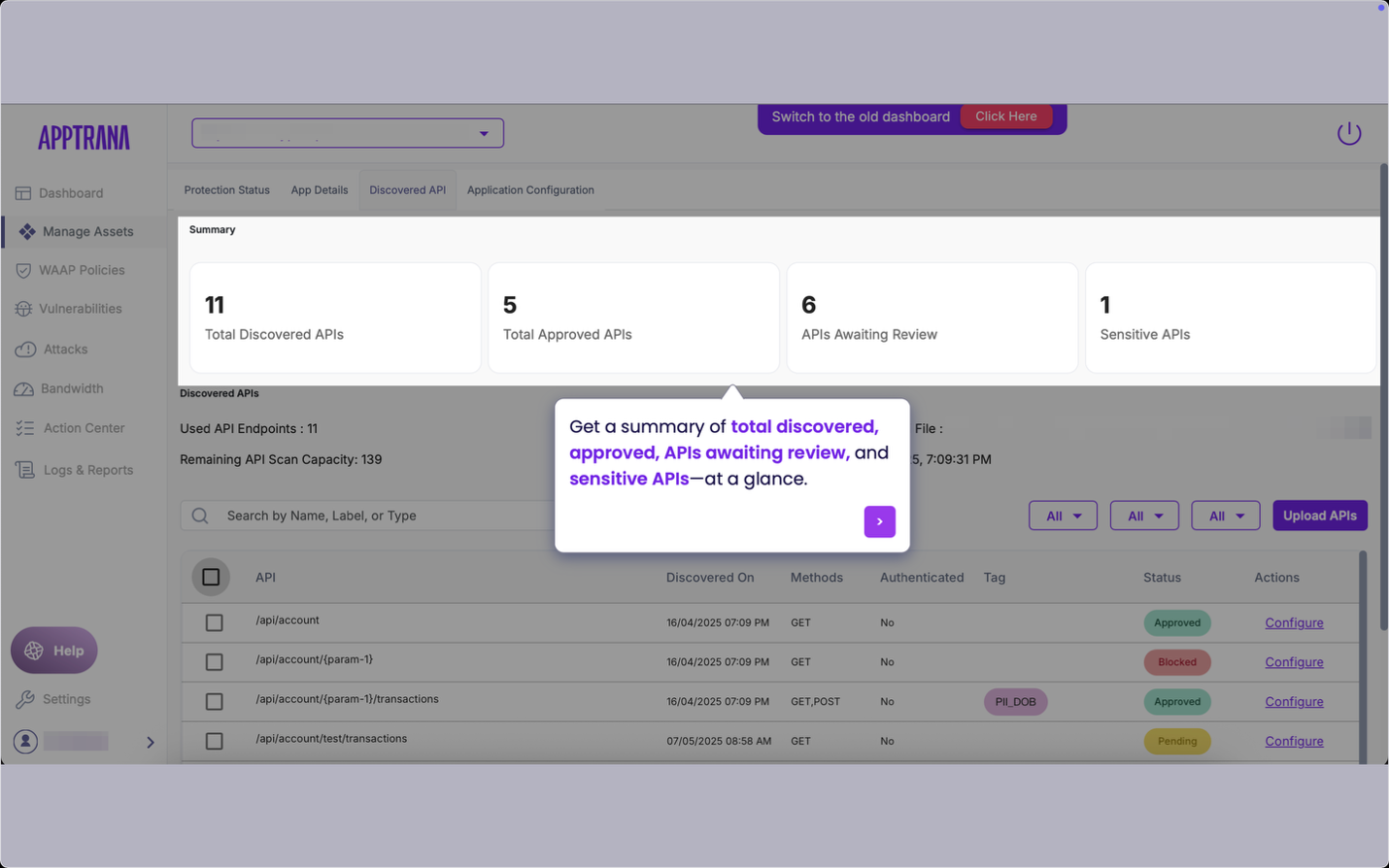
It also includes analytics on API traffic patterns, attack trends, and misconfiguration alerts, empowering teams to make data-driven security decisions.
8. Built-In Defense Against OWASP API Top 10 Vulnerabilities
AppTrana’s discovery, classification, and enforcement workflows are designed to directly reduce the risks outlined in the OWASP API Security Top 10. For example:
- API10:2023 – Unsafe Consumption of APIs: Prevents blind trust in third-party APIs by blocking unknown endpoints and enforcing schema validations.
- API9 – Improper Inventory Management: Keeps a centralized, continuously updated inventory to avoid shadow, zombie, and rogue APIs.
- API1 – Broken Object Level Authorization: Allows tight controls over path parameters and access permissions for each endpoint.
By providing discovery, vulnerability scanning and protection in a single platform, AppTrana provides a single pane of glass view on API endpoints, their vulnerabilities and protection status.
In an era where attackers target APIs more aggressively than websites, API discovery is the first and most crucial defense layer. AppTrana ensures that defense is continuous, intelligent, and actionable.
Curious how AppTrana helps uncover hidden APIs, enforce OWASP protections, and maintain a live inventory, all in one platform?
Experience it yourself in this interactive demo.
Whether you are building new APIs or securing legacy infrastructure, AppTrana WAAP empowers your teams with the visibility and control needed to protect what matters most.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 June 19, 2025
June 19, 2025




