Website Security – 10 Effective Website Protection Strategies
In 2023 alone, the global landscape faced a staggering 6.8 billion cyberattacks on websites, underlining the critical need for robust security measures.
Banking, finance, and insurance sectors witnessed over 90% bot attacks, while healthcare sites experienced a 100% bot attack rate.
These alarming statistics highlight the urgent need for robust website security measures. This blog explores the fundamentals of website protection and best practices to secure your website.
What is Website Security?
Website security refers to implementing measures to protect a website from unauthorized access, data theft, and other malicious activities. It encompasses various techniques, tools, and best practices to mitigate vulnerabilities and ensure online resources’ confidentiality, integrity, and availability.
By adopting robust security measures, you can effectively secure your website from various threats, including:
Malware Infections: Malicious software is designed to compromise website functionality, steal data, or facilitate unauthorized access.
DDoS Attacks: Distributed Denial of Service attacks overwhelm a website’s servers, rendering it inaccessible to legitimate users.
SQL Injection: Exploiting vulnerabilities in web applications to execute malicious SQL commands, enabling attackers to access, modify, or delete sensitive data.
Cross-Site Scripting (XSS): Injecting malicious scripts into web pages viewed by other users, allowing attackers to steal cookies, session tokens, or other sensitive information.
Brute Force Attacks: Attempting to gain unauthorized access to a website by systematically trying various username and password combinations.
Check out our in-depth blog to discover the top website security threats and learn the solutions to mitigate their impact.
Why Does Your Business Need Website Security?
Ensuring the security of your business website is not just a matter of protecting against cyber threats; it’s a crucial investment in your company’s longevity and reputation.
With the global cost of cybercrime expected to reach a staggering $10.5 trillion by 2025, neglecting website security is simply not an option.
Consider the case of the Canada Revenue Agency in August 2021, where a password cyber-attack shut down their online systems for several days and compromised over 5000 accounts.
This incident, caused by credential stuffing, highlights the risks of overlooking web security measures.
Here’s why website protection is indispensable for your business:
Protecting Sensitive Data: Websites often store valuable information, including customer data, payment details, and intellectual property. Implementing robust security measures is vital to defend this sensitive information from unauthorized access or theft.
Preserving Reputation and Trust: A security breach can severely affect a business’s reputation and erode customer trust. By prioritizing website protection, businesses demonstrate their commitment to protecting customer data and maintaining a secure online environment.
Regulatory Compliance: Many industries are subject to regulatory requirements governing data protection and security. Failure to comply with these regulations can result in hefty fines, legal liabilities, and damage to brand reputation. Implementing comprehensive website security measures ensures compliance with relevant regulations and standards.
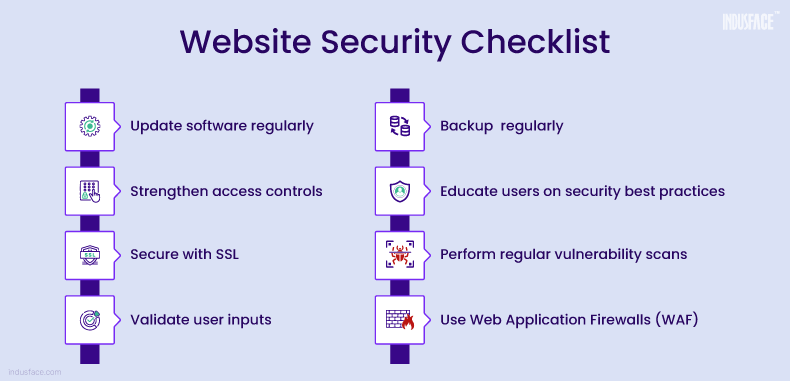
Website Protection Checklist: 10 Key Steps to Secure Your Site
To help you secure your website, we’ve compiled a comprehensive checklist of essential web security strategies.
1. Security from Web Development Stages
Web security begins at the development stage, where vulnerabilities can arise due to insecure coding practices, framework choices, and configuration errors.
To ensure robust security:
Choose Secure Frameworks: Opt for frameworks with a strong security track record and active community support. Conduct thorough research to identify frameworks with known vulnerabilities and select ones that prioritize security.
Adopt Secure Coding Practices: Train developers on secure coding practices, such as input validation, output encoding, and parameterized queries, to mitigate common vulnerabilities like SQL injection and cross-site scripting (XSS).
Conduct Security-Focused Testing: Integrate security testing into the development process, including static code analysis, dynamic application security testing (DAST), and penetration testing, to identify and remediate vulnerabilities early.
2. Keep Software Updated
It is obvious yet overlooked. Regularly updating software is a simple yet effective website security measure.
Prioritize updates for the following:
- Server Operating Systems: Apply security patches promptly to address known vulnerabilities.
- Content Management Systems (CMS): Keep your CMS up to date to prevent exploitation of known security flaws.
- Third-Party Applications: Update all software used on your website, including plugins and themes, to mitigate the risk of attacks targeting vulnerable versions.
3.Strong Access Control
Implementing robust access controls helps prevent unauthorized access to sensitive areas of your website reducing the likelihood of website security mistakes.
Key access control measures include:
- Multi-Factor Authentication (MFA): Require users to provide multiple forms of identification before accessing privileged accounts.
- Role-Based Access Control (RBAC): Assign users to specific roles with predefined access privileges based on their responsibilities.
- Limit Login Attempts: Implement measures to thwart brute force attacks by restricting the number of login attempts.
- Automatic Logout/Session Expiry: Enforce session timeouts to mitigate the risk of session hijacking.
- Secure File Uploads: Restrict file uploads to trusted users and validate uploaded files to prevent the execution of malicious scripts or unauthorized access to the server.
4. Install SSL
Securing data in transit is essential to prevent interception and tampering against potential website security mistakes.
- HTTPS Protocol: Encrypt communication between the server and the client to protect sensitive information from eavesdropping.
- Trust and Credibility: Displaying the padlock icon and HTTPS in the URL instills confidence in users and improves trust in your website.
- SSL Certificate Management: Regularly renew SSL certificates and configure them to adhere to industry best practices, such as using strong encryption algorithms and disabling deprecated protocols.
5. Continuous Vulnerability Scanning and Penetration Testing
Regularly scan your website for vulnerabilities and conduct penetration tests to identify and remediate security weaknesses:
- Automated Vulnerability Scanning: Deploy automated vulnerability scanning tools to continuously monitor your website for known security issues, such as OWASP Top 10 vulnerabilities, and prioritize remediation efforts based on risk severity.
- Periodic Penetration Testing: Conduct periodic penetration tests by skilled security professionals to simulate real-world attacks and identify complex security flaws that automated scanners may miss.
Indusface WAS Basic Scanning (Free Forever) conducts biweekly security scans focusing on the OWASP Top 10 and SANS Top 25 vulnerabilities.
Additionally, authenticated scans uncover 2X number of vulnerabilities. In the premium plan, you also have access to managed services and manual penetration testing options.
6. Input Sanitization and Validation
Prevent injection attacks and other vulnerabilities by thoroughly validating and sanitizing user inputs:
- Input Validation: Validate user input to ensure it adheres to expected formats and reject any input that contains potentially malicious content, such as SQL injection payloads or XSS scripts.
- Output Encoding: Encode user-supplied data before displaying it on web pages to prevent XSS attacks and ensure that user-controlled content is treated as data, not executable code.
7. Password Security Best Practices
If you’re wondering how to secure your website from hackers, start by focusing on your passwords. They’re often the first line of defense against unauthorized access.
- Enforce Strong Password Policies: Require users to create complex passwords containing a mix of uppercase and lowercase letters, numbers, and special characters, and enforce password length and complexity requirements.
- Hashing and Salting: Hash user passwords using strong cryptographic algorithms like SHA and add a unique salt to each password before hashing to protect against rainbow table attacks.
8. Monitoring Traffic Surges
Keeping a vigilant eye on website traffic patterns is crucial for detecting and mitigating DDoS attacks and other malicious activities. Here’s how to effectively monitor traffic surges:
- Real-time Monitoring: Utilize web traffic monitoring tools to continuously monitor incoming traffic in real-time. Set up alerts for unusual spikes or patterns that may indicate a potential attack.
- Traffic Analysis: Analyze traffic data to identify legitimate users versus suspicious or malicious bots. Look for patterns such as unusually high request rates from specific IP addresses or geographical regions.
- Rate Limiting: Implement rate-limiting measures to restrict the number of requests from individual IP addresses or user agents, preventing excessive traffic from overwhelming the website.
- DDoS Mitigation Services: Consider using DDoS mitigation services provided by specialized vendors or cloud service providers. These services employ advanced traffic filtering and mitigation techniques to protect against large-scale DDoS attacks.
Learn about the best practices for DDoS protection in our comprehensive guide on mitigating DDoS attacks.
9. Content Delivery Networks (CDNs)
Content Delivery Networks (CDNs) play a vital role in enhancing website protection by optimizing content delivery and mitigating certain types of attacks. Here’s how CDNs contribute to the website security:
- Distributed Caching: CDNs cache website content on geographically distributed servers, reducing latency and improving website performance for users worldwide. By serving content from edge servers closer to the end users, CDNs minimize the impact of DDoS attacks and improve website availability.
- Traffic Offloading: CDNs offload a significant portion of incoming traffic from the origin server, reducing the load and potential strain on the infrastructure during traffic surges or DDoS attacks. This helps maintain website uptime and performance even under heavy loads.
10. Implement Web Application Firewall (WAF)
A WAF serves as a critical component of defense against web-based attacks, offering the following benefits:
- Real-Time Threat Protection: WAFs inspect incoming web traffic in real time, identifying and blocking malicious requests before they reach the web server.
- Behavioral Analysis: Advanced WAFs leverage behavioral analysis and machine learning algorithms to detect anomalous traffic patterns indicative of sophisticated attacks, providing proactive threat mitigation.
- Granular Control: WAFs allow administrators to define custom security rules and policies based on specific application requirements and attack patterns, providing granular control over security posture.
- Virtual Patching: When immediate patching is impractical, WAFs offer virtual patches by blocking known exploit patterns and vulnerabilities, reducing risk until underlying issues are resolved.
According to our AppSec report, 31% of vulnerabilities remain unresolved after 180 days. Failure to address these vulnerabilities promptly leads to compliance issues and exposes businesses to more severe exploits, jeopardizing data, reputation, and overall business integrity.
AppTrana WAAP’s SwyftComply significantly reduces vulnerability windows from over 180 days to just 72 hours, ensuring rapid compliance with a “Clean, Zero vulnerability report.”
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 February 27, 2024
February 27, 2024