New Black Basta Ransomware Attack Brings Down 50 Organizations Globally
As hackers found more and more ways to exploit information security loopholes, they started using a new strain of ransomware called “Black Basta” ransomware virus.
While the linkages are yet to gain momentum as regular patterns, it’d be worth observing to see how a new threat as Black Basta could become a huge problem for your enterprise.
What is Black Basta Ransomware?
The Black Basta is a program that steals confidential data, encrypts the data before exfiltration, and then threatens victims with the public release of decrypted stolen data.
“Since Black Basta is relatively new, not a lot is known about the group. Due to their rapid ascension and the precision of their attacks, Black Basta is likely operated by former members of the defunct Conti and REvil gangs, the two most profitable ransomware gangs in 2021.”
Lior Div, Cybereason CEO and Co-founder
Black Basta’s rise on the ransomware scene happened swiftly, from a little-known player at the beginning of February to the most notorious ransomware group by the end of April. In April 2022, user Black Basta advertised its intention to buy and monetize corporate network access credentials for a share of the profits on underground forums known for hosting questionable material.
They are considered a higher threat than some other groups because they first use data extraction (exfiltration) before deploying their other malicious attacks.
50 businesses have already been affected by the Black Basta ransomware group since its inception earlier this year. They have demanded as much as $2M from some companies.
These companies originate from several countries, including Australia, Canada, New Zealand, and the US, where most victims are located. This group has only been active for less than a year, and as seen from these numbers, it is already impacting companies.
How Does Black Basta Ransomware Attacks Work?
Black Basta leverages a double extortion scheme involving two parallel attacks. First, it steals confidential data and dumps it on the cyber-locker before encrypting its contents. This allows these criminals to threaten victims with the public release of their valuable information without actually releasing it to the media or making good on that promise.
Step 1:
Black Basta ransomware needs administrative privileges to run. The Black Basta ransomware attack is using a modular information stealer, QakBot, using Windows Management Instrumentation to help it spread laterally through an organization, perform reconnaissance, gain access to data and execute the payload.
QB can act as a reconnaissance robot, collecting details about an environment; it can then gain access to that environment and return with data and credentials to hand over. From there, it can access areas laterally, taking more information and planting more infected systems.
Step 2:
Getting harvesting credentials and a thorough knowledge of network architecture from QaBot, the Black Basta ransomware aims at the Domain Controller of a network. It uses PsExec to execute arbitrary commands via a command-line interface on computers across the entire network.
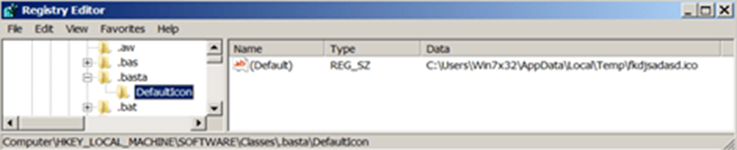
Group Policy Objects (GPOs) can be used to make computer changes that are then applied to non-administrator accounts. Inspired by this, on compromised domain controllers, the Black Basta ransomware creates a GPO to disable Windows Defender and other anti-virus programs while also trying to take down QBot-Egregor attacks that use similar techniques.
Step 3:
Once the Black Basta ransomware has been able to bypass a security measure that may have otherwise helped customers protect files, the group then deploys a ransom loader via encoded PowerShell command that uses built-in Windows Network capabilities to reach out to targeted IP addresses.
To increase the speed and efficiency of its encryption process, Black Basta Ransomware splits files into 64-byte blocks that it encrypts before interspersing them with 128-byte sections of plain-text data.
In the Black Basta’s last step, it changed the background image on a victim’s computer to include the message:
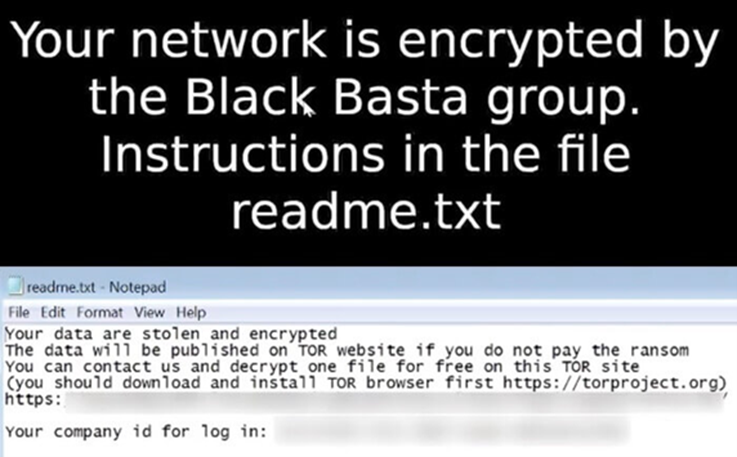
Black Basta creates files in every folder on your computer that is encrypted, with a name that depends upon the ID of your attack. Inside each file will be a readme file along with a link to your chat room where you can negotiate for the return of your files.
How to Protect Your Organization from Ransomware Attacks?
1. Ensure software updates are always up-to-date
One of the most common ways cybercriminals can hack into a computer is by finding loopholes in the system and exploiting software vulnerabilities. In May 2022, a Windows Printing Spooler Exploit was discovered to be in use by malicious Ransomware groups.
It’s important to stay on top of all security issues due to an update. That way, there is less of a chance that cybercriminals will be able to exploit vulnerabilities in your programs because the latest version has already been applied to consider such threats.
2. Establish backups of all your data
You should back up your files and enable encryption with a strong password, especially if you are storing data on remote computers. If your data becomes encrypted by ransomware, you can restore it on new devices or the infected computer once it has been correctly cleaned up.
3. Enforce Zero Trust policy
The Zero Trust policy is a great way to keep up with security as technology rapidly advances. It would help if you established trust policies that verify every new device, person, or partner that wants access to your network or data.
4. Take network security assessment with a managed firewall for contextual actions
One must have comprehensive protection against attack vectors as it relates directly to vulnerabilities and get them patched immediately. One way of doing this effectively is using a WAF (Web Application Firewall).
5. Use strong and unique passwords to protect sensitive data and accounts
Use strong passwords and implement strong password policies to ensure all credentials are stored in one-way hashes with salt so that no one will ever be able to crack them.
Conclusion
Cyber attackers will never stop trying to breach walls of defense, so make sure when it comes to security holes to plug them up because if you leave anything unsecured, the attackers will get in. They could exploit the vulnerabilities and wreak havoc on your business with no mercy.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn


 August 23, 2022
August 23, 2022





