HTTP/2 Rapid Reset Attack Vulnerability
Google, Amazon Web Services & others recently disclosed a vulnerability in HTTP/2 protocol, which is being tracked as “CVE-2023-44487”. The flaw lies in how the HTTP/2 protocol was implemented to increase the efficiency of transmitting various messages between endpoints by “Stream multiplexing”.
What is HTTP/2 Rapid Rest Attack Vulnerability (CVE-2023-44487)?
HTTP/2 protocol provides a mechanism for clients to request the cancellation of a previously initiated stream by transmitting an RST_STREAM frame to the server. This cancellation process assumes that the cancellation occurs immediately on the server side once RST_STREAM frames are received. However, the client can send a reset stream immediately after sending the request frame, which is received by the server, processed, and rapidly resets. The requests are canceled, but the connection remains open.
As the cancellation is immediate and not dependent on the server side, the client can initiate many such streams simultaneously, followed by streams containing HTTP/2 headers and/or data frames within the limit of concurrent allowed streams negotiated between the client and server. In a default HTTP/2 implementation, the server still needs to process the canceled requests, eventually causing resource exhaustion on the server.
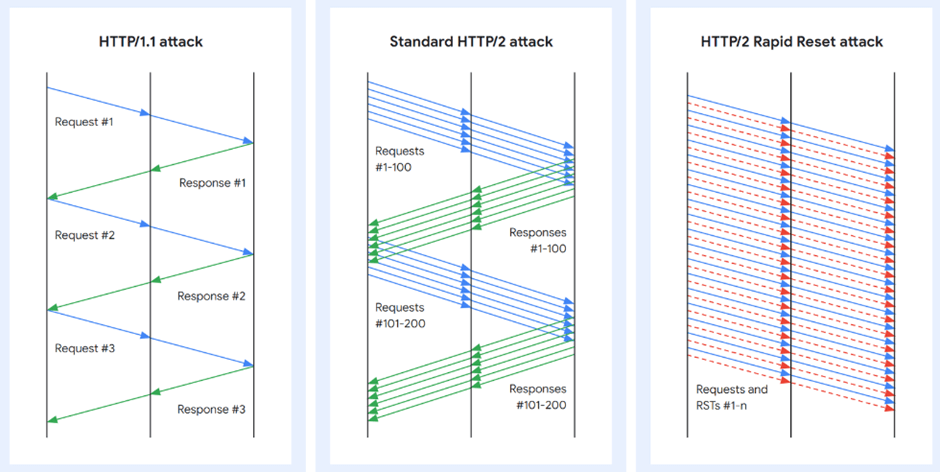
Image source: TechRepublic
It is now popular as a “Rapid Reset Attack,” and the vulnerability allows a remote, unauthenticated attacker to cause an increase in CPU usage that can lead to a denial-of-service (DoS). It is also known to be exploited in the wild from August through October 2023, and multiple exploits are available to the public.
Severity: HIGH
CVSSv3.1: Base Score: 7.5 HIGH
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
CVSSv2: Base Score: 5 MEDIUM
Vector: CVSS2#AV:N/AC:L/Au:N/C:N/I:N/A:P
Exploit available in public: Yes.
Exploit complexity: Low
Active Exploitations
It is also known to be exploited in the wild from August through October 2023, and multiple exploits are available to the public.
In parallel, the CISA also issued an advisory regarding the vulnerability, incorporating it into their Known Exploited Vulnerabilities (KEV) list.
Prevention and Mitigation
- Apply vendor-recommended patches/security updates.
- Disable the HTTP/2 protocol on your web server if vendor updates are unavailable.
- Restrict access to external/public to your web applications wherever possible.
- For .NET and Kestrel, servers without HTTP/2 enabled are not affected. Include a protocol setting for each Kestrel endpoint to limit your application to HTTP1.1.
AppTrana WAAP Threat Coverage
AppTrana customers are protected from the vulnerabilities from Day 0.
Beyond the vendor-supplied patches, AppTrana WAAP provides additional protection patterns that can serve as an extra line of defense against potential exploits.
References
- HTTP/2 protocol
- Google: How it works: The novel HTTP/2 ‘Rapid Reset’ DDoS attack
- AWS: CVE-2023-44487 – HTTP/2 Rapid Reset Attack
- NGINX: HTTP/2 Rapid Reset Attack Impacting NGINX Products
- Microsoft Response to Distributed Denial of Service (DDoS) Attacks against HTTP/2
- CISA: Understanding and Responding to Distributed Denial-of-Service Attacks
- CISA: Additional DDoS Guidance for Federal Agencies


 October 17, 2023
October 17, 2023



