How to Decode Your Vulnerability Assessment Report for Real Security Gaps
A vulnerability assessment report is more than a technical document. It is a strategic blueprint for improving your organization’s security posture and reducing risks. When interpreted correctly, it empowers organizations to make informed security decisions, prioritize investments, and demonstrate ROI.
Yet in many organizations, these reports are underused. They are treated as compliance artifacts or raw checklists rather than insights for strategic action. To get real value, you need to decode what is beneath the surface such as risk patterns, remediation gaps, and exposure trends that influence your bottom line.
This blog explores how to use your vulnerability report as a decision-making tool not just for fixing security weaknesses, but for improving security maturity, operational efficiency, and long-term risk reduction. It also highlights what to expect from an effective report, like the one provided by Indusface WAS.
What Is a Vulnerability Assessment Report?
A vulnerability assessment report is the output of a systematic scan and analysis of your IT infrastructure. It identifies potential security weaknesses across systems, applications, databases, and APIs, highlighting:
- Known vulnerabilities (CVEs)
- Misconfigurations
- Insecure protocols or services
- Outdated software and unpatched systems
It often includes:
- Severity ratings (CVSS scores)
- Asset-level findings
- Remediation recommendations
- Scan methodology and scope
- Risk categorization
But the real power of this report lies not in the list; it is in interpretation.
Why Decoding the Report Matters More Than You Think
Most reports tell you what is wrong, but not necessarily:
- How urgent the issue is in your environment
- Whether the vulnerability is exploitable
- What the real-world impact could be
- If the issue is part of a larger pattern
Decoding your report properly means transforming raw data into:
- Security decisions (what to fix now vs. later)
- Remediation strategies (how to fix them efficiently)
- Compliance documentation (how to demonstrate action)
What a High-Impact Vulnerability Report Should Deliver
Let us break down the key capabilities a powerful vulnerability assessment report should include using Indusface WAS as a benchmark for what “effective” looks like.
1. Contextual Risk Mapping for Smarter Prioritization
Vulnerability severity means nothing without knowing where the issue exists. A SQL injection in a dev server is not the same as one on your public-facing login page.
What to look for:
- A breakdown of risk by individual asset
- Classification into Exposed, Unhealthy, and Healthy
- Risk scoring based not only on CVSS but exploitability, exposure, and business criticality
Indusface WAS Insight:
Uses the proprietary AcuRisQ feature to assess risk in context. So, you can focus on vulnerabilities that are exploitable in your environment, not just those with a high theoretical.
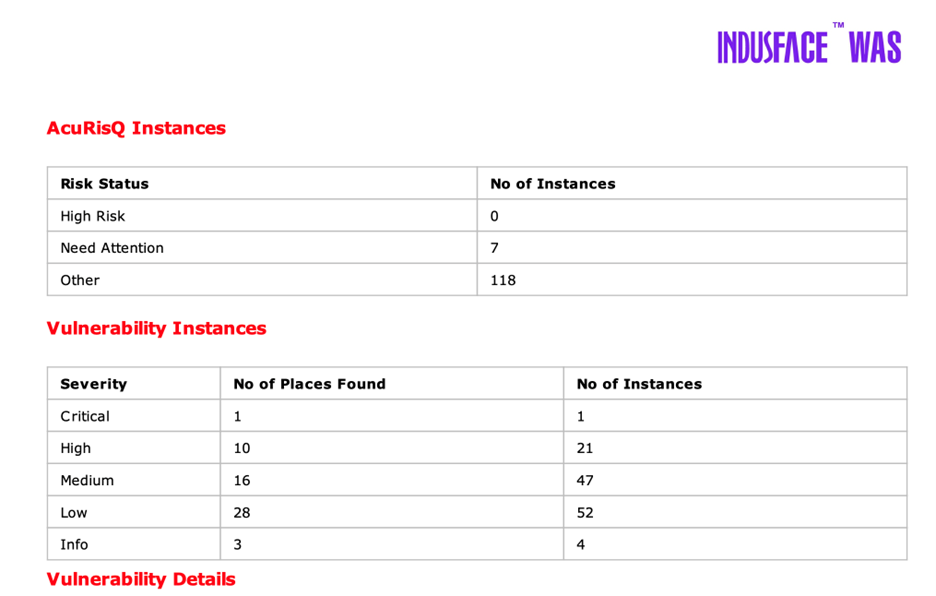
Even better, it enables you to instantly patch all open vulnerabilities through SwyftComply with AppTrana WAAP, providing immediate protection while you work on permanent fixes.
2. Visual Summaries that Guide Action
Decision-makers and stakeholders need a high-level view. A good report should instantly answer:
- How many assets are at risk?
- What is the trend of vulnerabilities over time?
- Are we improving or falling behind?
Indusface WAS Delivers:
At-a-glance dashboards with actionable summaries, ideal for aligning security decisions with goals like reducing downtime or meeting SLAs.
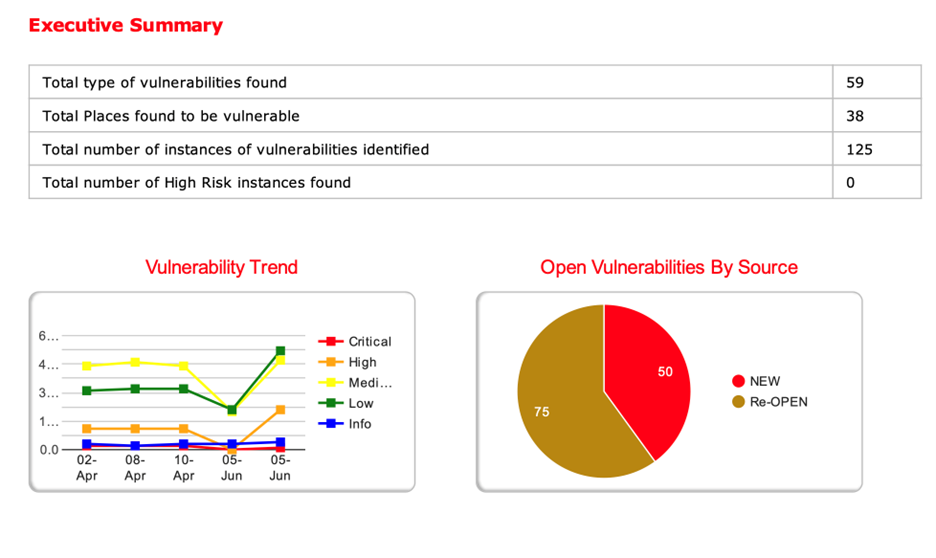
The intuitive executive summary highlights total sites scanned, sites at risk, top vulnerabilities, unresolved issues over time, and remediation activity. So, you can brief leadership or compliance officers in minutes, not hours.
With autonomous vulnerability remediation Indusface WAS also helps you achieve a zero–vulnerability report, ensuring continuous protection and audit readiness.
3. Pattern Recognition for Process Improvement
When vulnerabilities repeat across environments or teams; it is not just a security flaw, it is a workflow issue.
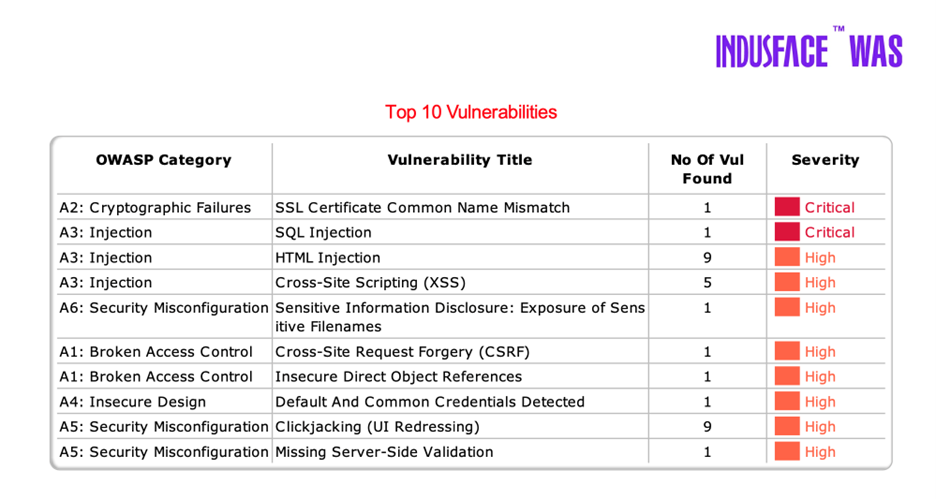
The report should highlight vulnerabilities by type and frequency, not just severity. So that you can uncover deeper issues like insecure coding practices or misconfigured deployments.
What matters:
- Categorization by OWASP Top 10 or similar
- Insights on repeated issues (e.g., misconfigurations, XSS)
- Data showing whether issues are isolated or systemic
Indusface WAS Difference:
Indusface WAS helps you go beyond fixing individual vulnerabilities by identifying patterns across apps, APIs, and environments. It categorizes issues by OWASP Top 10, highlights recurring flaws like XSS or misconfigurations, and shows whether problems are isolated or systemic helping teams address the root cause, not just the symptoms. For example, if Clickjacking or XSS appears across multiple pages, you know it is a systemic issue, not a one-off error.
4. Remediation Timelines that Show Accountability
Mean Time to Remediate (MTTR) is not just a metric; it reflects process maturity and team efficiency. The difference between proactive security and reactive firefighting often lies in how fast vulnerabilities are resolved. Your report should highlight:
- New, open, and re-opened vulnerabilities to track the flow and recurrence of issues.
- MTTR across severity levels to measure how fast critical vulnerabilities are addressed compared to low-risk ones.
- Aging data showing vulnerabilities unresolved for 30, 60, or 90+ days, pinpointing bottlenecks and potential process failures
With Indusface WAS:
Indusface WAS brings these insights into a single, actionable view. It tracks the full lifecycle of each vulnerability from detection to resolution across applications and APIs. The platform visualizes remediation timelines, identifies overdue issues, and enables teams to set and monitor SLAs. By surfacing trends like re-opened vulnerabilities or long-standing unresolved issues, it holds teams accountable and supports continuous improvement in your remediation workflows.
5. Clarity on API Risks and Exposure
Modern businesses rely heavily on APIs. However, many reports blur API vulnerabilities with web app issues.
What to expect:
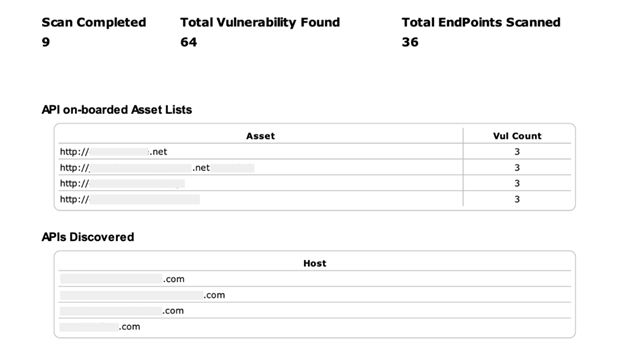
- Dedicated sections for API vulnerabilities
- Discovered undocumented API endpoints
- Vulnerability counts per API path
Indusface WAS API Module:
Isolates API vulnerabilities clearly, making it easier to assign fixes to the right backend or microservices teams and avoid miscommunication.
It provides detailed API scan results, endpoint discovery, and OWASP-mapped API vulnerabilities like authentication bypass, insecure direct object references, and injection flaws. This lets you assign fixes to backend teams without misinterpretation.
6. Runtime Threat Detection Beyond Scan Results
Static scans only show part of the picture. Runtime threats like malware or behavioral anomalies appear between scans and require immediate attention.
WAS Malware Module Includes:
- Continuous runtime scanning for malware
- Behavioral indicators of compromise
- Status of newly found or re-opened threats
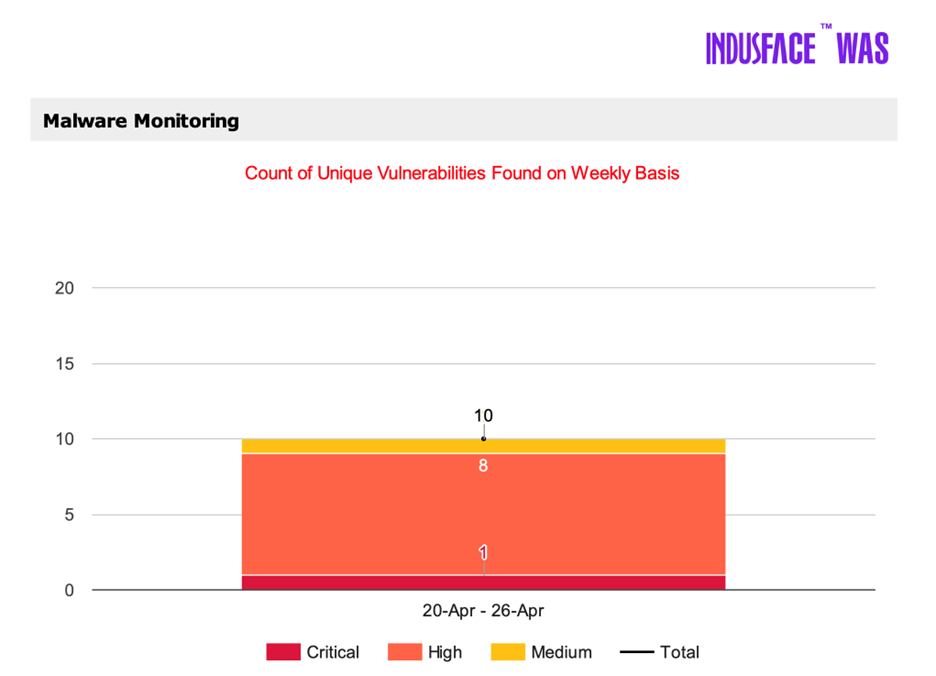
This allows organizations to go beyond “point-in-time” security to ongoing visibility, a major boost for operational resilience.
7. Remediation Guidance with Verification Steps
Many reports leave remediation advice vague, with generic “apply a patch” suggestions. That is not enough.
What to expect:
- Clear, actionable remediation steps
- CVE references and verification instructions
- Guidance specific to your environment (e.g., API vs. web apps)
- Proof of Concept (PoC) that shows how the vulnerability could be exploited
Indusface WAS Delivers:
Tailored remediation instructions written by security experts, aligned with best practices, and designed to reduce risk without business disruption. The report also includes PoC demonstrations for critical and high-severity vulnerabilities.
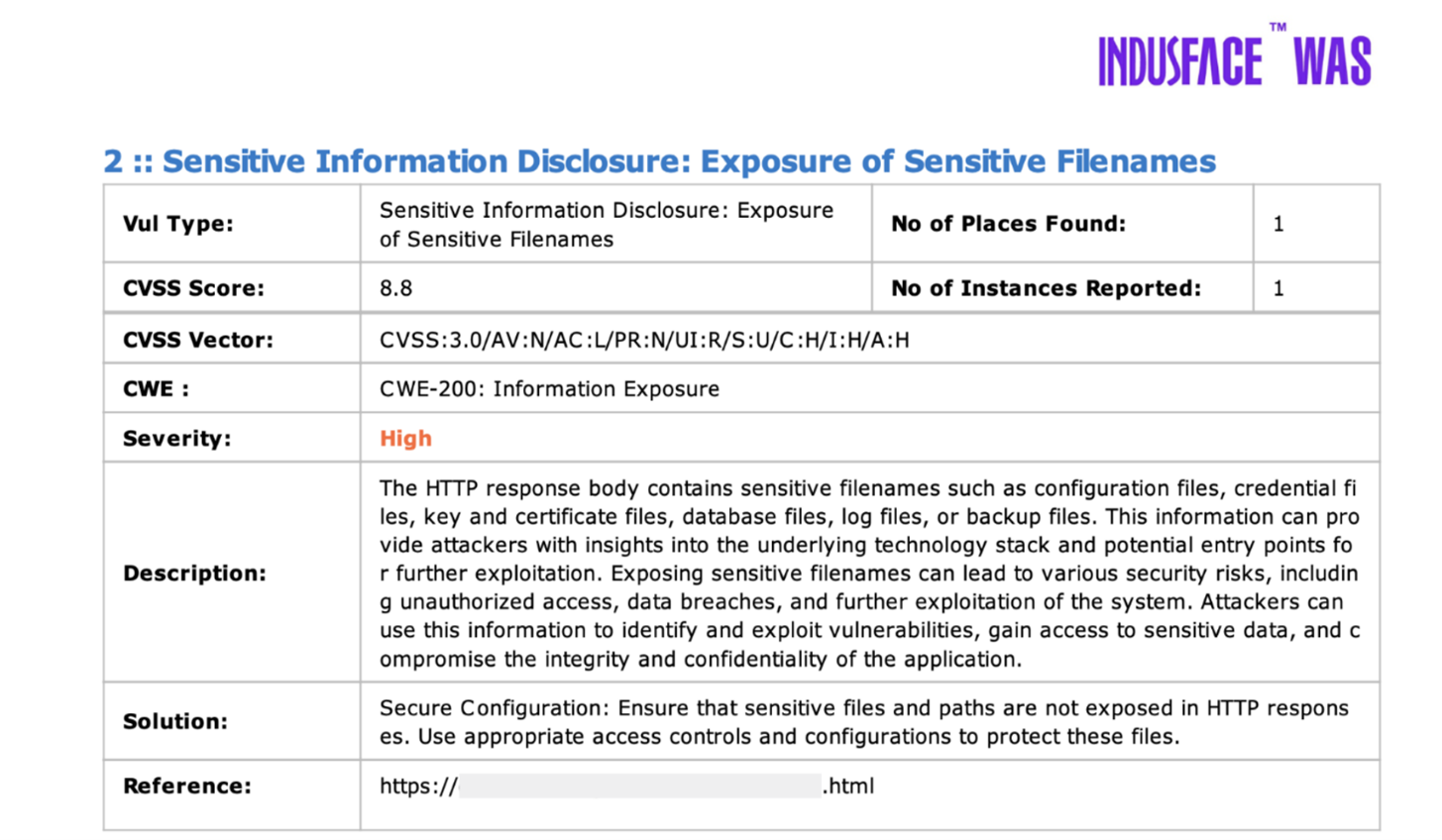
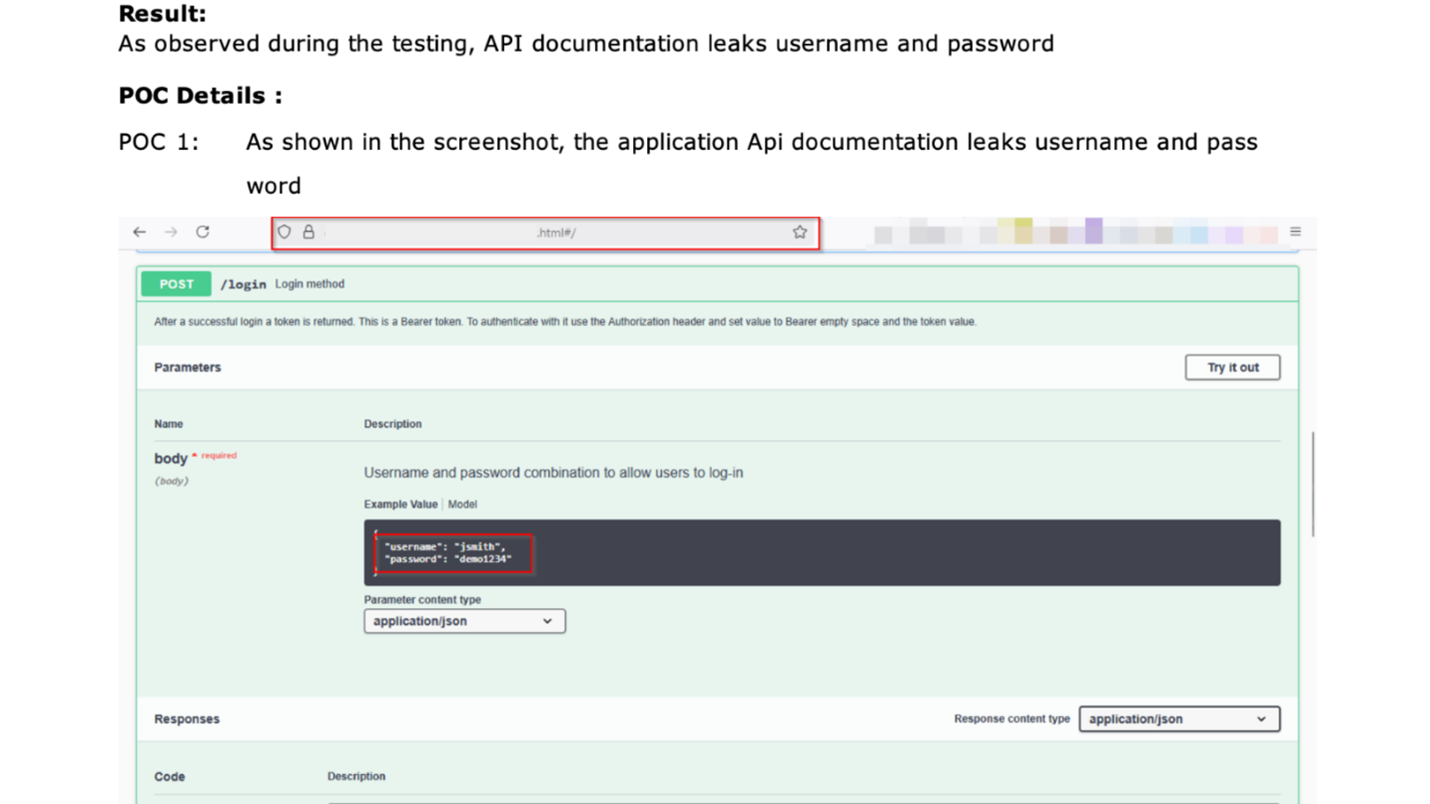
8. Tracking Usage, Manual Testing, and Compliance Coverage
Most enterprises use both automated scanning and manual testing for critical assets. An effective report should reflect:
- License utilization – how many licenses are used vs. allocated, giving insight into asset coverage and tool adoption.
- Manual testing coverage – what percentage of your applications and APIs have been manually tested by security experts.
- Impact of manual testing – where manual PT has uncovered real, exploitable vulnerabilities missed by automation.
Indusface WAS Tracks:
Indusface WAS offers a unified view of your automated and manual testing efforts. It logs and visualizes manual penetration testing (PT) usage across all applications, mapping these efforts against actual vulnerabilities discovered. This helps distinguish the value manual testing adds, especially in complex or logic-heavy scenarios.
The platform also provides a license usage summary, helping teams understand coverage gaps and optimize testing allocation. Additionally, WAS maps all findings such as automated and manual to key compliance frameworks like PCI DSS, HIPAA, and ISO 27001, making audit preparation significantly easier.
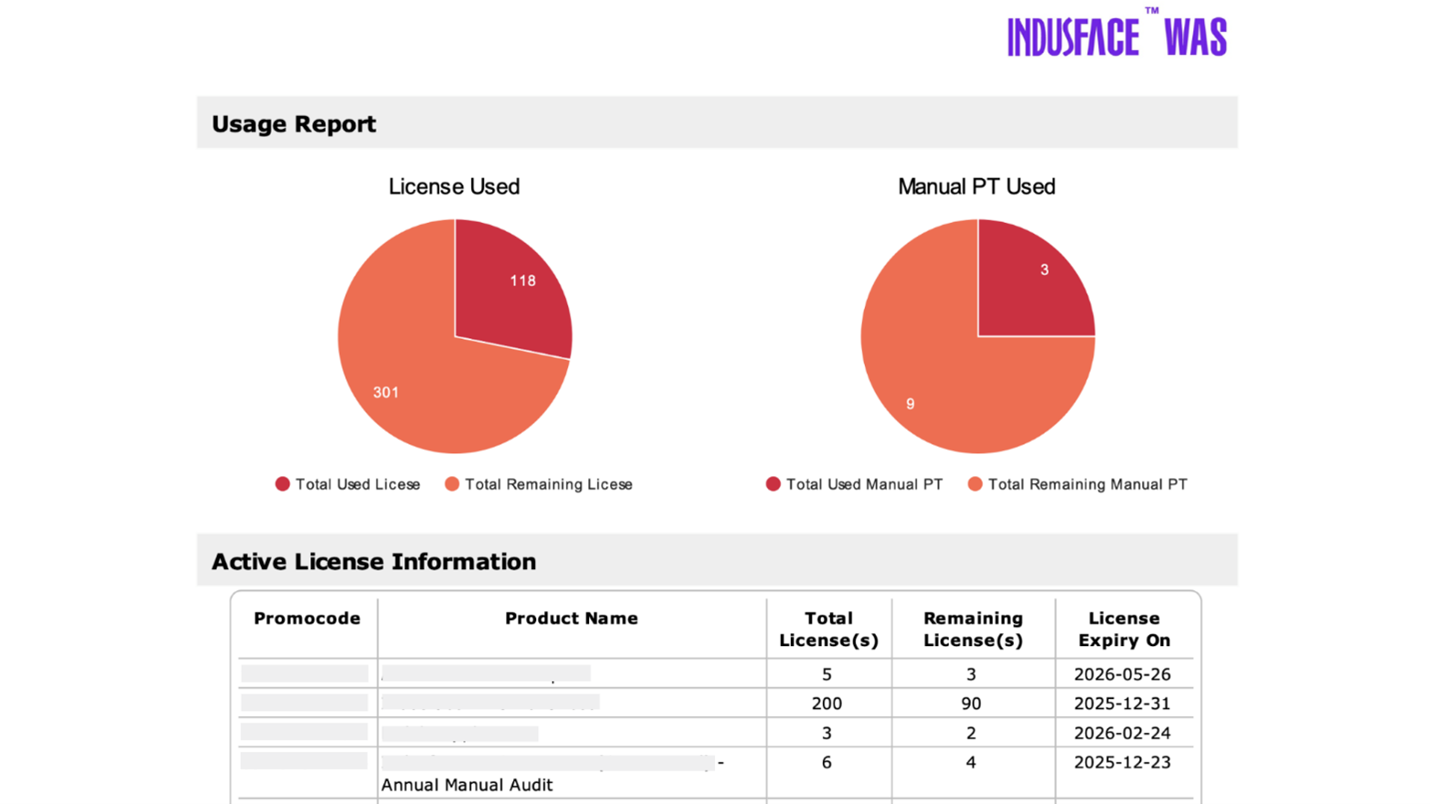
The result?
You gain a clear picture of testing depth, effectiveness, and compliance readiness supporting smarter investments and giving stakeholders confidence in your security posture.
How to Turn the Vulnerability Assessment Report into a Roadmap
Once you have decoded your report, here is how to make it actionable:
1. Prioritize Exposed Assets First
Fix the ones marked as “Exposed” by your scanner. They are often public, critical, and exploitable. Indusface WAS goes beyond prioritization, it offers the option to instantly patch all open vulnerabilities through SwyftComply, reducing exposure time drastically.
2. Patch Across Environments
Do not just patch production. Vulnerabilities in staging, QA, or internal portals can leak into live systems or be exploited laterally.
3. Automate Where Possible
Use tools that support instant patching, WAF rules, and ticket integration to reduce MTTR.
4. Measure Progress
Track metrics like:
- MTTR
- % of vulnerabilities closed within SLA
- of re-opened issues
- Risk score reduction over time
Not sure what to do after identifying vulnerabilities? Check out our Vulnerability Remediation Guide to learn the next steps.
Final Checklist: Turning Your Report into a Risk Reduction Strategy
Once you have decoded the report, here is how to act:
| Task | Why It Matters |
|---|---|
| Prioritize “Exposed” assets | These pose immediate risk |
| Address repeat issues | Indicates broken processes |
| Track MTTR trends | Helps prove program efficiency |
| Use report data in board briefings | Aligns security with business |
| Close gaps in non-prod environments | Prevent lateral threats |
| Align remediation to compliance timelines | Prevent penalties and audit failures |
From Report to Remediation: What Comes Next
Your vulnerability report should not overwhelm; it should empower you. A well-structured report:
- Surfaces the most dangerous risks
- Highlights trends and weaknesses
- Aligns with compliance and business goals
- Supports fast, effective remediation
Ready to see how clear and actionable your next vulnerability report can be? Start your scan now and experience reporting that drives results, not just awareness.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 June 20, 2025
June 20, 2025






