Beware! Qakbot Banking Trojan Picked Up New Tricks
Attackers have begun using new malware to gain an initial foothold onto compromised networks and systems in recent campaigns. What started as a Trojan malware called Qbot in 2007 has now evolved into Qakbot with new tricks.
Qakbot has been active since it was first discovered and continues to threaten financial institutions and individual bank customers. This multi-purpose Trojan malware is designed to steal banking credentials such as login information and passwords. Because it is so versatile, Qakbot malware has become a top threat that organizations must be aware of.
What is Qakbot?
The Qakbot malware phishing attack spreads via an email-driven botnet is dangerous as it can masquerade as a conversation thread the recipient already has. This makes it difficult to detect, as the email may appear to come from a trusted sender. This attack can spread quickly as employees share infected email attachments.
The Qakbot malware is like a machine with different parts working together. The core engine is the primary component, and then there are other pieces it can download and add depending on what it needs. These extra pieces are called plugins, and they can be used to carry out different tasks – like stealing information or taking control of parts of the system.
Qakbot has become a go-to malware attack for threat actors because it provides many different capabilities like:
- Gather information
- Move laterally through networks
- Exfiltrate data
- Deliver next-stage payloads such as ransomware on devices
How Does Qakbot Work?
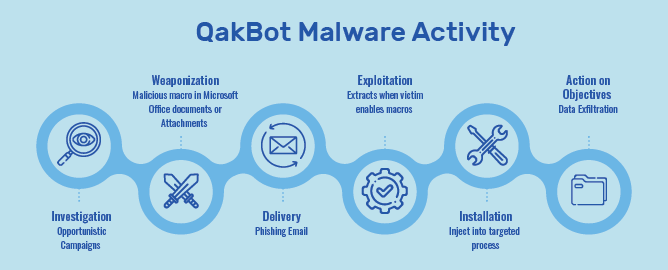
Qakbot phishing contains 2 essential parts, namely
- A URL – Contains information about malicious ZIP or any online drive link (e.g., Microsoft One Drive)
- An attachment – Contains an ISO image, HTML, and a DOC file
The messages in QakBot malware email campaigns are designed to look like they come from a person or a company that you know.
They come up with a call-to-action with brief text content, e.g. “please see attached document” or “click here to view a file”, followed by a ZIP file, to get you to open the file that would infect your computer with their malware.
When you open the password-protected zip file, there’s another file inside it with an ISO image. This ISO image file contains four different files.
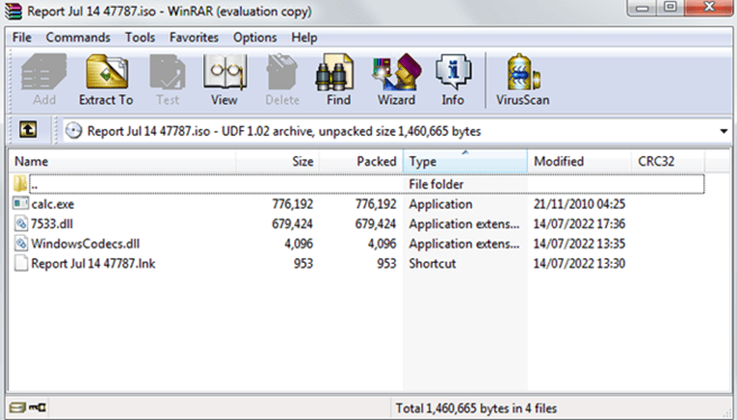
Being a Victim of Botnet
The Qakbot malware is pretty devious. It crawls through your email conversations and sends a “context-aware” reply-all message with a short sentence and a link to either a website or a zip file.
The scariest part is that the message seems like it came from you convincingly. So, your friends and colleagues not only see the message but also think it’s coming from you.
Thereby it prompts the victim to open it. Once the victim opens the attachment, their device will become infected with the malware.
Moreover, the Qakbot malware botnet infection chain is a serious threat to any network and constantly scans for weaknesses and vulnerabilities. This makes it very difficult to protect against.
What’s new in QAKbot Techniques?
From the initial delivery method of delivering XLM Macros, the Quakbot malware has shifted to .LNK files since May 2022. Windows use LNK files to create shortcuts to programs, and Qakbot takes advantage of this by infecting them with malicious code.
Qakbot has always been a sneaky little malware, but the newer versions are becoming more and more adept at hiding their tracks.
For example, the newer versions of the malware will insert this information directly into the registry. Previously malware writes encrypted configuration information to a file where it could be easily found and traced back to the Qakbot infection. This makes it more difficult to find and remove the infection. Also, makes the Qakbot malware capable to hijack email and browser data without being detected.
3 Best Practices to Avoid Getting Infected in Qakbot
The following 3 best practices will help protect your business from Qakbot malware, even in data-intensive environments.
1. Monitor for New Service Creation with Vulnerability Scanning
Many entry points, or gateways of network endpoints provide opportunities for threat actors to enter and orchestrate attacks.
Qakbot malware takes advantage of unsecured vulnerabilities to gain access and wreak havoc. By securing these vulnerabilities, you can better protect against such attacks.
Web application vulnerability scanning, along with real-time alerts, is an important security measure for organizations. By identifying vulnerabilities, you can fix them before attackers exploit them.
2. Staff Awareness About Threat Source
Qakbot malware can quickly spread through email attachments. The best way to protect your organization from Qakbot is to educate your employees on how to spot spam emails, types of untrusted materials, and files and report them to the IT team.
3. Employ Virtual Patching
One of the most critical tasks security teams struggle with is how to keep their systems up to date with the latest security patches. Another big challenge is dealing with known vulnerabilities that have not yet been patched. And then there are the unknown vulnerabilities that could pop up anytime.
Using an effective WAF with an automation virtual patching solution, you can apply for instant protection from vulnerabilities before being exploited.
What’s Next?
It is no secret that automated website scanning and malware removal are essential in preventing threats. When it comes to website security, you want to ensure you have the best scanner possible.
Indusface WAS, equipped with self-learning capabilities and certified security specialist supports, ensures your website is secure and protected against all kinds of potential threats.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn


 September 6, 2022
September 6, 2022






