Take the Application Security Quiz
Recent web application security attacks happened.
Do you know about the recent bank cyber heist attempt in Bangladesh? Apparently, hackers tried to steal $951 million from the country’s account at the Federal Reserve Bank of New York. Although they were not able to get through with all the transactions, $81 million were still transferred in the Philippines.
So, why are we talking about it in the application security quiz? Well, banks spend around 90% of their security budget on perimeter security. Application security gets just the remaining 7-10%, which is insufficient given the number of attacks happening every year.
In fact, the scenario is more or less the same for other sectors too. According to the ‘Ponemon Application Security Risk Management Report’, a large part of the problem is underestimating and risks and wrong perceptions of how attackers exploit weakness within Layer 7. This quiz aims to raise awareness of some of the most burning issues.
Question 1) What is the cost of carrying out an application DDoS attack on an average website?
- $5,000
- $200
- $500
- $10,000
Answer: (b)
As unlikely it may seem, anyone can hire bots and use cloud machines to carry out full-fledged distributed denial of service attacks powerful enough to shut the server down. For $200-250, anyone including rivals and employees can cause severe damage.
Unfortunately, there is no absolute protection against DDoS attacks. Massive traffic surges can happen from any part of the world and you can’t keep universal blocking rules of all of them. Learn more about it at “Deadly App DDoS and How to Stop It”.
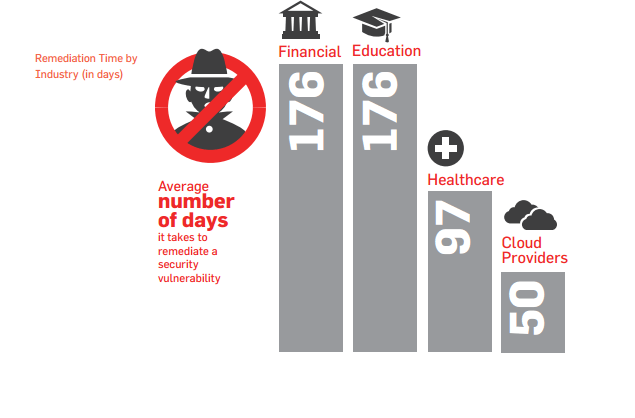
Question 2) On average, how many days financial companies take to fix found vulnerabilities?
- 1 day
- 15 days
- 150 days
- 175 days
Answer: (d)
Financial companies are bound by resource, time, and compliance issues before they can even think of fixing found issues. Surprisingly, that’s why the 2015 State of Vulnerability Risk Management showed that financial companies take around 176 days to fix a security vulnerability.
Remediation can take time. The next best thing is to patch vulnerabilities virtually so that the attackers cannot exploit them. Indusface Web Application Firewall can help secure vulnerabilities instantly.
Question 3) What is the top vulnerability leading to data breaches?
- SQL Injection
- Cross-Site Scripting
- Cross-Site Request Forgery
- Sensitive Data Exposure
Answer: (a)
SQL Injection has been accounted for around 97% of the data breaches across the globe. Although this application vulnerability was detected 15 years ago, it still tops the OWASP 10 list. While detecting SQLi is fairly simple, protecting the website against exploitation is difficult. You can read more about it at “All You Need to Know About SQL Injection“.
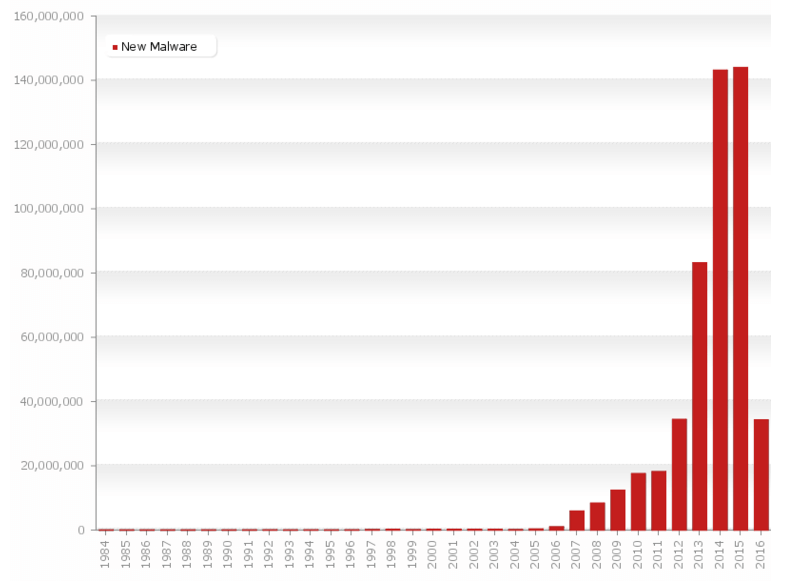
Question 4) How many malware exist?
- 40
- 4,000
- 4 million
- 400 million
Answer: (d)
Currently, there are 500 million different identified malware. Out of these, 30 million were found recently. Every day, the malware count is increasing exponentially and if your application security is unable to keep up with the newly-found threats, chances are that your business will face exploitation sooner or later.
Question 5) How do security professionals rate their management’s application security outlook?
- Very well informed of the risks
- Fairly informed
- Informed
- Underestimate risks
Answer: (d)
Ponemon Institute’s Application Security Risk Management Report shockingly revealed that 60% of the respondents thought that their management underestimates potential security risks. In fact, they also agreed that this risk outlook jeopardizes their ability to fight attackers.
Question 6) What is the highest loss component attributed to data breaches?
- Customer acquisition spending
- Reputation damage
- Lost business
- Lost business
Answer: (d)
According to the Ponemon Institute’s 2014 Cost of Data Breach Study, organizations in the United States suffer the highest due to loss of business after a publicized data breach incident. The damage is calculated to up to $3.3 million for US organizations and $400 thousand for Indian companies.
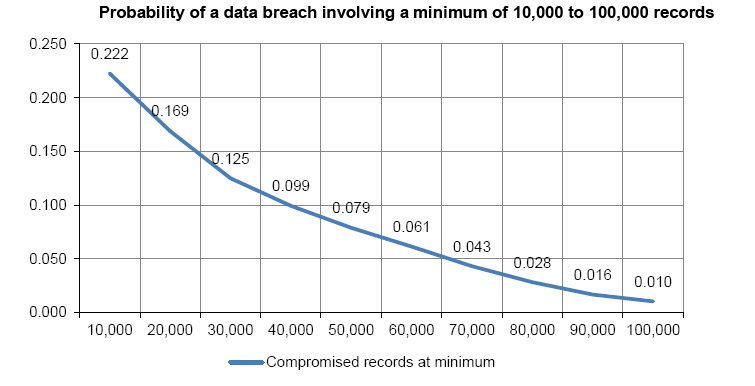
Question 7) What size of companies are more likely to be exploited?
- Large and enterprise companies
- Startups, cloud, and medium-sized companies
Answer: (b)
While it’s a common understanding that large companies have a higher number of records that are more likely to be hacked, statistics show otherwise. The probability of data breach is considerably higher for companies dealing with 10, 000 records as opposed to ones with 100, 000 record or more. Higher application security standards and spending in enterprise organizations explain the data.
Question 8) Around 70% of the cyberattacks happen at which layer?
- Network layer
- Session layer
- Data Link layer
- Application layer
Answer: (b)
According to information technology research giant Gartner, 70% of all cyberattacks occur at the application layer. As we already mentioned, only 10% of the IT security budget is allotted to application security as management teams remain ignorant of the risks.
Indusface Application Security Awareness Campaign
The way attackers are exploiting application-layer vulnerabilities, it will be mandatory for not only security professionals but also managed to learn more about it. Indusface has taken the initiative of raising awareness on the basic issues. Here is the list of our top articles to help you start.
- OWASP Top 10, Hacking, and Business Impact: Business Manager Series – Part 1
- OWASP Vulnerabilities and Attacks Simplified: Business Manager Series – Part 2
- OWASP Part 3: Mobile Application Risks
- OWASP Part 4: Mobile Application Risks
- Once Frank Survived a DDoS Attack
And if you are looking for complete application security, Indusface Total Application Security can help scan application vulnerabilities with web application scanning, prevent hacking attempts with web application firewalls, and continuously monitor for emerging threats and DDoS attacks to mitigate them.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 March 31, 2016
March 31, 2016