In today’s high-risk cyber environment, vulnerability reports are not just technical logs. They are proof of your security posture. Whether you are preparing for a compliance audit, responding to a customer security questionnaire, or evaluating your own risk exposure, one phrase carries enormous weight:
Zero vulnerabilities found!
A zero-vulnerability report reflects more than just clean scan results. It signals a mature, proactive, and well-managed security program. But what does it really take to achieve this? And is it realistic in a constantly evolving threat landscape?
This level of hygiene is not achieved with basic scanning alone. It demands a modern approach combining automation, threat intelligence, remediation orchestration, and expert validation.
This blog explores the importance of clean reports, how autonomous protection supports that goal, and how AppTrana SwyftComply makes it possible.
What Is a Zero-Vulnerability Report?
A zero-vulnerability report is the outcome of a full security assessment in which no critical, high, or medium vulnerabilities remain open. It reflects that:
- All discovered vulnerabilities have been remediated or mitigated
- No known threats currently impact the application’s availability, integrity, or confidentiality
- The environment meets risk thresholds required by compliance and customer security policies
These reports are often used during audits, client security assessments, or internal reviews to show real-time risk posture and security maturity.
Here’s a Snapshot from an AppTrana SwyftComply Report:
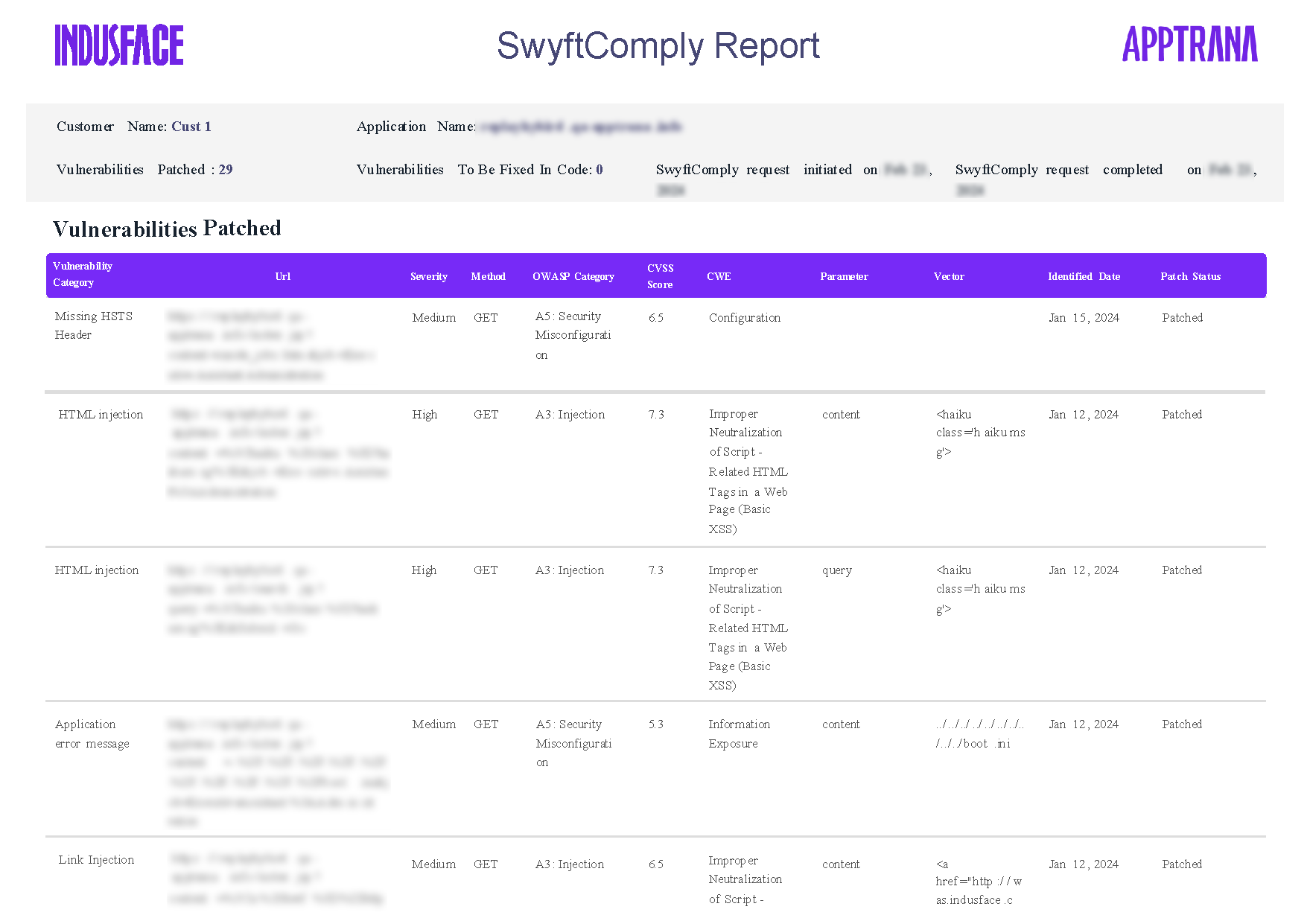
This snapshot reflects how vulnerabilities across OWASP categories (like XSS, HTML injection, and session misconfigurations) were not just detected but remediated or protected, leaving zero open issues in the final report.
Why Traditional Scanning Is not Enough
Generating a clean report is not about turning on a scanner. Most organizations face these common blockers:
- Hundreds of vulnerabilities with no remediation path
- False positives that consume time and lead to alert fatigue
- Delays between detection and fix (weeks, sometimes months)
- Scans without context, timelines, or compliance alignment
That is why achieving a zero-vulnerability state consistently requires automation, protection, and process maturity not just detection.
Why Zero-Vulnerability Reports Are Now a Must-Have
A zero-vulnerability report delivers value far beyond the security team. Here is how it impacts key operational and business outcomes:
1. Security Without Proof Does not Count Anymore
It is no longer enough to claim you are secure. Auditors, enterprise buyers, and regulators now expect evidence-based reporting. Without a zero-vulnerability report or its equivalent, security maturity becomes anecdotal not defensible.
Whether you are preparing for:
- A SOC 2 Type II audit
- A PCI DSS 4.0 quarterly ASV scan
- A HIPAA technical safeguards assessment
- Or a customer due diligence questionnaire
…you will likely be asked to produce a recent, validated report showing no open exploitable vulnerabilities.
2. Compliance Frameworks Expect It
Compliance standards worldwide increasingly expect security teams to not only detect, but resolve vulnerabilities within defined timeframes.
For standards like PCI DSS (Requirement 11.3.1, 6.3.3), SOC 2 (CC7.1/7.2), HIPAA (45 CFR §164.308), and ISO 27001 (A.8.8, A.5.36), clean reports serve as direct evidence of vulnerability detection, response, and closure.
They simplify audits, shorten evidence cycles, and reduce the need for manual documentation or exception reporting.
| Framework | Relevant Requirement | Expectation |
|---|---|---|
| PCI DSS 4.0 | Req. 11.3.1, 6.3.3 | Quarterly external scans + verified remediation |
| SOC 2 (TSC) | CC7.1, CC7.2 | Detection + response tracking |
| HIPAA | §164.308(a)(1)(ii)(A)(B) | Risk analysis + timely mitigation |
| ISO 27001 | A.8.8, A.5.36 | Control effectiveness for vulnerabilities |
| GDPR | Article 32 | Technical measures to ensure low-risk processing |
Learn how to align application security with compliance requirements
A zero-vulnerability report directly addresses these requirements reducing audit friction and demonstrating continuous control effectiveness.
3. Enterprise Buyers Demand It During Security Reviews
If you are selling SaaS or handling sensitive user data, chances are your prospects or partners require proof of recent vulnerability assessments before proceeding.
A clean report:
- Accelerates procurement approvals
- Speeds up vendor onboarding
- Differentiates your product with security assurance
In regulated industries like fintech, healthtech, and edtech, this can be a deciding factor in closing a deal.
4. It Drives Operational Accountability
Internally, a zero-vulnerability report functions as a performance indicator for your security program. It shows that:
- Vulnerability SLAs are being met
- Application and API surfaces are protected
- DevSecOps teams are closing the loop from detection to remediation
- Risk is being measured and reduced consistently
It also gives leadership and compliance teams a clear, point-in-time view of residual risk, with traceability and timelines to back it up.
5. It is Critical for Incident Readiness and Reporting
In the event of a data breach, being able to demonstrate that your environment had:
- No unpatched known vulnerabilities
- Active remediation workflows
- Real-time protection in place
…can significantly reduce regulatory penalties and demonstrate responsible security posture to investigators and stakeholders.
A zero-vulnerability report, maintained and updated regularly, serves as part of your incident response documentation.
- It Supports Growth Through Contracts, Partners, and Integrations
Many customer contracts and third-party partnerships include security and vulnerability management clauses. Before signing or renewing agreements, your stakeholders may ask for proof of:
- Remediated vulnerabilities
- Regular scanning practices
- Clean third-party risk posture
A zero-vulnerability report helps:
- Fulfill customer contract obligations
- Accelerate third-party integration approvals (e.g., payment gateways, IDPs, SaaS connectors)
- Streamline vendor onboarding and renewal
In industries like fintech, health tech, or ecommerce, such validation is often mandatory.
7. It Impacts Cyber Insurance, M&A, and Investor Trust
Security is no longer a technical detail; it is a board-level concern. A zero-vulnerability report plays a powerful role in:
Cyber Insurance – Providers increasingly require documented proof of risk posture. A clean report may qualify you for better premiums, faster claims, and broader coverage.
Mergers & Acquisitions (M&A) – During technical due diligence, clean vulnerability reports assure buyers there are no hidden threats in your code or infrastructure reducing negotiation risks and increasing valuation confidence.
Investor and Board Security Reviews – As investors and board members demand visibility into cyber readiness, a zero-vulnerability report becomes your trusted, point-in-time snapshot, showing that your security posture is defensible, measurable, and under control.
How AppTrana SwyftComply Makes Zero-Vulnerability a Reality
Reaching a zero-vulnerability state requires more than detection. SwyftComply, a core capability within AppTrana WAAP, provides autonomous vulnerability remediation with real-time oversight.
Key Highlights:
- Remediates all open vulnerabilities instantly
- Applies virtual patches immediately for risks that cannot wait for code fixes
- Ensures full visibility into detection, protection, and resolution timelines
- Generates audit-ready reports mapped to compliance frameworks like PCI DSS, SOC 2, HIPAA, and ISO 27001
- Supported by human-validated insights, reducing the risk of false positives or broken workflows
Whether it is code flaws, configuration issues, or newly exposed APIs, SwyftComply helps security teams move from alert to resolution and prove it with clear, defensible documentation.
Clean Reports, Clear Trust
The journey from vulnerability detection to demonstrable resolution is what separates reactive security from operational excellence.
A zero-vulnerability report shows that:
- You are monitoring threats continuously
- You are remediating fast and intelligently
- You are ready to prove your posture any time, to anyone
In today’s compliance-driven and trust-sensitive market, that is no longer a nice-to-have.
It is a baseline expectation.
Want to experience what a real zero-vulnerability report looks like for your app? Request a Demo.



