What is an Advanced Persistent Threat?
An Advanced Persistent Threat is a prolonged, targeted cyberattack where an intruder gains access to a network and remains undetected for an extended period. The attacker typically seeks to steal sensitive information, disrupt operations, or gain long-term strategic access.
The term breaks down into:
- Advanced: Uses sophisticated techniques, often involving zero-day exploits, social engineering, and custom malware.
- Persistent: Maintains access for months or even years, evading detection through stealthy behavior.
- Threat: Conducted by organized groups, often nation-states or well-funded cybercriminals, with specific goals in mind.
Common Goals of APTs
Unlike opportunistic cyberattacks that focus on short-term gains, APTs are designed for long-term access and strategic outcomes. Their goals typically include:
- Espionage: APT groups frequently target intellectual property, proprietary research, and confidential communications. This is common in sectors like defense, healthcare, manufacturing, and government, where stolen data can provide significant strategic or economic advantage.
- Sabotage: Some APTs aim to disrupt or damage operations by targeting critical infrastructure, industrial control systems, or supply chains. These attacks may result in service outages, equipment failures, or data corruption, often aligned with geopolitical motives.
- Financial Gain: While less direct than typical cybercrime, APTs may engage in silent theft of financial data, unauthorized transactions, or manipulation of systems to generate long-term financial benefits without triggering immediate detection.
- Political Motives: Nation-state APTs may pursue political objectives such as surveillance, election interference, or disinformation campaigns. These operations are often part of broader efforts to influence public opinion or destabilize governments.
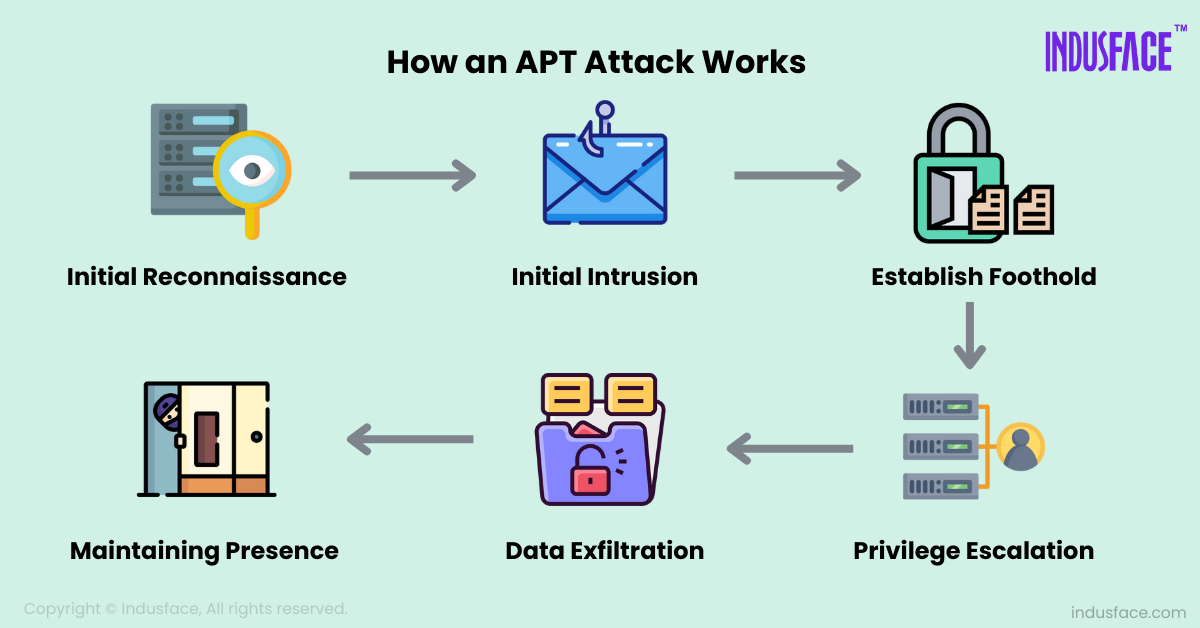
The APT Lifecycle: How Do APTs Work?
APTs unfold in a sequence of carefully planned phases, each designed to maintain stealth and persistence over an extended period.
1. Initial Reconnaissance: Attackers begin by gathering intelligence on the target, such as employee roles, software in use, network infrastructure, and potential vulnerabilities. This helps them plan an entry point with the least resistance.
2. Initial Intrusion: Using phishing emails, zero-day exploits, or stolen credentials, attackers breach the network. These initial actions are crafted to avoid detection and appear harmless.
3. Establishing a Foothold: Once inside, attackers deploy malware like remote access tools or backdoors to ensure they can re-enter the system, even if the breach is partially detected.
4. Privilege Escalation: They move deeper into the network, gaining higher privileges by exploiting weak controls or misconfigurations, eventually reaching sensitive systems.
5. Data Exfiltration: The attackers identify valuable data, such as financial records, trade secrets, or personal information, and extract it in small, encrypted batches to avoid triggering alarms.
6. Maintaining Presence & Covering Tracks: To remain undetected, they erase logs, hide malware, and use encryption to mask communications. The goal is to stay inside for as long as possible without raising suspicion.
Common Techniques Used in APTs
- Spear Phishing: Tailored emails targeting specific employees to gain credentials or install malware.
- Zero-Day Exploits: Targeting unpatched vulnerabilities in software or hardware.
- Supply Chain Attacks: Infiltrating the target organization by compromising trusted third-party vendors, software updates, or service providers. Learn more about supply chain attacks
- Watering Hole Attacks: Compromising websites commonly visited by the target organization.
- Command and Control (C2) Communication: Securely communicating with infected systems to issue instructions.
- Credential Dumping: Extracting user credentials to move laterally within the network.
Real-World Examples of APTs
Despite advanced defenses, organizations continue to fall victim to APT groups using stealth, zero-day exploits, and social engineering. Here are some of the most recent APT campaigns that made headlines in 2024:
1. Salt Typhoon’s Telecom Breach (2024)
Salt Typhoon, a Chinese state-sponsored APT group, infiltrated major U.S. telecom providers including AT&T, Verizon, and T-Mobile. By exploiting zero-day vulnerabilities, the group gained unauthorized access to lawful intercept systems used for government wiretaps. The breach enabled them to monitor sensitive communications and exfiltrate call metadata, raising serious national security concerns.
2. Lazarus Group’s Crypto Heists (2024)
The North Korean APT group Lazarus escalated its operations in 2024 with a series of cryptocurrency-focused attacks. Using fake job offers and LinkedIn phishing campaigns, the group deployed malware like CookiePlus and exploited a Google Chrome zero-day (CVE-2024-4947). These campaigns led to the theft of over $500 million from exchanges such as WazirX and DMM Bitcoin, highlighting the group’s shift toward high-reward financial cybercrime.
3. APT29’s European Espionage Campaign (2024)
APT29, linked to Russia’s Foreign Intelligence Service, launched a broad phishing campaign targeting European embassies and political organizations. The group exploited a WinRAR vulnerability (CVE-2023-38831) and deployed malware like WINELOADER to steal credentials and access sensitive government systems. In parallel, they conducted watering hole attacks on government websites in Mongolia, further extending their global surveillance operations.
How Advanced Persistent Threats Avoid Detection
Advanced Persistent Threats are built for stealth, making them hard to detect—often only after significant damage has occurred.
- Use of Legitimate Credentials
APT actors often gain access using valid usernames and passwords stolen via phishing or brute force. This allows them to move through systems like trusted users, bypassing many security controls. - Living off the Land (LotL) Techniques
Instead of introducing new malware, attackers use native system tools such as PowerShell, WMI, or scheduled tasks to execute malicious commands—helping them evade detection by traditional antivirus solutions. - Polymorphic and Custom Malware
When malware is deployed, it is typically tailored to the environment and regularly modified. This avoids detection by signature-based tools and security software. - Slow, Controlled Operations
APTs don’t act all at once. They progress in small, deliberate steps—sometimes over weeks or months—so their activity blends in with normal traffic and behavior patterns. - Complex, Multi-Stage Attack Paths
The attack may span multiple systems, user accounts, and layers of infrastructure. This makes it difficult to trace how the intrusion occurred or what data was accessed.
On average, APTs remain undetected for over 200 days, giving attackers plenty of time to monitor, steal, and manipulate data without setting off alarms.
Who is Behind APTs?
APTs are not random or opportunistic, they are carefully orchestrated by well-resourced threat actors:
Nation-State Groups: Backed by governments, these groups conduct cyber espionage, sabotage, or influence campaigns for political and strategic gain.
Cybercriminal Syndicates: Some APTs are profit-driven, targeting financial systems, stealing data for resale, or engaging in stealthy extortion schemes.
Hacktivist Collectives: Motivated by ideology or protest, these actors may use APT tactics to breach institutions and make a statement rather than seek financial or political leverage.
These groups typically operate with high skill, advanced tools, and long-term objectives in mind.
How to Protect Against Advanced Persistent Threats (APTs)
Patch and Vulnerability Management
In 2024 alone, 2,851 zero-day vulnerabilities were discovered in websites protected by AppTrana WAAP, underscoring how frequently critical flaws are exposed in the wild. According to the Verizon 2025 Data Breach Investigations Report, vulnerability exploitation surpassed phishing as the leading cause of data breaches.
What’s even more alarming is the speed—zero-day vulnerabilities are now being exploited within days of discovery, leaving security teams with an increasingly narrow window to respond. To stay protected against such fast-moving threats and APTs, organizations must implement continuous vulnerability scanning, prioritize rapid patching, and use virtual patching where immediate fixes aren’t possible. These proactive steps help close security gaps before attackers can take advantage of them.
Zero Trust Architecture
Zero Trust assumes no implicit trust—every user and device must be verified. This model reduces the risk of lateral movement by strictly limiting access based on role, device health, and location. Enforcing least privilege and using Multi-Factor Authentication (MFA) are key steps. Even if an attacker gains access, Zero Trust makes it harder to move through the network.
Endpoint and Extended Detection
EDR and XDR tools monitor endpoints for suspicious behavior like privilege escalation or unusual file access. They enable rapid detection and automatic response actions, such as isolating infected systems or terminating processes. Integrating them with a SOC or SIEM platform improves investigation and threat containment.
Network Monitoring and Threat Intelligence
Continuous network monitoring helps detect abnormal traffic patterns, like large data transfers or unexpected communication with external servers. Combining this with threat intelligence feeds allows faster detection of known attack indicators. A strong SIEM setup helps correlate data across systems for better visibility.
User Awareness and Phishing Protection
Since many APTs start with spear-phishing, employee awareness is crucial. Regular training, phishing simulations, and enforcing policies around email attachments or suspicious links can help stop attacks at the entry point.
Segmentation and Encryption
Segmenting your network limits the spread of an attack. Sensitive systems should be isolated with access controls. Encrypting data—both in transit and at rest—ensures that even if data is stolen, it remains unusable.
How AppTrana WAAP Protects Against APT Attacks on Websites and APIs
Advanced Persistent Threats (APTs) are sophisticated, multi-stage cyberattacks that typically target networks, endpoints, and applications. Thwarting them requires a layered security approach that combines tools for all three areas. While endpoint detection and network security solutions play a crucial role, application-layer protection is equally critical—especially as web applications and APIs are increasingly targeted as entry points.
AppTrana waap delivers managed protection against APTs by combining a Web Application Firewall, bot mitigation, API security, DDoS protection, and continuous vulnerability management. It detects unusual behavior through real-time traffic analysis and threat intelligence, allowing its 24×7 security team to respond swiftly and block suspicious activity before it escalates.
AppTrana includes an inbuilt DAST scanner that scans live applications for vulnerabilities, such as SQL injection and XSS. When open vulnerabilities are detected, AppTrana ensures automatic remediation within 72 hours, drastically cutting down remediation windows from months to just 72 hours, preventing potential exploits before they can impact the system.
With its risk-based approach, AppTrana tailors protection based on your application’s exposure, securing APIs and defending against OWASP Top 10 threats. It blocks automated attacks, including credential stuffing and scanning attempts, which are common in APT campaigns. Combined with expert-driven monitoring and continuous rule updates, AppTrana ensures your application remains secure from both known and evolving threats.