What is a Clickjacking? – Types, Examples and Prevention
Clickjacking, also known as UI redress attack or user interface (UI) manipulation, is a malicious technique used to trick users into clicking on elements of a web page without their knowledge or consent.
By overlaying transparent or opaque layers on legitimate web content, attackers can trick users into performing unintended actions, such as clicking on hidden buttons or links.
How Does a Clickjacking Attack Work?
Once a user innocently clicks on an attractive link, the clickjacking attack begins its deceptive process. Here’s a simplified breakdown of how it typically unfolds:
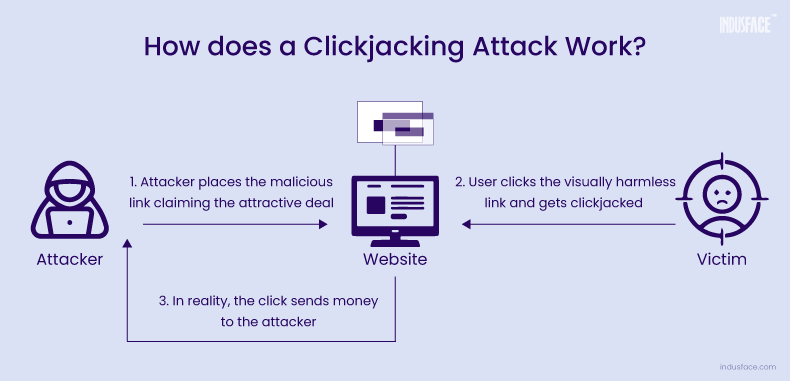
- The attacker discreetly verifies if the user is logged into critical accounts, such as banking or online shopping platforms.
- The attackers manipulate the user interface by overlaying fake buttons or links on top of real ones, creating the illusion of risk-free content.
- When the user interacts with what appears to be a legitimate offer or action, they unknowingly click on the concealed buttons beneath the surface.
- These hidden clicks trigger unauthorized transactions or actions without the user’s awareness or consent.
- While the user is distracted by the fake offer or content, the attacker executes their hidden motive, such as fraudulent transfers or data theft.
- Since the user initiated the actions while logged in, tracing the attack back to the attacker becomes challenging.
In essence, clickjacking exploits user trust and the visual presentation of web interfaces to facilitate malicious activities, posing significant risks to both users and businesses.
Strategies Used in Clickjacking Attacks
Exploiting Vulnerable Applications
Cyber-criminals exploit vulnerabilities in applications, such as the Adobe Flash Player plug-in, to access attached hardware like cameras and microphones.
Transparent Page Manipulation
Attackers leverage browser vulnerabilities to embed authenticated pages within malicious web pages. They selectively hide certain elements of the original application, displaying only controlled elements like form fields and buttons to manipulate user actions.
JavaScript Manipulation
By using JavaScript instead of HTML alone, cyber-criminals can manipulate the user interface in various ways. For example, they may always place a button under the user’s cursor by embedding a malicious webpage in the browser, forcing users to unintentionally click.
iFrame Overlay
Attackers create malicious websites with two components: fake UI code and an iFrame overlay covering part of a legitimate application. This tactic tricks users into believing they are interacting with a legitimate application, leading them to take unintended actions.
Types of Clickjacking Attacks
Likejacking
Likejacking is a type of clickjacking attack specifically targeting social media platforms like Facebook. Attackers overlay deceptive elements on top of legitimate content, tricking users into unknowingly clicking on hidden “like” buttons. These clicks result in the user unintentionally endorsing or sharing malicious content on their social media profiles.
Cookiejacking
Cookiejacking involves exploiting vulnerabilities in web browsers to gain access to cookies stored on a user’s device. Cookies contain sensitive information such as session tokens and authentication credentials, allowing attackers to impersonate users and perform actions on their behalf on targeted websites.
Example:
An attacker exploits a browser vulnerability to access cookies stored on a user’s device. By obtaining the session token from the cookie, the attacker gains unauthorized access to the user’s account on a targeted website, allowing them to perform actions such as making unauthorized purchases or accessing sensitive information. Learn more about the web browser attacks and preventive measures.
Filejacking
Filejacking attacks exploit vulnerabilities in web browsers to gain unauthorized access to files stored on a user’s local file system. Attackers can steal sensitive files or upload malicious files to the user’s device, potentially compromising their privacy and security.
Cursorjacking
Cursorjacking is a clickjacking variant that involves hijacking and manipulating the cursor position to deceive users into clicking on hidden elements on a web page.
Password Manager Attacks
Password manager attacks target vulnerabilities in password management tools and exploit their auto-fill functionality to steal sensitive information. Attackers overlay deceptive forms or input fields on web pages, tricking password managers into auto-filling login credentials or other sensitive data.
The Consequences of Clickjacking
The effects of falling victim to clickjacking attacks can be severe, both for individual users and organizations:
Financial Loss: Clickjacking attacks can result in unauthorized transactions, fund transfers, or purchases, leading to significant financial losses for users.
Data Theft: Attackers can exploit clickjacking to steal sensitive information such as login credentials, personal data, or financial details.
Identity Theft: Clickjacking attacks may facilitate identity theft, enabling cybercriminals to impersonate users and execute fraudulent activities.
Reputation Damage: Businesses that fail to protect their users from clickjacking attacks risk damaging their reputation and losing the trust of their customer base.
Legal Consequences: Inadequate security measures and breaches resulting from clickjacking attacks may expose organizations to regulatory fines, lawsuits, and legal liabilities.
How to Prevent Clickjacking Attacks?
While clickjacking may seem harmless at first glance, it’s a serious threat. It’s not just a playful trick – it’s intended to harm. To protect your finances, customers, and brand reputation, it’s crucial to take steps to prevent these attacks.
Secure web applications from vulnerabilities to prevent unauthorized access. Opt for a managed WAF for round-the-clock defense, immediate vulnerability patching, and continuous threat monitoring, ensuring zero false positives.
The other measures to take to prevent clickjacking attacks are as follows:
Frame Busting
Implement frame-busting techniques in your web application to prevent it from being loaded within iframes on malicious sites. Frame-busting scripts can detect when a web page is being framed and break out of the frame, ensuring that your content is displayed in its intended context.
<script>
if (top !== self) {
top.location = self.location;
}
</script>
This JavaScript code snippet detects if the current window is being framed within another window. Once identified, it executes a breakout from the frame, ensuring the page is loaded in the top-level window, thus mitigating the risk of clickjacking.
X-Frame-Options Header
Set the X-Frame-Options HTTP header to deny or restrict iframe embedding on your web pages. By configuring this header, you can specify whether your content can be framed by other sites, reducing the risk of clickjacking attacks.
For example –
X-Frame-Options: DENY
Set the X-Frame-Options header to DENY to prevent the web page from being loaded in any iframe.
Three permitted values for the header are:
- DENY: disallows any domain/ site to display the page within a frame
- SAMEORIGIN: allows the current page to be displayed in a frame on another page, but only within the current domain
- ALLOW-FROM *uri*: allows the page to be displayed only in a frame on the specified origins/ in a specified URL
However, the security provided by X-Frame options is limited and is ineffective in multi-domain sites.
Content Security Policy (CSP)
Implement a Content Security Policy (CSP) to control the sources from which your web content can be loaded. CSP allows you to define trusted sources for scripts, stylesheets, and other resources, limiting the ability of attackers to inject malicious content into your web pages.
<meta http-equiv="Content-Security-Policy" content="frame-ancestors 'none';">
This meta tag sets a Content Security Policy (CSP) directive to restrict the framing of the web page to prevent clickjacking. The ‘none’ value indicates that the page should not be framed by any precursor pages.
JavaScript Event Handlers
Use JavaScript event handlers to detect and prevent clickjacking attempts. Monitor mouse movements and interactions to ensure that user actions originate from legitimate elements on the page, helping to identify and block clickjacking activity.
window.addEventListener('click', function(event) {
if (event.target !== event.currentTarget) {
// Check if the click event originates from a legitimate element
// Add logic to handle legitimate clicks
} else {
// Handle clickjacking attempts
alert('Clickjacking attempt detected!');
}
event.stopPropagation();
}, true);
This JavaScript code snippet adds a click event listener to the window object. It checks if the click event originates from a legitimate element on the page. If not, it alerts the user about the clickjacking attempt.
UI Redress Protection
Implement UI redress protection mechanisms to detect and mitigate attempts to manipulate the user interface. This can involve techniques such as verifying the visibility and positioning of UI elements to prevent them from being overlaid or obscured by malicious content.
/* Prevent overlapping of elements */
.legitimate-element {
position: relative;
z-index: 9999; /* Ensure the element is on top */
}
Use CSS to ensure that legitimate UI elements have a higher z-index value, making them appear on top of any potentially malicious elements. This prevents elements from being overlaid or obscured by clickjacking content.
Content Verification
Regularly audit and verify the content of your web pages to detect any unauthorized changes or overlays. By monitoring for unexpected modifications to the user interface, you can identify and address potential clickjacking vulnerabilities before they are exploited by attackers.
User Education and Awareness
Educate users about the risks of clickjacking and advise them to exercise caution when interacting with unfamiliar or suspicious web content. Encourage users to report any suspicious behavior or unexpected changes in the user interface to help identify and mitigate clickjacking attacks.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 March 21, 2024
March 21, 2024



