Are you unknowingly victimizing the end-users of your website?
by Venkatesh Sundar, Chief Technology Officer, Indusface
Web applications frequently redirect and forward users to other pages and websites, and use untrusted data to determine the destination pages. Without proper validation, attackers can redirect victims to phishing or malware sites, or use forwards to access unauthorized pages.
The practice of unvalidated redirects and forwards, also often referred to as an “open redirect”, appears fairly benign on the surface. However, it can readily be employed in conjunction with a combination of social engineering and other malicious activity such as a fraudulent website designed to elicit personal information or serve malware.
Example:
Let’s imagine we’ve seen a link to this domain through a channel such as Twitter. It might appear something like this:
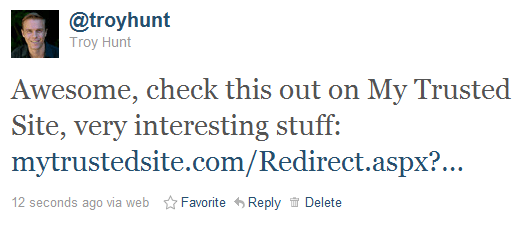
As best as a casual observer can tell, this is a perfectly legitimate link. It establishes confidence and credibility as the domain name is recognizable; there’s no reason to distrust it and for all intents and purposes, clicking on the link will load legitimate content on My Trusted Site. However:
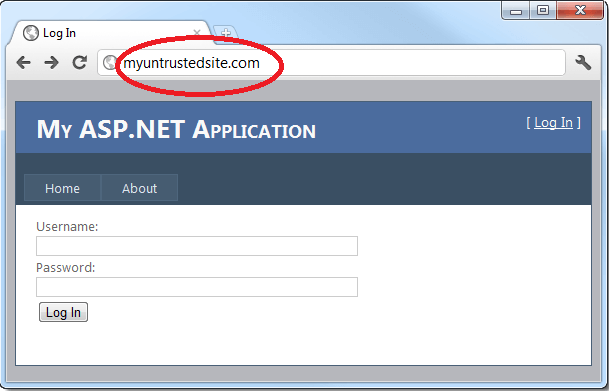
See the problem? It’s very subtle and indeed that’s where the heart of the attack lies: The address bar shows that even though we clicked on a URL that clearly had the hostname of mytrustedsite.com, we’re now on myuntrustedsite.com. What’s more, there’s a login form asking for credentials which you’d naturally expect would be handled properly under the circumstances. Clearly, this won’t be the case in this instance.
What made this possible?
This is a simple attack and clearly, it was made possible by a URL crafted like this:
http://mytrustedsite.com/Redirect.aspx?Url=http://myuntrustedsite.com
The code behind the page simply takes the URL parameter from the query string, performs some arbitrary logging then performs a redirect which sends an HTTP 302 response to the browser:
var url = Request.QueryString[“Url”];
LogRedirect(URL);
Response.Redirect(URL);
The attack was made more credible by the malicious site having a similar URL to the trusted one and the visual design being consistent (albeit both sample implementations). There is nothing that can be done about the similar URL or the consistent branding; all that’s left is controlling the behavior in the code above.
Who’s to blame?
Before getting into remediation, there’s an argument that the attack sequence above is not really the responsibility of the trusted site. After all, isn’t it the malicious site that is stealing credentials?
Firstly, the attack above is only one implementation of an unvalidated redirect. Once you can control where a legitimate URL can land an innocent user, a whole world of other options opens up. For example, that could just as easily have been a link to a malicious executable. Someone clicks the link then gets prompted to execute a file. Again, they’re clicking a known, trusted URL so confidence in legitimacy is high. All the User Account Control (UAC) in the world doesn’t change that fact.
The ability to execute this attack via your site is your responsibility because it’s your brand which cops the brunt of any fallout. “Hey, I loaded a link from mytrustedsite.com now my PC is infected.” It’s not a good look and you have a vested interest in this scenario not playing out on your site.
Is your website vulnerable to ‘Unvalidated Redirects and Forwards’?
The best way to find out if an application has any unvalidated redirects or forwards is to:
- Review the code for all uses of redirect or forward (called a transfer in .NET). For each use, identify if the target URL is included in any parameter values. If so, if the target URL isn’t validated against a whitelist, you are vulnerable.
- Also, spider the site to see if it generates any redirects (HTTP response codes 300-307, typically 302). Look at the parameters supplied prior to the redirect to see if they appear to be a target URL or a piece of such a URL. If so, change the URL target and observe whether the site redirects to the new target.
- If the code is unavailable, check all parameters to see if they look like part of a redirect or forward URL destination and test those that do.
How to Prevent ‘Unvalidated Redirects and Forwards’?
Safe use of redirects and forwards can be done in a number of ways:
- Simply avoid using redirects and forwards.
- If used, don’t involve user parameters in calculating the destination. This can usually be done.
- If destination parameters can’t be avoided, ensure that the supplied value is valid, and authorized for the user.
It is recommended that any such destination parameters be a mapping value, rather than the actual URL or portion of the URL and that server-side code translates this mapping to the target URL.
Applications can use ESAPI to override the ‘send redirect’ method to make sure all redirect destinations are safe.
Avoiding such flaws is extremely important as they are a favorite target of phishers trying to gain the user’s trust.
To know more about Phishing trends: Click here
For Free Website Security scan from malware: Click here
Sources: OWASP, Wikipedia, Indusface Internal Research


 August 1, 2014
August 1, 2014






