Self Service Rules – AppTrana Feature Update Overview
Introducing Self Service Rules, a new addition to our fully managed security suite!
AppTrana empowers you to take control, allowing you to create, view, and manage the custom rules All By YOURSELF!
What are WAF Rules?
WAF rules set the guidelines for how the Web Application Firewall responds when it identifies a match between incoming web traffic and the conditions specified in the security rules.
These settings formalize the enforcement criteria, enabling organizations to define the appropriate responses and mitigation measures for various security threats or vulnerabilities.
AppTrana security rules include two types of rules:
- Predefined Rules – a set of preconfigured rules designed to address common web applications and API security threats and vulnerabilities.
- Custom Rules – The managed security team can set custom rules to tailor the WAF’s protection to the organization’s unique application and security needs.
Here is a detailed blog on how WAF security rules can detect and block known attack patterns
Pre-defined Rules
AppTrana WAAP stands out as a unique turn-key solution due to its comprehensive set of predefined rules. These rules are crafted based on blocklists, known signatures, and IP reputation lists such as HoneyPot Project and spamhaus DB.
Our managed security team ensures regular updates, keeping the rules dynamically adaptive to combat the latest threats.
Download AppTrana Protection WAF Rules Coverage Report
Custom Rules
AppTrana’s custom WAF rules go beyond standard configurations, offering advanced settings for precise control and manipulation of application traffic. With the support of AppTrana’s round-the-clock managed team, organizations can create custom rules tailored to their environment.
Our security experts’ specialized knowledge ensures that the rules effectively mitigate threats, minimize false positives, and deliver optimal protection for web applications.
Latest Feature: Self Service Rules
Nobody understands your web application better than you do. Our self-service rules acknowledge this by allowing you to develop custom rules in the self-service mode that align perfectly with your application’s unique architecture, functionality, and business logic.
By enabling you to take charge, you no longer have to rely on our managed security team for rule creation and configuration.
Note: Adding this feature doesn’t take away the managed services support by Indusface. But, the feature is just an add-on to the overall product offering.
Here is a brief demo of the self service rules feature – a quick walkthrough:
To access this feature, visit the Settings > WAF tab > Custom Rule Categories > Create Custom Rules
Create Custom Rules includes 3 steps:
Step 1: Rule Basic Details
The rule’s basic information is captured in this section.
| Parameters | Descriptions |
| Rule Name | Allows you to provide a descriptive name for your rule |
| Description | It enables you to provide a comprehensive description of the rule’s characteristics |
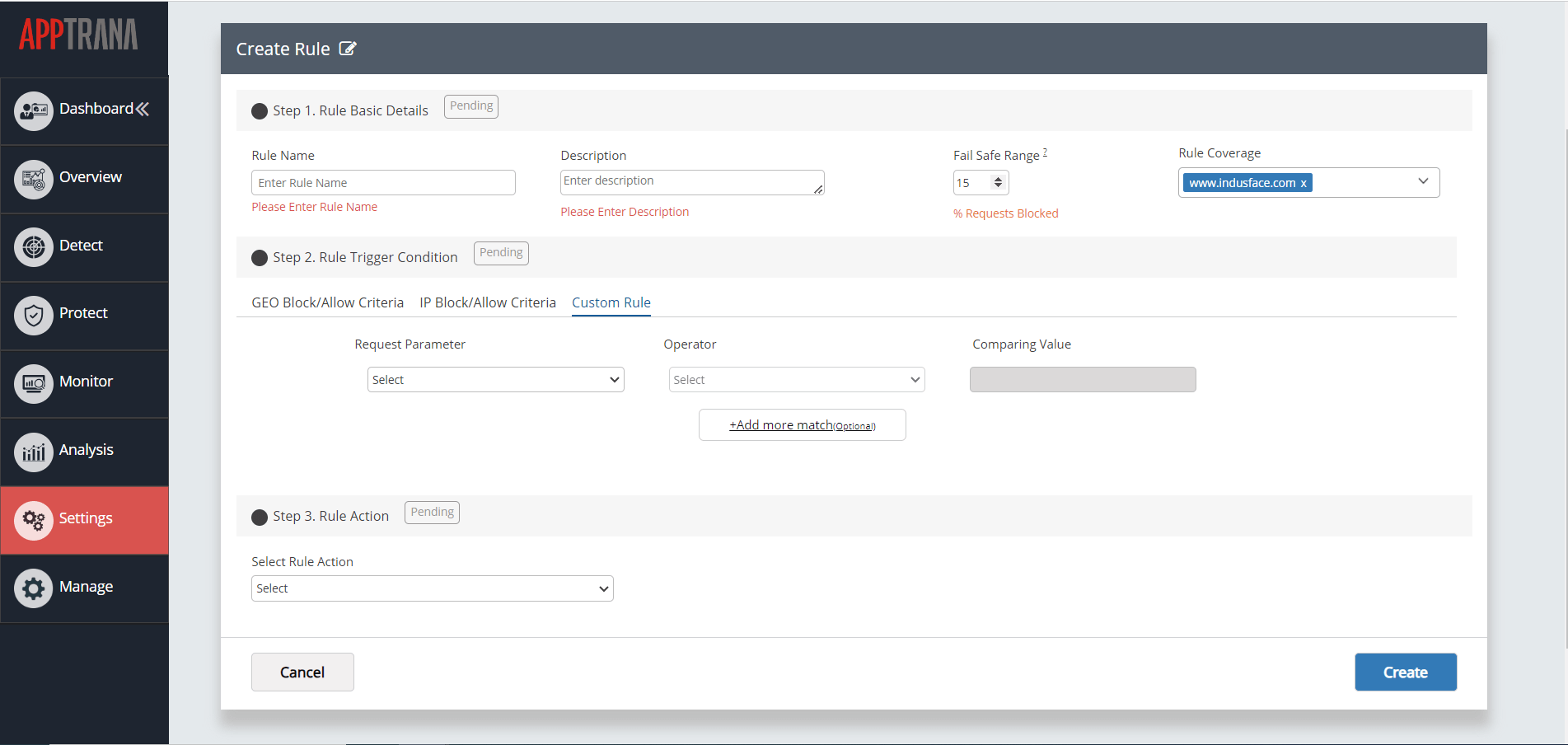
| Fail-Safe Range | The fail-safe range of the rule in percentage value is given here. The ‘Fail-safe range’ ensures that any rule added by a user does not disrupt behaviour of WAF in the event of rules being wrongly created.
This is achieved by moving the rules to ‘log-only’ mode when the % of requests blocked by WAF exceeds the expected % of rules to be blocked. |
| Rule Coverage | Allows you to specify the applications to which the rule will be applied |
Step 2: Rule Trigger Condition
The rule trigger condition refers to the criteria or set of conditions that need to be met for a rule to be triggered or activated within an application.
By defining rule trigger conditions, you can specify the circumstances under which the rule’s actions or protections should be applied.
The section includes three unique criteria categories:
- Geo Block/Allow Criteria
- IP Block/Allow Criteria
- Custom Rule
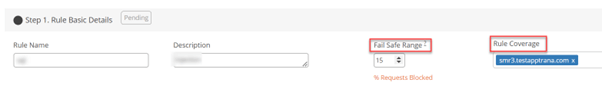
GEO Block/Allow Criteria
The Geo Block/Allow Criteria condition allows you to implement rules based on the geographic location of incoming traffic. You can selectively block or allow access to your web application based on country/countries.
In this criterion, you can select from two different conditions to apply:
- Block req. from selected countries
- Allow req. ONLY from the selected countries (block all other countries)
Geo Block/Allow Criteria Use Case
Suppose you have an e-commerce website that operates globally but wants to restrict access to certain countries due to regulatory requirements or security concerns. You can create a custom rule using the Geo Block/Allow Criteria in this scenario.
Condition: Block requests from selected countries
You can select specific countries you want to block access from. For instance, you may choose to block access from countries known for high rates of fraudulent activities or unauthorized access attempts. Once the rule is applied, any incoming traffic originating from those selected countries will be blocked, preventing potential security breaches.
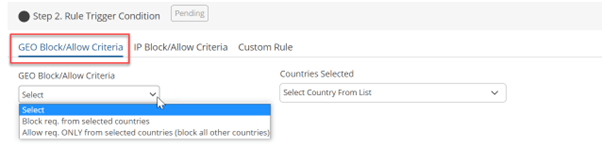
IP Block/ Allow Criteria
This criterion enables users to define rules for IP addresses, granting them the flexibility to allow, block, or whitelist specific IPs.
Within the IP Block/Allow Criteria, you will find three distinct conditions to choose from:
- Allow req. ONLY from the selected IP addresses (block all others)
- Block all req. from selected IP addresses
- Whitelist selected IP addresses
IP Block/Allow Criteria Use Case
Suppose you have identified a suspicious IP address that is repeatedly attempting unauthorized access to your web application. To enhance the security of your system, you can leverage the IP Block/Allow Criteria to create a custom rule.
Condition: Block all requests from selected IP addresses
You can specify the suspicious IP address in the rule configuration and set the rule condition to block all requests from the selected IP address. Once the rule is applied, any traffic originating from that particular IP address will be blocked, preventing further unauthorized access attempts.
Custom Rule
Within the Custom Rule criterion, users can define rules for multiple parameters, including URI, User Agent, HTTP Method, HTTP Referrer, and ARGS.
Each parameter has its own set of rule actions that users can choose from.
| Parameters | Rule actions |
| URI | URI starts with, does not start with, ends with, does not end with, contains, does not contain, equals, and does not equal |
| User Agent | Starts with, Does not Equals to |
| HTTP Method | URI starts with, does not start with, ends with, does not end with, contains, does not contain, equals, and does not equals to |
| HTTP Referrer | Equals to, Does not Equals to |
| ARGS | Starts with, Ends with, Contains, Equals to |
Step 3: Rule Action
This section is exclusive to the Custom Rule Criteria category.
Rule action refers to the predefined response or operation that is associated with a particular rule. It outlines the action to be taken when the rule conditions are met.
Actions for rules with conditions URI, USER AGENT, HTTP METHODS, HTTP REFERRER:
- Whitelist Request and Log
- Skip Rule Category (Whitelist Rule) and Log
- Skip Rule and Log
- Log only
- Block Request and Log
Custom Rule Use Case
Custom Rule to Avoid Cookie Validation to Reduce False Positive
In some instances, strict cookie validation may lead to false positives, causing legitimate user requests to be flagged as suspicious. To prevent such false positives while still maintaining security, you can create a custom rule with appropriate configurations using the Custom Rule criteria.
Instead of blocking requests that fail cookie validation, you can configure the rule to allow those requests to proceed. By setting the rule action to “Allow,” you ensure that legitimate users are not denied access or interrupted by false positive detections.
- Request Parameter: ARGS
- Comparing Value: false cookie
- Rule Action: Skip Rule for Selected ARG
To whitelist specific rules, you can access the Whitelisted Rules field drop-down menu, select the desired rules, and then click the Create button. This allows you to define exceptions for certain arguments and ensure that the associated rules are skipped during the validation.
Take control, create custom rules that align perfectly with your unique application requirements, and upgrade your defense to new heights. To know more about the feature in detail, contact us.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 June 7, 2023
June 7, 2023



