Petya Ransomware Attack: Deadlier Than WannaCry?
Just seven weeks after the WannaCry attack crisis, yet another ransomware attack is wreaking havoc. Dubbed NotPetya because it masquerades as the Petya ransomware, it has already hit more than 2000 computers in a dozen countries.
The attack was first reported earlier yesterday in Ukraine, where computers at banks, metro, state power utility, Kiev’s airport, and several government offices were affected. The extent of damage was such that employees at the former nuclear plant at Chernobyl had to use handheld devices to monitor radiation.
What is Petya Malware?
Petya is malicious software or malware that spreads through emails or websites. Once it is installed on the computer, it blocks access to important files through encryption. If victims do not have a backup, they face losing all the data or have to pay to the hackers for decryption.
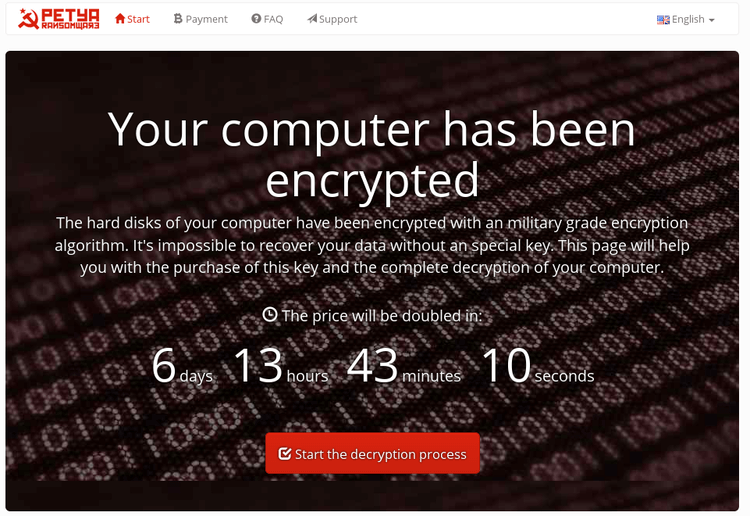
How does Petya Ransomware work?
This ransomware affects Microsoft Windows systems exploiting the EternalBlue vulnerability or through Windows administrative tools. Although Microsoft had released patches for it, not everyone had installed it even after the infamous WannaCry attack.
It encrypts MFT (Master File Tree) tables for NTFS partitions and overwrites the MBR (Master Boot Record) with a custom bootloader that shows a ransom note and prevents victims from booting their computer.
Malware Spread Timeline
9 am: First News
News broke out that several ATMs stopped working in the capital of Ukraine. Just about away, employees at an old nuclear plant were forced to monitor radiation manually as systems went down.
10 am: WPP confirms the hack
The British advertising giant confirms to be a victim of the attack.
10.11 am: Maersk down
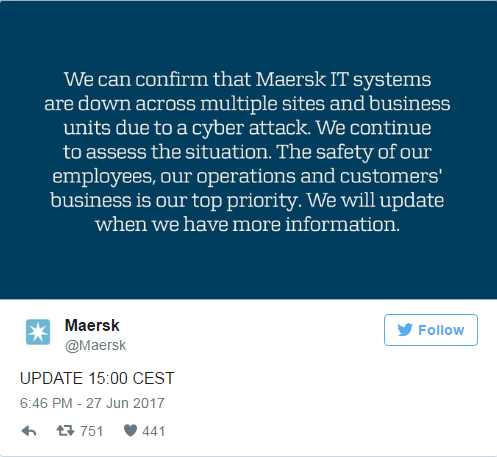
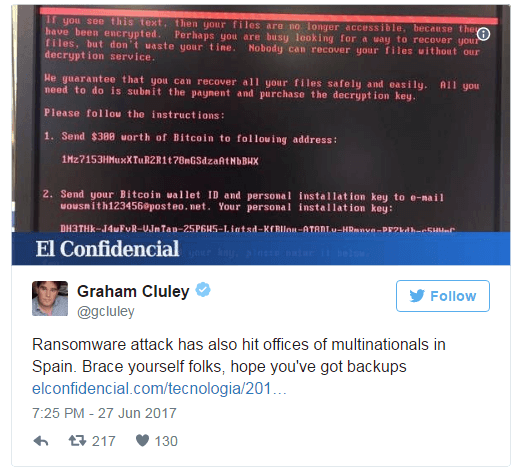
10.27 am: Malware reaches Spain
10.48 am: News from Russia and Ukraine
Russian oil giant Rosneft said that their servers had suffered a powerful cyber attack. Ukraine also reported more attacks at banks and airports.
10.51 am: Malware recognized ‘Petya’
“There have been indications of late that Petya is in circulation again, exploiting the SMB (Server Message Block) vulnerability,” the Swiss Reporting and Analysis Centre for Information Assurance (MELANI) said in an e-mail.
11.12 am: Shipping terminals closed
Maersk’s terminals in Rotterdam completely shut down after data being locked up by the hackers.
11.21 am: Lithuania braces for attacks
Dozens of companies in Lithuania reported attacks
11.45 am: Experts Speak
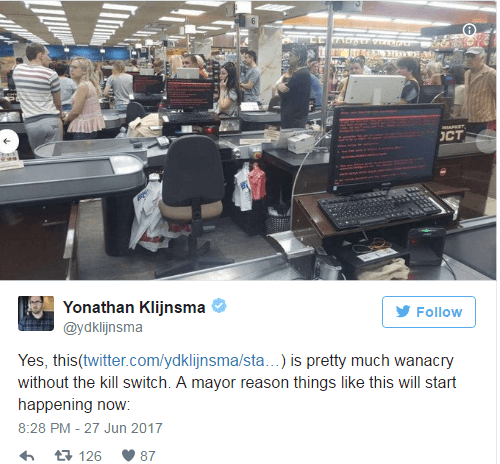
11.56 am: Firms hit in Israel
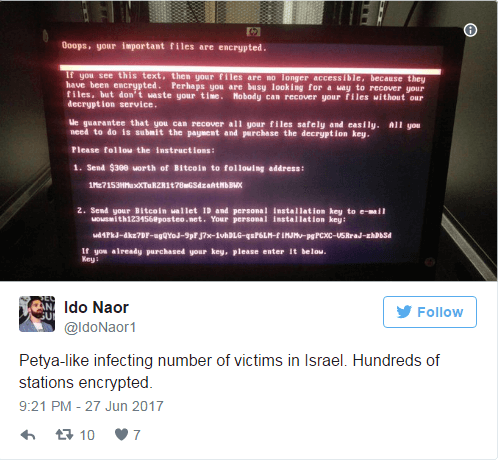
By now, Petya had also affected firms in Ukraine, Russia, Poland, Italy, Germany, and Belarus including pharmaceutical company Merck and law firm DLA Piper.
3.08 pm: Cadbury chocolate factory closed
While Petya wreaked havoc around the world, major incidents were reported in Australia where 50 traffic cameras went offline and Cadbury had to shut down operations in its cocoa coffers.
List of companies affected so far: 1. Rosneft (Russia's top oil producer) 2. A.P. Moller-Maersk (Danish shipping giant) 3. WPP (biggest advertising company) 4. Merck & Co. 5. Russian Banks 6. Ukrainian Banks & Power Grid 7. Ukrainian International Airport 8. Saint Gobain (French construction materials company) 9. Deutsche Post (German postal and logistics company) 10. Germany’s Metro System 11. Mondelez International 12. Evraz (Russian steelmaker) 13. Mars Inc (candy manufacturer) 14. Beiersdorf AG (Indian unit) 15. Reckitt Benckiser (Indian unit)
Secure All Your Computers
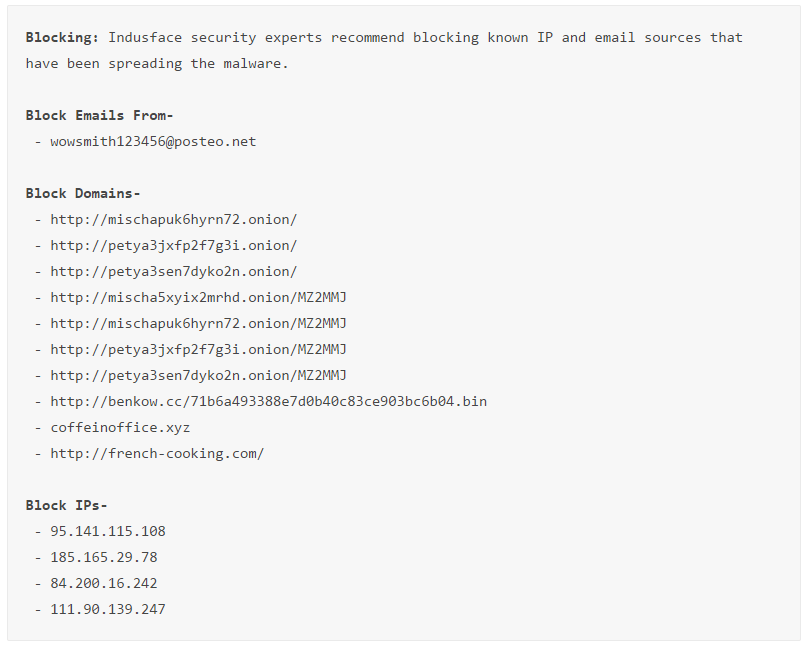
Security Patch: If any of your systems are still using Windows XP, upgrade it to a more recent operating system on priority. For other Windows operating system versions, install this security patch by Microsoft.
Issue Internal Warning: Microsoft has advised users to avoid downloading random attachments and click on links from email senders they do not recognize. You should send out a warning email to all the employees about it.
Disable Server Message Block (SMB) version 1: As a temporary measure, disable SMBv1 on the SMB client and server components.
Update Antivirus: Most leading antivirus providers have issued a patch to monitor the threat, update immediately.


 June 28, 2017
June 28, 2017






