How to Define Risks during a Vulnerability Assessment?
The advancement of technology in today’s digital world has escalated the phenomenon of cyber-attacks, which have been increasing exponentially owing to the technological dependency of humans across the globe. Now, there is a need to question the vulnerability assessment and cybersecurity of the organizations.
It is human to make errors but some errors can carry a lot of destructive power for the organizations as cybercriminals always look for chances to intrude the networks to extract valuable or confidential data. It could be through a processor, server, VPN network, or an operating system; all companies become prone to vulnerabilities at some point or the other.
Cybercriminals are always on the lookout for loopholes in the systems, which is why a 100% safety cannot be guaranteed. This is why it is important to have a comprehensive vulnerability assessment checklist so that you can safeguard yourselves against most of the cyber threats effectively.
To counter new threats, companies must be ready and equip themselves accordingly. This could be their very own traditional way, virtualized, hybrid, and cloud. Generally, companies use vulnerability scanners that automatically search and identify for unpatched software. However, this is not sufficient.
Companies need a proper plan and vulnerability management that includes vulnerability assessment, and the required actions to be taken that protects the overall organization from any external and internal cyber threats.

Vulnerability Assessment – All you need to know
A vulnerability assessment is a process of defining, identifying, classifying, and prioritizing the vulnerabilities in computer systems, software applications, and network infrastructures to help organizations with the necessary awareness and risk background to thoroughly understand the cyber threats.
Importance of vulnerability assessments
Having a vulnerability assessment done provides an organization with the loopholes of the security and gives a proper direction on how to proceed further by understanding the assets, the overall security flaws, and the risks involved. It also helps to reduce cybercriminal activities and protects the organizations.
Non-implementation of vulnerability assessment might get you to face serious consequences like data breaching, injection of malicious files into the computers, and stealing confidential information of the organization.
Types of vulnerability assessments
Discovering the various types of vulnerability assessments depends on network vulnerabilities. These include using a variety of scanners, tools, threats, and risks in order to identify network vulnerability assessment.
With a proper vulnerability assessment checklist, it is easy to proceed with the required vulnerability assessment. Some of the different types of vulnerability assessment the scans include:
- Network-based scans are used to detect network security attacks. This can also detect the vulnerable systems on both the wired and non-wired networks.
- Host-based scans are helpful to identify and locate the possible vulnerabilities on the working stations, servers, and other networks as well.
- This host-based scan detects issues that could cause vulnerability to network-based scans.
- However, it gives great visibility for the patch-based software scanned systems and also for settings of the system.
- Next is wireless network scans of an organization that works on Wi-Fi. It focuses on the most probable point of attacks on the wireless network structure.
- Apart from identifying faulty access points, these can also approve an organizational network whether it is safely configured or not.
- Application scans are used to examine the websites for detecting the most known software vulnerabilities or for any possible errors in the configuration in the network.
- Database scans help to identify the faulty connections in the database to prevent cyber-attacks, like spam, injecting malicious software and SQL injections, and many more.
What more you should know about vulnerability assessment?
As our topic suggests, a vulnerability assessment is a process to identify the vulnerabilities that the normal network and systems scan cannot locate for an organization. This has various vulnerability assessment checklists and procedures that properly identify and detect the scope of the vulnerabilities.
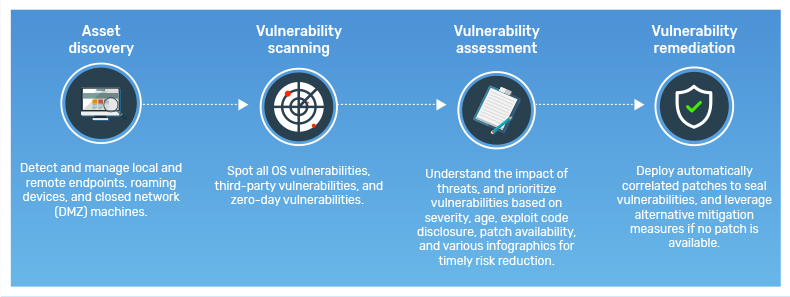
Often, this is referred to as a vulnerability assessment or sometimes a penetration testing. A vulnerability assessment makes use of the available network security scanning tools and these are reported on the assessment report. And the organization should fix these vulnerabilities according to the report.
Therefore, the organizations must implement vulnerability assessment checklists and network vulnerability tests on a timely basis to make sure that if any changes are made on network security. These changes made could be adding another network, opened ports, or new activity recorded.
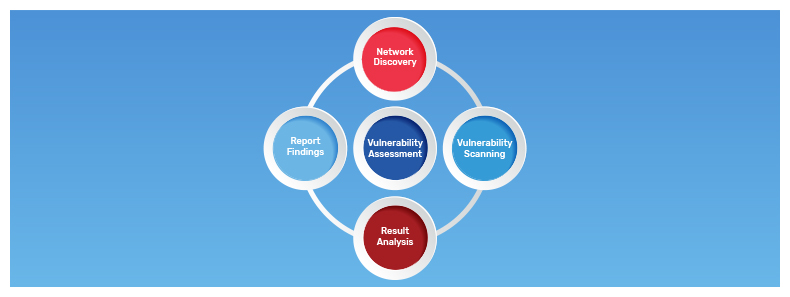
Moving further in the topic, let us discuss the different analysis for vulnerability assessment.
1. Threat assessment
This is the basic step towards vulnerability management or assessment. So a threat assessment considers all the factors, like natural, criminal, accidental, and terrorist threats for any given situation.
However, the ISC standard only addresses man-made threats. But the other agencies can expand the cause of the threats if they feel it is important. All the information should be taken into consideration to carefully evaluate the situation.
Each threat level is divided into a specific quantity of tests. Large numbers of assessments are performed by a team of cyber experts. Here are some of the threat levels listed below:
Man-made (Defined): This is a defined man-made threat assessment. The cybercriminals will target a specific area in the organization.
Man-made (Credible): These are the cyber attackers who use tactics to acquire information about the targets. There could be any previous history of the same attack that they possibly do again.
Occasionally, there could be no threat identified or received by the enforcement agencies. Moreover, this kind of incident occurs periodically every 10 years. Man-made potential threats also utilize the tactic the same way as an above credible man-made threat, but there is no specific target in this.
2. Vulnerability assessment
The main aspect of a vulnerability assessment is estimating the potential loss from the recent or successful attack and also the vulnerability to that organization or an area. A key aspect of the vulnerability assessment is a proper definition of the ratings for the loss and also the vulnerability. However, these may vary from each one.
We have provided a sample of definitions that might help you to assess the vulnerability assessment to a great level. These are the definitions for the organizations that generate revenues and a public sector.
Devastating: As the name suggests, this is beyond the regular use of the product or the facility. Here most of the items can be lost, damaged, or even destroyed beyond repair. The organization might malfunction for up to 75% over time.
Severe: So the product or the facility is partially damaged. Examples include structural breaching, or breaching of weather, water, fire, or any kind of damage to some areas. But the facility remains standard and intact and the leftover facilities may be moved to other locations to protect from the damage.
The number of visitors could be reduced to 50% for some time.
Noticeable: In this kind of noticeable assessment when the facility is either temporarily closed or can operate for a few days with disruption. Only several assessments could figure the damage and the majority of the facilities may function normally. The estimated reduction might be around 25% for only a limited time.
Minor: Minor damages that have no significant impact on the smooth operations of the organization and there is no major loss for the organizations.
3. Risk analysis
An organization can assess the risk analysis by the loss ratings and the vulnerability ratings. These can be used to evaluate the risk of the organization from a threat. These are classified as the following loss rating and the relevant vulnerability ratings.
Very high: As the analysis indicates, this is dangerous and immediate safety measures must be taken to avoid any loss.
High: This risk isn’t acceptable either. It needs immediate checks and necessary measures should be taken to minimize the loss or the damage.
Medium: This is the period where we cannot overlook the damage that has already been caused. Proper planning and steps should be taken to control further loss or damage.
Low: Low risks are acceptable and can be rectified through proper security measures. Make sure these do not increase in the danger graph for the organization.
Upgrade recommendation
By going through the above-mentioned findings or the analysis, the next step is to come up with safety measures to cope up with the loss or the damages. An organization needs to upgrade to the next level to avoid any of these cyber threats that happened earlier.
These countermeasures should be included in the risk upgrading recommendation list.
If any other additional measures are available, it can be upgraded so as to be helpful to address other unknown cyber threats for the organization.
Re-Evaluation of Risks
The re-evaluation of the risks mentioned above should be implemented for better cybersecurity and also for stern structural security of the organization. These security upgrades have an overall positive impact on vulnerability issues that the organization is facing.
Conclusion
To conclude this topic, we can say that cyberattacks and threats are common and also change in the way they occur through the times. Every organization should implement vulnerability management and assessment, assessment checklists, and should start the vulnerability assessment and vulnerability management program on the applications first. Application vulnerability assessment automatically covers the network components it interacts with, and most importantly, is the central point of any digital business and service. So, if you mitigate the risk of your applications, you mitigate the risks of your business. Getting expertise on this front on a continuous basis can be a challenge, which is why it is highly recommended to partner with experts who can offer products for assessment and provide management around it for a living.


 June 23, 2020
June 23, 2020



