Fundamentals of Origin Server Protection
Modern web applications rely on distributed architectures where content delivery, caching, and security often happen away from the core application. The backend environment that stores your web server, APIs, and data is known as the origin server. It is the true source of your digital experience.
Even when layers of CDN, proxy, and WAF are in place, attackers look for ways to reach this core directly. Once they succeed, the results can include downtime, data theft, or full service disruption. Understanding how to protect your origin server is therefore a basic requirement for every IT and security professional.
What Is an Origin Server?
In simple terms, an origin server is the backend machine that holds your application’s original content and logic. When a user requests your website or API, that request first hits various intermediaries such as CDNs, reverse proxies, or web application firewalls. These may cache or filter the request before it reaches the origin.
Think of the CDN and WAF as your fortress walls. The origin server sits inside, storing the most valuable assets such as application code, databases, and configuration. Every asset not cached at the edge ultimately comes from the origin. That is why it is both valuable and vulnerable.
If an attacker discovers your origin IP or exploits a weak configuration, they can bypass all those protective walls and strike directly at the core. This is why origin server protection is one of the most important security fundamentals.
Why Origin Servers Are a High-Value Target
Attackers are drawn to origin servers because they provide both access and leverage.
Access to sensitive data
The origin layer interacts with databases and internal APIs. If a vulnerability such as remote code execution or SQL injection is found here, attackers can exfiltrate data or move laterally into other internal systems.
A single point of failure
Even in a distributed setup, the origin server is usually the last stop for every request. A denial-of-service attack or a simple configuration error at this level can take the entire application offline.
Bypass potential
Organizations often believe that a CDN or WAF completely hides the origin. In reality, mistakes like exposed DNS records, leaked IPs, or unrestricted ports make it easy for attackers to connect directly. Once that happens, all edge protections are bypassed.
Common Threats to the Origin Layer
Several categories of risk can compromise an origin server. The most frequent include:
Application Vulnerabilities
Unpatched CMS plugins, legacy frameworks, or poorly validated input can expose critical flaws. Attackers automate scans to find such weak points at scale.
Server-level Vulnerabilities
Misconfigured SSL/TLS settings, outdated OS kernels, or open admin ports create opportunities for privilege escalation or remote takeover.
Direct-to-Origin (D2O) Attacks
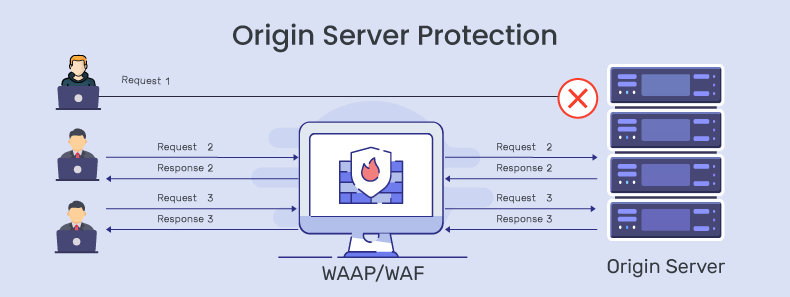
Attackers can identify origin server IPs through open-source techniques such as regex searches on search engines or by scanning exposed DNS records. Once they find the IP address, they can launch direct-to-origin DDoS attacks that completely bypass WAF defenses. Instead of targeting the public domain, the attack traffic goes straight to the origin server (for example, 153.42.1x.5xx), where no edge filtering applies.
Because these requests never pass through your WAF, its rules and rate limits offer no protection. Implementing an allow-list policy on origin servers can help reduce this risk, but it is often complex because WAF and CDN providers use dynamic, geographically distributed IP ranges. As a result, many WAAP vendors include secure origin access as an enterprise-level add-on. Before deploying any WAAP, confirm which origin protection features are available by default and which require an additional configuration or license.
DDoS Attacks
Even when a CDN absorbs volumetric floods, attackers may still target the origin with smaller but sustained Layer 7 requests that consume resources and cause outages.
Credential and Configuration Leaks
Code repositories, DNS records, or third-party integrations can accidentally reveal the origin address, allowing attackers to connect directly.
Building a Resilient Origin Protection Strategy
Protecting the origin requires multiple layers of visibility, testing, and control.
1. Maintain Complete Visibility
The first step is knowing what you have. Maintain an updated inventory of all applications, subdomains, and APIs that point to your origin. Regular discovery scans help uncover forgotten assets or IPs that are still reachable from the internet. Clear mapping ensures you know which assets are actually routed through your WAF.
2. Test Continuously
Penetration testing and vulnerability scanning help you find exploitable flaws before attackers do. Combine automated scans with manual validation to ensure findings are real and not false positives.
Integrating dynamic testing tools within your CI/CD pipeline allows early detection before new deployments go live. The faster you identify a risk, the faster you can patch or virtually patch it.
3. Patch and Harden Regularly
Unpatched systems remain a leading cause of breaches. Keep your operating systems, web servers, and frameworks updated with the latest security releases.
Use configuration management tools to enforce baseline security settings. Disable unused services, apply strong authentication for administrative access, and isolate the origin in a separate subnet. Simple hygiene steps like enforcing least privilege and using multi-factor authentication prevent many incidents.
4. Use CDNs and Load Balancers Wisely
A content delivery network helps serve cached content from edge locations and reduces the load on your origin. This improves performance and absorbs many volumetric attacks.
Load balancers distribute traffic across multiple origin servers, adding both scalability and redundancy. However, always configure your origin to accept traffic only from known CDN or load-balancer IP ranges. If you do not, attackers can still send requests straight to the backend.
5. Enforce Strict Access Controls
Only trusted intermediaries should reach the origin. Implement IP allow-lists so that requests come only through approved WAF, CDN, or reverse proxy routes.
Where possible, establish private connections between your edge and origin using secure tunnels or private networking. Examples include AWS PrivateLink or Cloudflare Tunnel. Keeping the origin off the public internet is one of the strongest controls available.
6. Deploy a Web Application and API Protection (WAAP) Layer
A WAAP solution monitors both web and API traffic for malicious payloads, bots, and DDoS behavior. It should sit in front of your origin and inspect every incoming request.
Make sure the origin IP is hidden, that all requests are routed through the WAAP, and that regular tests confirm there are no bypass paths.
Managed WAAP solutions that include 24×7 monitoring can also apply virtual patches when new vulnerabilities are discovered, reducing the time between detection and protection.
Misconfigurations That Expose the Origin
Even well-managed systems can become vulnerable because of small oversights. Common issues include:
- Origin IPs appearing in DNS or SSL certificate details.
- Direct HTTP or HTTPS access enabled without restriction.
- Outdated allow-lists after the CDN or WAF provider changes IP ranges.
- Shared environments where staging or testing servers reside next to production.
- Weak or self-signed SSL certificates on the backend.
Periodic origin exposure tests can help catch these problems before they are exploited.
Measuring the Strength of Your Protection
Security cannot improve without measurement. A few practical indicators include:
- Drop in direct-to-origin traffic after implementing allow-lists.
- Time taken to patch vulnerabilities after discovery.
- Number of validated vulnerabilities per testing cycle.
- Mean time to mitigate ongoing attacks.
- Ratio of requests served from CDN versus those reaching the origin.
These metrics reveal whether your protection layers are performing as intended.
Defense in Depth and Operational Discipline
Origin protection is only one layer in a complete defense strategy. Other elements such as identity management, secure coding, and real-time monitoring also play a vital role.
No single tool can guarantee safety. Strong protection comes from disciplined processes, consistent visibility, and continuous validation. When every team understands which assets are public and which are private, the chances of accidental exposure drop significantly.
How AppTrana Protects Origin Servers
Organizations that want a managed and automated approach can use AppTrana, a Web Application and API Protection (WAAP) platform from Indusface. AppTrana combines continuous monitoring, AI-based detection, and a 24×7 managed security team. The service ensures that only legitimate traffic reaches your origin and that any new vulnerability or attack pattern is addressed quickly through virtual patching.
To learn more about how AppTrana prevents attackers reach origins directly, read Preventing WAF Bypass: How Attackers Target the Origin Server. Together, these two articles provide a clear view of why origin server protection matters and how to achieve it in practice.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.
Frequently Asked Questions (FAQs)
An origin server is the backend system that stores the original version of your web application, database, and APIs. Even if you use a CDN or WAF, attackers who find the origin’s IP address can bypass those layers and target it directly. Protecting the origin prevents downtime, data leaks, and unauthorized access to critical infrastructure.
Attackers use methods such as DNS lookups, regex searches on search engines, certificate transparency logs, or leaked configuration files to identify exposed IP addresses. Once they have the IP, they can perform scans or launch direct-to-origin (D2O) DDoS attacks that bypass the WAF entirely.
A Direct-to-Origin attack occurs when attackers send requests straight to the backend server’s IP address instead of the public domain name. Since this traffic avoids edge protection like WAF or CDN filters, it can overwhelm or exploit the server directly. These attacks are often used to take down applications or exfiltrate sensitive data.
The most effective method is to restrict access to the origin so that only approved intermediaries such as the WAF or CDN can connect. This involves IP allow-listing, private network tunnels, and regular origin exposure testing. Continuous monitoring and managed WAAP services can also help detect bypass attempts early.
Typical errors include leaving the origin IP visible in DNS records or SSL certificates, failing to update allow-lists when a CDN provider changes its IP ranges, or hosting staging environments on the same network as production. Each of these missteps can make the origin reachable from the public internet.
Not always. Some WAAP vendors provide origin protection and private connectivity only in enterprise-tier plans. Before deployment, verify which features are included by default and whether secure origin access or IP allow-listing requires additional configuration or licensing.

 October 24, 2025
October 24, 2025







