CVE-2025-31650 – Apache Tomcat DoS Risk via HTTP Priority Header
The Apache Software Foundation has disclosed a high-severity vulnerability in Apache Tomcat that could let attackers exploit improperly handled Priority headers in HTTP/2 to cause a denial of service (DoS).
Tracked as CVE-2025-31650, this flaw stems from improper input validation, specifically when the server handles malformed Priority headers in HTTP/2, resulting in memory leaks and potential OutOfMemoryExceptions.
Given Tomcat’s widespread use in enterprise Java deployments, the impact of this vulnerability is far-reaching. Administrators and security teams should treat this as a priority, especially since no authentication is required to exploit the flaw—making it ripe for automated exploitation.
CVE-2025-31650 – Risk Analysis
Severity: HIGH
CVSSv3.1: Base Score: 7.5 HIGH
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
Exploit available in public: Yes
Exploit complexity: Low
Apache Tomcat’s HTTP/2 module mishandles malformed HTTP Priority headers, failing to clean up memory after rejecting invalid requests. Instead of discarding these malformed requests safely, Tomcat fails to properly release memory associated with failed requests. This incomplete clean-up leads to a memory leak. If an attacker sends a large volume of such requests, the server eventually runs out of memory and crashes—resulting in a denial-of-service condition.
Affected Versions
- Apache Tomcat 9.0.76 – 9.0.102
- Apache Tomcat 10.1.10 – 10.1.39
- Apache Tomcat 11.0.0-M2 – 11.0.5
This attack requires no authentication, meaning that any unauthenticated attacker can flood a server with invalid requests and bring it down.
Potential Impacts of CVE-2025-31650
1. Denial of Service (DoS)
The most direct outcome is that the application becomes unavailable to legitimate users. This is particularly damaging for customer-facing services or critical business operations.
2. Resource Depletion
Repeated memory leaks can exhaust system resources, slow down performance, and cause other unintended behaviors.
3. Operational & Business Risks
- Increased troubleshooting time
- Urgent patching requirements
- Service-level agreement (SLA) violations
- Damage to user trust or reputation
CVE-2025-31650 – Mitigation and Recommendations
The Apache Software Foundation urges users to upgrade to fixed versions:
- Apache Tomcat 9.0.104
- Apache Tomcat 10.1.40
- Apache Tomcat 11.0.6
If an upgrade is not immediately feasible:
- Apply rate limiting to control excessive malformed requests.
- Use a Web Application Firewalls (WAFs) to block malicious HTTP headers.
- Monitor for sudden spikes in memory usage or unusual request patterns.
Why Input Validation Matters
This vulnerability highlights a classic case of improper input validation—a recurring weakness in software development.
Failing to validate input like HTTP headers can lead to unexpected behaviors such as:
- Memory corruption
- Resource exhaustion
- Application crashes
Best Practices for Input Validation
- Validate all inputs server-side, even if client-side checks exist.
- Use a whitelist/allowlist approach—only allow known, expected values.
- Enforce limits on length, format, and type of input.
- Canonicalize input to a standard format prior to validation.
- Conduct regular audits to identify edge case vulnerabilities in input processing.
AppTrana WAAP Coverage for CVE-2025-31650
To immediately mitigate the Apache Tomcat DoS vulnerability (CVE-2025-31650), the managed security service team has rolled out a dedicated security rule to block exploitation attempts targeting malformed or malicious Priority headers.
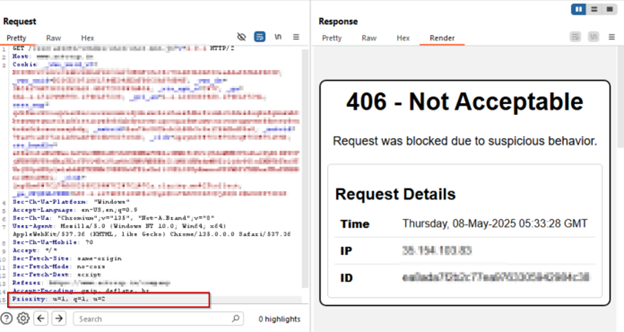
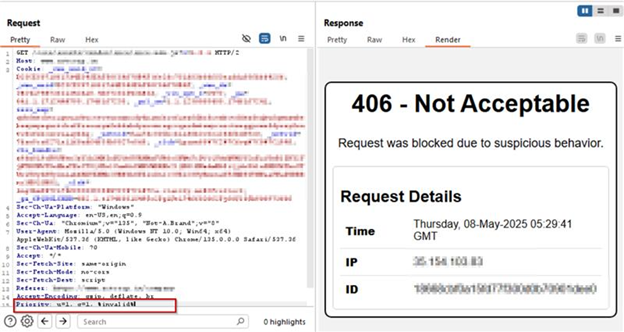
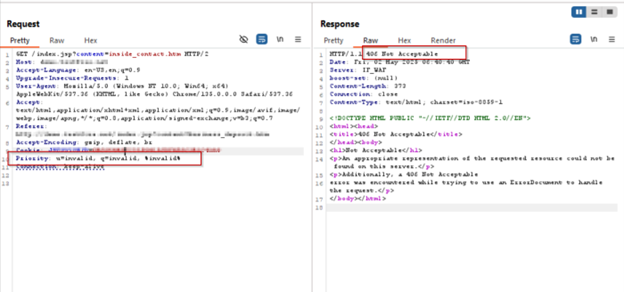
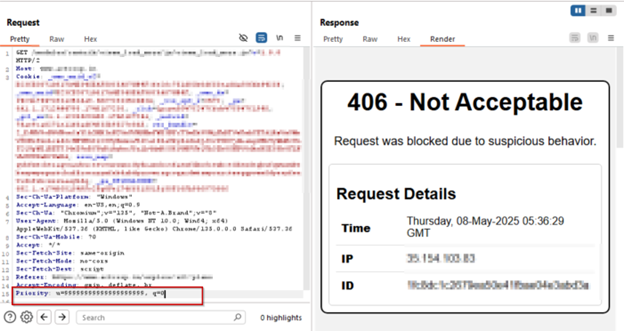
AppTrana WAAP’s custom rule effectively blocked CVE-2025-31650 exploitation attempts during proof-of-concept (PoC) simulations, as illustrated in the following screenshots.
Payload 1: u=1, q=1, u=2
Payload 2: u=1, q=1, %invalid%
Payload 3: u=invalid, q=invalid, %invalid%
Payload 4: u=99999999999999999999, q=0
Key Protection Features:
- AI/ML-Based Anomaly Detection: AppTrana uses machine learning to identify deviations from normal HTTP behavior, flagging suspicious patterns even if they don’t match a known signature.
- Behavioral-Based Rate Limiting: The WAAP analyzes traffic behavior over time and dynamically throttles suspicious request spikes—especially those targeting HTTP/2 endpoints—without impacting legitimate users.
- Real-Time Mitigation: All malicious payloads are intercepted in real time, preventing memory exhaustion or server instability.
- Zero-Day Defense: The WAAP is continuously updated with new rules to combat emerging threats—helping organizations stay secure even during the window between disclosure and patch deployment.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 May 8, 2025
May 8, 2025



