Adobe ColdFusion Vulnerabilities Exploited in the Wild
Adobe ColdFusion, a popular web development platform, has been targeted by malicious actors exploiting the recently disclosed vulnerabilities, including severe CVE-2023-29300. The exploit has been observed in the wild, posing a significant risk to organizations and individuals relying on the software.
Here is an in-depth analysis of these vulnerabilities, including their potential impacts and vital protective measures to protect against these attacks.
Recently Disclosed Vulnerabilities on Adobe ColdFusion
Adobe ColdFusion is a versatile and powerful web development platform known for its rapid application development capabilities. It enables developers to create dynamic websites and web applications using its server-side scripting language, ColdFusion Markup Language (CFML).
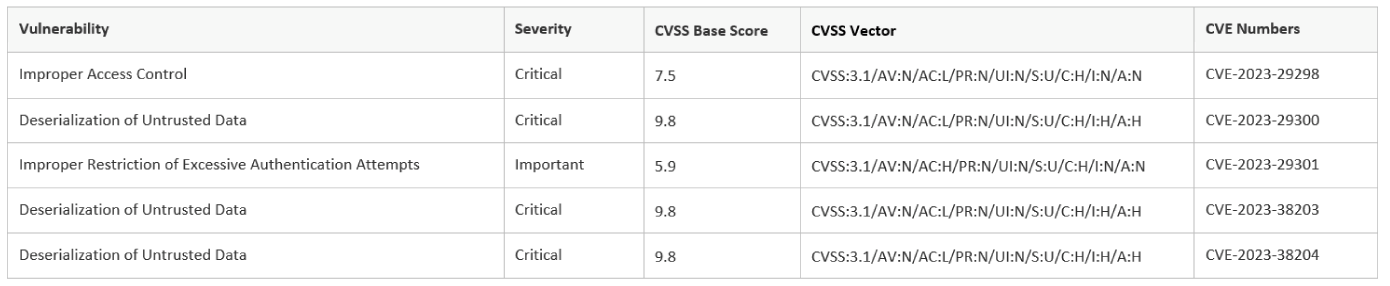
Adobe recently disclosed three critical vulnerabilities:
- CVE-2023-29298 – Improper access control, potentially leading to security feature bypass
- CVE-2023-29300 – Deserialization of untrusted data poses a severe threat as it allows remote code execution, potentially enabling attackers to take control of the system
- CVE-2023-29301 – Improper restriction of excessive authentication attempts, could lead to the bypassing of security measures
Adobe released security updates on July 11, addressing these critical vulnerabilities in its ColdFusion versions 2023(Update 1), 2021(Update 7), and 2018(Update 17). These updates effectively mitigate the risk of potential threats such as arbitrary code execution and security feature bypass, making it crucial for users to apply these patches promptly.
Observed Exploit Attempts
On June 12, Project Discovery disclosed a n-day exploit targeting CVE-2023-29300 for which Adobe published a patch for the deserialization vulnerability on July 11. However, during their disclosure, Project Discovery accidentally detailed CVE-2023-38203, a new zero-day exploit (subsequently taken down) chain.
On July 13, Multiple exploitation attempts of Adobe ColdFusion were observed that chained CVE-2023-29298 and CVE-2023-38203, resulting in the execution of PowerShell commands to create a web shell for access to the targeted endpoint. In most cases, the webshell is detected residing in the \wwwroot\CFIDE directory.
.\ColdFusion11\cfusion\wwwroot\CFIDE\ckeditr.cfm
To address the vulnerability (CVE-2023-29300) related to WDDX functionality, Adobe faced a challenge, as removing it entirely would disrupt dependent processes. As a solution, they opted not to prohibit WDDX data deserialization entirely, but implemented a denylist of specific Java class paths that are not allowed to be deserialized. This approach ensures security while preserving functionality for Adobe ColdFusion versions 2023, 2021, 2018, and earlier users.
However, the Project Discovery experts discovered a functional gadget using the class (com.sun.rowset.JdbcRowSetImpl), which was not part of Adobe’s denylist. This gadget enabled remote code execution through deserialization, leading to the revelation of a new 0-day vulnerability (CVE-2023-38203) that acted as a bypass for CVE-2023-29300.
On July 14, Adobe issued patch fixes for CVE-2023-38203 (a bypass for CVE-2023-29300), a deserialization issue that could lead to arbitrary code execution.
However, in the latest blog (earlier taken down) shared by Project Discovery, they mentioned that the previous exploit seemed to be working even after applying the patch for CVE-2023-38203.
The researchers found a mistake in Adobe’s filter-matching process. When input Lcom.sun.rowset.JdbcRowSetImpl; was provided; it successfully matched and blocked the payload. The filter expected only the “L” and “;” characters and replaced them with an empty string. However, if the input was Xcom.sun.rowset.JdbcRowSetImplX did not find any match leading to another bypass.
On July 19, Adobe released a new update that resolves the patch bypass issue and has assigned the vulnerability identified as CVE-2023-38204.
Affected Versions
The following versions of ColdFusion are vulnerable:
- Adobe ColdFusion 2023 Update 1 and earlier
- Adobe ColdFusion 2021 Update 7 and earlier
- Adobe ColdFusion 2018 Update 17 and earlier
Mitigation
Customers must upgrade to the latest available versions of Adobe ColdFusion vulnerabilities to patch these vulnerabilities:
- Adobe ColdFusion 2023 Update 3
- Adobe ColdFusion 2021 Update 9
- Adobe ColdFusion 2018 Update 19
For more information, please refer to the Adobe Security Advisories on APSB23-40, APSB23-41, and APSB23-47.
CVE Details:
Protecting Against Vulnerabilities: AppTrana WAF Coverage
Customers using AppTrana WAF have enhanced protection for these vulnerabilities. The following WAF rules offer protection against these vulnerabilities:
- 99855 – Adobe ColdFusion Vulnerability Policy (Adobe ColdFusion Deserialization)
- 99856 – Adobe ColdFusion Vulnerability Policy (Adobe Cold Fusion Access Control Bypass)
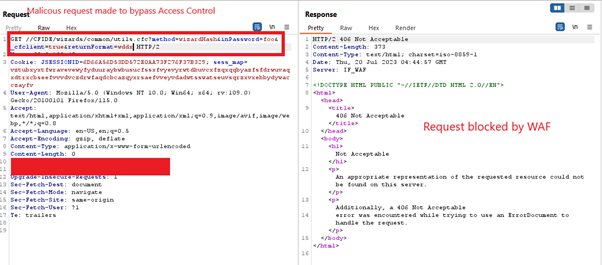
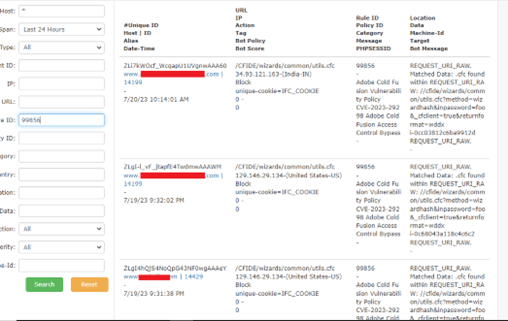
The screenshot below showcases how AppTrana WAF prevents ColdFusion vulnerability exploitation attempts, effectively blocking malicious requests.
CVE-2023-29298
CVE-2023-38203
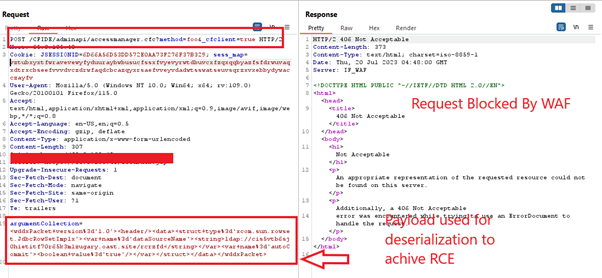
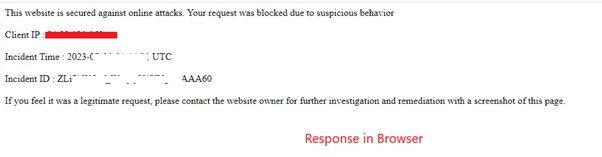
The following screenshots depict the example logs detected by our security rules:
99855 – CVE-2023-38203 Adobe ColdFusion Deserialization
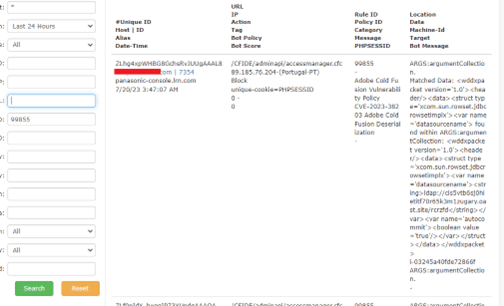
99856 – CVE-2023-29298 Adobe Cold Fusion Access Control Bypass
Given the active exploitation of these critical vulnerabilities, securing your ColdFusion environment becomes paramount. Employing essential security updates, strong patch management practices, and leveraging the capabilities of AppTrana WAF vulnerability management, you can effectively shield your systems and defend against evolving threats.
References:
- https://blog.projectdiscovery.io/adobe-coldfusion-rce/
- https://www.rapid7.com/blog/post/2023/07/17/etr-active-exploitation-of-multiple-adobe-coldfusion-vulnerabilities/
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 July 20, 2023
July 20, 2023



