20 API Security Tips Every Enterprise Should Implement
Cloud services have made the world a highly interconnected ecosystem. Enterprises leverage services (virtual and physical) provided by other enterprises rather than build them from scratch, creating a web of connected devices, applications, and users. An API is one such service.
An Application Programming Interface (API) allows different programs to connect. The PayPal API, for example, can be used by an e-commerce store to collect payments rather than build a payment gateway of their own. It’s evident why APIs are useful – they deliver the necessary function while saving the enterprise time and effort.
API security solution involves protecting these APIs and all connected apps and users from security threats and breaches.
This article covers 20 API security tips that enterprises should implement immediately.
Why is API Security Important?
Enterprises use APIs to connect applications and platforms, connecting to the database that stores sensitive user information. A compromised API can quickly lead to attacks on connected applications and, worse, the loss or theft of user data.
API security is the responsibility of the company that developed it and the one that uses it.
20 API Security Tips Every Enterprise Should Implement
1. Implement a Secure Authentication and Authorization Protocol
Authenticating and authorizing the right users is the first step in API security strategy. Access points are the first point of attack, and attackers attempt to exploit flaws in the authentication process of the API to gain temporary or permanent access to accounts.
There are a couple of ways to tighten authentication and authorization security:
- Basic authentication via username and password with the requirement for complex passwords
- The use of API keys where unique identifiers are configured for each connecting application
- Using OAuth for login
OAuth is probably one of the best ways to implement maximum authentication security. It enables SSO convenient for the user and eliminates the need to send the username and password to the API server, preventing the credentials from being phished.
2. Use the ‘Least Privilege’ Principle
In information security, ‘least privilege’ involves giving users or applications access only the data and operations they need to perform their functions properly.
Here are a few ways to implement the principle of least privilege within an API:
- Keep the principle of least privilege in mind when developing the API
- Perform regular access audits and evaluate the API calls being made to identify overprivileged apps (apps that have access to data or operations they don’t need access to)
- Revoke the permission overprivileged apps have to unnecessary data and operations
By limiting access to only necessary operations, the attack surface is reduced, and this helps limit the exposure to security breaches.
3. Limit Data Sharing
One way of minimizing API vulnerabilities is by minimizing exposure. For a product to work, data is shared between APIs, APIs and applications, and APIs and users. This could be access data like tokens, user data, JSON code, etc.
As the amount of data being shared between nodes increases, the risk exposure also increases. A mechanism like OAuth works well against security threats – it reduces the data being shared between platforms to an authorization key rather than the user’s credentials, so in case of an attack, the attacker does not get any useful information.
Track the data being shared between apps, APIs, and users to identify points of vulnerability and then secure them by limiting the shared data.
4. Always use HTTPS
An HTTP connection does not protect data and can be highjacked to steal information.
An HTTPS connection, on the other hand, encrypts most of the data and helps secure the connection. An HTTPS connection guarantees three things:
- Authenticity – The connection has been made with the real API or application and not an imposter
- Confidentiality – All data (metadata, cookies, and so on) is encrypted and secure
- Integrity – The data being transferred can be trusted and has not been modified or tampered with
APIs use an HTTP connection, to begin with and require Secure Sockets Layer (SSL) or Transport Layer Security (TLS) encryption to secure the data being transferred.
API Economy and Why Effective Security is Important
5. Store Passwords Securely with One-Way Password Hashing
Ensuring APIs have a strong strategy for password storage is vital to minimizing security breaches.
APIs that use basic authentication (username and password) have to store this data within a database. If the database is hacked by an external threat or accessed internally by a bad actor, user credentials can be stolen and used to access personal accounts.
One way of protecting credentials is by hashing passwords before committing them to the database.
Hashing uses a hash function (like SHA-1) to convert an input string of any size to a hashed string of a fixed size. For example:
Input data of different characters and lengths are converted to fixed-size hash keys.
Unlike encryption which has a decryption key that can extract the original data from the encrypted output, the output of a hashing function cannot be reversed to obtain the original data.
When a user tries to log in, the API will hash the entered password and match it against the stored hash. The hash will be the same only if the entered password is the same, and this is how users are authenticated.
If the database is compromised, all the attacker gets are hashed strings that cannot be reversed to get the original data.
6. Enforce a Zero-Trust Policy
When it comes on API security Tips, we can exclude the zero-trust policy. It assumes that every user, device, and server is untrusted until proven trustworthy.
The conventional verification model is to trust some connections based on predefined protocols, for example, a connection made from a device within the company network or by a user who has accessed the API before. Any connection from outside this predefined perimeter is asked to authenticate and verify itself before it can access data.
In the zero-trust model, all connections (with absolutely no exceptions) are asked to authenticate before they can access resources. This greatly reduces security risks.
7. Have a Holistic Approach to API Security Testing
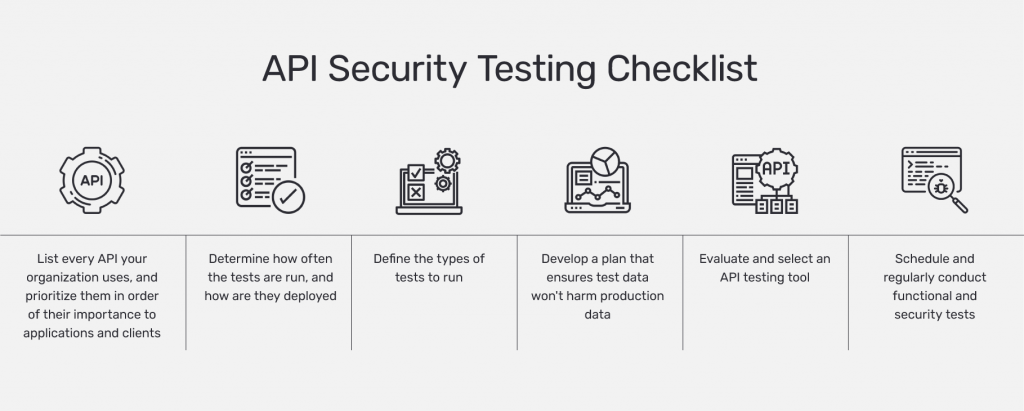
When it comes on API security tips, adopt a holistic approach to testing is the one that we can’t skip. Assume anything that can go wrong and test every aspect of the API for security vulnerabilities. Some tests that can be performed are:
- Parameter tampering – Test what parameters being sent between APIs can be tampered with
- Command injection – Test if the API is vulnerable to code injection
- Input fuzzing – Test to check if data passed between APIs can be modified
- HTTP methods – Test if any URL is sending data over an unencrypted connection
8. Use Application Priority Buckets
Applications can be sorted into buckets based on their priority – apps that are most used, used the longest, rarely used, and so on. Ideally, these buckets should be dynamic, and apps should automatically move from one bucket to another depending on which one they are best suited to.
Different policies can then be applied to each bucket to improve API security strategy without hampering the performance of apps.
9. Encrypt Data Using TLS
It’s prudent to encrypt all data handled by the API, whether it is Personally Identifiable Information (PII) or connection data being transmitted. Encrypted data cannot be misused, even if attackers somehow steal it. One way of encrypting data in transit is by using TLS with REST/API.
10. Consistently Audit the API Build
With technology, there’s always room for improvement. Maintain an audit cycle wherein the API build is audited regularly. Test for vulnerabilities, errors, and other build issues that attackers can exploit. Always maintain audit logs to track version updates and bug fixes.
11. Keep Vendors in The Loop
Whenever an update or a patch is rolled out (most often after an audit), make sure all API users are aware of it and stress the importance of updating to the latest version.
With APIs, security is not limited to the business that develops it but also encompasses the vendors who use it. If a vendor’s application or server is attacked because of vulnerability in the API, both the vendor and the API developers are responsible.
Use email, push alerts, in-app messages, and other forms of communication to deliver the news of a patch to all vendors, and actively monitor which vendors have not updated their API version.
12. Implement Data Logging
Next on our list of API security tips is data logging. Logs are incredibly useful in troubleshooting issues and finding solutions, enabling server and application-level logging.
Define a retention period for these logs, so there is enough historical data to identify breaches much after they have occurred while also ensuring storage space isn’t exceeded.
Logs help with manual inspection and monitoring and give admins a ton of information that can be used to improve API security.
13. Set API Rate-limiting
API limiting, or API rate limiting, is enforcing a limit on clients’ quantity or size of data being requested (or consumed).
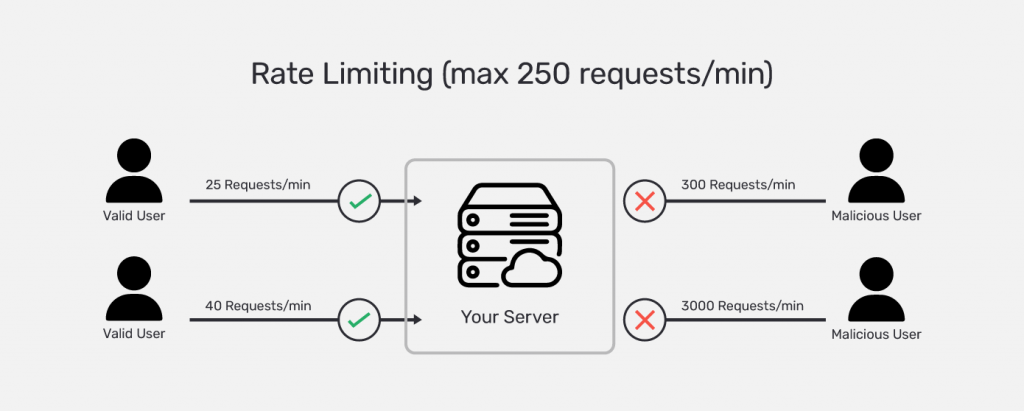
The number of connections being made, and the size of requests affects the API’s performance. Allowing unrestricted access can result in excessive connections, which will cause the API server to lag and eventually crash, which happens in the case of a Denial of Service (DoS) attack. In a DoS attack, attackers continuously send large volumes of requests to overload and crash the server, denying service to actual users.
Applying API rate limits helps mitigate the risk of API crashes. Admins can limit the number of requests and transactions per request to maintain balance and optimum performance.
14. Implement Monitoring and Alerting Software
Another great way of proactively mitigating security threats is implementing monitoring and alerting software (like SCOM, for example). These platforms monitor API calls, logs, and other aspects of the API to detect anomalies and alert admins, who can then take preventive or reactive measures to address security threats.
It also provides an opportunity to implement other API security tips more easily.
15. Follow the OWASP API Security Guidelines
The non-profit foundation Open Web Application Security Project (OWASP) listed a set of 10 API security guidelines in 2017. The priority of the reasons for security breaches was updated in 2021, and they are as follows:
- Broken access control
- Cryptographic failures
- Injection
- Insecure design
- Security misconfiguration
- Vulnerable and outdated components
- Identification and authentication failures
- Software and data integrity failures
- Security logging and monitoring failures
- Server-side request forgery
Addressing each of the potential vulnerabilities in OWASP API Top 10 is a great way to approach API security, and when starting, this list can act as a blueprint.
16. Perform Content Negotiation
Content negotiation is a method of serving data and resources dynamically over the same URL. Different versions (in terms of language, extension, format, and so on) of the same resource are delivered to users based on certain predefined criteria.
Implementing content negotiation within the API server allows users to build applications that leave content negotiation to the API’s server reducing the chances of a security breach.
17. Scan Every API Request
API requests are vulnerable to attacks like phishing and tampering. The parameters within the request URL, for example, can be tampered with to trick the API into providing sensitive user data.
Scanning every API request for anomalies will help mitigate this threat. There are solutions available (like Fiddler, for example) that monitor API requests and provide actionable information through a UI.
Comprehensive Risk-based API Protection
18. Define Data Processing Security Measures
Securing all data processing services and operations is vital to API protection. This includes identifying and verifying users, authorizing access based on level, logging and reporting access events, etc.
Creating an API guide that defines data processing operations will help implement each operation’s security measures.
19. Sanitize Input
User inputs are used by functions to access the database and retrieve information and are therefore a security vulnerability. Code injection, for example, is a security threat where an attacker passes code through an input field that gets executed on the API server.
One way to mitigate this risk is through input sanitization. Input sanitization is a cybersecurity strategy of checking, cleaning, and filtering input data that is sent to the API of unwanted characters and strings. This prevents bad actors from injecting malicious code and breaching the API server.
20. Implement Web Application and API Protection (WAAP)
The list of API security tips will be incomplete without WAAP. With the widespread use of cloud services, most businesses use at least one application hosted on the web (as opposed to a complete on-prem infrastructure). Web applications and connected APIs are accessed via the internet and are more susceptible to breaches.
Traditional physical Web Application Firewall (WAF) devices are no longer enough to secure web apps and APIs. Web Application and API Protection, or WAAP, is a security tool specifically built to protect web applications and APIs.
WAAP addresses the flaws in conventional security devices and protocols and increases the security of web apps and APIs.
Conclusion
With technology and the internet, security is a constant effort. Unfortunately, security threats will not cease to exist, and as technology like IoT becomes more common, the vulnerabilities and risks will only increase.
While security breaches are frightening, steps can be taken to prevent them and protect users, devices, and applications. The key is being proactive – in monitoring existing technology, fixing vulnerabilities, and incorporating modern cybersecurity solutions.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 May 31, 2022
May 31, 2022






