What is Single Sign-on?
Single sign-on is a user authentication method process that gives rights to a user to enter one name and password in order to access multiple applications the user owns. In this authenticates the user for all the applications they have been given permits to and eliminates further prompts & actions when they switch applications during a session.
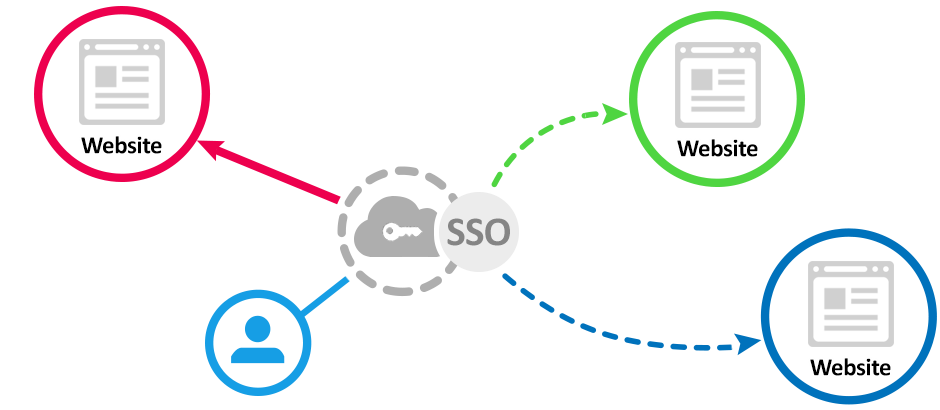
How SSO works?
When someone (using a browser) sends an HTTP request for access to a protected resource, a policy agent intercepts the request and examines it. In case of invalid SSO session token (In order to provide proof of authentication) is found, the policy agent contacts the server which then invokes the authentication and authorization processes. In order to access a protected resource, the requestor needs to be authenticated and have the authorization to access the resource.
SSO Process
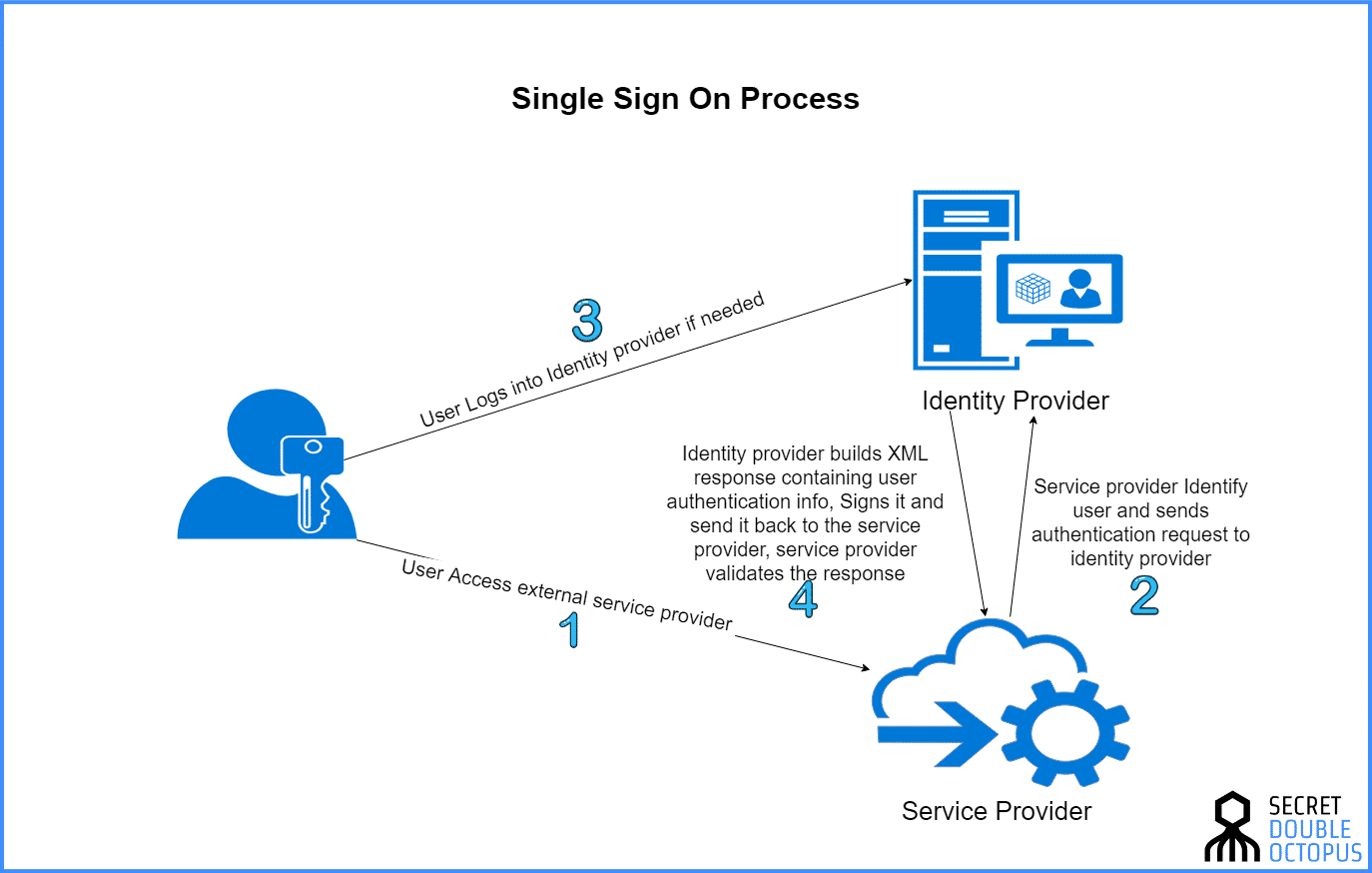
5 Types of Single Sign-on (SSO)
1. Basic Web Based SSO
- Browser-based application
- Cookie support is required
- Applications deployed on a single web server (domain)
2. Cross-Domain SSO
- Multiple realms that manage user credentials.
- A user authenticated in one area gets signed-on to an application using another area.
3. Federated SSO
- Extend SSO across enterprises.
- Users from each company/organization get access across each other’s web properties. Hence, federated SSO provides an authentication token to the user which is trusted across organizations. So, the user does not need to create a different account for every organization in the federation to access web properties and applications.
- Liberty Alliance, OASIS, IBM/Microsoft.
4.Password Synchronization
- Passwords across multiple computers and devices and/or applications.
- Each computer, device, the application still authenticates but, on the backend.
- Products: MTech’s P-Synch, SecurePass, SAM Pass Synch
5. Enterprise SSO
- Enterprise or Employee SSO.
- After the main authentication, it intercepts advanced login prompts and fills them for you.
- Learns as you use different apps.
- Screen Scraping
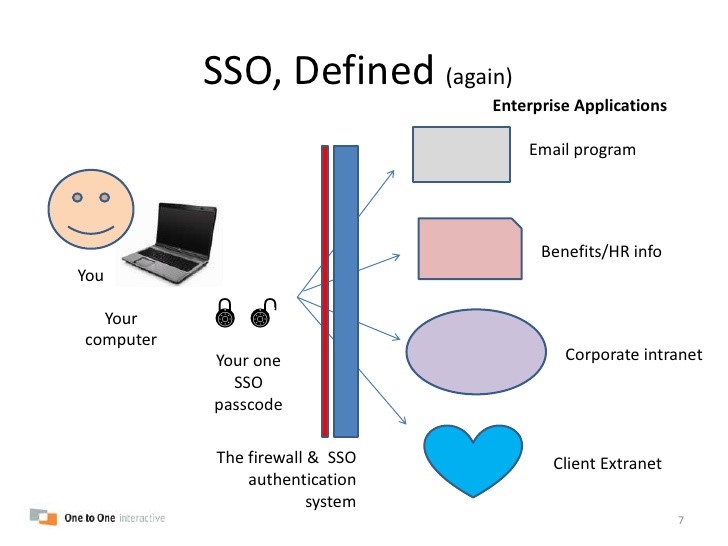
Benefits of Single Sign-on (SSO) (Enterprise Applications)
SSO Authentication Methods
- Passwords
- One Time Passwords
- Tokens and Smartcards
- Digital / Machine Fingerprints
- Biometrics
Why SSO? (Pros)
- It eliminates the requirement for users to memorize multiple usernames/emails and passwords beyond their initial login.
- It helps reduce work to the Help Desk about locked accounts and forgotten usernames and passwords.
- Solo-entry point to the corporate network and its useful resources.
- Better user experience.
- Advanced Security to Systems (e.g. Smart cards, On-time Tokens)
Disadvantages of an SSO (Cons)
- Critical impact in case of credentials exposed.
- Complex Logic and pitfalls.
- It should be combined with strong authentication methods like (Smart cards, One-time Tokens).
General Security Principles
- Implement Authentication with Adequate Strength
- Enforce Least Privilege
- Protect Data in Storage, Transit and Display
- Enforce Minimal Trust
- Log and Trace User Action
- Fail Securely and Gracefully
- Apply Defense in Depth
- Apply Security by Default
Authentication Flaws
- Mandatory to restrict access to validated users.
- Strength depends on application risk/data classification.
- Compliant with regulations/standards.
- Provide for secure password and account management.
- Mitigates brute-forcing and credentials harvesting.
- Mitigates Man in The Middle Attacks (MiTM).
Authorization Flaws
- Flaws in Role-Based Access Controls (RBAC)
- Flaws regarding horizontal and vertical privilege escalation & forced browsing.
Session Management Flaws
- Session cookies and authentication tokens unprotected (e.g. clear text) between client and server.
- Missing session invalidation at idle-timeout and user logout.
- New session token to prevent re-use for authentication.
- Non-secure storage in a session in cleartext.
- Lack of strong random generation of session cookies and identifiers.
- Lack of coordinated session between application tiers.
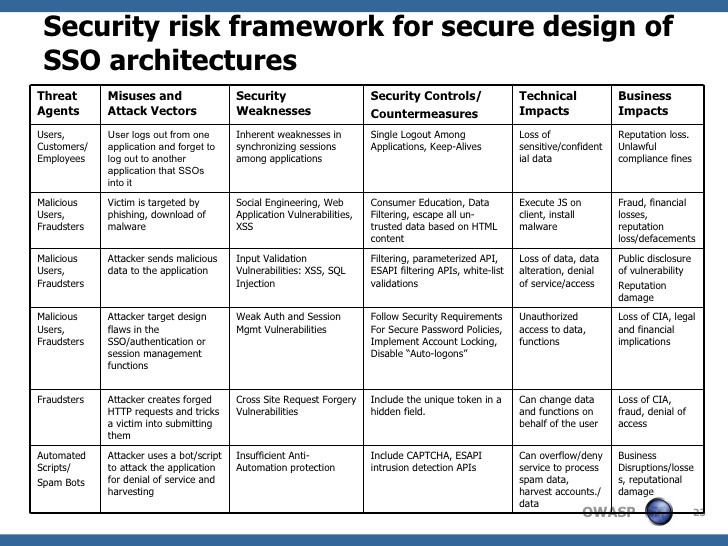
A Security Framework for SSO Architectures (OWASP)


 May 24, 2019
May 24, 2019



