Understanding Cloud DDoS Attacks and Cloud-based DDoS Protection
Today’s organizations can’t ignore the flexibility and cost savings granted by cloud computing technologies. With increased demand to deliver services or applications with a minimal budget, migration to the cloud continues. Enterprises are increasingly adopting cloud technologies and hosting their apps on cloud environments. As more businesses are relying on the cloud-based services, DDoS attacks (Distributed Denial of Service) becomes a general and critical attack on the cloud, which proves extremely damaging.
Fortunately, we have a wide range of options to address this attack. Application-based DDoS mitigations are one of the best options. However, its limiting scale-up architecture is no longer adequate to track a large amount of traffic flow records as well as individual IP addresses, which operationally characterize today’s cloud-based solutions. The enterprise should opt for the best of breed DDoS protection, which inherent cloud’s distributed nature to globally safeguard services from cloud DDoS attacks. This is called cloud-based DDoS protection.
Alarming DDoS Attacks 2020
The main reason that cloud DDoS attacks has become easier and cheaper to execute is due to the proliferation of IoT (Internet of Things) devices. Most of the IoT products are available with default access credentials, which aren’t reset – it becomes easy for attackers to take control of them. Attackers can compromise hundreds of thousands of vulnerable IoT products to generate traffics to take targets down. However, owners of the insecure IoT devices are unaware that they have been conceded and their traffic-generating power is being used to take the targets offline.
2020, the toughest year in all our lives. Adding to this is the largest reported Distributed Denial of Service attack.
In June 2020, AWS mitigated 2.2 terabits of DDoS attacks, which could have made thousands of their clients’ services unavailable for an unknown period. AWS also stated that the cloud DDoS attack size was 44% larger than the data volume recorded earlier on the amazon network.
AWS were not the only victims, other network hosts in different parts of the world are suffering from the cloud DDoS attacks.
In August and September 2020, several organizations across the world saw a series of DDoS attacks. Kaspersky compared the number of DDoS attacks in Q3 and Q2 of 2020 and Q3 of 2019 and reported that there is 1.5 times increase in the total attack in Q3 over Q3 of 2019.
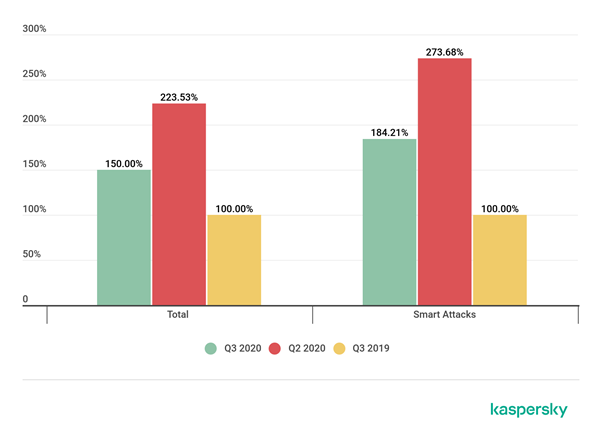
Netscout reveals that Q1 and Q2 of 2020 witnessed a change in the methodologies of DDoS attack – faster, shorter, and harder-hitting multi-vector attacks, which expect to continue. Hackers focused to attack online platforms and services essential in the digital world like education, financial services, e-commerce, and healthcare.
One of the main reasons for the large surge in cloud DDoS attacks is the financial benefits that these attacks offer. Bulletproof’s “2019 Annual Cyber Security Report” states that DDoS attacks can cost a lot of money. A small company could lose from $120,000 to $2 million if they become a victim of a DDoS attack.
Further, CISCO Visual Networking Index predicts that the number of global DDoS attacks is expected to double by 2023.
No matter the adversary, target, or methodology used, it is important that organizations should remain vigilant in these challenging days and leverage cloud-based DDoS protection solutions to protect their critical infrastructure.
What Does Modern Cloud DDoS Attacks Look Like?
The impacts and patterns of DDoS attacks are different between traditional physical data centers and Clouds. The limited aim of DDoS attacks is killing a service availability and impair customer experience. Without cloud DDoS mitigation, which can distinguish valid traffic from malicious, it is unusual for cloud DDoS attacks go unnoticed. Instead, just as they do in physical data centers, it ruins the customer experience in cloud environments.
The cloud infrastructure offers abundant benefits and opportunities to businesses and the same set of the offering are available as well as useful for attackers. Auto-scaling, pay-as-you-go, and multi-tenancy are three main features, which stands behind the success of the cloud paradigm.
An infrastructure cloud typically has several servers ready for handling virtual machines in virtualized multi-tenant environments. While aiming cloud DDoS attack, attackers might target to attack economic sustainability factors of cloud consumers. With a few other contributions, this attack has been known as the FRC (Fraudulent Resource Consumption) attack. Attacks plant trojans and bots on insecure machines over the target web services and the Internet with DDoS attacks. Few organizations also called Booters provide a network of bad bots to their users to plan cloud DDoS attacks on their competitor’s sites. The intentions of these attacks range from political rivalry, extortion, business competition, to cyberwars among countries.
Consider the scenario where an attacker who planned a cloud DDoS attack sends enough fake requests. In a cloud environment, these requests would generate severe resource utilization on the target server. An auto-scaling feature of cloud would take this overload position as feedback and add more resources including, CPUs, storage, web servers, and other network resources to the existing pool of this VM resource.
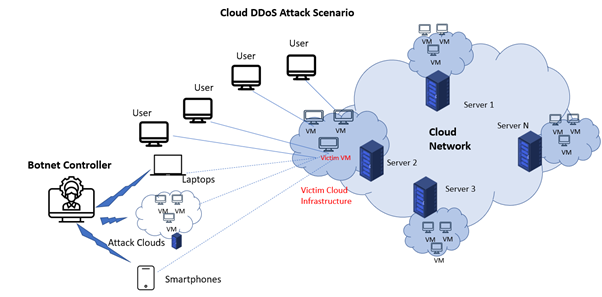
Overloaded VM may include some resources and upgraded to a higher resource capacity server. If there is no cloud-based DDoS protection system in place, this process will continue to add the resource till the consumer can pay or the cloud service provider uses all the resources. Lastly, it will result in Service Denial, which causes major trouble to service availability. This kind of flooding will raise the cloud usage bill drastically and thus economic losses over the planned budget.
When it comes to cloud DDoS attacks and cloud DDoS Mitigation, pricing, or accounting plays a major role. Generally, consumers are charged on an hourly basis. Cloud instances can be allotted on a pay as you go basis, fixed basis, and by auctions. Likewise, network bandwidth and storage are measured based on the total size as well as data transfer in and out.
Effects of Cloud DDoS Attacks
Direct Effects
- Economic Losses due to downtime
- Service Downtime
- Dependent Service Downtime
- Scaling Driven Economic Losses
- Business and Revenue Losses
Indirect Effects
- Smoke screening Effects
- Cloud DDoS attack mitigation costs
- Reputations & brand image losses
- Energy consumption Costs
- Collateral Damages in Cloud
Get URI-Based DDoS Protection for your Applications
Using Cloud-Based DDoS Protection for Uncompromised Protection
Inline DDoS protection solutions installed on-premises at the company’s data center are powerful enough to detect and mitigate DDoS attacks at network layer, application, and SSL-based layer DDoS attacks. On-premises DDoS mitigation includes several benefits like, consumes less time to detect as well as mitigate DDoS attacks.
However, one significant drawback with on-premises DDoS protection is that it is not enough to safeguard against huge volumetric DDoS attacks, which flood the internet pipe. Cloud DDoS attacks use hundreds of thousands of packets per second to render downstream.
Furthermore, on-premises DDoS mitigation can defend applications in the organization’s data center, and ineffective in protecting web apps hosted on cloud infrastructures. Some organizations are limited with in-house expertise to install and manage the DDoS protection appliances.
Cloud DDoS protection services overcome these challenges. Cloud-based DDoS protection service absorbs mass volumetric cloud DDoS attacks and filters out legitimate and malicious traffic. This alternative solution for cloud DDoS mitigation can be categorized into:
- Always on Cloud-based DDoS Protection – in this category, traffic of an organization is always channeled through a local POP (Point of Presence) – thereby it detects and mitigates all kinds of cloud DDoS attacks at all layers before they reach the organization’s services. This method offers a practical approach to cloud DDoS protection.
- On-demand Cloud-based DDoS Protection – In this category, traffic of an organization is routed to a cloud-based scrubbing center only when the massive volumetric traffic is detected. In this cloud DDoS mitigation method, internet link utilization is tracked with remote monitoring periodically. If a breach of a specific threshold occurred, the cloud-based DDoS protection measure triggers a diversion of the inbound traffic to the cloud scrubbing center.
- Hybrid Cloud-based DDoS Protection – This cloud DDoS mitigation service combines the service of on-premises DDoS protection and Cloud-based DDoS protection services and ensures most of the benefits of both alternatives while avoiding their drawbacks. On-premises protection mitigates most DDoS attacks locally and employs cloud DDoS mitigation for volumetric attacks.
Indusface’s AppTrana offers cloud-based DDoS protection services. Its unified DDoS protection solution built to detect and mitigate all kinds of DDoS attacks delivers automated DDoS mitigation with a consistent security policy and a top-notch reporting feature for visibility and control. Its market-leading cybersecurity solutions featuring not only the cloud-based DDoS mitigation service, but also generate protection against zero-day attacks.
The Closure
As companies become more dependent on the internet and cloud paradigm for routine tasks and critical processes, cloud-based solutions will be crucial to avoid downtime. Managed cybersecurity services and Cloud DDoS protection services remain the keys to the frontline of defense against application-layer DDoS attacks and helping to ensure your end-users can always reach your website.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 November 23, 2020
November 23, 2020





