SessionReaper (CVE-2025-54236): Impact, Detection, and Mitigation
SessionReaper (CVE-2025-54236), an unauthenticated vulnerability in the Commerce REST API enables session takeover and possible RCE. If you run Adobe Commerce or Magento Open Source, this critical, pre-auth vulnerabilities can let attackers hijack customer accounts, manipulate orders, and in many real-world setups drop persistent PHP web shells on your servers.
Adobe released an emergency hotfix; public PoCs and mass exploitation activity followed, so you must apply the official hotfix immediately and hunt your environments for indicators of compromise.
What is SessionReaper(CVE-2025-54236)
SessionReaper (CVE-2025-54236) is a critical improper input validation vulnerability in Adobe Commerce / Magento Open Source that allows an unauthenticated actor to take over customer sessions and, in many realistic deployments, to escalate to pre-auth remote code execution (RCE).
Risk Analysis
Severity: CRITICAL
CVSSv3.1: Base Score: 9.1 CRITICAL
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N
Exploit available in public: Yes
Exploit complexity: Low
Root cause: improper input validation in the ServiceInputProcessor (Web API) that accepts and deserializes nested input types. The validation is insufficient, enabling crafted API requests to bypass expected type constraints and cause the backend to deserialize attacker-controlled payloads. Under some configurations (notably file-based PHP session storage or certain deserialization paths), this leads to remote code execution; at minimum it enables session takeover via the Commerce REST API.
Why it is critical: it is pre-auth (no user interaction required) and directly affects session handling and deserialization, two high-impact areas. That explains the high CVSS and the account takeover / RCE potential.
All Adobe Commerce/Magento 2.4.x versions are affected and must be patched immediately.
Impact / Real World Outcomes
- Account takeover: attackers can hijack customer accounts (order history, stored payment tokens, address changes, etc.). Adobe and several vendors report account takeover as the primary scenario.
- Remote code execution (RCE): technical analyses and POCs show that, in common configurations (especially file-based session storage), attackers can escalate to unauthenticated RCE and drop PHP web shells, giving persistent server access. Multiple researchers described nested deserialization enabling RCE.
- Observed effects in the wild: mass probing, PHP backdoors/web shells dropped, phpinfo() reconnaissance and enumeration. Security vendors documented hundreds of attempts and many confirmed backdoors discovered in stores.
Key Indicators of a SessionReaper Compromise
- Unauthenticated POSTs to API endpoints, especially file/upload endpoints
- Newly created PHP files in upload/media directories
- Requests containing serialized blobs, unusual __type fields, or deeply nested JSON
- Evidence of phpinfo() probes, unexpected cron jobs, or new admin users
CVE-2025-54236: Immediate Mitigation Steps for SessionReaper
- Isolate affected node(s) (or throttle via WAF while preserving logs).
- Capture forensics: webroot, php-fpm/webserver logs, DB dumps.
- Remove web shells and restore from known-good deploy artifacts.
- Rotate all secrets and credentials (admin, API, DB).
- Rebuild nodes from trusted images and apply hotfix before reconnecting.
- Monitor closely for 30–90 days.
SessionReaper Defense: What Comes Next
- Centralize session storage and harden deserialization code paths.
- Automate version inventory and emergency patch workflows for platform components.
- Combine WAF + runtime detection + file-integrity monitoring for layered defense.
- Limit public exposure of sensitive API endpoints (IP allow-lists, zero-trust access).
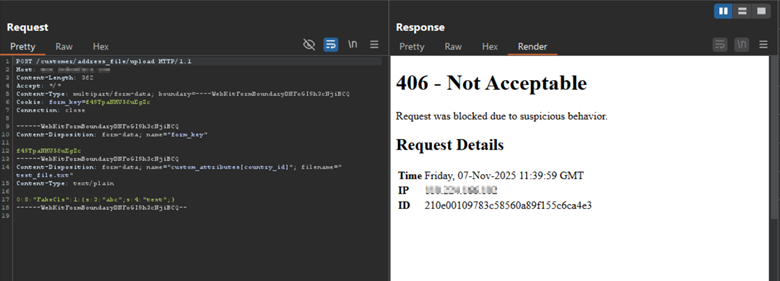
AppTrana WAAP Coverage for CVE-2025-54236 (SessionReaper)
AppTrana WAAP delivers out-of-the-box protection against exploitation attempts targeting CVE-2025-54236. Its AI-powered managed WAF automatically analyzes and blocks malicious attempts abusing improper input validation, session manipulation, and deserialization pathways used to hijack accounts or achieve RCE.
The following example demonstrates how AppTrana WAAP mitigates exploitation attempts tied to CVE-2025-54236 (SessionReaper)
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 November 11, 2025
November 11, 2025






