How to Sell Premium Web Security Retainers
For the last decade, the agency model relied on a simple formula: Build a high-value asset, hand it over, and charge a nominal fee to keep the lights on. That model is breaking and the smartest agencies have already moved on.
- The Market Reality: Comprehensive analysis of over 170 agency service models confirms the aggressive adoption of “Managed Protection”. Agencies across all major technology stacks and regions now actively sell security-as-a-service. This service functions as the primary commercial driver for modern agency growth.
- The Value Shift: While Artificial Intelligence compresses the cost ofbuilding websites, it exponentially increases the threat of breaking them. Clients view security as an intrinsic component of keeping their business online.
- The Old Model: Agencies charged $50–$100/mo for “Maintenance” (updates and backups).
- The New Model: Agencies are charging $500–$2,000/mo for “Security Assurance” (WAF, DDoS protection, and guarantees).
- The Opportunity: The “Build and Transfer” era is ending. The “Secure and Scale” era is here. Agencies that fail to make this switch risk being trapped in a “commoditized maintenance” race to the bottom.Agencies that embrace it are securing 20–30% net margins and deepening client trust.
This guide shows you how to package, price, and sell that assurance without hiring an internal security team.
Sell the Outcome: The Client-Facing Value Proposition
Clients purchase business continuity and compliance confidence. They buy the assurance that their revenue generation continues without interruption and their platforms meet rigorous security standards. Account Executives succeed by mapping the technical features of the retainer directly to these business outcomes.
The Core Proposition: Risk Management as a Service
This retainer functions as an insurance policy for your digital asset. It converts unpredictable security risks and compliance hurdles into a predictable operational strategy.
The Five Pillars of Managed Security
Use these five pillars to define the value of the Premium Security Tier.
1. Revenue Assurance (We Keep You Online)
Uptime equals revenue.This service protects your transaction flow and lead generation forms from disruption. We implement unmetered DDoS protection to absorb traffic spikes and ensure your site remains fast and accessible during peak demand.
2. Perimeter Defense (We Stop Attacks at the Door)
We block malicious threats at the network edge before they reach your infrastructure.The Web Application Firewall (WAF) filters exploit attempts, SQL injection, and malware probes instantly. This proactive stance prevents server overload and protects your database integrity.
3. Traffic Integrity (We Protect the Customer Experience)
Legitimate customers require seamless access. We utilize advanced bot management to filter out scrapers and malicious actors while guaranteeing access for real users. We back this with a “Zero False Positives” commitment, ensuring your security measures support your sales goals.
4. Compliance Confidence (We Pass Your Audits)
Enterprise clients and microsite projects require strict adherence to regulatory standards.We provide the automated Vulnerability Assessment and Penetration Testing (VAPT) reports necessary to satisfy these mandates. Our system maps protection directly to key frameworks like PCI-DSS and ISO 27001. You receive “Audit-Ready” documentation that proves vulnerability remediation is active and effective.
5. Visible Accountability (We Prove the Work)
You receive transparent, monthly reporting on your risk status. These reports document the specific attacks we blocked and the vulnerabilities we patched virtually. This documentation provides the evidence required for internal compliance reviews and stakeholder assurance.
The Closing Analogy
Standard maintenance keeps the house in order. Managed security ensures the doors remain locked. This service provides the lock, the alarm, and the 24/7 guard.
Productize the Retainer: Eliminate Decision Fatigue
The outcomes establish the value. The packaging streamlines the purchase. Sales conversations stall when the scope feels ambiguous or custom. You remove this friction by standardizing the offer into clear, productized tiers. This structure empowers the client to self-select the right level of protection immediately.
Tier 1: Essential Security (The “Peace of Mind” Plan)
The Pitch: This plan serves the “Brochure Site” client. These businesses primarily need brand visibility and basic availability. For them, security is about reputation management.
The Focus: Position this as the baseline requirement for professional hosting. You protect their domain from defacement and automated spam. The monthly report validates that the site remains online, clean, and fast.
Tier 2: Business Assurance (The “Lead Gen” Plan)
The Pitch: This plan targets the “Active Business” client. These organizations rely on their website to generate phone calls, contact forms, or membership sign-ups. For them, a broken form or a slow load time directly impacts their pipeline.
The Focus: Position this as “Lead Integrity.” You ensure that legitimate prospects access the site without friction while the WAF filters out bot traffic that skews their analytics. The monthly report proves that you actively tuned the security rules to keep their lead flow smooth and uninterrupted.
Tier 3: Revenue Guard (The “eCommerce” Plan)
The Pitch: This plan protects the “Transaction Engine.” This is for the , or the high-volume portal where downtime equals immediate financial loss. For these clients, security is an operational necessity, not an optional add-on.
The Focus: Position this as “Revenue Continuity.” You implement aggressive anti-fraud measures to stop carding attacks and inventory hoarding. You provide compliance-grade reports that satisfy their internal audits and payment processor requirements. The monthly report correlates 100% uptime directly to their ability to process sales during peak traffic.
Show Me the Money: The Pricing and Margin Story for Agency Owners
Clear packaging removes the friction from the sales process. The next step aligns these tiers with a pricing model that secures agency profitability. You need a formula that accounts for both the hard costs and the often-overlooked cost of internal labor.
The Simple Unit Economics Model
Profitability hinges on controlling the variables. Use this formula to calculate the true margin of your security retainer:
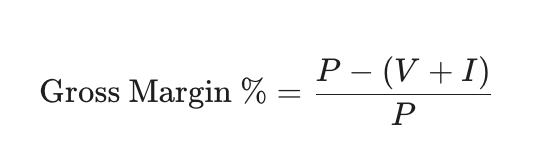
- P (Price): The monthly fee you charge the client.
- V (Vendor Cost): The cost of the Platform + SOC license. This remains a private, fixed expense.
- I (Internal Cost): The cost of your team’s time.
The Internal Cost Factor (I) determines the success of this model. In a typical self-managed setup, internal delivery costs spiral quickly. A single hour spent by a senior developer investigating a false positive erodes the margin for the entire month. The Managed SOC model keeps “I” near zero by offloading the technical labor to the vendor.
The Multiplier Rule: Pricing Made Easy
You simplify pricing decisions by applying a standard multiplier to your cost base (). This approach guarantees a healthy margin floor:
- 2× Cost Base: Yields a 50% Gross Margin.
- 5× Cost Base: Yields a 60% Gross Margin.
- 3× Cost Base: Yields a ~67% Gross Margin.
This framework allows you to price confidently, knowing that every contract contributes significantly to the agency’s bottom line.
Why $500/mo Is Realistic (The Operational Reality)
Agencies often hesitate to charge premium rates for security because they fear the operational workload. This fear stems from the “Do It Yourself” era.
The Scalability Shift: With a Managed SOC partner, the operational heavy lifting moves off your plate. The SOC handles rule tuning, false positive resolution, and 24/7 monitoring. Your internal delivery minutes remain low and predictable, regardless of attack volume. This operational leverage allows you to charge $500/mo based on the value delivered(outcome) rather than the hours worked (effort).
The MRR Ladder: Building Enterprise Value
Upgrading existing clients generates immediate revenue growth.
The Growth Math Moving a client from a standard $200 maintenance plan to a $500 security retainer creates a $300 net increase in Monthly Recurring Revenue (MRR).
- 10 Clients Upgraded:+$36,000/yr
- 25 Clients Upgraded:+$90,000/yr
The Valuation Impact Security retainers create “stickier” revenue than marketing or design services. Clients rarely cancel security protection once it is in place. This high-quality, low-churn recurring revenue directly increases the enterprise valuation of your agency.
Handling the Sticker Shock: The “Category Switch” Strategy
The jump $500 retainer feels steep only when viewed as a price increase. It becomes acceptable when viewed as a category switch. You move the client from purchasing “Admin Tasks” to purchasing “Revenue Insurance.”
1. Change the Comparison, Anchor
Clients view existing retainers as a “Hosting Tax”—a necessary evil like a utility bill. They compare it to the cost of cheap shared hosting. Clients view $500 as “Risk Management”, a strategic investment. You anchor this price against the cost ofdowntime.
- The Math:For a store generating $50,000 a month, a single day of downtime costs $1,600. The $500 retainer prevents this loss. The cost of protection remains a fraction of the cost of the problem.
2. Target the Right Tier
The $500 price point targets your Tier 3 (eCommerce/Revenue) clients. These businesses understand that uptime equals money. For your Tier 1 and Tier 2 clients (Brochure and Lead Gen), the upgrade path leads to the $150–$250 range. This smaller jump aligns with the value of “Business Assurance” without breaking their budget. You segment the upsell based on the client’s risk profile.
3. The Cost of Clean Up
Hack recovery is expensive. A manual malware cleanup often bills at $2,000+ in emergency hourly rates. The retainer spreads this cost into a predictable monthly operating expense. Clients prefer a flat $500 fee over a surprise $5,000 emergency invoice. You sell financial predictability.
The Sales Motion: Turn Risk into Revenue
You close high-value retainers by following a structured, data-driven narrative. This playbook guides Account Executives from identification to the final signature, using data to drive urgency.
Step 1: Identify the Right Accounts (Follow the Money)
Focus your sales efforts on clients where the cost of downtime is calculable and immediate. You target environments where the website functions as a primary revenue engine. The ideal prospect runs a transaction engine like a WooCommerce store, a Magento shop, or a membership portal. These businesses rely on “Money Pages”, login portals, checkout flows, and admin panels, where any interruption impacts the bottom line directly.
Step 2: The “Trojan Horse” Strategy (The DAST Scan)
Data drives the sale. You initiate the conversation by running a Dynamic Application Security Testing (DAST) scan on the target site. This report transforms a theoretical risk into a tangible business problem.
Instead of presenting raw technical data, you present a business story. You explain exactly what is exposed, such as open ports or unpatched plugins. You then map these exposures to specific operational impacts, like data theft or ransomware. Finally, you quantify the financial risk, positioning the managed retainer as the necessary mechanism to control this specific threat profile.
Step 3: The 3-Slide Close
Simplify the proposal into a narrative arc that respects the executive’s time.
- Slide 1: The Risk Snapshot. Start with the reality of their current situation. You display the specific vulnerabilities found in the scan and highlight the “Money Pages” currently exposed to attack. This validates the urgency of the problem.
- Slide 2: The Protection Plan. Pivot immediately to the solution. You detail the “Day 1” countermeasures, specifically the activation of Block Mode and the application of Virtual Patches to neutralize the discovered threats instantly. You emphasize the “Zero False Positives” guarantee to assure them that security will support, rather than hinder, their sales.
- Slide 3: The Proof Loop. Finish with the ongoing value. You show a sample executive report illustrating exactly what they receive every month: a record of blocked attacks, a log of virtual patches, and a summary of rule tuning. This visualizes the “invisible work” you perform to keep them safe.
Step 4: The Outcome-Based Guarantee
Close the deal by defining success through operational metrics. You establish trust by promising measurable outcomes. Commit to specific Service Level Agreements (SLAs) for response times and threat mitigation. Leverage the backing of your vendor partner to offer a 100% application availability SLA. This frames the retainer as a partnership centered on shared success and operational reliability.
Proving Value Every Month: The Reporting System That Makes Renewals Easy
Security is invisible until it fails. To secure the renewal, you must make the invisible work visible. You achieve this by delivering a reporting system that proves the Return on Investment (ROI) every single month.
The Reporting Pyramid: Value First, Proof Second
Your reporting structure dictates how the client perceives the value. The optimal report follows a pyramid format.
- The Executive Summary:This sits at the top. It provides a “Board-Ready” slide that a marketing director or CEO can paste directly into their own internal presentations.
- The Technical Appendix:This follows the summary. It provides the granular logs and evidence required to satisfy a technical stakeholder who wants to verify the work.
The 4 Proof Blocks Every Report Must Include
Standardize your monthly deliverable around these four evidence categories.
1. Protection Volume
Summarize the total volume of attacks blocked.Identify the top attack categories (e.g., SQL Injection, Cross-Site Scripting) and highlight any significant bot activity trends. This metric quantifies the “silent noise” you filter out daily.
2. Vulnerability Remediation
This is your high-value differentiator.List the specific vulnerabilities detected by the scanner and confirm their active mitigation via virtual patching. This proves you manage risk, rather than just software updates.
3. Change Management
Document the work performed. List the key rule tuning adjustments and exceptions added to reduce false positives. This section proves the service is managed and adaptive, rather than static.
4. Response Timelines
Log the response times for support tickets.Show exactly how fast the SOC responded to potential issues or false positive inquiries. This metric validates your Service Level Agreement (SLA) commitment.
Generating these insights requires speed and consistency. You must select a partner platform that consolidates all four proof blocks into a single, centralized view. The ideal dashboard offers customizable templates to align the visual output with your agency brand standards immediately. Automated scheduling options ensure the data arrives ready for distribution. This specific capability reduces the entire monthly reporting cycle to a simple 15-minute task.
The Partner Advantage: Why Agencies Choose AppTrana
You need a technology partner that aligns with your business model. AppTrana functions specifically as an extension of your agency, providing both the operational labor to run the service and the strategic data to sell it.
1. The “You Sell, We Run” Operational Model
AppTrana operates as your backend security division. You own the client contract and the billing relationship. Our Security Operations Center (SOC) manages the technical execution. Our engineers handle rule creation, false positive tuning, and 24/7 monitoring. This division of labor allows you to scale your security practice without hiring additional engineering staff.
2. The Built-In Sales Engine (Integrated DAST)
The platform includes the “Trojan Horse” required to close deals. You utilize the integrated Dynamic Application Security Testing (DAST) scanner to identify the specific vulnerabilities that drive your sales motion. This tool generates the risk data for your initial proposal and the proof data for your monthly retention report. The system links detection directly to mitigation, creating a closed-loop report that validates your work automatically.
3. The Zero False Positive Guarantee
We back our accuracy with a contractual guarantee. The AppTrana SOC manually validates rules to ensure they distinguish between malicious bots and legitimate customers. You receive a “Zero False Positives” commitment, ensuring your clients’ revenue streams remain uninterrupted. This guarantee transforms the WAF from a potential friction point into a reliable business asset.
4. The 24-Hour Virtual Patching SLA
We commit to a 24-hour Service Level Agreement (SLA) for virtual patching of critical vulnerabilities. When a vulnerability is disclosed, our team applies a custom rule at the WAF level to block the specific exploit path immediately. This capability secures the site instantly, granting your development team the time to test and deploy permanent code fixes safely.
5. Unmetered DDoS Protection
We provide unmetered DDoS protection across all plans. You receive a predictable flat rate, regardless of attack volume or duration. This pricing model protects your agency margins from the volatility of “surge pricing” during a cyber-attack.
6. Block Mode Enforcement from Day 1
We onboard applications in “Block Mode” immediately. Our onboarding process validates traffic patterns to ensure safe enforcement from the first minute. You deliver active protection to your client instantly, rather than waiting weeks for a “learning mode” to complete.
Stop leaving revenue on the table. Partner with us today. Request a demo.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.
Frequently Asked Questions (FAQs)
Hosting and maintenance cover uptime basics, updates, and housekeeping. Security assurance covers active risk: stopping attacks, mitigating vulnerabilities fast, protecting checkout and login flows, and producing audit-ready evidence. The value is not “a tool.” It is reduced downtime risk, reduced breach risk, and visible accountability every month.
Start with clients where downtime has a clear cost:
- eCommerce stores (WooCommerce, Magento)
- Membership portals and logged-in experiences
- Lead-gen sites with high paid traffic
- Any business with “money pages” like checkout, login, forms, account dashboards
For brochure sites and low-risk sites, position a lower tier.
Do a category switch, not a price increase:
- Re-anchor the comparison to downtime cost, breach cost, and emergency cleanup cost
- Position it as revenue insurance plus operational proof
- Use a baseline risk scan and show “here is what is exposed today”
- Offer tiers so the client can self-select based on risk, not budget pressure
You are selling Security Assurance, which includes controls (WAF, DDoS, bot mitigation) plus outcomes (availability, reduced risk, compliance confidence) plus proof (monthly reporting). Clients buy continuity and confidence, not acronyms.
Lead with practical business language:
- “We want your checkout, login, and forms to stay online and clean.”
- “We will show you a risk snapshot and a monthly proof report.”
Use risk evidence to create clarity, not panic. One scan + one short story beats doom messaging.
Run a DAST scan and translate it into a business narrative:
- What’s exposed (in plain language)
- What can happen (downtime, fraud, data exposure)
- What parts of the site are impacted (money pages)
- What you will do to reduce risk immediately and continuously
Avoid dumping raw findings without context.
Plugins help, but they do not replace active security operations:
- Attacks evolve and require ongoing tuning
- False positives require human validation
- DDoS and abuse patterns require monitoring and response
- Clients need proof and reporting, not just a tool installed
Position plugins as a component, not the assurance program.
This is the key reason premium pricing becomes realistic. In a managed model:
- Your agency owns the relationship and the retainer
- The security partner’s SOC handles tuning, monitoring, false positives, and response
This keeps your internal cost predictable so margins hold as you scale.

 January 23, 2026
January 23, 2026






