SAP Zero-Day CVE-2025-31324: Unauthenticated RCE in NetWeaver VCFRAMEWORK
SAP disclosed a critical RCE vulnerability(CVE-2025-31324) on April 24, 2025, impacting the Visual Composer Framework in NetWeaver Application Server Java, version 7.50. This flaw poses a serious risk to enterprises relying on SAP NetWeaver for their mission-critical operations.
Unauthenticated attackers can exploit this vulnerability to upload and run arbitrary files on SAP servers, potentially resulting in complete system compromise.
CVE-2025-31324 – Risk Analysis
Severity: CRITICAL
CVSSv3.1: Base Score: 9.8 CRITICAL
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Exploit available in public: Yes
Exploit complexity: Low
CVE-2025-31324 is rooted in the Visual Composer Framework (VCFRAMEWORK), a component used to build business applications without code. Although not installed by default, it is often enabled in SAP NetWeaver environments to assist analysts and developers in rapid app development.
Here’s the problem:
One of the endpoints in this framework, located at
/developmentserver/metadatauploader,
does not require authentication. That means attackers can access it without any credentials. Once inside, they can upload any file they want—including malicious scripts that allow them to take control of the system.
In simpler terms, this bug lets hackers break into SAP servers from the internet and run commands as if they were administrators.
How the Exploitation Works
Since April 29, 2025, a China-linked threat actor, has been using this vulnerability to compromise SAP NetWeaver servers. According to a recent report by Forescout Vedere Labs, the group has been deploying web shells and the Brute Ratel C4 post-exploitation framework to maintain access to the compromised systems.
Here’s a step-by-step look at how attackers exploit this vulnerability:
1. Accessing the Vulnerable Endpoint:
The endpoint /developmentserver/metadatauploader is publicly accessible, and it does not enforce authentication or authorization.
2. Uploading Malicious Files:
Attackers target the endpoint with specially crafted HTTP POST requests carrying malicious payloads, often JSP files such as helper.jsp or cache.jsp.
3. File Written to Web-Accessible Location:
Due to the lack of validation, the server writes the file into directories such as:
…/irj/servlet_jsp/irj/root/, allowing browser-based access.
4. Remote Command Execution:
Once uploaded, the attacker can trigger the web shell via a browser, granting command execution as the sidadm user—the SAP system administrator.
5. System Takeover:
With privileged access, attackers can move laterally, exfiltrate data, create reverse shells, or establish persistent access.
Why This Vulnerability is So Dangerous
- No Authentication Required: Anyone on the internet can exploit it if the endpoint is exposed.
- High Privileges: The code runs with SAP system-level permissions, making it easy for attackers to take over completely.
- Actively Exploited: Security agencies like CISA have flagged this vulnerability as actively being used in attacks.
- Common Component: While the Visual Composer isn’t always installed by default, it’s widely used in enterprises for internal app development—making this vulnerability more common than you might think.
Are You Affected?
If your organization uses SAP NetWeaver AS Java 7.50, there’s a strong chance the affected component might be present—especially if developers use Visual Composer tools.
To check if you’ve been compromised, look for suspicious .jsp, .class, or .java files in folders like:
C:\usr\sap\<SID>\<InstanceID>\j2ee\cluster\apps\sap.com\irj\servlet_jsp\irj\root
SAP also advises monitoring your logs for access to this URL:
/developmentserver/metadatauploader
Recommended Actions and Patch Guidance
1. Apply the Patch
SAP has released a patch under Security Note 3594142. Make sure you’re using version 18 or higher of this note.
2. Remove the Component (if not needed)
If you don’t use Visual Composer, consider removing the vulnerable component:
sap.com/devserver_metadataupload_ear
3. Check for Signs of Exploitation
Scan for webshells or unknown files in your SAP directories. If found, treat it as an incident and begin a full investigation.
4. Harden Your Perimeter
Ensure the vulnerable endpoint is inaccessible from the public internet. Use firewalls and WAFs to block access.
5. Monitor for Unusual Activity
Attackers may return even after initial exploitation. Watch for outbound connections, unknown users, or changes to critical system files.
AppTrana WAAP Coverage for SAP Zero-Day CVE-2025-31324
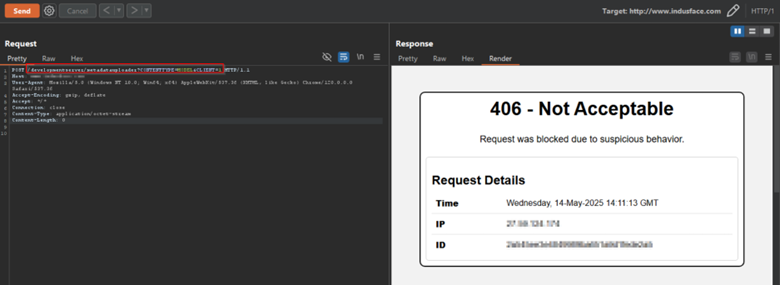
Customers leveraging AppTrana WAAP are protected from CVE-2025-31324 exploitation attempts from Day 0. The platform’s real-time monitoring and mitigation features enable early detection and automatic blocking of threats.
During proof-of-concept (PoC) testing, AppTrana’s custom security rules successfully blocked exploitation attempts related to CVE-2025-31324, as illustrated in the screenshot.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 May 15, 2025
May 15, 2025



