If you operate insecure infrastructure – Microsoft may seize it for “greater-good”
According to the recent actions of technology heavy weight Microsoft, if a company operates insecure infrastructure, that is repeatedly used to spread malicious software, they could seize the underlying assets.
Internet is a critical part of our lives, from e-commerce, entertainment, and social media to research while these activities are well-known examples of how internet enhances our lives. Average customers don’t realize that internet is instrumental in powering their houses for ensuring that the trains run on time. Actions that put the security of the internet at risk, need to be prevented. One of the most dangerous cybercrime is to spread malware. Parties that enable these actions – either knowingly or inadvertently – should be subjected to corrective actions…and that is exactly what Microsoft seems to be doing.
What did Microsoft do?
According to an official Microsoft company blog. they have seized control of 23 domain names of NoIP (NoIP is owned by Vitalwerks Internet Solutions, LLC based in Reno, Nevada). NoIP is an operator of a high-availability anycast network to provide end users, SMBs and enterprises managed DNS service.
As per Microsoft court filings, No-IP:
- Infrastructure was involved in 93% of all Bladabindi-Jenxcus infections
- Infrastructure is infected by 245 different types of malware currently
- Infrastructure can be connected to about 6.9M Bladabindi-Jenxcus infections in the last 12 months
- Has not heeded to numerous request for increased security measures from the security community
- Seized domains know that bad traffic will now be allowed to be directed to Microsoft’s sinkhole to classify and identify threats.
Domain owners must act responsibly by monitoring for and defending against cybercrime on their infrastructure.
– Microsoft
What are Jenxcus & Bladabindi?
Jenxcus family of worms can collect your personal information and send it to a malicious hacker, along with potential access and control of your PC. Your computer can get infected with Jenxcus worms from a drive-by download attack or can be installed when you visit a compromised webpage or use an infected removable drive.
Bladabindi is malicious worms that can use your PC camera or record your keystrokes and send your sensitive details to a hacker, along with potentially giving him/her control over your PC. Bladabindi can get installed on your machine via infected USB drives or Trojans.
Microsoft is in good company – When complaining about No-IP
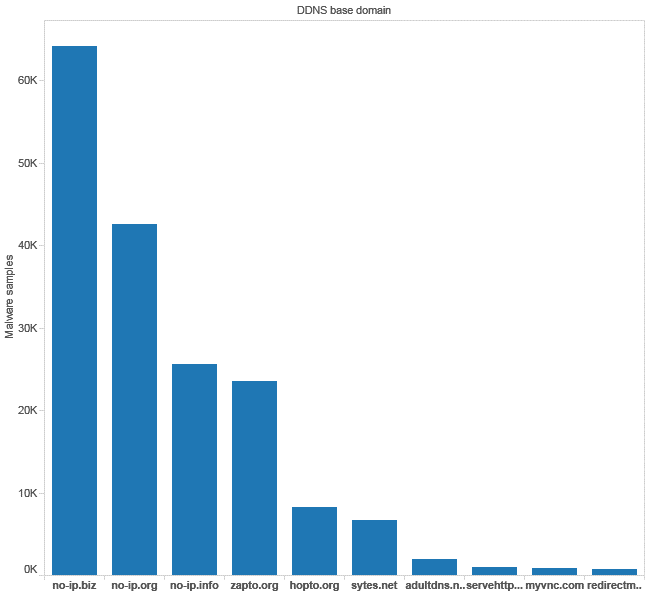
According to a recent Cisco Systems blog on Dynamic DNS, no-IP assets were ranked as top 3 for number of malware samples per domain names starting from ~25K/DN for no-ip.info to as high as 60K/DN for no-ip.biz http://blogs.cisco.com/security/dynamic-detection-of-malicious-ddns/
No-IP – Cleaning up the act?
A comment on the official blog of No-IP suggests that all the domains are now back in their control and that they are in the process of restoring service for millions of their users. The company has given details on how they have pro-actively cleaned up the quality of their traffic in the past. They claim that in spite of all reasonable actions “our free dynamic DNS service does occasionally fall prey to cyber scammers, spammers, and malware distributors”.
Some may deem Microsoft’s actions to be heavy-handed, but we beg to differ here. We think these actions are justifiable and set precedence to put the onus on infrastructure operators to renew focus on security. If your infrastructure is involved in millions of instances of malware distribution, you need to do the needful. If the infrastructure operator is not capable of addressing the problem, maybe they should ask for help from others who can. After a certain point, some action needs to be taken. Fundamentally, we agree with the actions… maybe there could have been a less intrusive way to handle it.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 July 7, 2014
July 7, 2014



