CVE-2026-21858 (Ni8mare): Unauthenticated Remote Code Execution in Self-Hosted n8n
A critical unauthenticated remote code execution (RCE) vulnerability has been disclosed in n8n, a widely used open-source workflow automation platform that orchestrates business processes, SaaS integrations, and event-driven automation pipelines.
Tracked as CVE-2026-21858 and referred to as Ni8mare, the vulnerability carries a CVSS v3.1 score of 10.0 (Critical) and allows unauthenticated attackers to execute arbitrary system-level code on vulnerable self-hosted n8n instances. Successful exploitation can lead to complete server compromise, unauthorized access to sensitive data, manipulation of automation workflows, and abuse of connected downstream systems.
With nearly 60,000 internet-facing n8n instances identified as vulnerable as of January 2026, exposure remains widespread. Many of these deployments expose public webhook or form-based workflows, making this flaw a priority-zero risk for organizations running self-hosted n8n as part of their core automation infrastructure.
What Is CVE-2026-21858?
Risk Analysis
Severity: CRITICAL
CVSS v3.x Base Score: 10.0
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:N
Exploit available in public: No
Exploit complexity: Low (conditional)
Affected Product: n8n (self-hosted deployments)
Affected Versions: Versions from 1.65.0 up to, but not including, 1.121.0
CVE-2026-21858 is an unauthenticated remote code execution vulnerability stemming from vulnerabilities in how n8n processes HTTP requests to Form and Webhook workflows. The vulnerability can be exploited remotely without prior authentication.
The vulnerability allows attackers to manipulate request data to trigger internal file-handling logic, enabling arbitrary file reads from the host system, including configuration files and authentication secrets. Using this information, attackers can forge valid administrative sessions and bypass authentication controls.
With administrative access, attackers can abuse built-in workflow capabilities to execute arbitrary operating system commands, resulting in full compromise of the n8n instance. While availability impact is not intrinsic to the vulnerability itself, the level of access obtained enables data exfiltration, credential abuse, and lateral movement into connected systems.
Root Cause Behind CVE-2026-21858
The root cause of CVE-2026-21858 lies in a Content-Type confusion vulnerability within n8n’s Form Webhook request processing logic.
n8n applies different request parsers based on the Content-Type header. Requests marked as multipart/form-data are processed by a file upload parser that safely constructs file objects. Other content types, such as application/json, are handled by a generic body parser that trusts user-supplied data.
The vulnerability arises because the Form Webhook logic later assumes that any files object present in the request was created by the multipart parser. No validation is performed to confirm that assumption. As a result, attackers can submit a JSON request containing a fully attacker-controlled files object that is treated as legitimate by downstream logic.
CVE-2026-21858 -Exploitation Flow
Exploitation of CVE-2026-21858 occurs in multiple stages and builds progressively toward full system compromise.
Stage 1: Arbitrary File Read
By injecting a forged req.body.files object, an attacker can specify arbitrary file paths and trigger internal file-handling routines. This allows reading sensitive files from the host system, including configuration files, databases, and system files such as /etc/passwd.
Stage 2: Authentication Bypass
n8n uses a signed JWT cookie (n8n-auth) for session management. The information required to forge a valid admin session, user details and the instance-specific signing secret, can be retrieved through the file read capability. With these values, attackers can generate a valid administrator session and bypass authentication entirely.
Stage 3: Remote Code Execution
Once authenticated as an administrator, attackers can create or modify workflows and leverage built-in nodes such as Execute Command to run arbitrary operating system commands. This results in full remote code execution with the privileges of the n8n process.
Preconditions That Influence Real-World Exploitability
CVE-2026-21858 is not automatically exploitable in every deployment. Successful exploitation typically requires:
- A publicly accessible Form or Webhook workflow
- The workflow allowing unauthenticated submissions
- A method to retrieve or act on read file contents (such as logs, workflow execution output, or administrative access)
CVE-2026-21858: From Workflow Compromise to Full Environment Access
The real danger of CVE-2026-21858 lies in what n8n sits at the center of. n8n is rarely a standalone tool; it often acts as an automation hub that connects cloud platforms, CI/CD pipelines, databases, SaaS applications, and increasingly, AI systems. A single compromised instance can expose OAuth tokens, API keys, cloud credentials, and internal services, turning one vulnerability into a gateway for wider infrastructure compromise.
Because these workflows frequently bridge systems that are otherwise segmented, successful exploitation can trigger cascading access across an organization’s environment rather than a contained breach.
From an exposure perspective, researchers have identified multiple ways to locate publicly accessible n8n instances. Common indicators include static assets such as @n8n/chat/dist/chat.bundle.es.js, HTML elements tied to n8n Forms, and distinct favicon hashes visible through internet-wide scanning tools. While many instances are discoverable, only a subset exposes the specific unauthenticated Form or Webhook configurations required for exploitation, making misconfiguration, rather than mere exposure, the decisive risk factor.
CVE-2026-21858 – Mitigation and Remediation Guidance
The primary remediation for CVE-2026-21858 is to upgrade self-hosted n8n deployments to version 1.121.0 or later, which fully addresses the vulnerability. Given the severity, delaying this update materially increases risk.
In addition to patching, organizations should reassess how n8n is exposed. Publicly accessible Forms or Webhooks should be limited to essential use cases, with authentication enforced on all Form submissions. High-risk workflow nodes, especially those capable of executing system-level commands such as Execute Command, should be restricted or disabled where possible.
Finally, rotate all credentials stored within workflows and review execution logs for signs of unauthorized or suspicious activity that may indicate prior compromise.
How AppTrana WAAP Helps Mitigate CVE-2026-21858
AppTrana WAAP has provided protection against exploitation attempts targeting CVE-2026-21858 from day zero by detecting and blocking malicious HTTP requests aimed at exposed n8n Form and Webhook workflows. By inspecting request structure, headers, and abnormal payload patterns at the application layer, AppTrana helps prevent unauthorized access paths used to initiate exploitation.
Screenshot showing malicious request payloads associated with CVE-2026-21858, detected and blocked by AppTrana WAAP.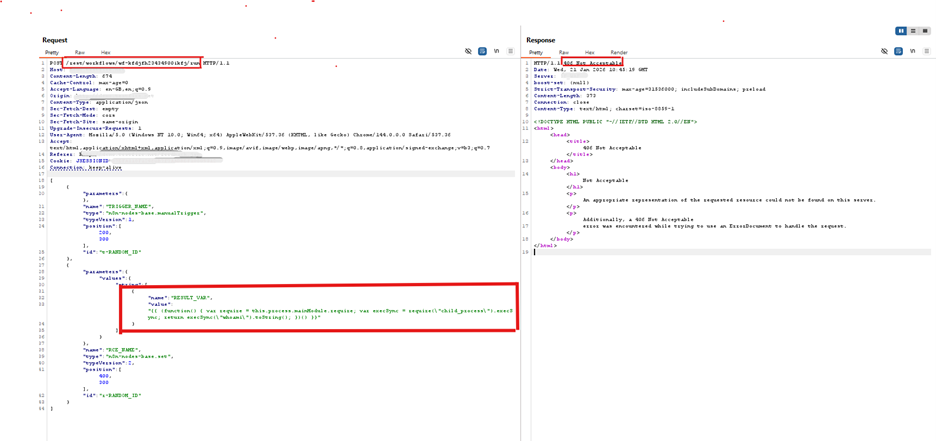
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 January 27, 2026
January 27, 2026



