CVE-2026-1357: WordPress Plugin RCE Exposes Sites to Full Takeover
A critical vulnerability in the WPvivid Backup & Migration WordPress plugin allows unauthenticated attackers to upload and execute arbitrary PHP files on exposed websites. Tracked as CVE-2026-1357, the vulnerability affects vulnerable versions of the plugin and enables remote code execution through network-accessible functionality intended for backup and migration workflows.
With over 900,000 active installations, WPvivid is widely deployed across production WordPress environments. Because exploitation requires no authentication and enables direct server-side code execution, internet-facing sites running affected versions face immediate risk of full compromise.
What is CVE-2026-1357?
Risk Analysis
Severity: CRITICAL
CVSS v3.x Base Score: 9.8
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Exploit available in public: Yes
Exploit complexity: Low
Affected Product: WPvivid Backup & Migration WordPress Plugin
Affected Installations: 900,000+ active sites
CVE-2026-1357 is a remote code execution vulnerability in the WPvivid Backup & Migration plugin caused by vulnerabilities in its backup receiving mechanism. The vulnerability allows attackers to send crafted HTTP requests that result in arbitrary PHP file upload and execution on the server.
Because the affected functionality is remotely accessible and does not enforce authentication, exploitation requires minimal effort. The availability of public exploit code further increases the risk of automated scanning and large-scale targeting of unpatched WordPress deployments.
Successful exploitation enables arbitrary PHP execution within the WordPress environment, resulting in:
- Confidentiality Impact: Access to database contents, configuration files, and stored secrets
- Integrity Impact: Ability to upload and execute malicious code
- Availability Impact: Site defacement, disruption, or complete service loss
If left unpatched, the vulnerability can lead to full site compromise.
Root Cause Behind CVE-2026-1357 in WordPress
CVE-2026-1357 is the result of two combined weaknesses in the plugin’s backup handling logic.
1. Failure to Halt on Decryption Errors
The plugin uses openssl_private_decrypt() to process encrypted session keys for incoming backup data. If decryption fails, execution should terminate. Instead, the function returns false, and this value is passed forward into phpseclib’s AES implementation.
phpseclib interprets the Boolean false as a null-byte string, producing a predictable encryption key. This behavior undermines the intended cryptographic protection and allows attackers to reliably construct payloads that bypass encryption safeguards.
2. Inadequate File Name Sanitization
After decryption, the plugin processes file names derived from attacker-controlled input. These file names are not properly sanitized to prevent directory traversal sequences such as ../.
This allows attackers to:
- Escape the intended backup directory
- Write files into arbitrary locations within the WordPress installation
- Place executable PHP files in web-accessible paths
The combined effect of predictable decryption behavior and insufficient path validation enables unauthenticated file upload followed by direct execution.
Exploitation Flow of CVE-2026-1357
CVE-2026-1357 is exploitable remotely without authentication and follows a structured execution path. Because the vulnerable functionality is exposed over HTTP, no WordPress credentials are required.
The attack typically proceeds as follows:
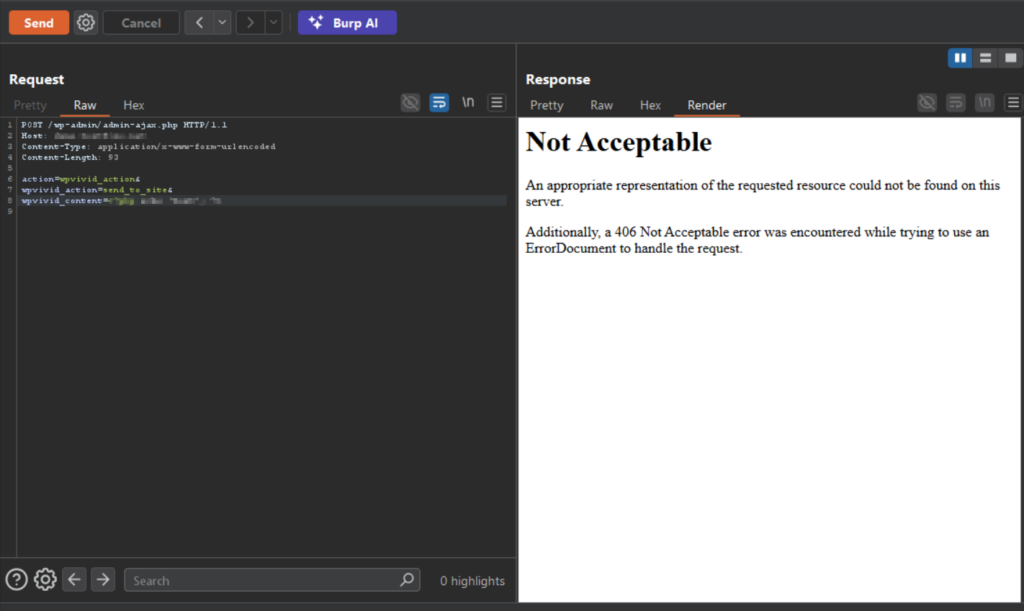
- Targeting the endpoint
A crafted HTTP request is sent to thewpvivid_action=send_to_site endpoint, used for backup transfer operations. - Forcing RSA decryption failure
The request is designed to break the plugin’s RSA decryption logic. Instead of rejecting the input, the plugin mishandles the failure condition. - Abusing a predictable null-byte key
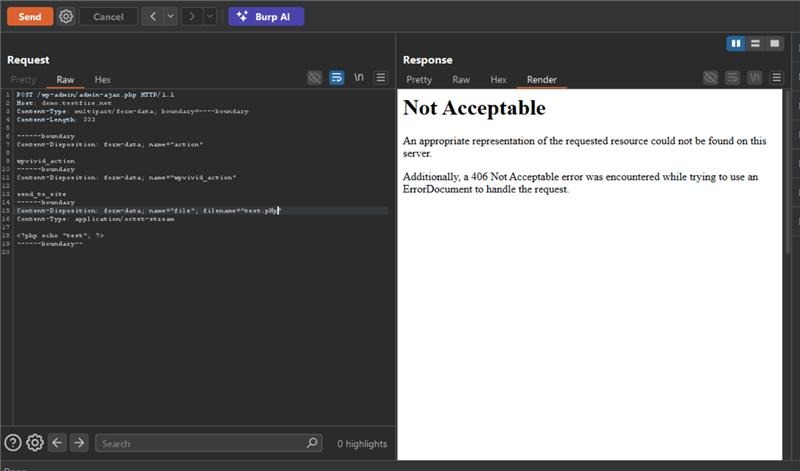
Due to improper error handling, a null-byte key is used to process attacker-controlled data bypassing intended cryptographic checks. - Injecting directory traversal in filename
The attacker supplies a file name containing traversal sequences to escape the designated backup directory. - Writing a malicious PHP file
The payload is written to a web-accessible location outside the intended path. - Executing the payload
The attacker directly accesses the uploaded file, triggering arbitrary PHP execution on the server.
Since the endpoint is remotely accessible and unauthenticated, automated scanning and mass exploitation against exposed WordPress sites is feasible.
Affected Versions
CVE-2026-1357 affects WPvivid Backup & Migration plugin versions prior to 0.9.124.
Sites running earlier versions remain vulnerable, particularly where the “receive backup from another site” feature is enabled and accessible over the network.
Version 0.9.124 includes:
- Proper handling of RSA decryption failures
- Strict validation of file paths
- Enforcement of allowed file types for upload operations
Administrators should promptly verify the installed WPvivid version across all environments and upgrade affected instances without delay.
CVE-2026-1357 – Mitigation and Remediation Guidance
The most effective remediation for CVE-2026-1357 is toupgrade WPvivid Backup & Migration to version 0.9.124 or later, where the unauthenticated file upload and execution vulnerability has been addressed. Because the vulnerability enables direct PHP execution without authentication, patching should be treated as an urgent priority.
In addition to upgrading, organizations should take the following hardening measures:
- Disable backup-receive functionality if not actively required. Any feature that accepts inbound backup files increases exposure and should not remain enabled unless operationally necessary.
- Restrict access to backup and administrative endpoints. Where possible, limit access to trusted IP ranges, enforce authentication controls, and ensure these endpoints are not publicly accessible.
- Conduct file integrity reviews. Inspect the WordPress installation directory, especially upload and plugin paths, for unexpected or recently modified PHP files that may indicate exploitation.
- Audit web server and application logs. Look for suspicious POST requests targeting WPvivid-related endpoints, particularly requests involving file upload parameters or anomalous payload sizes.
- Implement WAF protections. WAF rules can help detect and block malicious file upload attempts or abnormal request patterns associated with exploitation.
Given that this vulnerability enables unauthenticated server-side code execution, remediation should focus first on patch deployment, followed by validation checks to confirm that no malicious artifacts remain on the system.
AppTrana WAAP Coverage for CVE-2026-1357
AppTrana WAAP has provided protection against exploitation attempts related to CVE-2026-1357 from day zero by identifying and blocking malicious requests targeting WPvivid’s vulnerable backup functionality. Through application-layer inspection, AppTrana helps prevent unauthorized file upload and execution attempts during active exploitation and patching windows.
Screenshot showing suspicious upload activity linked to CVE-2026-1357 detected and blocked by AppTrana WAAP.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 February 17, 2026
February 17, 2026



