CVE-2026-1281 & CVE-2026-1340: Actively Exploited Pre-Authentication RCE in Ivanti EPMM
Approximately 1,600 Ivanti Endpoint Manager Mobile (EPMM) instances are currently exposed globally, creating a significant attack surface for enterprise mobile infrastructure. Ivanti has disclosed two critical vulnerabilities, CVE-2026-1281 and CVE-2026-1340, that allow unauthenticated remote code execution on affected on-premises deployments.
CVE-2026-1281 has been confirmed exploited prior to disclosure and is now listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog. Ivanti has acknowledged that a limited number of customers were compromised before patches were released, underscoring the operational risk for organizations running exposed EPMM systems.
CVE-2026-1281 & CVE-2026-1340 – What are they?
Risk Analysis
| CVE Number | CVSS Score (Severity) | CVSS Vector | CWE | Exploit Available in Public | Exploit Complexity |
|---|---|---|---|---|---|
| CVE-2026-1281 | 9.8 (Critical) | AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H | CWE-94 | Yes (Public PoC available) | Low |
| CVE-2026-1340 | 9.8 (Critical) | AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H | CWE-94 | Yes (Public PoC available) | Low |
CVE-2026-1281 and CVE-2026-1340 are critical vulnerabilities that enable unauthenticated remote code execution over the network. Any exposed EPMM instance reachable by an attacker is therefore a viable target.
No credentials or user interaction are required, significantly lowering the barrier to exploitation and increasing the likelihood of automated scanning and mass targeting of internet-facing systems.
Successful exploitation allows attackers to execute arbitrary operating system commands with appliance-level privileges, leading to full system compromise, data exposure, configuration manipulation, and possible lateral movement.
Technical Root Cause: Bash Arithmetic Expansion Abuse
The vulnerabilities stem from improper handling of user-supplied input in backend Bash scripts invoked by specific EPMM endpoints. These are not simple command injection vulnerability. Instead, exploitation abuses Bash arithmetic expansion behavior during timestamp comparison logic.
The affected backend scripts include:
- /mi/bin/map-appstore-url
- /mi/bin/map-aft-store-url
These scripts process attacker-controlled input passed through vulnerable endpoints:
- /mifs/c/appstore/fob/
- /mifs/c/aftstore/fob/
During execution, user-supplied parameters are inserted into variables evaluated inside conditional arithmetic comparisons. By carefully crafting parameters, attackers can force Bash to perform unintended command substitution during arithmetic evaluation. This results in arbitrary command execution at the operating system level.
Because the exploit leverages subtle shell behavior rather than obvious injection patterns, naive filtering and signature-based detection may fail to identify malicious input.
CVE-2026-1281 & CVE-2026-1340 – Exploitation Behavior and Public PoC Activity
Public proof-of-concept (PoC) code was released shortly after disclosure, accelerating exploitation attempts against exposed EPMM systems. The PoC demonstrates how crafted HTTP requests can manipulate vulnerable endpoints to trigger command execution within backend Bash scripts.
Observed payload behavior includes:
- Timing-based validation usingsleep 5 to confirm command execution
- Writing command output to disk, such asid > /mi/poc, to verify system-level access
- Manipulation of parameters likest and h to influence script evaluation
- Abuse of the HTTP Host header to control input processing
- Execution of arbitrary commands through specially crafted HTTP GET requests
While exposure alone does not confirm compromise, the availability of public PoC code substantially lowers the barrier for automated exploitation.
CISA’s decision to include CVE-2026-1281 in the KEV catalog and assign a three-day remediation window for federal agencies highlights the operational urgency associated with this vulnerability.
CVE-2026-1281 & CVE-2026-1340 – Impact of Successful Compromise
Ivanti EPMM operates at a central control layer within enterprise environments. It enforces mobile device policies, manages authentication integrations, and governs application distribution across managed devices. As a result, exploitation does not simply affect a single appliance; it compromises a high-trust management platform.
If attackers achieve remote code execution on EPMM, the potential impact includes:
- Access to personally identifiable information (PII) stored within the management system
- Extraction of device metadata, including phone numbers, GPS information, and configuration details
- Unauthorized modification of mobile security policies
- Manipulation of LDAP, SSO, or directory-based authentication settings
- Deployment of malicious or unauthorized applications to managed devices
- Alteration of network and connectivity configurations
- Pivoting into adjacent enterprise systems for lateral movement
Because EPMM manages enterprise mobile devices and policies, a compromise can disrupt device trust, authentication settings, and security controls across the organization. The impact goes beyond the appliance itself, affecting the wider mobile management and identity environment.
Affected Versions
CVE-2026-1281 and CVE-2026-1340 impact on-premises Ivanti EPMM deployments across multiple 12.x release branches. Organizations running the following versions should assess exposure and apply the appropriate remediation package.
RPM 12.x.0.x Patch Applies To:
- 12.7.0.0 and prior
- 12.6.0.0 and prior
- 12.5.0.0 and prior
- Also compatible with 12.3.0.x and 12.4.0.x
RPM 12.x.1.x Patch Applies To:
- 12.6.1.0 and prior
- 12.5.1.0 and prior
Ivanti has clarified several important considerations regarding remediation:
- Patches are version-specific and must align with the installed release branch.
- RPM installation does not require appliance downtime.
- The RPM-based mitigation does not persist through version upgrades.
- A permanent code-level fix is scheduled for inclusion in version 12.8.0.0.
Organizations should verify their exact EPMM version before applying remediation to ensure proper patch alignment and long-term stability.
CVE-2026-1281 & CVE-2026-1340 – Threat Hunting and Detection Guidance
Organizations operating affected EPMM versions should proactively review logs for indicators of suspicious activity targeting vulnerable endpoints.
Ivanti has provided the following regular expression for Apache log analysis:
^(?!127\.0\.0\.1:\d+ .*$).*?\/mifs\/c\/(aft|app)store\/fob\/.*?404
Security teams should specifically investigate:
- Requests to /mifs/c/appstore/fob/
- Requests to /mifs/c/aftstore/fob/
- POST requests directed at HTTP error pages such as 401.jsp
- Unexpected WAR or JAR file artifacts
- Indicators of web shells or reverse shell activity
- Long-running outbound connections originating from the EPMM appliance
It is important to note that the absence of obvious indicators does not confirm system integrity. Sophisticated exploitation may not leave easily identifiable artifacts.
Ivanti has also released a separate detection RPM that generates an ivanti_checks log file within the /log directory. Findings from this tool should be reviewed in conjunction with full forensic analysis. Suspicious activity observed prior to patching may indicate compromise, while activity after patching may reflect scanning or probing attempts.
CVE-2026-1281 & CVE-2026-1340 – Incident Response Recommendations
If compromise is suspected, organizations should initiate a structured response process immediately.
Recommended actions include:
- Review EPMM administrator accounts and authentication configurations.
- Audit recently created or modified device policies.
- Inspect application push history for unauthorized deployments.
- Examine changes to network or security configurations.
- Assess systems reachable through Ivanti Sentry for lateral movement indicators.
- Restore from a known-good backup or perform a full rebuild and controlled data migration.
Where integrity cannot be confidently verified, a full rebuild and migration is the most conservative and defensible remediation approach.
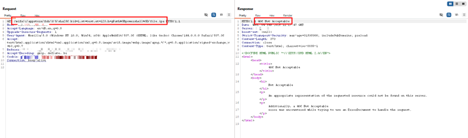
AppTrana WAAP Coverage for CVE-2026-1281 & CVE-2026-1340
AppTrana WAAP has provided protection against exploitation attempts related to CVE-2026-1281 and CVE-2026-1340 and blocking malicious HTTP requests targeting vulnerable EPMM endpoints. By enforcing application-layer inspection, AppTrana helps prevent unauthorized command execution attempts during active exploitation and patching cycles.
Screenshot showing malicious request patterns associated with CVE-2026-1281 and CVE-2026-1340 detected and blocked by AppTrana WAAP.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 February 13, 2026
February 13, 2026



