CVE-2025-55752: Apache Tomcat Path Traversal Vulnerability
Apache Tomcat continues to play a central role in hosting Java-based web applications across enterprises, cloud services, and government systems. Its reliability and lightweight architecture make it a go-to choice for developers, but its ubiquity also means that a single vulnerability can have widespread security implications. CVE-2025-55752, disclosed in late 2025, highlights how a subtle processing regression can evolve into a high-impact vulnerability under the right conditions.
What Caused CVE-2025-55752?
Risk Analysis
Severity: CRITICAL
CVSSv3.1: Base Score: 7.5 HIGH
Vector: CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H
Exploit available in public: No
Exploit complexity: High
At the core of this vulnerability is a vulnerability in Tomcat’s URL rewriting process. When rewrite rules are enabled, Tomcat mistakenly normalizes the rewritten URL before decoding it. This order-of-operations issue allows attackers to embed traversal sequences in encoded form. These sequences evade normalization but resurface after decoding, allowing them to slip past Tomcat’s intended protections.
Sensitive directories such as /WEB-INF/ and /META-INF/ are normally shielded from users. With CVE-2025-55752, a crafted URL can bypass these guardrails when certain rewrite configurations are in use. This behavior stems from a regression introduced during an earlier bug fix, demonstrating how well-intentioned patches can inadvertently introduce new vulnerabilities.
Why CVE-2025-55752 is a Serious Concern for Tomcat Users?
Individually, the traversal vulnerability is dangerous, but the severity increases significantly when paired with HTTP PUT. PUT is usually disabled by default, but in environments where it is active such as systems supporting WebDAV, custom upload interfaces, or administrative tooling, an attacker could upload files directly into protected directories.
This scenario transforms a traversal weakness into a potential remote code execution (RCE) pathway. A malicious JSP file placed inside /WEB-INF/ is enough to give attackers near-complete control over the affected server.
However, this chain requires a very specific set of conditions, which is why the vulnerability is rated Important, not Critical. Rewriting must modify the request path in a particular manner, and PUT must be available to untrusted users, conditions not typical of most hardened production deployments. Still, real-world environments are often messy, and exceptions in configuration create opportunities attackers readily exploit.
Systems Affected by CVE-2025-55752
CVE-2025-55752 impacts a wide set of Tomcat versions:
- Tomcat 11: 11.0.0-M1 to 11.0.10
- Tomcat 10.1: 10.1.0-M1 to 10.1.44
- Tomcat 9.0: 9.0.0-M11 to 9.0.108
- Certain EOL Tomcat 8.5 builds
Many organizations still rely on older Tomcat installations tucked away in legacy apps or shadow IT systems. These deployments often remain unpatched longer, increasing the risk of exposure, especially when tied to public-facing services.
Apache has released patches addressing the faulty normalization step. The corrected versions include:
- Tomcat 11.0.11
- Tomcat 10.1.45
- Tomcat 9.0.109
These updates realign the decoding and normalization processes so that traversal sequences cannot bypass directory access controls.
For older, end-of-life builds, patches will not be provided. Organizations relying on outdated versions must either upgrade or engage commercial extended-support vendors.
How Attackers Exploit CVE-2025-55752
Exploitation hinges on the interaction between URL rewriting and encoded traversal sequences. An attacker would craft a request in which:
- Suspicious path elements are encoded to avoid detection.
- The rewrite engine modifies the request.
- Tomcat normalizes the rewritten path too early.
- The subsequent decoding exposes the traversal pattern.
If PUT is enabled, the attacker’s next step is to upload a malicious payload. Without PUT, the attacker may still access internal resources or application files that were never meant to be public.
Current Exploitation Status of CVE-2025-55752
While widespread exploitation has not yet been observed, several developments increase the likelihood:
- Proof-of-concept (PoC) code is publicly available.
- Security researchers have verified traversal bypass scenarios.
- Tomcat-focused scanning activity historically ramps up quickly after disclosures.
Given how quickly attackers weaponized CVE-2025-24813 earlier in the year, less than 30 hours after disclosure, organizations should assume that exploitation of CVE-2025-55752 may follow a similar trajectory.
Mitigating CVE-2025-55752: What Organizations Should Do
1. Upgrade Tomcat (Highest Priority)
The most effective mitigation is to upgrade to a patched Tomcat version as soon as possible. This should be treated as the top action item.
2. Temporary Risk-Reduction Steps (If Patching Is Delayed)
If an immediate upgrade is not possible, apply the following controls to reduce exposure:
- Disable HTTP PUT, or allow it only for trusted, authenticated users.
- Review and harden URL rewrite rules so user-controlled input cannot influence file paths.
- Restrict upload endpoints by placing them behind strong authentication and authorization checks.
- Increase monitoring for suspicious encoded paths, unexpected file uploads, or abnormal request patterns.
3. Pay Special Attention to Legacy and Unmaintained Systems
Old Tomcat servers, internal lab setups, and forgotten development environments often have the perfect conditions for exploitation. Ensure these systems are audited, upgraded, or isolated immediately.
CVE-2025-55752: AppTrana WAAP Coverage
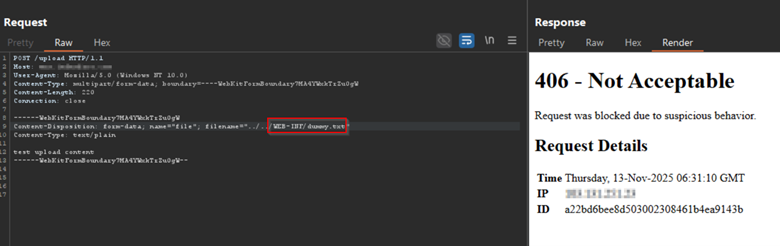
AppTrana WAAP delivers proactive, zero-day defense against CVE-2025-55752 by blocking malicious request patterns that attempt to exploit this Tomcat vulnerability. Even before official patches are applied, AppTrana’s adaptive security engine analyzes request paths, encoded payloads, and abnormal HTTP methods to prevent unauthorized file manipulation or remote code execution attempts.
The following example demonstrates how AppTrana WAAP mitigates exploitation attempts tied to CVE-2025-55752:
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 November 18, 2025
November 18, 2025



