CVE-2025-54253: Critical Zero-Day Vulnerability in Adobe Experience Manager Forms
A newly discovered zero-day vulnerability, tracked as CVE-2025-54253, affects Adobe Experience Manager (AEM) Forms on JEE versions 6.5.23.0 and earlier. Adobe has responded by issuing an urgent security update to prevent exploitation. Rated critical with a CVSS score of 10.0, this vulnerability can allow attackers to bypass authentication and execute arbitrary code remotely without requiring any user interaction.
With a public proof-of-concept (PoC) already available, the risk of real-world exploitation is extremely high, making this one of the most urgent vulnerabilities organizations must address.
What is CVE-2025-54253?
Risk Anlysis
Severity: CRITICAL
CVSSv3.1: Base Score: 10.0 CRITICAL
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
Exploit available in public: Yes
Exploit complexity: Low
CVE-2025-54253 is an authentication bypass vulnerability in the FormServer module of Adobe Experience Manager Forms Leading to Arbitrary Code Execution. A vulnerable servlet processes user-supplied input by decoding and deserializing it without proper validation, creating an entry point for attackers.
Because of this vulnerability, vulnerable AEM Forms environments can be remotely hijacked, allowing attackers to achieve Remote Code Execution (RCE) and run arbitrary commands on the server. Exploitation does not require privileges or user interaction, which means attackers can target vulnerable systems over the network with minimal effort.
How the CVE-2025-54253 Exploit Works
Security researchers demonstrated how the zero-day vulnerability can be weaponized:
- Crafting a Malicious Payload – Using tools like ysoserial, attackers can generate a serialized Java payload designed to trigger deserialization vulnerabilities.
- Delivering the Payload – Attackers can wrap the malicious serialized object inside a crafted GET request and deliver it to the exposed servlet.
- Executing Remote Code – Once processed, the payload triggers command execution on the server, allowing the attacker to take control.
- Callback to Attacker’s System – Exploitation can establish a reverse connection (HTTP callback) to the attacker’s infrastructure, enabling further compromise.
This attack chain makes CVE-2025-54253 a high-value target for exploitation, particularly given that it can be automated and scaled against multiple vulnerable AEM instances.
Both standalone deployments (e.g., JBoss) and co-deployed installations with standard AEM setups may be impacted, though standalone deployments are considered more exposed.
Potential Impact of CVE-2025-54253
If successfully exploited, CVE-2025-54253 could lead to:
- Remote Code Execution (RCE): Attackers gain full control over the vulnerable server.
- Bypassing Security Mechanisms: Misconfiguration allows circumvention of existing controls, enabling stealthy exploitation.
- Data Breaches: Sensitive files and customer data can be accessed or exfiltrated.
- Persistence & Pivoting: Compromised systems can be used to launch further attacks within the organization.
Given AEM’s role in managing digital experiences, exploitation could severely disrupt customer-facing services, internal business processes, and regulatory compliance obligations.
Public PoC and Threat Landscape
Researchers have already published proof-of-concept code for CVE-2025-54253. Although Adobe notes that no active exploitation has been observed so far, the availability of a working exploit dramatically raises the chance of it being used in real-world attacks.
Attackers are likely to target:
- Instances where the AEM Forms admin panel is exposed to the internet and Struts2 developer mode is left enabled are especially attractive targets.
- Organizations that have delayed patching due to operational dependencies.
- Standalone AEM Forms on JBoss or other J2EE servers, which may not be as tightly monitored as standard AEM co-deployments.
CVE-2025-54253 – Mitigation Guidance
Adobe strongly recommends immediate patching:
- Apply the emergency update by moving to AEM Forms on JEE version 6.5.0-0108 or newer, which addresses this vulnerability.
If patching cannot be applied immediately, consider these mitigations:
- Restrict Network Access: Limit AEM Forms access to internal networks only.
- Deploy a WAF/IDS: Use a Web Application Firewall (WAF) or Intrusion Detection System to detect and block suspicious serialized payloads.
- Audit Configurations: Ensure that Struts2 developer mode is disabled and review servlet configurations.
- Monitor Logs: Look for signs of unusual serialized input or outbound callbacks to attacker-controlled IPs.
CVE-2025-54253: AppTrana WAAP Coverage
AppTrana WAAP provides Day 0 protection against exploitation attempts targeting CVE-2025-54253. Its AI-driven platform analyzes threat feeds, prioritizes exploits, and adapts defenses in real time. Leveraging real-time threat intelligence, virtual patching, and managed rule updates, AppTrana blocks malicious OGNL payloads at the edge before they ever reach the vulnerable AEM Forms instance.
The vulnerability can be exploited via specially crafted requests to the /adminui/debug endpoint, where attackers inject OGNL expressions to execute system-level commands. In an unprotected setup, these payloads would return sensitive system information or grant remote access. With AppTrana, such requests are intercepted and denied with a 406 response, effectively neutralizing the exploit.
The following screenshots demonstrate how AppTrana WAAP blocks different OGNL payload attempts tied to CVE-2025-54253:
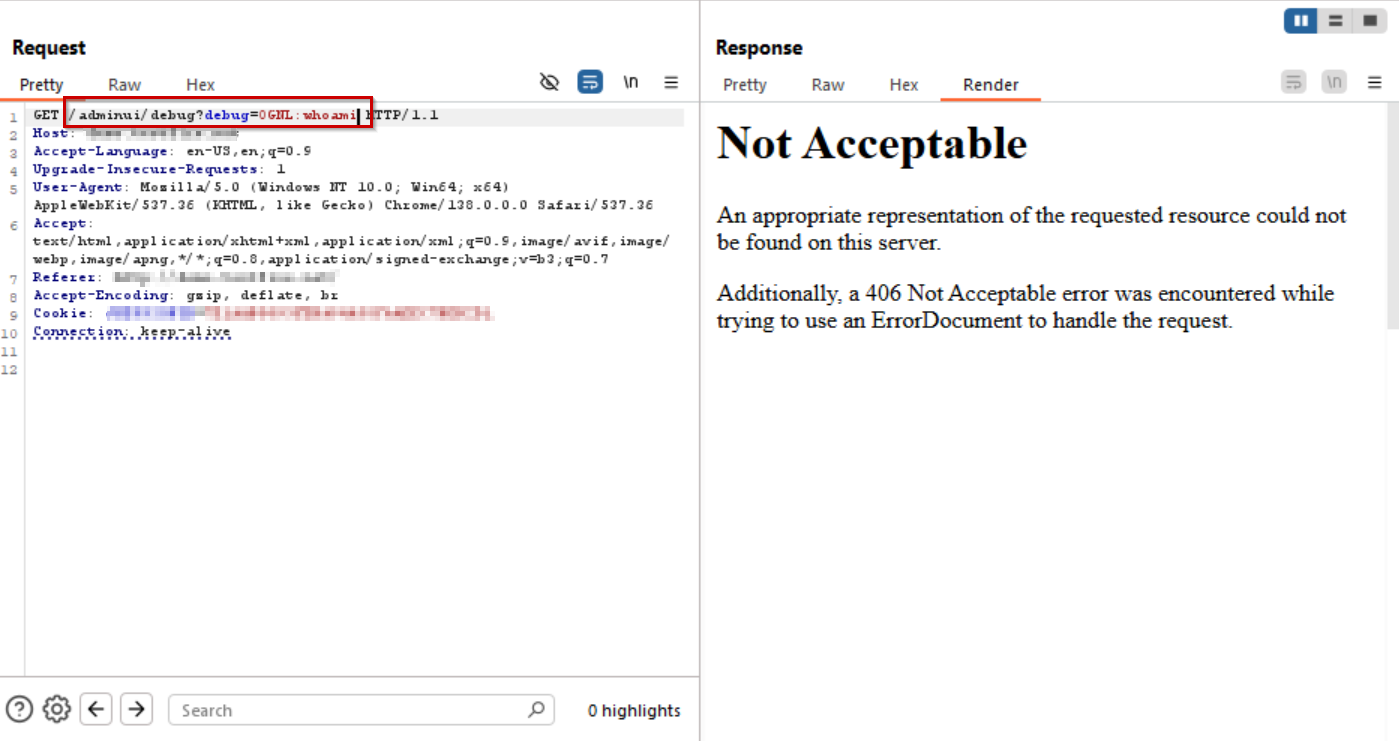
Payload: /adminui/debug?debug=OGNL:whoami
AppTrana WAAP blocks the malicious OGNL payload (whoami) by returning a 406 response.
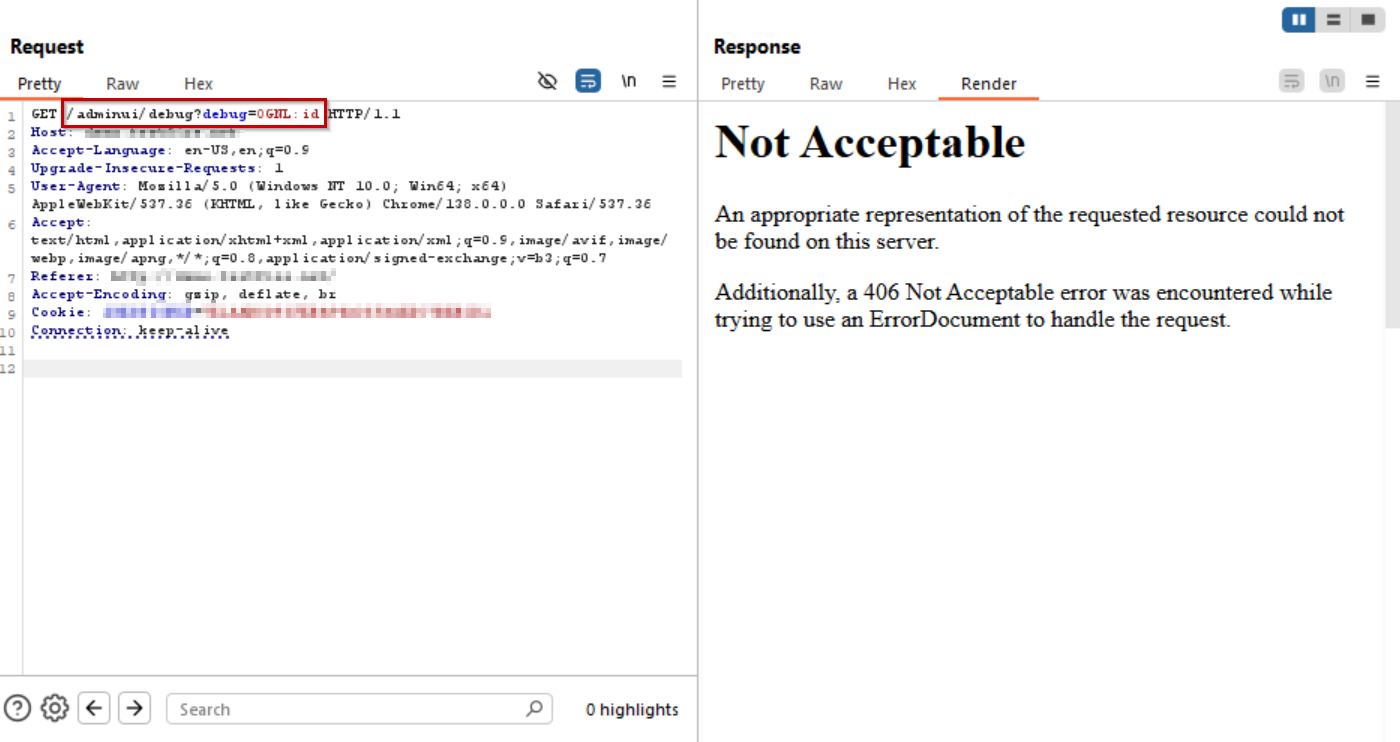
Payload: /adminui/debug?debug=OGNL:id
AppTrana WAAP prevents execution of the injected OGNL command (id), stopping the exploit attempt.
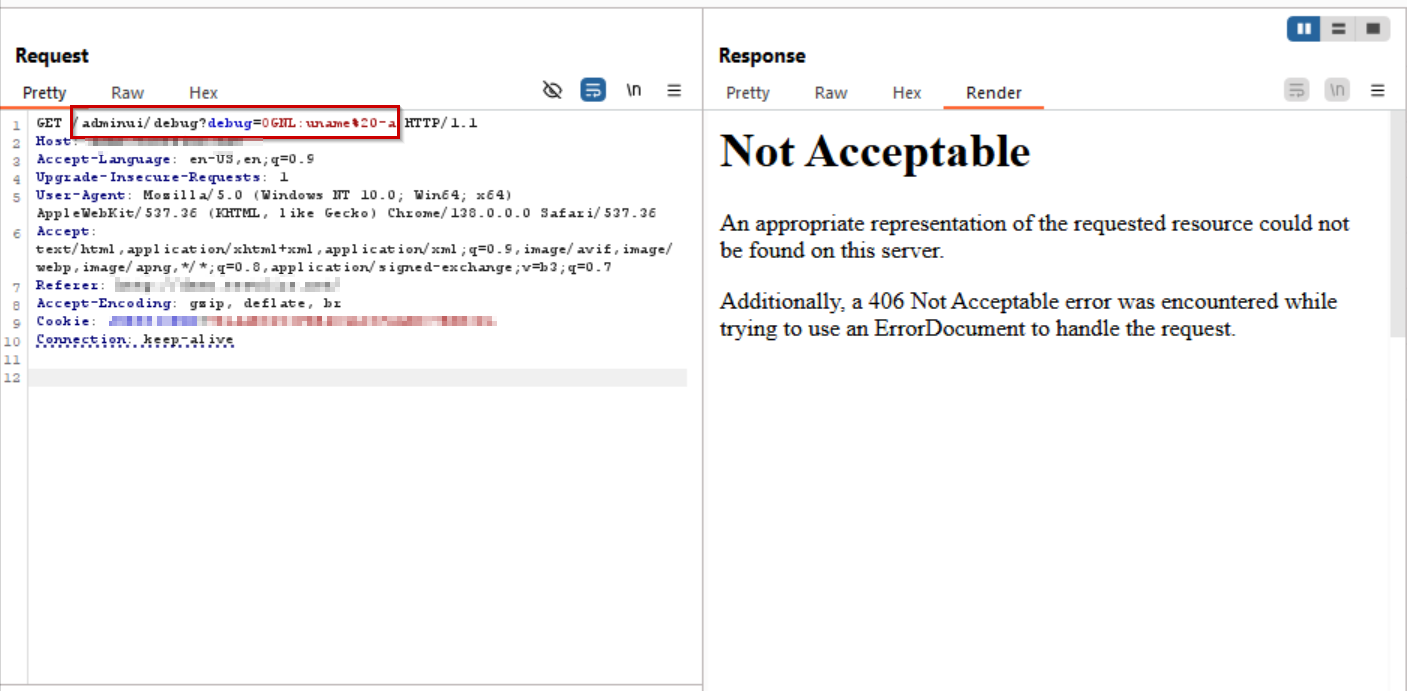
Payload: /adminui/debug?debug=OGNL:uname -a
AppTrana WAAP intercepts the payload (uname -a) and responds with 406, ensuring no command execution.
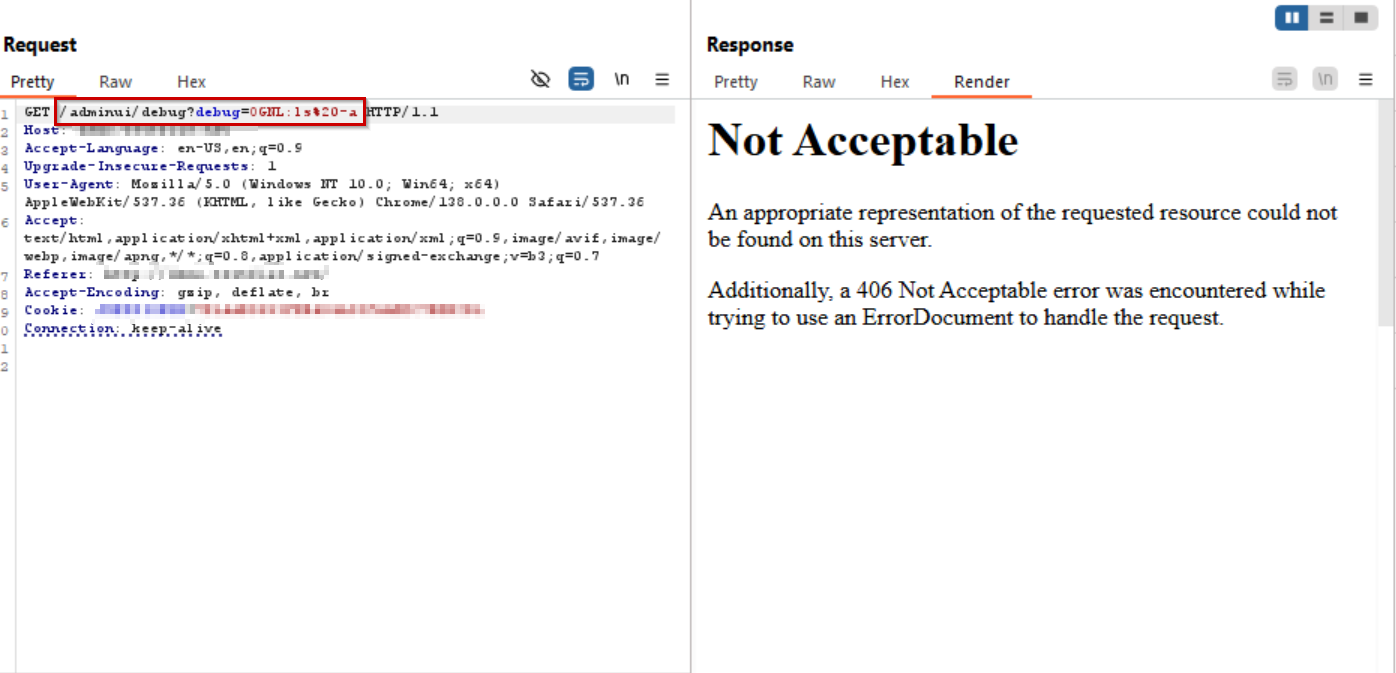
Payload: /adminui/debug?debug=OGNL:ls -a
AppTrana WAAP blocks the directory listing attempt (ls -a) by returning a 406 response, preventing attackers from enumerating server files.

 August 19, 2025
August 19, 2025



